By Yong Yang
To make our tool more universal and to review how to customize a Spring Boot starter, we will make this tool a starter. This will allow it to be directly referenced in future Spring Boot projects.
First, we create a Spring Boot project and import the spring-boot-starter-web dependency.
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
<scope>provided</scope>
<version>2.4.3</version>
</dependency>• 1.Because our tool is developed for web projects and will definitely be used in a web environment in the future, we set scope to provided when importing the dependency.
After adding the dependency, let's define an encryption tool class for future use. There are several encryption options, including symmetric encryption (with algorithms such as AES, DES, and 3DES) and asymmetric encryption. In this case, we will use keys from Alibaba Cloud KMS for encryption.
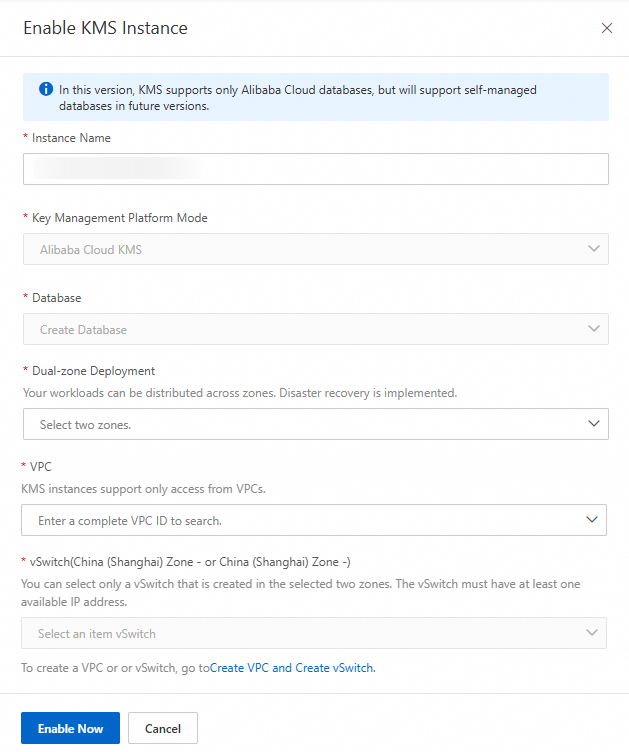
KMS adopts a dual-zone architecture to further enhance stability. You need to select the two zones where your business will be deployed and your Alibaba Cloud VPC in the Enable KMS Instance panel, and then click OK.
You need to create a key that uses the AES algorithm. This key supports rotation and will be updated according to a custom rotation cycle to further enhance its security. Compared with the open source encryption keys provided by Spring Boot, this key offers improved security. Since keys are used for security purposes, they must be kept secure.
<dependency>
<groupId>com.aliyun</groupId>
<artifactId>alibabacloud-dkms-gcs-sdk</artifactId>
<version>0.5.2</version>
</dependency>package aesUtils;
import com.aliyun.dkms.gcs.openapi.models.Config;
import com.aliyun.dkms.gcs.sdk.Client;
public class InitKmsClient {
public Client InitKmsClient(String protocol,String endpoint,String clientKey,String clientKeyPass,String KmsCacert) throws Exception {
Client client = new Client(new Config().setProtocol(protocol).setEndpoint(endpoint).setCaFilePath(clientKey).setClientKeyFile(clientKey).setPassword(clientKeyPass));
return client;
}
}package aesUtils;
import com.aliyun.dkms.gcs.sdk.Client;
import com.aliyun.dkms.gcs.sdk.models.*;
import java.nio.charset.StandardCharsets;
public class KmsAesEncUtils {
// Use a KMS AES key to encrypt data.
public byte[] kmsAesAdvEncrypt(Client kmsClient,String keyId,String plaintext) throws Exception{
AdvanceEncryptRequest request = new AdvanceEncryptRequest();
request.setKeyId(keyId); // The name of the key created by KMS.
request.setPlaintext(plaintext.getBytes(StandardCharsets.UTF_8));
// Call the advanced encryption API for encryption.
// If you want to ignore the server certificate, you can use the commented-out code below to call the API.
//RuntimeOptions runtimeOptions = new RuntimeOptions();
//runtimeOptions.setIgnoreSSL(true);
//AdvanceEncryptResponse response = client.advanceEncryptWithOptions(request, runtimeOptions);
AdvanceEncryptResponse response = kmsClient.advanceEncrypt(request);
byte[] cipherbolb=response.getCiphertextBlob();
return cipherbolb;
}
// Use a KMS AES key to decrypt data.
public String kmsAesAdvDecrypt(Client kmsClient,byte[] cipherbolb) throws Exception {
AdvanceDecryptRequest request = new AdvanceDecryptRequest();
// Call the advanced decryption API for decryption.
// If you want to ignore the server certificate, you can use the commented-out code below to call the API.
//RuntimeOptions runtimeOptions = new RuntimeOptions();
//runtimeOptions.setIgnoreSSL(true);
//AdvanceDecryptResponse response = client.advanceDecryptWithOptions(request, runtimeOptions);
request.setCiphertextBlob(cipherbolb);
AdvanceDecryptResponse response = kmsClient.advanceDecrypt(request);
return new String(response.getPlaintext());
}
}You can use JitPack for publishing.
First, let's create a repository on GitHub and upload our code to it.
After the upload is successful, click the Create a new release button on the right to release an official version. You can reference the published starter as follows:
<dependencies>
<dependency>
<groupId>com.github.lenve</groupId>
<artifactId>encrypt-spring-boot-starter</artifactId>
<version>0.0.3</version>
</dependency>
</dependencies>
<repositories>
<repository>
<id>jitpack.io</id>
<url>https://jitpack.io</url>
</repository>
</repositories>This is done by creating a Spring Boot web project and importing the starter dependency.
[1] https://developer.aliyun.com/article/1436356 (in Chinese)
[2] Key Management Service > KMS Instance SDK for Java > Initialize KMS Instance SDK for Java/Use the client to call an operation
Disclaimer: The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.

1,347 posts | 477 followers
FollowAlibaba Cloud Native Community - February 20, 2025
Alibaba Clouder - December 25, 2017
Alibaba Clouder - November 17, 2020
Alibaba Cloud Indonesia - January 15, 2024
Léon Rodenburg - December 24, 2019
Alibaba Cloud Community - November 19, 2024

1,347 posts | 477 followers
Follow Cloud Hardware Security Module (HSM)
Cloud Hardware Security Module (HSM)
Industry-standard hardware security modules (HSMs) deployed on Alibaba Cloud.
Learn More Key Management Service
Key Management Service
Create, delete and manage encryption keys with Alibaba Cloud Key Management Service
Learn More Managed Security Service
Managed Security Service
Identify vulnerabilities and improve security management of Alibaba Cloud WAF and Anti-DDoS and with a fully managed security service
Learn More IDaaS
IDaaS
Make identity management a painless experience and eliminate Identity Silos
Learn MoreMore Posts by Alibaba Cloud Community