By Jia Zhang, from Alibaba Cloud, owner of Confidential Computing for Cloud Native SIG in the OpenAnolis community.
Inclavare, pronounced as [ˈinklɑveə], is the Latin etymology of the word enclave, which means to isolate the user's sensitive workload from the untrusted and uncontrollable infrastructure in order to meet the protection requirement for the data in use.
Inclavare Containers is an open-source container runtime technology stack for confidential computing scenarios. Inclavare Containers, developed by Alibaba Cloud and Ant Group and cooperated with Intel, is the industry's first open source container runtime for confidential computing. Inclavare Containers significantly reduces the user's threshold for use. A variety of different enclave forms are available, providing more choices and flexibility between safety and cost for end users.
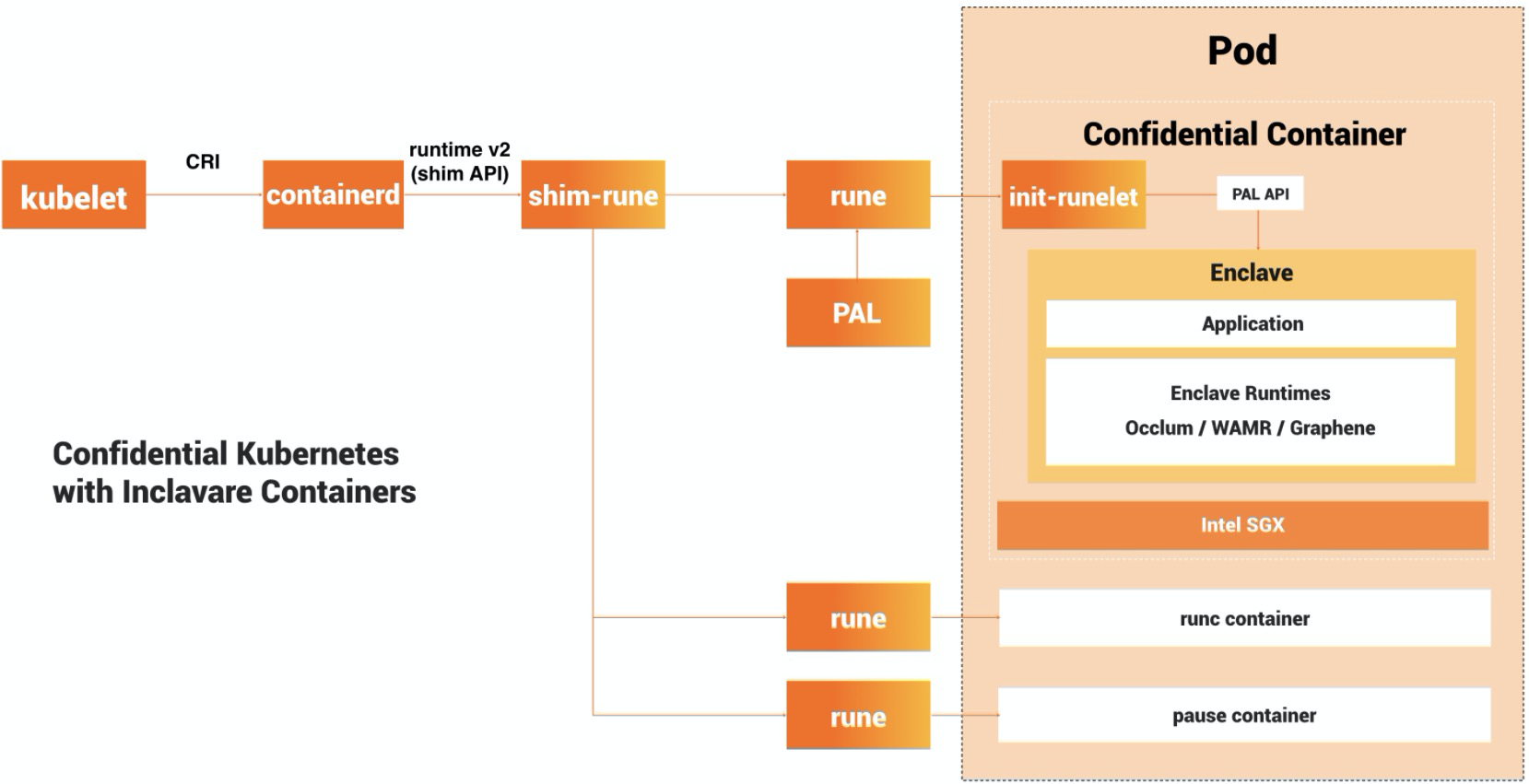
The major components of Inclavare Containers are:
rune is a CLI tool for spawning and running enclaves in containers according to the OCI specification. rune is already written into OCI Runtime implementation list.
shim-rune resides in between containerd and rune, conducting enclave signing and management beyond the normal shim basis. In particular shim-rune and rune can compose a basic enclave containerization stack for confidential computing, providing low barrier to the use of confidential computing and the same experience as ordinary container. Please refer to this doc for the details.
The backend of rune is a component called enclave runtime, which is responsible for loading and running trusted and protected applications inside enclaves. The interface between rune and enclave runtime is Enclave Runtime PAL API, which allows invoking enclave runtime through well-defined functions. The softwares for confidential computing may benefit from this interface to interact with cloud-native ecosystem.
One typical class of enclave runtime implementations is based on Library OSes. Currently, the recommended enclave runtime interacting with rune are occlum and graphene.
Occlum is a memory-safe, multi-process Library OS for Intel SGX. Graphene is an open-source library OS based on Intel SGX (Software Guard Extensions) that can run unmodified programs.
And another typical class of enclave runtime is WebAssembly Micro Runtime (WAMR) with Intel SGX, a standalone WebAssembly (WASM) runtime with a small footprint, including a VM core, an application framework and a dynamic management for WASM applications.
In addition, you can write your own enclave runtime with any programming language and SDK (e.g, Intel SGX SDK) you prefer as long as it implements Enclave Runtime PAL API.
Inclavare Containers is intended to provide a containerized technology base for confidential computing. It focuses on open-source, community, standards, and ecology. Currently, it is open-source on GitHub. Inclavare Containers currently supports the confidential computing technology, Intel SGX.
More tenant businesses, especially enterprise loads, need to use the elastic resources provided by cloud computing for massive data processing. Those tenants require a Cloud Service Provider (CSP) to provide a better security and isolation solution. In particular, during the processing of tenant's confidential data in the computing phase, the confidential data cannot be exposed in the memory in plaintext. At the same time, the security of the tenants' running environment cannot depend on CSP. This data privacy issue worries enterprise users that plan to migrate to the cloud. It requires engineering technology to solve it, such as confidential computing.
The three key functions in confidential computing are listed below:
The key functions above are implemented with Intel SGX technology. Intel SGX provides stronger privacy data protection than pure memory encryption technology. It provides minimal, application-level granularity TCB and strong security isolation based on cryptography. However, the strong security features also come with many compatibility and performance issues. As a result, Inclavare Containers integrated container ecology, library OS, and language runtime to make it more user-friendly and introduce the Intel SGX Enclave into cloud-native scenarios.
ACK-Trusted Execution Environment (ACK-TEE) is a trusted computing container platform built by the Alibaba Cloud Container Team, Operating System Security Team, Ant Security Team, Alibaba Cloud Security Team, and Compiler Team. It aims to provide a trusted execution environment (TEE) based on Intel SGX hardware encryption technology for cloud users with strong security demands on digital assets (algorithms, data, and code). ACK-TEE also aims to lower the application threshold of confidential computing technology and simplify the development, delivery, and management costs of trusted/confidential applications. At the same time, ACK-TEE is committed to building a cloud-native universal base of confidential computing for trusted businesses, applications, cloud migration for two-party products.
ACK Encrypted Computing Managed Cluster (ACK-TEE 1.0) launched in January 2020. It supports trusted applications developed based on the SGX SDK, Occlum and Graphene-SGX and supports EPC memory scheduling.
Data security protection is becoming increasingly important, which brings potential and opportunities to the entire data security market, specifically in the confidential computing field. Gartner included confidential computing in the Innovation Trigger phase for the first time in the computing infrastructure technology maturity curve in 2019. This also indicated that confidential computing is also an emerging field in the world.
Confidential computing is concerned with the interests of tenants. CSPs are aware of this and are developing technologies and products for this purpose. However, this cannot be achieved overnight. Therefore, the Enclave form, which is not confidential computing-oriented, began to appear. In this regard, CSP should support different hardware security capabilities and Enclave forms horizontally. This way, it can achieve all-around technical solutions, including confidential and non-confidential computing, and provide more options to cover the widest range of user groups with data security protection needs during computing. This is Inclavare Containers' mission.
Let's take a look at the tenants' attitude in confidential computing scenarios: they want to use the cloud computing capabilities provided by CSP while not trusting CSP. This is a seemingly contradictory demand, but it has great win-win potential. CSP should take it as an excellent opportunity to push themselves to think from the customer's perspective. We to create a rosy future for confidential computing with data security and Inclavare Containers.
"Confidential Computing" for Everyone: Getting Started with Occlum and Its Related Technologies

96 posts | 6 followers
FollowOpenAnolis - June 9, 2022
Alibaba Clouder - October 10, 2020
Alibaba Container Service - February 24, 2021
OpenAnolis - June 30, 2022
OpenAnolis - July 8, 2022
Alibaba Cloud Community - June 10, 2022

96 posts | 6 followers
Follow ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More Managed Service for Prometheus
Managed Service for Prometheus
Multi-source metrics are aggregated to monitor the status of your business and services in real time.
Learn More Container Registry
Container Registry
A secure image hosting platform providing containerized image lifecycle management
Learn MoreMore Posts by OpenAnolis