If you add a website to Web Application Firewall (WAF) in CNAME record mode and the
website uses HTTPS to transmit data, you can customize TLS version settings and cipher
suites for the domain name of the website. This way, WAF can block requests that use
the TLS versions and cipher suites that are not within the specified ranges. This
topic describes how to configure custom TLS settings and cipher suites.
Prerequisites
- A website is added to WAF in CNAME record mode. For more information, see Add a domain name.
- The website uses HTTPS to transmit data, and the required HTTPS certificate is uploaded.
For more information, see Upload an HTTPS certificate.
Procedure
- Log on to the WAF console. In the top navigation bar, select the resource group and the region to which your
WAF instance belongs. The region can be Chinese Mainland or Outside Chinese Mainland.
- In the left-side navigation pane, choose .
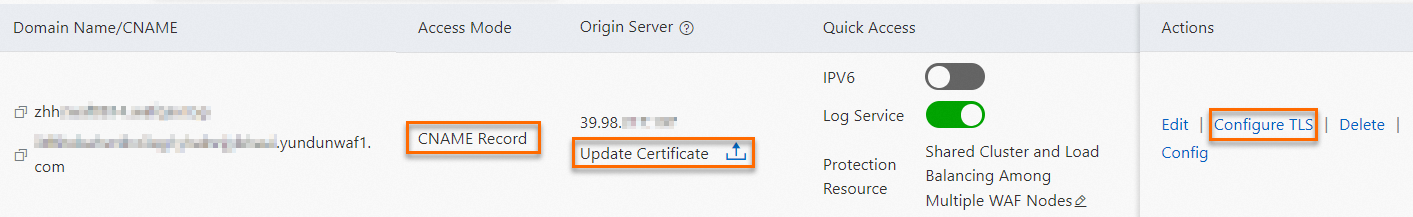
- On the Domain Names tab, find the domain name for which you want to configure custom TLS settings. Then,
click Configure TLS in the Actions column. Make sure that the Access Mode for the domain name is CNAME Record and Update Certificate is displayed in the Origin Server column.
Important You can configure TLS settings only for the domain names that use HTTPS to transmit
data. Configure TLS appears in the Actions column only if a domain name uses HTTPS and an SSL certificate is uploaded for the
domain name.
- On the Configure TLS Security Policy page, configure the TLS version settings and cipher suites, and click Save.
| Parameter |
Description |
| Domain Name |
The domain name for which you want to configure TLS settings. This value is automatically
filled. You do not need to enter the domain name.
|
| TLS Versions |
The TLS version that is used by the website. Valid values:
- Support TLS 1.0 and Later (High Compatibility and Low Security): WAF supports TLS 1.0 and later for your website.
- Support TLS 1.1 and Later (Moderate Compatibility and Moderate Security): WAF supports TLS 1.1 and later for your website. If an access request of the website
uses TLS 1.0, the request fails.
- Support TLS 1.2 and Later (Moderate Compatibility and High Security): WAF supports TLS 1.2 and later for your website. If an access request of the website
uses TLS 1.0 or 1.1, the request fails.
|
| Support TLS 1.3 |
You can also select Support TLS 1.3. |
| Cipher Suite |
The cipher suite template that you want to use. Valid values:
- All Cipher Suites (High Compatibility and Low Security): The following cipher suites are supported:
- Strong cipher suites:
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- Weak cipher suites:
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_CBC_SHA
- SSL_RSA_WITH_3DES_EDE_CBC_SHA
- Custom Cipher Suite (Select It Based on Protocol Version. Proceed with Caution.)
|
