The secret-free component of Contain Service for Kubernetes (ACK) automates the authentication process of image pulls and eliminates the need to configure imagePullSecrets. This topic describes how to install, configure, and use the secret-free component for image pulls as well as relevant precautions.
How the secret-free component works
If you do not turn on Pull from Anonymous Users for a Container Registry instance, you must provide your username and password for authentication each time you want to pull a container image from the Container Registry instance for an ACK cluster. You can store your username and password in a Kubernetes secret to facilitate authentication. However, this method may have the following issues:
Secrets are Base64-encoded plaintext and easy to be leaked.
You must specify the
imagePullSecretsparameter each time you pull an image for a workload.By default, a secret can only be used within the namespace of the secret.
To resolve the preceding issues, you can use the secret-free component of ACK. The following procedure describes how the component works:
aliyun-acr-credential-helper obtains the temporary account and token from the Container Registry instance.
aliyun-acr-credential-helper stores the temporary account and token in a secret.
aliyun-acr-credential-helper associates the secret with the service accounts that you specified in the acr-configuration ConfigMap.
By default, workloads in the service accounts use the temporary account and token that are saved in the secret to pull images.
aliyun-acr-credential-helper can manage service accounts in multiple namespaces at the same time and regularly update the temporary accounts and tokens that are saved in secrets based on your configurations in the ConfigMap. This reduces the leakage risk of temporary accounts and tokens. aliyun-acr-credential-helper eliminates the need to specify imagePullSecrets for your workloads. You are not charged for using aliyun-acr-credential-helper.

Only Container Registry Personal Edition instances that were created on September 8, 2024 or earlier and Container Registry Enterprise Edition instances support aliyun-acr-credential-helper.
Container Registry Personal Edition instances created on or after September 9, 2024 do not support aliyun-acr-credential-helper. If you want to pull images from Container Registry Personal Edition instances that were created later than September 8, 2024, we recommend that you store the username and token that are used to log on to the Personal Edition instance in a secret and then reference the secret in the
imagePullSecretsparameter in the YAML file of the workload.
Editions of the secret-free component
The secret-free component provided by ACK is available in the managed edition (managed-aliyun-acr-credential-helper) and the self-managed edition (aliyun-acr-credential-helper). You can have only one edition installed at the same time. The following table compares the editions.
Item | managed-aliyun-acr-credential-helper | aliyun-acr-credential-helper (self-managed edition) |
Supported cluster versions |
|
|
Deployment method | Deployed in the control plane of the cluster. | Deployed in a Kubernetes cluster by using a workload. By default, a pod that has 0.5 vCPU and 0.5 GiB memory is created for aliyun-acr-credential-helper (self-managed edition) in the kube-system namespace of the cluster. |
Query logs of the component | Not supported. | Supported. |
How to pull images from Container Registry instances across Alibaba Cloud accounts | Use the RAM Roles for Service Accounts (RRSA) feature. | Use worker roles, RRSA, or AccessKey pairs. |
Enable the webhook feature to ensure the instance use of service accounts | Not supported. | Supported. |
Card in the Container Registry console (You can check the edition of the component on the component management page in the Container Registry console.) |
|
|
Prerequisites
Your cluster version is supported by the edition of the secret-free component. For more information, see the table in the preceding "Editions of the secret-free component" section of this topic.
Your Container Registry instance is a Personal Edition instance that was created on September 8, 2024 or earlier or an Enterprise Edition instance.
The RAM role that uses the secret-free component is grant the permissions that are required to access Container Registry instances, read from and write into the image repository, and manage and update secrets. If the RAM is not granted permissions, go to grant permissions to the RAM role.
Use managed-aliyun-acr-credential-helper
Install the component
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left-side pane, choose .
On the Add-ons page, click the Security tab, find the aliyun-acr-credential-helper (Managed) card in the Security section, and then click Install in the lower-right corner of the card.
On the Install aliyun-acr-credential-helper page, you can see the AcrInstanceInfo-related parameters and other parameters. The AcrInstanceInfo-related parameters specifies the information about the Container Registry instances that you want the secret-free component to manage. Other parameter specifies the information about the secret-free component. The following tables describe the parameters.
NoteYou can modify the AcrInstanceInfo-related parameters and other parameters after the secret-free component is installed.
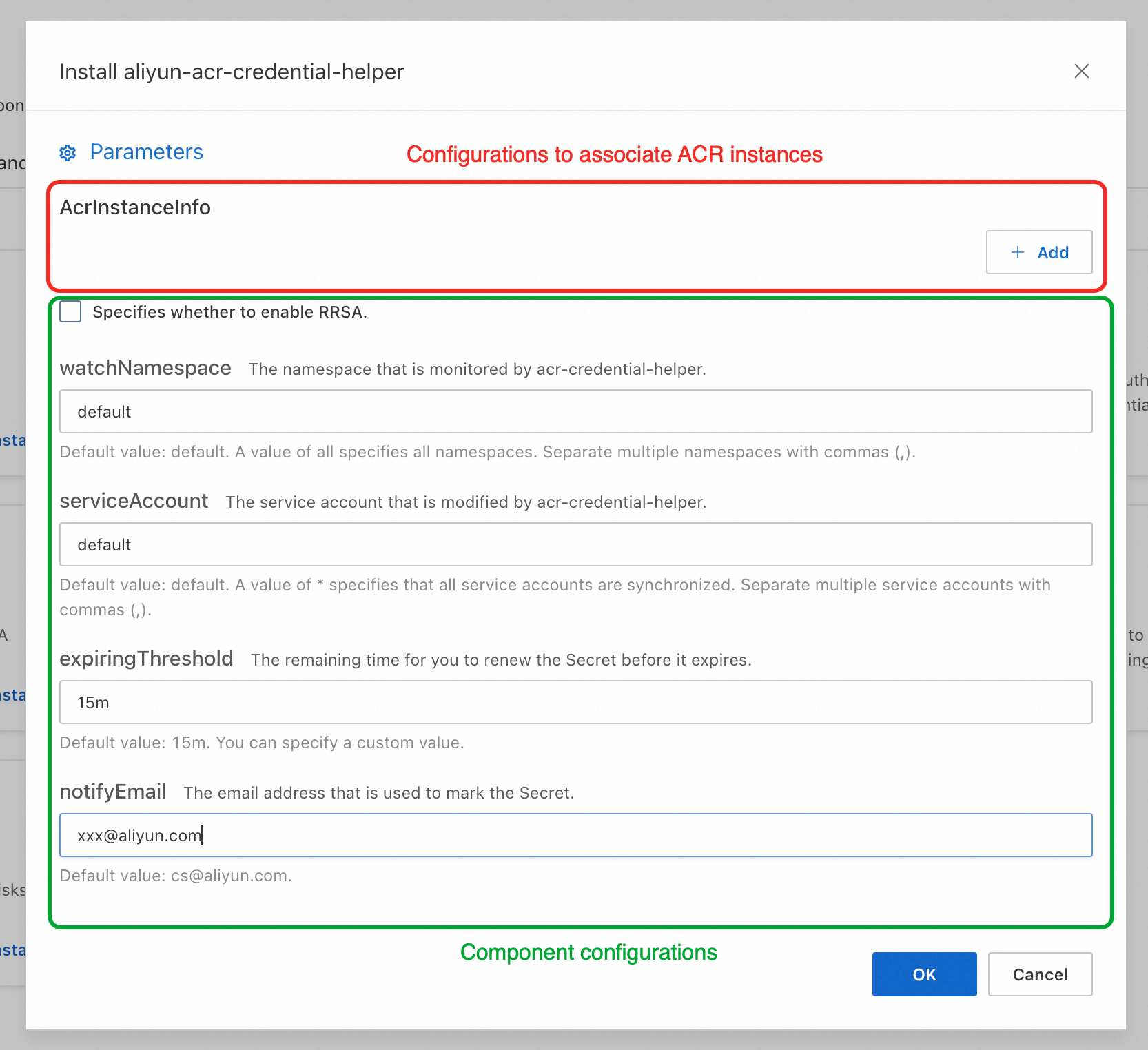
Parameters about the associated Container Registry instances
AcrInstanceInfo
Description
InstanceId
The ID of the Container Registry instance. You can obtain the ID in the Container Registry console.
ImportantLeave this parameter empty if you use a Container Registry Personal Edition instance. You must specify this parameter if you use a Container Registry Enterprise Edition instance.
regionId
The region ID of the Container Registry instance. You can obtain the region ID in the Container Registry console.
ImportantYou must specify this parameter if you want to pull images across regions.
domains
The domain name that the secret-free component uses to access the Container Registry instance. By default, all public domain name and VPC domain name of the Container Registry instance are filled in. You can specify specific domain names. Separate multiple domain names with commas (,).
Specify these parameters only if you want to pull images across accounts
assumeRoleARN
The Alibaba Cloud resource name (ARN) of the RAM role assumed by the owner of the Container Registry instance.
expireDuration
The validity period of the secret that is used to pull images across Alibaba Cloud accounts. Valid values: 3600 to 43200. Default value: 3600. Unit: seconds. Set MaxSessionDuration of the RAM role of Account B to 43200.
rrsaRoleARN
The ARN of the RAM role assumed by the owner of the ACK cluster.
rrsaOIDCProviderRoleARN
The ARN of the OIDC (OpenID Connect) IdP (identity provider) of the ACK cluster.
Parameters about the secret-free component
Parameter
Description
Specifies whether to enable RRSA
Select this option to enable the RRSA feature if you want to pull images across accounts.
watchNamespace
Specify the namespaces from which you want to pull images without using a secret. Default value:
default. A value ofallspecifies all namespaces in the Container Registry instance. You can specify multiple namespaces. Separate multiple namespaces with commas (,). We recommend that you configure your business namespaces for the parameter. If you set the parameter toallor the namespace in which system components of the cluster are stored, system component images may fail to be pulled.serviceAccount
Specify the service accounts that are associated with managed-aliyun-acr-credential-helper. Default value:
Default. A value ofDefaultspecifies the default service accounts of all specified namespaces. A value of an asterisk (*) specifies all service accounts in the specified namespaces. You can specify multiple service accounts. Separate the service accounts with commas (,).expiringThreshold
Specify the period of time after which the secret expires. Default value:
15m. We recommend that you use the default value. The default value specifies that the secret is automatically updated 15 minutes before the secret expires.notifyEmail
You do not need to specify this parameter.
Update the configurations of the secret-free component
To update the configurations of the secret-free component, you can click Configuration in the lower-right corner of the aliyun-acr-credential-helper (Managed) card on the Add-ons page. For information about the parameters used to update the configurations, see preceding tables "Parameters about the associated Container Registry instances" and "Parameters about the secret-free component".
Pull images
After you install and configure the secret-free component, you can specify a service account that is associated with the secret-free component when you create a workload to pull images without using a secret.
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
serviceAccountName: my-service-account # Specify a service account that is associated with the secret-free component.
containers:
- name: nginx
image: ******.cn-hangzhou.cr.aliyuncs.com/nginx/nginx:latest # Specify the address of the Container Registry image.
ports:
- containerPort: 80More operations
Pull images across accounts
managed-aliyun-acr-credential-helper allows you to pull images across Alibaba Cloud accounts by using RAM Roles for Service Accounts (RRSA).
Only in ACK Basic clusters, ACK Pro clusters, and ACK Serverless Pro clusters that run Kubernetes 1.22 or later, you can configure RRSA to pull images from Container Registry Enterprise Edition instances.
After you enable the RRSA feature, the secrets that are generated by managed-aliyun-acr-credential-helper cannot be used to pull private images of Container Registry Personal Edition instances. After you enable the RRSA feature, you cannot use other authentication methods that are described in this topic, such as the AccessKey pair method.
To enable the RRSA feature for managed-aliyun-acr-credential-helper, you must enable RRSA for the cluster on the Basic Information tab of the Cluster Information page in the ACK console and then configure RRSA for managed-aliyun-acr-credential-helper. If you configure RRSA for managed-aliyun-acr-credential-helper and then enable RRSA for the cluster, you must delete the pod that corresponds to managed-aliyun-acr-credential-helper after you enable RRSA for the cluster. This allows RRSA to take effect.
Enable the RRSA feature for the cluster. For more information, see the "Enable RRSA" section of the Use RRSA to authorize different pods to access different cloud services topic.
After the RRSA feature is enabled for the cluster, navigate to the Security and Auditing section under the Basic Information tab. If you hover your mouse over the Enabled label next to RRSA OIDC, the URL and Alibaba Cloud Resource Name (ARN) of the OpenID Connect (OIDC) provider are displayed.
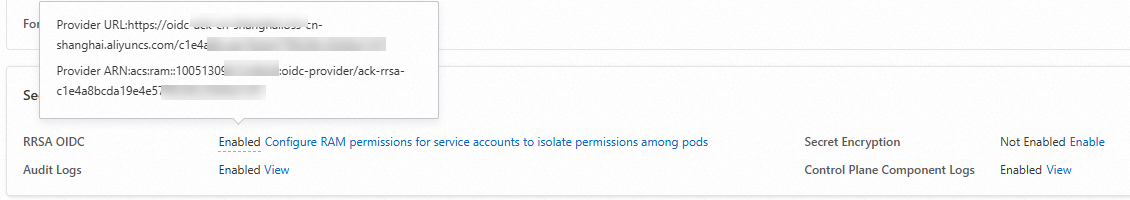
Grant the RAM user of the cluster owner the permissions that are required to access Container Registry resources across accounts.
After you enable the RRSA feature for the cluster, you must perform the following operations to grant permissions to the RAM user of the cluster owner. For example, the current cluster is in Account A and the Container Registry instance is in Account B. If you want to pull images from the Container Registry instance, you must grant the cluster in Account A the permissions to access Container Registry resources of Account B.
Configure the RAM role of Account A.
Create a RAM role in Account A and attach the AliyunSTSAssumeRoleAccess policy to the RAM role. This policy grants the RAM role the permission to assume other RAM roles. Modify the trust policy of the RAM role, as shown in the following code.
Replace
<oidc_issuer_url>in the example with the OIDC IdP URL of the cluster that you recorded in Step 1.Replace
<oidc_provider_arn>in the example with the OIDC IdP ARN of the cluster that you recorded in Step 1.
{ "Statement": [ { "Action": "sts:AssumeRole", "Condition": { "StringEquals": { "oidc:aud": "sts.aliyuncs.com", "oidc:iss": "<oidc_issuer_url>", "oidc:sub": "system:serviceaccount:kube-system:aliyun-acr-credential-helper" } }, "Effect": "Allow", "Principal": { "Federated": [ "<oidc_provider_arn>" ] } } ], "Version": "1" }Configure the RAM role of Account B.
Create a RAM role that has the cr.* permissions in Account B. Click the name of the RAM role. On the Trust Policy tab, enter the ARN of the RAM role of Account A in the Principal field of the trust policy. Attach the following policy to the RAM role of Account B. This policy grants the RAM role of Account B the permissions to obtain information about Container Registry instances and pull images from the instances.
{ "Version": "1", "Statement": [ { "Action": [ "cr:GetAuthorizationToken", "cr:ListInstanceEndpoint", "cr:PullRepository" ], "Resource": "*", "Effect": "Allow" } ] }You can specify the MaxSessionDuration parameter for the RAM role. Valid values of this parameter range from 3600 to 43200 seconds. You must specify the expireDuration parameter in the following step 7 when you configure managed-aliyun-acr-credential-helper. For more information, see Specify the maximum session duration for a RAM role. We recommend that you specify the same value for MaxSessionDuration and expireDuration. The value of expireDuration can be smaller than or equal to the value of MaxSessionDuration.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left-side pane, click Cluster Information.
In the left-side navigation pane, choose .
On the Add-ons page, click the Security tab, find the aliyun-acr-credential-helper (Managed) card in the Security section, and then click Configuration in the lower-right corner of the card. In the aliyun-acr-credential-helper Parameters dialog box, click Add and then use the Container Registry instance information of Account B to configure parameters in the AcrInstanceInfo section. Click OK. Then, users can pull images from the Container Registry instance of Account B.
Use aliyun-acr-credential-helper
Install the component
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left-side pane, choose .
On the Add-ons page, click the Security tab, find the aliyun-acr-credential-helper card in the Security section, and then click Install in the lower-right corner of the card.
In the Install aliyun-acr-credential-helper dialog box, select a permission mode that the component uses from the tokenMode drop-down list and then click OK. The following table describes the permission modes that can be used by the component. After you install the component, you must configure the component before you can use the component to pull images without using a secret. For information about how to configure the component, see Update the configurations of the secret-free component.
tokenMode
Description
auto
(Recommend) The component detects when the cluster was created and automatically determines the permission mode that the component uses. If the cluster was created before April 03, 2023, the component uses the workerRole permission mode. If the cluster was created on or after April 03, 2023, the component uses the managedRole permission mode.
ImportantThe version of aliyun-acr-credential-helper that was released after April 03, 2023 provides configuration items to allow you to specify the RAM role on which the component relies. For more information, see [Product Changes] Revoke the permissions on which aliyun-acr-credential-helper relies.
managedRole
The component uses the AliyunCSManagedAcrRole role that is granted specific permissions in the Prerequisites to obtain permissions.
workerRole
The component uses the worker role of the cluster to obtain permissions. To use this mode, you must grant specific permissions to the worker role of the cluster. For more information, see aliyun-acr-credential-helper uses the workerRole permission mode.
ImportantSelect this mode if you want to pull images across accounts by role assuming.
Update the configurations of the secret-free component
After the aliyun-acr-credential-helper component is installed, you must configure the acr-configuration ConfigMap by using the ACK console or kubectl before you can pull images.
ACK console
On the Clusters page, click the name of the one you want to change. In the left-side navigation pane, choose .
In the upper part of the ConfigMap page, select kube-system from the Namespace drop-down list. Then, find the acr-configuration ConfigMap and configure the parameters. The following table describes the parameters.
Component configurations
Description
watch-namespace
The namespaces from which you want to pull images without using a secret. Default value: default. A value of all specifies all namespaces in the Container Registry instance. Separate multiple namespaces with commas (,). We recommend that you configure your business namespaces for the parameter. If you set the parameter to
allor the namespace in which system components of the cluster are stored, system component images may fail to be pulled.acr-api-version
Use the default value.
expiring-threshold
The period of time after which the secret expires. Default value:
15m. We recommend that you use the default value. The default value specifies that the secret is automatically updated 15 minutes before the secret expires.acr-registry-info
The information about Container Registry instances. Each instance can be specified by three parameters of the string type in a YAML file.
instanceId: The ID of the Container Registry instance. You can obtain the ID in the Container Registry console.ImportantLeave this parameter empty if you use a Container Registry Personal Edition instance. You must specify this parameter if you use a Container Registry Enterprise Edition instance.
regionId: The region ID of the Container Registry instance. You can obtain the region ID in the Container Registry console.ImportantYou must specify this parameter if you want to pull images across regions. See the following configuration example.
domains: The domain name that the secret-free component uses to access the Container Registry instance. By default, all domain names of the ACR instance in theinstanceIdare entered. You can specify specific domain names. Separate multiple domain names with commas (,).
service-account
The service accounts that are associated with aliyun-acr-credential-helper. Separate multiple service accounts with commas (,). A value of default specifies the default service accounts of all namespaces specified in watch-namespace. A value of an asterisk (
*) specifies all service accounts in the specified namespaces.
kubectl
Run the following command to modify the
acr-configurationConfigMap based on the following information.kubectl edit cm acr-configuration -n kube-systemKey
Description
Value
service-account
The service accounts that are used by the aliyun-acr-credential-helper component to pull images.
Default value: default.
NoteSeparate multiple service accounts with commas (,). An asterisk (
*) specifies all service accounts in all namespaces.acr-registry-info
The information about Container Registry instances. Each instance can be specified by three parameters of the string type in a YAML file.
NoteParameters for specifying an instance:
instanceId: the ID of the Container Registry instance. This field is required for Container Registry Enterprise Edition instances.
regionId: the ID of the region where the Container Registry instance resides. This parameter is optional. The default value is the region where your ACK cluster resides.
domains: the domain names of the Container Registry instance. This parameter is optional. By default, all domain names of the instance are specified. Separate multiple domain names with commas (,).
Sample configuration for a Container Registry Enterprise Edition instance:
- instanceId: <cri-instanceId> regionId: "cn-hangzhou" domains: "xxx.com,yyy.com"watch-namespace
The namespaces from which you want to pull images without using a secret.
Default value: default. A value of all specifies all namespaces in the Container Registry instance. Separate multiple namespaces with commas (,).
NoteWe recommend that you set the values to your production namespaces. If you set the value to all or namespaces of the system components of the cluster, images in the namespaces may fail to be pulled.
expiring-threshold
The period of time after which the cached Secret expires.
Default value: 15m.
NoteWe recommended that you use the default value. The default value specifies that the Secret is updated 15 minutes before the cached Secret expires.
Pull images
After you install and configure the secret-free component, you can specify a service account that is associated with the secret-free component when you create a workload to pull images without using a secret.
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
serviceAccountName: my-service-account # Specify a service account that is associated with the secret-free component.
containers:
- name: nginx
image: ******.cn-hangzhou.cr.aliyuncs.com/nginx/nginx:latest # Specify the address of the Container Registry image.
ports:
- containerPort: 80Precautions
Use Container Registry Personal Edition instances
If you want to pull images from a Container Registry Personal Edition instance, leave instanceId empty.
data:
service-account: default
watch-namespace: all
expiring-threshold: 15m
notify-email: c*@example.com
acr-registry-info: |
- instanceId: "" # Leave this parameter empty if you want to pull images from a Container Registry Personal Edition instance.
regionId: cn-xxxxaliyun-acr-credential-helper uses the workerRole permission mode
If you select workerRole as the permission mode used by aliyun-acr-credential-helper, the worker role of the cluster must have the following permissions:
{
"Version": "1",
"Statement": [
{
"Action": [
"cr:GetAuthorizationToken",
"cr:ListInstanceEndpoint",
"cr:PullRepository"
],
"Resource": "*",
"Effect": "Allow"
}
]
}More operations
Pull images across accounts
aliyun-acr-credential-helper allows you to use the following methods to pull images from a Container Registry instance across accounts.
Use RRSA: Service accounts in the cluster of Account A assume the role of Account B. Pods that use the service accounts can pull private images of Account B.
Use the worker role: The worker role of Account A assumes a RAM role of Account B that has the cr.* permissions. Then, aliyun-acr-credential-helper uses the worker role to pull private images of Account B. To use this method, you must select the workerRole permission mode for aliyun-acr-credential-helper.
Use the AccessKey pair of a RAM user of the Container Registry instance owner: aliyun-acr-credential-helper of Account A uses the AccessKey pair of a RAM user of Account B to pull private images of Account B. This method is easy to use, but the AccessKey pair of the RAM user of Account B are stored in plaintext and may be leaked.
Use RRSA
Only in ACK Basic clusters, ACK Pro clusters, and ACK Serverless Pro clusters that run Kubernetes 1.22 or later, you can configure RRSA to pull images from Container Registry Enterprise Edition instances.
To enable the RRSA feature, you must update aliyun-acr-credential-helper to v23.02.06.1-74e2172-aliyun or later.
To enable the RRSA feature for managed-aliyun-acr-credential-helper, you must enable RRSA for the cluster on the Basic Information tab of the Cluster Information page in the ACK console and then configure RRSA for managed-aliyun-acr-credential-helper. If you configure RRSA for aliyun-acr-credential-helper and then enable RRSA for the cluster, you must delete the pod that corresponds to aliyun-acr-credential-helper after you enable RRSA for the cluster. This allows RRSA to take effect.
Enable the RRSA feature for the cluster. For more information, see Enable RRSA.
After you enable the RRSA feature for the cluster, in the Security and Auditing section of the Basic Information tab on the Cluster Information page, move the pointer over Enabled next to RRSA OIDC to view and record the URL and ARN of the OIDC IdP.

Grant the RAM user of the cluster owner the permissions that are required to access Container Registry resources across accounts.
After you enable the RRSA feature for the cluster, you must perform the following operations to grant permissions to the RAM user of the cluster owner. For example, the current cluster is in Account A and the Container Registry instance is in Account B. If you want to pull images from the Container Registry instance, you must grant the cluster in Account A the permissions to access Container Registry resources of Account B.
Create a RAM role in Account A and attach the AliyunSTSAssumeRoleAccess policy to the RAM role. This policy grants the RAM role the permission to assume other RAM roles. Modify the trust policy of the RAM role, as shown in the following code.
Replace
<oidc_issuer_url>in the example with the OIDC IdP URL of the cluster that you recorded in Step 1.Replace
<oidc_provider_arn>in the example with the OIDC IdP ARN of the cluster that you recorded in Step 1.
{ "Statement": [ { "Action": "sts:AssumeRole", "Condition": { "StringEquals": { "oidc:aud": "sts.aliyuncs.com", "oidc:iss": "<oidc_issuer_url>", "oidc:sub": "system:serviceaccount:kube-system:aliyun-acr-credential-helper" } }, "Effect": "Allow", "Principal": { "Federated": [ "<oidc_provider_arn>" ] } } ], "Version": "1" }Create a RAM role that has the cr.* permissions in Account B. On the Trust Policy tab, enter the ARN of the RAM role of Account A in the Principal field of the trust policy.
{ "Statement": [ { "Action": "sts:AssumeRole", "Effect": "Allow", "Principal": { "RAM": [ <ARN of the RAM role that you created for Account A> ] } } ], "Version": "1" }Attach the following policies to the RAM role of Account B. The policies grants the RAM role of Account B the permissions to obtain information about Container Registry instances and pull images from the instances.
{ "Version": "1", "Statement": [ { "Action": [ "cr:GetAuthorizationToken", "cr:ListInstanceEndpoint", "cr:PullRepository" ], "Resource": "*", "Effect": "Allow" } ] }You can specify the MaxSessionDuration parameter for the RAM role. Valid values of this parameter range from 3600 to 43200 seconds. You must specify the
expireDurationparameter in the following Step 3 when you configure the acr-configuration ConfigMap. We recommend that you specify the same value for MaxSessionDuration andexpireDuration. The value ofexpireDurationcan be smaller than or equal to the value of MaxSessionDuration.
Configure the acr-configuration ConfigMap
Modify the acr-configuration ConfigMap based on the following information.
data: service-account: "default" watch-namespace: "all" expiring-threshold: "15m" notify-email: "c*@example.com" acr-registry-info: | - instanceId: "cri-xxx" regionId: "cn-hangzhou" domains: "instance.default.domain.com,instance.custom.domain.com" rrsaRoleARN: aUserRoleARN rrsaOIDCProviderRoleARN: aUserClusterOIDCProviderRoleARN assumeRoleARN: bUserRoleARN expireDuration: 3600 rrsa: | enable: trueParameter
Description
Example
rrsaRoleARNThe ARN of the RAM role that you created for Account A.
acs:ram::aaa
rrsaOIDCProviderRoleARNThe ARN of the OIDC IdP that you obtained on the Basic Information tab of the Cluster Information page in the ACK console.
acs:ram::bbb
assumeRoleARNThe ARN of the RAM role that you created for Account B.
acs:ram::ccc
expireDurationThe session period of the RAM role that you created for Account B. The session period is equal to the validity period of the secret that is generated by aliyun-acr-credential-helper.
ImportantThe expireDuration value cannot be greater than the MaxSessionDuration value of the RAM role of Account B.
Default value: 3600. Valid values: 3600 to 43200. Unit: seconds.
Use the worker role
You must select the workerRole permission mode for aliyun-acr-credential-helper.
The RAM role of Account B must have the cr.* permissions to pull private images from a specified private repository of a Container Registry instance.
Account B allows the worker role of the ACK cluster of Account A to assume the RAM role of Account B. This rule requires you to modify the trust policy of the RAM role of Account B.
The worker role of the ACK cluster of Account A must have the permission to assume the RAM role of Account B. This rule requires you to attach the AliyunAssumeRoleAccess policy to the worker role of Account A.
Create a RAM role for Account B. Specify Cloud Account as the trusted entity of the RAM role. Make sure that the RAM role is granted the permissions that are required to pull private images from Container Registry instances of Account B. For more information, see Create a RAM role for a trusted Alibaba Cloud account.
{ "Version": "1", "Statement": [ { "Action": [ "cr:GetAuthorizationToken", "cr:ListInstanceEndpoint", "cr:PullRepository" ], "Resource": "*", "Effect": "Allow" } ] }Modify the trust policy of the RAM role of Account B to allow the worker role of the ACK cluster of Account A to assume the RAM role of Account B.
Obtain the ARN of the worker role of the ACK cluster.
For information about how to obtain the ARN of a RAM role, see How do I view the ARN of a RAM role?
Modify the trust policy of the RAM role of Account B.
Log on to the RAM console. In the left-side navigation pane, click Roles. On the Roles page, find the RAM role of Account B and click the role name.
On the details page of the RAM role, click the Trust Policy tab and enter the ARN of the worker role of Account A in the Principal field of the trust policy.
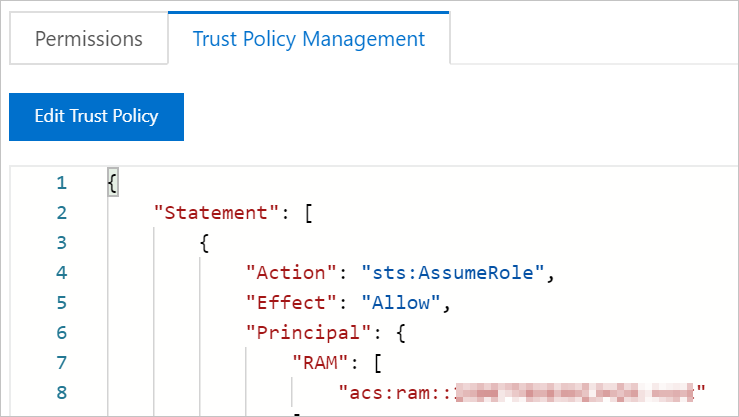
Check whether the worker role of the ACK cluster in Account A is granted the AssumeRole permission. For more information, see View the information about a policy.
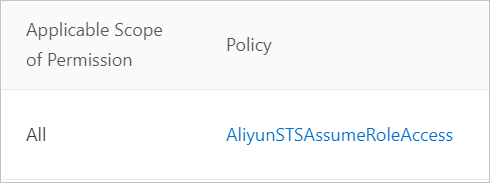
Add the assumeRoleARN parameter to the acr-configuration ConfigMap.
Set the value of the assumeRoleARN parameter to the ARN of the RAM role of Account B. For information about how to obtain the ARN of a RAM role, see How do I view the ARN of a RAM role? The following JSON file shows the sample configuration of acr-configuration.
data: service-account: "default" watch-namespace: "all" expiring-threshold: "15m" notify-email:"c*@example.com" acr-registry-info: | - instanceId: "" regionId: "cn-beijing" domains: "registry.cn-beijing.aliyuncs.com" assumeRoleARN: "acs:ram::.*:role/kubernetesworkerrole-test" expireDuration: 3600
Use the AccessKey pair of a RAM user of the Container Registry instance owner
Enable the webhook feature to ensure the instant use of service accounts
To enable the webhook feature, you must update aliyun-acr-credential-helper to v23.02.06.1-74e2172-aliyun or later.
After you enable the webhook feature, the secret-free component uses the webhook feature to monitor changes of service accounts in the cluster. After a service account is created, the secret-free component immediately injects the secret into the service account. If you want to use a service account immediately after it is created, for example, if you use a Helm chart to create a service account and a Deployment, you can enable the webhook feature. The webhook feature can impact the performance of the secret-free component. We do not recommend you enable the webhook feature in other scenarios.
To use the webhook feature, you must add the following parameters to the acr-configuration ConfigMap:
data:
webhook-configuration: |
enable: true
failure-policy: Ignore
timeout-seconds: 10Parameter | Description |
| Specifies whether to enable the webhook feature.
|
| Specifies how to handle the service account when the webhook feature does not work as expected.
Important Due to the limits of the cluster API Server, if you set |
| The timeout period of a request for creating service accounts. When a request for creating service accounts times out, the system responds based on the |
References
For information about the release notes of aliyun-acr-credential-helper, see aliyun-acr-credential-helper.