By Qianyue
In this article, we will explore Realm in detail, a new feature related to confidential computing in ARMv9.
Note: This article contains partial quotes and personal annotations from Introducing the Confidential Compute Architecture. All images used in this article are credited to anandtech.com
Over the last few years, we've seen security, and security breaches of hardware be at the forefront of the news, with many vulnerabilities such as Spectre, Meltdown, and all of their sibling side-channel attacks showcasing that there's a fundamental need for a re-think of how to approach security.
One way Arm wants to address this overarching issue is to re-architect how secure applications work with the introduction of the Arm Confidential Compute Architecture (CCA).
Based on Armv9 Realm Management Extension (RME, or Realm), Arm CCA isolates sensitive applications and OS in Realm; Realm is more versatile than confidential virtual machines and supports onfidential virtual machine forms and confidential OS forms.
The Arm CCA isolates sensitive applications and OS in Realm based on the Armv9 RME:
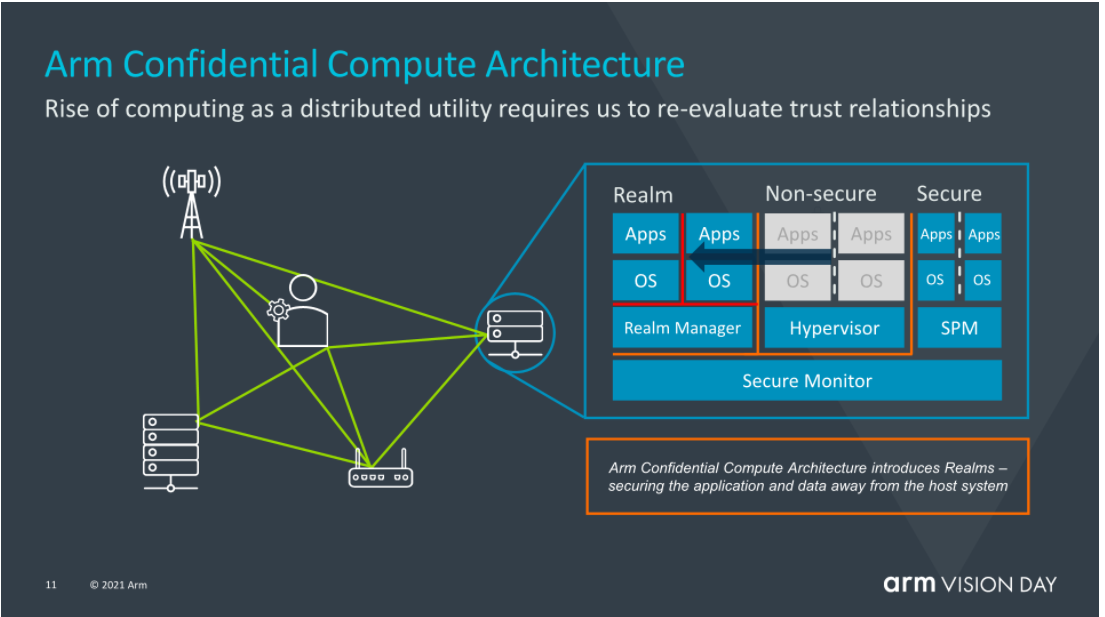
From the image above, we can summarize the following points:
Point 1: Non-Secure World, Secure World, and Realm are isolated.
How this isolation is implemented is not explained in the existing materials. The probable solution is hardware-based address space isolation technology.
The isolation of Realm depends on two aspects: Sensitive applications running in Realm may be malicious applications deployed by tenants. Therefore, the isolation of the Realm is necessary, which is two-way isolation.
Point 2: Realm can run OS (Realm OS for short), which means that Realm provides high-privilege support and can run EL1 privileged software.
Realm OS has many forms:
It is not necessarily a Linux kernel that has been tailored and security-hardened. It can be a TEE OS designed for Realm or an OS technology that supports other confidential computing to evolve to an additional Realm-supported LibOS (such as Enarx, Occlum, Graphene). But this TEE OS is unable to support TrustZone. This topic will be discussed later.
One of the current development trends of TEE OS is to reduce TCB and the potential attack surface of Rich OS to improve the overall security. However, differences remain on whether to provide good business logic compatibility.
One solution is to put security first without consideration of compatibility with business. The performance and compatibility will be moderately sacrificed.
Another solution still emphasizes compatibility with existing businesses and puts compatibility first, which requires a moderate sacrifice of performance and security.
PS: Unikernel has another chance!
Point 3: EL2 runs Realm Manager which is responsible for Realm scheduling and resource allocation. This will be supported by Arm CCA firmware architecture (similar to ATF, or directly extended to support in ATF).
Judging from the current data: Realm Manager is newly written by Arm, and the quantity of code is about one-tenth of the size of Hypervisor.
Realm Manager is similar to the SEAM Module in TDX. Realm Manager provides a new operating mode for this functional module at the processor architecture level. At the same time, the functional module assumes the features of Realm lifecycle and resource management, and other untrusted components in the system are unable to replace its functions and roles.
Point 4: TrustZone is untrustworthy to Realm. In other words, Realm does not solve the problem of computing resource isolation like TrustZone. It further solves the problem of sensitive data isolation.
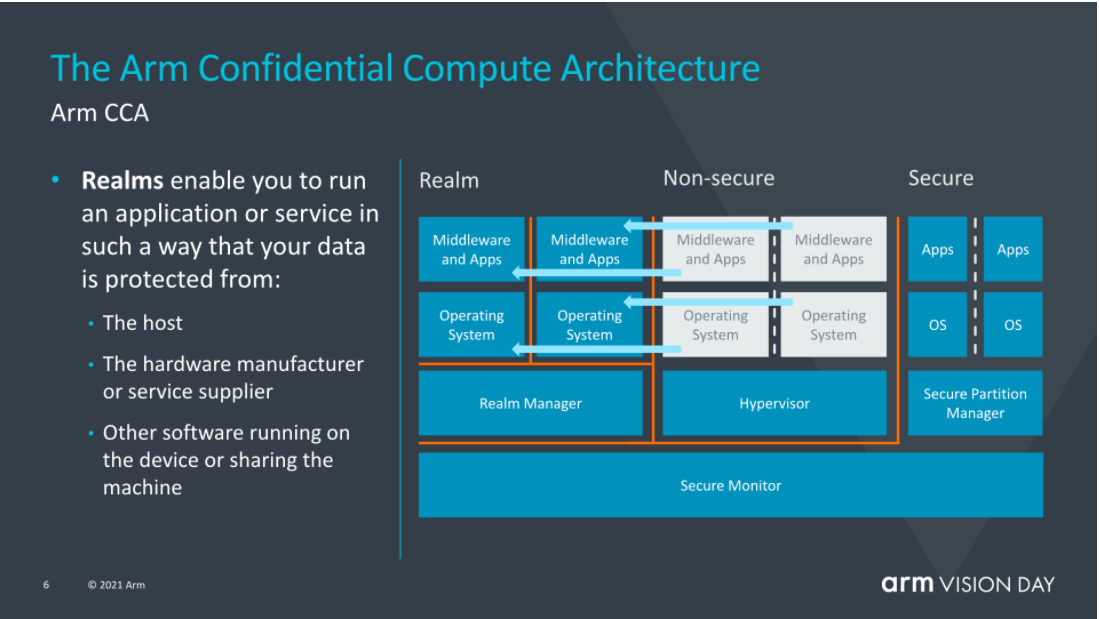
The figure explains Realm's security threat model. It can be seen that the model has the characteristics of typical confidential computing technology.
From this image, we can conclude that:
• The hardware manufacturer refers to the peripheral hardware device provider, not the hardware provider of the processor itself (such as the Arm or SoC manufacturer).
• Realm Manager is not part of Realm, but it is part of user TCB.
With the ability to run the complete OS, Realm seems to be comparable to the trust domain on TDX and confidential virtual machine on SEV/CSV, but the following usage reveals a more universal aspect of Realm than the confidential virtual machine.
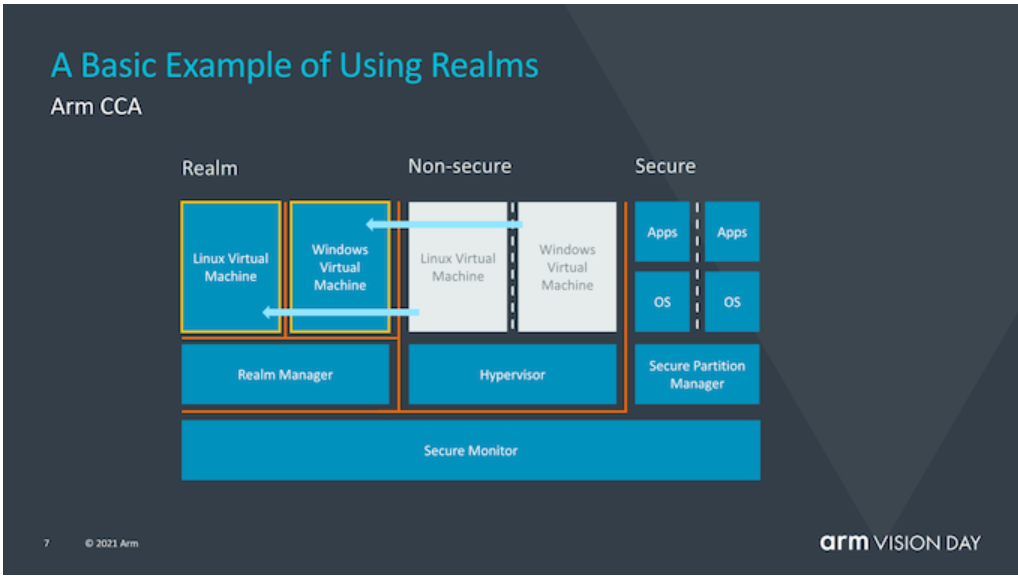
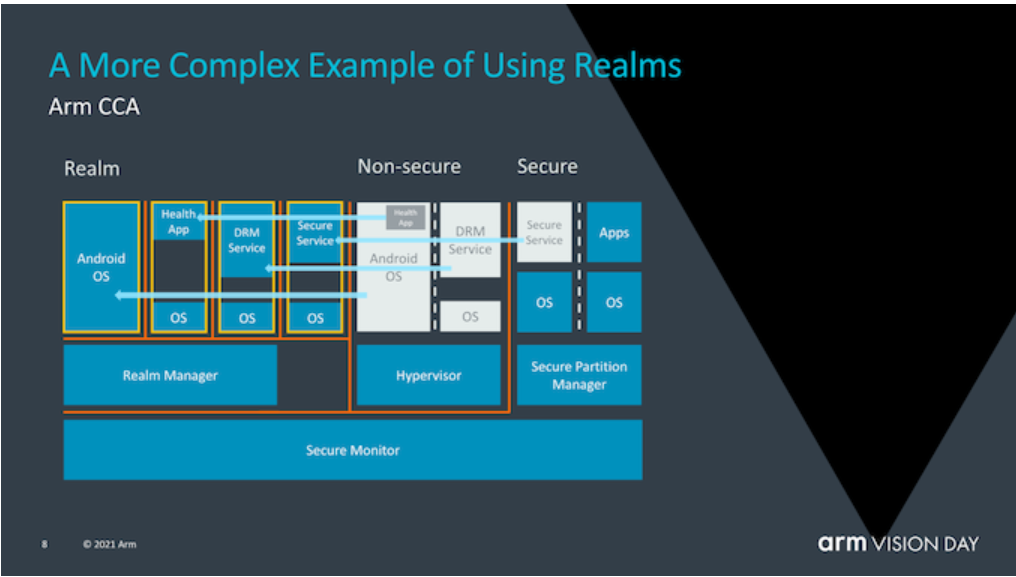
We can summarize the following points from the illustration above:
• The TEE OS in TrustZone is not a universal OS but is deeply customized in combination with TrustZone. It is impossible to directly load the TEE OS into Realm and run it. This breaks the original assumption that Realm will iterate based on the TrustZone architecture. However, TA adapted to the OP-TEE can run in Realm as long as Realm OS can support the OP-TEE TA API. In other words, this picture implies that Arm will provide support for TA in Realm OS, or it may only show Realm's compatibility. In addition, what has been mentioned above may take place in running Android applications in Realm.
• Realm Manager essentially acts as a Hypervisor-like management VM, but its object is Realm. When Realm runs VM, it can be considered that the logic related to Realm security in the hypervisor is moved to Realm Manager, while the parts not related to its security are kept in the traditional Hypervisor.
• Realm is only a hardware TEE especially for running sensitive applications. Users can load workload in their working environment and sensitive applications plus OS together into Realm through Realm Manager, or even load a complete virtual machine into Realm. Realm is not a confidential virtual machine, but a versatile and universal confidential computing running environment.
In a word, Realm technology reduces the trust requirements of sensitive applications and the cost of users adapting to Realm. And the security issues of OS will become transparent to Realm applications (but the services provided by Realm applications and the security of interfaces exposed by Realm OS still need to be paid attention to). In addition, critical applications can safely run in any CCA-enabled system, and today's enterprises often need special equipment with various security-compliant authorized software stacks to achieve this security. Therefore, this technology also reduces the investment of users in security.
Applications in Realm can attest Realm Manager to ensure its trustiness.
Memory Encryption. It is an essential capability for confidential computing.
Current data does not show how the universal operating capability provided by Realm supports the interaction between Realm and IO devices. The Confidential IO issue has not been solved in Realm 1.0 and may be solved in the next generation.
At present, Arm only provided a high level explanation of how CCA works, and more details on how the mechanism works will be released later this summer.
Attached Translation: Introducing the Confidential Compute Architecture https://www.anandtech.com/show/16584/arm-announces-armv9-architecture/2

96 posts | 6 followers
FollowAmuthan Nallathambi - May 12, 2024
Amuthan Nallathambi - August 24, 2023
Alibaba Cloud Indonesia - December 14, 2022
Alibaba Clouder - September 25, 2018
OpenAnolis - June 9, 2022
OpenAnolis - March 7, 2022

96 posts | 6 followers
Follow CloudOps Orchestration Service
CloudOps Orchestration Service
CloudOps Orchestration Service is an automated operations and maintenance (O&M) service provided by Alibaba Cloud.
Learn More ChatAPP
ChatAPP
Reach global users more accurately and efficiently via IM Channel
Learn More Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn More Elastic High Performance Computing Solution
Elastic High Performance Computing Solution
High Performance Computing (HPC) and AI technology helps scientific research institutions to perform viral gene sequencing, conduct new drug research and development, and shorten the research and development cycle.
Learn MoreMore Posts by OpenAnolis