The parameter store feature is used to dynamically maintain encrypted data through encryption parameters. You can use this feature to access encrypted data at a specific time. When you set the parameters, the parameters are stored and displayed in the encrypted format. In some scenarios, an Alibaba Cloud account includes several RAM users. However, some encrypted data cannot be accessed by all RAM users. To address this issue, a solution is provided. This topic describes how to grant a RAM user permissions on the access to different encryption parameters.
Procedure
Create encryption parameters.
Log on to the CloudOps Orchestration Service (OOS) console.
Create encryption parameters. For more information, see Manage encryption parameters.
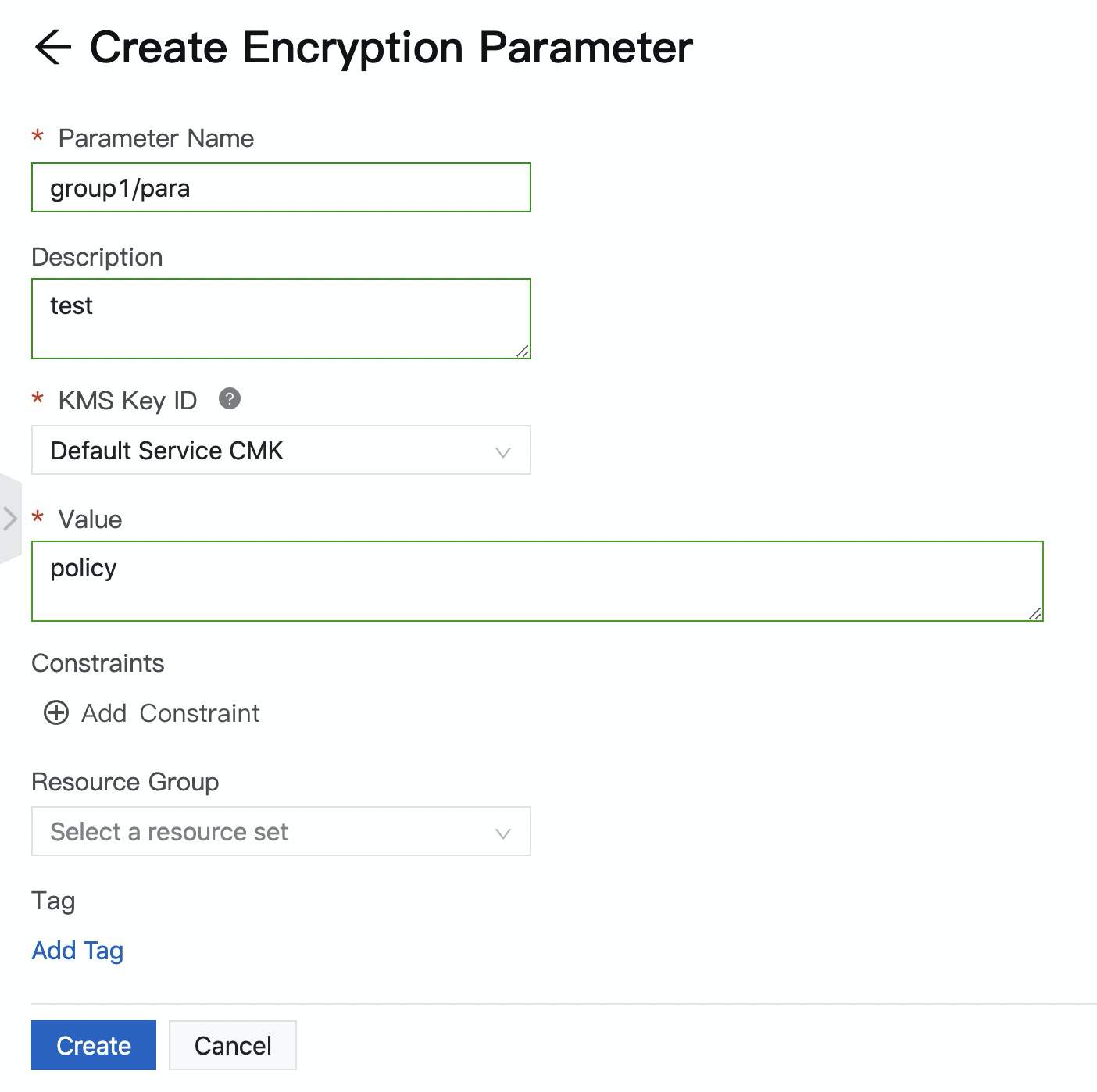
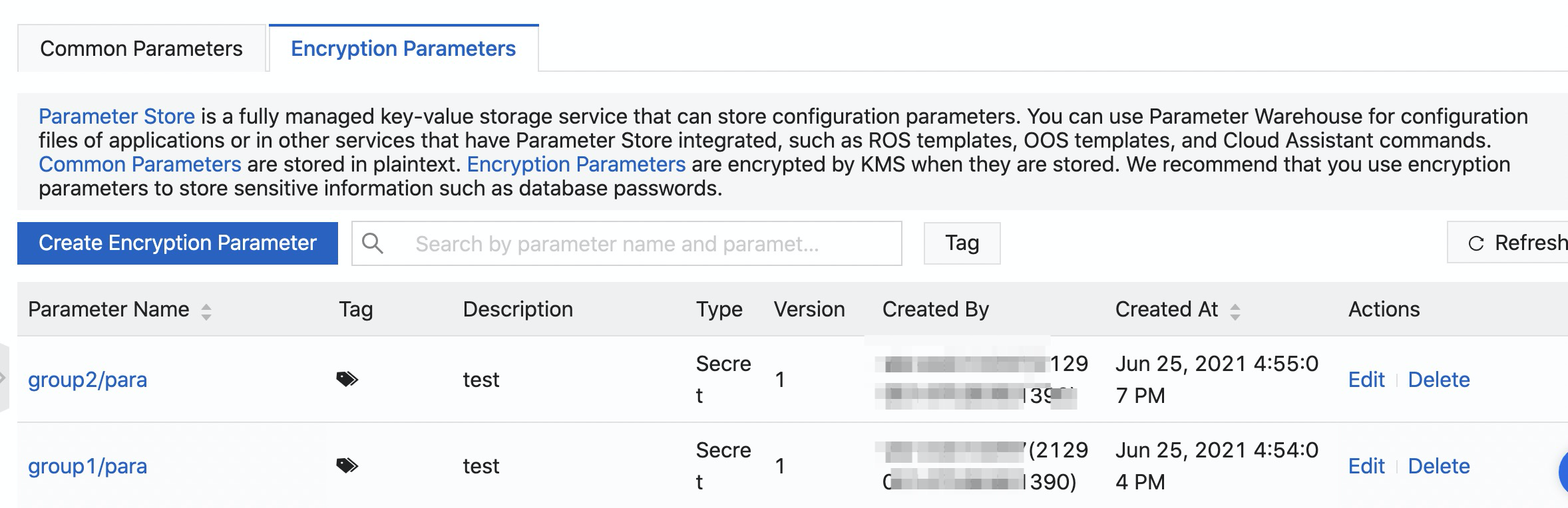
Create the group1/parameter and group2/parameter encryption parameters that are shown in the following figure.
Log on to the RAM console and configure a custom policy. For more information, see the "Create a custom policy on the JSON tab" section in Create a custom policy. Copy the following sample code to the required field. The following sample code is used to allow a RAM user to access the details about the encryption parameters that only start with group1 and query the list of all encryption parameters. You can also grant a RAM user permissions to query the values of all encryption parameters. For more information, see Appendix 1: Policy.
ImportantYou must specify Key Management Service (KMS) permissions for encryption parameters.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "oos:GetSecretParameter", "oos:ListSecretParameters", "kms:GetSecretValue" ], "Resource": [ "acs:oos:*:1234************:secretparameter/group1/*", "acs:kms:*:1234************:secret/oos/group1/*" ], "Condition": {} } ] }Attach the preceding custom policy to a RAM user. For more information about how to attach a custom policy to a RAM user or a RAM role, see Grant permissions to a RAM user or Grant permissions to a RAM role.
After you configure the policy, check whether you can query the details about encryption parameters.
In the preceding sample code, replace the original AccessKey pair with the AccessKey pair of the RAM user. When you use Alibaba Cloud CLI to query the details about the group1/parameter encryption parameter, the request succeeds. For more information, see CLI Reference.
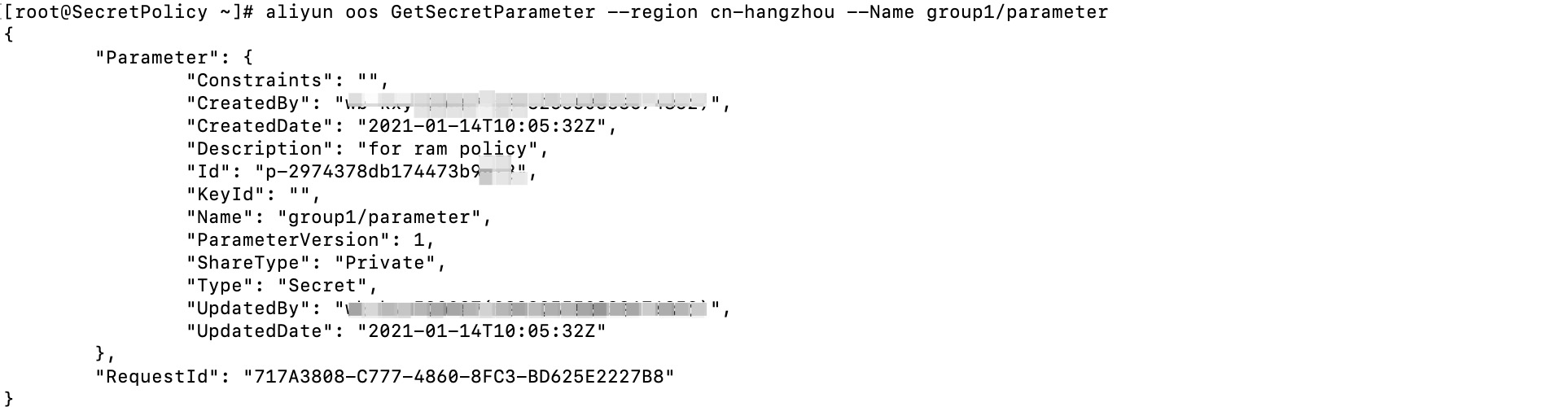
However, when you use Alibaba Cloud CLI to query the details of the group2/parameter encryption parameter, the request fails. An error, which indicates that the RAM user has no permissions, is returned. The following figure shows the details.

You first configure a policy that is used to allow access to encryption parameters that only start with group1 and attach the policy to a RAM user. Then, you obtain the preceding results: 1. Only an encryption parameter that starts with group1 can be accessed by the specified RAM user. 2. However, when the RAM user accesses the group2/parameter encryption parameter, the request fails. In addition, an error, which indicates that the RAM user has no permissions, is returned.
Appendix 1: Policy
The following policy can be used to allow a RAM user to access all encryption parameters:
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"oos:GetSecretParameter",
"oos:ListSecretParameters",
"kms:GetSecretValue"
],
"Resource": [
"acs:oos:*:1234************:secretparameter/*",
"acs:kms:*:1234************:secret/oos/*"
],
"Condition": {}
}
]
}