You can configure advanced features for the Security Center agent to improve security and resource efficiency. For example, you can enable Agent Protection to prevent malicious uninstallation or configure resource usage limits to control the CPU and memory consumption of operations such as local file detection. This topic describes the features that are available for agent capability configuration and how to configure them.
Agent Protection
Function overview
Agent self-protection is a built-in protection mechanism that ensures the stable operation of the Security Center agent. It actively intercepts unauthorized actions such as uninstallation and process termination. This prevents the agent from being disabled by attackers or abnormal processes, which ensures that Security Center provides continuous and effective server protection.
This feature protects only the agent itself and does not directly provide server security protection.
Core value
Prevent malicious uninstallation: Blocks attackers from removing the security agent after compromising a server.
Ensure process stability: Protects core agent processes from being terminated accidentally or maliciously.
Ensure protection continuity: Avoids security protection interruptions caused by agent failure.
Compatibility: This feature depends on specific operating systems and kernel versions. If the server environment is not compatible, the feature status shows 'Protection failed: Incompatible kernel version' and the feature will not take effect.
Scope
Edition limits: This feature is available to both free and paid users of Security Center.
Operating system and kernel version limits: For more information, see Appendix: Supported operating systems and kernel versions for agent self-protection.
Enable agent self-protection for a server
After you enable the defense mode for agent self-protection, the feature is automatically enabled for all servers that are within the protection scope and have the agent installed.
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
Click the tab. In the Agent Protection section, turn on the Defense Mode switch.
To the right of Protection Scope:, click Manage.
In the Agent Protection panel, select the servers for which you want to enable agent self-protection, and then click OK.
NoteAfter you enable Agent Protection for a server, the protection mechanism takes effect immediately. If you disable Agent Protection, the mechanism is disabled after 5 minutes.
View the agent self-protection status
Follow these steps to check the agent self-protection status for a server.
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
In the host asset list, find the target server and click the server name or click View in the Actions column.
On the server details page, click the tab. In the Defense Status section, view the Agent Protection status.
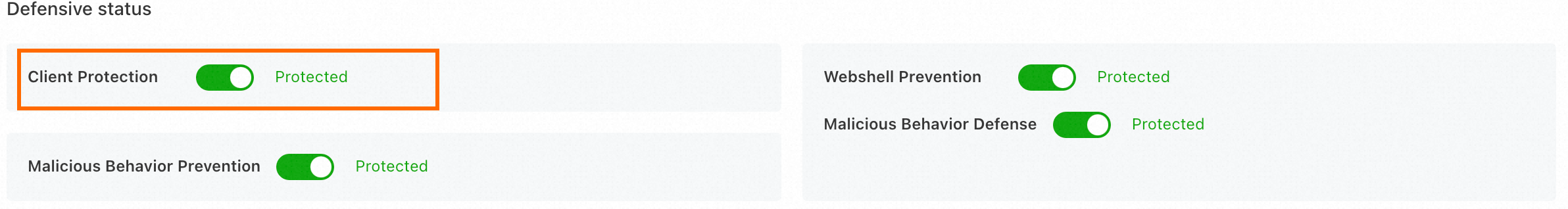
Uninstallation instructions
After you enable self-protection, agent uninstallation is restricted. You can uninstall the agent only using one of the following authorized methods:
Uninstall from the console: Uninstall the agent directly from the Security Center console.
Uninstall locally: First, disable the agent self-protection feature for the server in the console. Then, uninstall the agent locally on the server.
Local File Detection Engine
Function overview
The local file detection engine is a proprietary threat detection engine developed by Alibaba Cloud Security Center for local files. This engine reduces performance overhead from data uploads and cloud-based scanning, which improves detection efficiency.
After you enable this feature, files are scanned using a dual-engine mode that combines local and cloud-based scanning. The system first uses the local engine to scan files. If no threats are found, the files are then uploaded to the cloud for a secondary scan to ensure comprehensive detection.
Scope
Required subscription: Enterprise or Ultimate. If you are using a different edition, you must upgrade.
NoteThe protection edition for the server must be set to the edition that you purchased. For more information, see Attach a protection edition to a server.
Pay-as-you-go: This billing method is required for Host and Container Security. To enable it, see Purchase.
NoteThe server protection level must be set to Host Protection or Host and Container Protection. For more information, see Attach a protection level to a server.
Enable local file detection
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
Click the tab. In the Local File Detection Engine section, turn on the File Test switch.
To the right of Installation Scope, click Manage.
In the Local File Detection Engine panel, select the servers for which you want to enable local file detection, and then click OK.
In-depth Detection Engine
The deep detection engine helps you discover advanced security risks, such as rootkits, tunneling, and backdoors.
Scope
Required subscription: Enterprise or Ultimate. If you are using a different edition, you must upgrade.
NoteThe protection edition for the server must be set to the edition that you purchased. For more information, see Attach a protection edition to a server.
Pay-as-you-go: This billing method is required for Host and Container Security. To enable it, see Purchase.
NoteThe server protection level must be set to Host Protection or Host and Container Protection. For more information, see Attach a protection level to a server.
Enable deep detection
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
Click the tab. In the In-depth Detection Engine section, turn on the Depth Test switch.
To the right of Installation Scope, click Manage.
In the In-depth Detection Engine panel, select the servers for which you want to enable deep detection, and then click OK.
Client Resource Management
When the Security Center agent runs on a server, it consumes a small amount of server resources. Security Center provides three resource management modes that you can use to manage the agent's resource consumption. Select a suitable protection mode for your server to achieve optimal security protection.
Resource management modes
When you select any resource management mode, if the agent exceeds the maximum configured limits for memory or CPU usage, the agent pauses. The agent automatically restarts after resource usage drops to an acceptable level.
Protection mode | Maximum memory or CPU usage | Supported editions | Scenarios |
Low Consumption Mode |
| All editions | This mode is suitable for business scenarios with low security requirements. In this mode, the agent automatically downgrades features that consume large amounts of resources. This may cause delays in threat detection. We recommend that you enable Smooth mode. Note The low-consumption mode is enabled by default for newly added assets in Security Center. |
Smooth Mode |
| Anti-virus, Advanced, Enterprise, and Ultimate | This mode is suitable for protecting critical business. In this mode, the agent consumes more resources to collect data and ensure timely risk detection. |
Custom Mode |
| Enterprise and Ultimate | This mode is suitable for ensuring security during major events. In this mode, you can flexibly control memory and CPU usage. Important If the agent resource limit threshold is too low, some detection capabilities may fail. Configure this setting with caution. |
Set a protection mode
Log on to the Security Center console.
In the navigation pane on the left, choose . In the upper-left corner of the console, select the region where your assets are located: Chinese Mainland or Outside Chinese Mainland.
Click the tab. In the Client Resource Management section, click Manage to the right of Smooth Mode or Custom Mode.
In the Smooth Mode or Custom Mode panel, select the servers for which you want to set the resource management mode, and then click OK.
You can select only one resource management mode, either Smooth Mode or Custom Mode, for each server. For example, if a server is in Smooth Mode and you set it to Custom Mode, its protection mode changes to Custom Mode.
NoteIn Custom Mode, more types of alerts are detected and the detection engine is more sensitive. This may increase the false positive rate. We recommend that you monitor and handle alerts promptly.
(Optional) If you set a server to Custom mode, you can modify the memory and CPU usage thresholds.
Higher thresholds for memory and CPU usage allow for more precise protection. We recommend that you configure appropriate thresholds.
Appendix: Supported operating systems and kernel versions for agent self-protection
Operating system | Supported operating system versions | Supported kernel versions |
Windows (64-bit) |
| All versions |
CentOS (64-bit) |
| |
Ubuntu (64-bit) |
| |
Alibaba Cloud Linux (Alinux) (64-bit) | Alinux 2.1903 | |
Anolis (64-bit) | All versions | |
RHEL | RHEL 6, 7, and 8 |
|