This topic provides answers to some frequently asked questions about data security and encryption.
About IP whitelists
How can I allow a server to access only a specified node in a cluster?
You can use a custom cluster endpoint. Servers that connect to a custom cluster endpoint of a cluster are allowed to access only a specified node in the cluster.
How many IP addresses or CIDR blocks can I add to all IP whitelists?
You can add at most 1,000 IP addresses or CIDR blocks to all IP whitelists. Security groups do not have this limit.
Why am I unable to connect an Elastic Compute Service (ECS) instance to a cluster after I add the IP address of the ECS instance to an IP whitelist?
You can perform the following steps to locate the cause:
Check whether the setting of the IP whitelist is correct. If you want to connect the ECS instance to the internal endpoint of the cluster, you must add the private IP address of the ECS instance to the IP whitelist. If you want to connect the ECS instance to the public endpoint of the cluster, you must add the public IP address of the ECS instance to the IP whitelist.
Check whether the ECS instance and the PolarDB for MySQL cluster are deployed in the same type of network. If the ECS instance runs in a classic network, you can migrate the ECS instance to the virtual private cloud (VPC) where the PolarDB cluster is deployed. For more information, see Overview of migration solutions.
NoteIf you want to connect the ECS instance to other internal resources that are located in the classic network, do not migrate the ECS instance to the VPC. The ECS instance cannot connect to the classic network after you migrate the ECS instance to the VPC.
You can also use the ClassicLink feature to connect the classic network to the VPC network.
Check whether the ECS instance and the PolarDB for MySQL cluster run in the same VPC. If the ECS instance and the cluster run in different VPCs, you must purchase another PolarDB cluster in the VPC of the ECS instance, or activate Cloud Enterprise Network (CEN) to connect the two VPCs.
Why am I unable to connect to the public endpoint of a cluster?
You may fail to connect to the public endpoint of a cluster due to the following reasons:
If you connect an ECS instance to the public endpoint of the cluster, you must add the public IP address of the ECS instance to an IP whitelist of the cluster. Do not add the private IP address of the ECS instance.
Set the IP whitelist to
0.0.0.0/0and try to access the cluster. If you can access the cluster, the public endpoint that was used before is incorrect. For more information about how to check the public endpoint, see Manage the endpoints of a cluster.
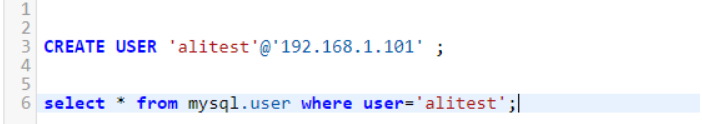
How can I allow a user account to access a PolarDB cluster from only a specified IP address?
You can create a privileged account by running the following commands. Then, you can log on with the privileged account and specify the IP address that standard accounts can use to access the cluster.
Why am I unable to access a database after I configure an IP whitelist for the cluster?
Check whether an IP whitelist is configured. To allow access from all sources, the IP address in the whitelist is
0.0.0.0/0, instead of0.0.0.0. If an IP whitelist is configured for the cluster, perform the following steps to check whether the IP whitelist is valid:Check the format of the IP whitelist.
To add a specified IP address to the whitelist, you do not need to specify a CIDR block. To add
1.1.1.1to a whitelist, you cannot set it to1.1.1.1/2.To add a CIDR block to the whitelist, the CIDR block must be in the
x.x.x.x/xformat.
To add public IP addresses to the whitelist, you must check the number of egress IP addresses in the current environment. Refresh the result multiple times to check whether the egress IP addresses change. If multiple egress IP addresses are configured, add all public IP addresses to the whitelist. If all public IP addresses in the current environment are added to the whitelist, or access over the internal network is abnormal, perform next steps.
Set the IP address in the whitelist to 0.0.0.0/0.
Connect to the database and execute the
select user(),current_user();statement. Add the obtained IP address to the whitelist.Delete 0.0.0.0/0 from the whitelist.
What can I do if my database is attacked?
Check whether the IP address in the whitelist of the cluster is set to 0.0.0.0/0.
Why am I unable to access a PolarDB database from an ECS instance?
You can perform the following steps:
Check whether the ECS instance and PolarDB cluster are deployed in the same region.
Check whether the ECS instance and PolarDB cluster use the same network type. If the ECS instance and PolarDB cluster use the VPC network type, they must be on the same VPC. If they are not on the same VPC, you can Use CEN and Basic Edition transit routers to connect VPCs in the same region.
Check whether the IP address of the ECS instance is added to the IP whitelist of the cluster. If you want to access the PolarDB database over the Internet, you must add the public IP address of the ECS instance to the IP whitelist of the PolarDB cluster. For more information, see Configure an IP whitelist.
About SSL encryption
What will happen if I do not renew an expired SSL certificate? Will my instance stop running or data security be compromised?
If you do not renew the SSL certificate after it expires, your instance can still run as normal and data security is not compromised. However, applications that connect to your instance through encrypted connections are disconnected.
About transparent data encryption (TDE)
Can I continue to use common database tools, such as Navicat, after I enable TDE?
Yes, you can continue to use common database tools after you enable TDE.
Why is data still displayed in plaintext after it is encrypted?
When data is queried, the data is decrypted and loaded to the memory. Therefore, the data is displayed in plaintext. After TDE is enabled, the stored data is encrypted.
Do I need to modify TDE for existing tables?
After TDE is enabled for an empty cluster, newly created tables are automatically encrypted. For existing tables, you need to perform DDL operations for encryption or decryption.
About security management
What is TDE encryption?
Transparent Data Encryption (TDE) allows you to perform real-time I/O encryption and decryption on data files. Data is encrypted before it is written to the disk and is decrypted when it is read from the disk to the memory. TDE for PolarDB for MySQL adopts the Advanced Encryption Standard (AES) algorithm. The key length is 256 bits. The keys that are used in TDE are generated and managed by KMS. PolarDB for MySQL does not provide keys or certificates. For more information, see Configure TDE for a PolarDB cluster.
What is SSL encryption?
SSL is developed by Netscape to allow encrypted communication between a web server and a browser. SSL supports various encryption algorithms, such as RC4, MD5, and RSA. This topic describes how to make data transmission more secure by configuring Secure Sockets Layer (SSL) encryption. You must enable SSL encryption and install SSL certificates that are issued by certificate authorities (CAs) in the required applications. SSL is used to encrypt connections at the transport layer and enhance the security and integrity of the transmitted data. However, SSL encryption increases the round-trip time. For more information, see Configure SSL encryption.
Q: What are the differences between TDE encryption and SSL encryption?
You must enable TDE for data file encryption. You must enable SSL for transmission encryption.
Q: Can I use a custom key for TDE?
Yes, you can optimize PHP short-lived connections in high concurrency scenarios.
If you do not have a custom key, you can create a key and import your own key material in the KMS console. For more information, see Create a CMK.
When you use an existing custom key, take note of the following points:
If you disable the key, configure a plan to delete the key, or delete the key material, the key becomes unavailable.
After the authorization to your PolarDB cluster is revoked, the PolarDB cluster becomes unavailable if you restart the PolarDB cluster.
You must use an Alibaba Cloud account or an account that has the AliyunSTSAssumeRoleAccess permission.
How do I manage custom keys for TDE?
By default, keys are built-in and managed by KMS. You can also use custom keys, which also can be managed in KMS. For more information, see Configure TDE for a PolarDB cluster.
How do I configure a SQL firewall?
PolarDB PolarProxy provides the SQL firewall feature, which can identify SQL statements to be allowed and blocked after you configure blacklist and whitelist rules. For more information, see Configure a blacklist rule.
Can data be encrypted if TDE is enabled?
To encrypt or decrypt tables after you enable TDE, you must log on to the database and execute the relevant DDL statements. The following table lists the DDL statements that are executed to encrypt and decrypt tables in the PolarDB for MySQL cluster of different MySQL versions. For more information, see Configure TDE for a PolarDB cluster.