This tutorial demonstrates how to use the anti-bot features of the Alibaba Cloud Web Application Firewall (WAF) to prevent against unauthorized access to servers and websites.
The WAF provides protection against many common threats such as database injection attacks, cross-site scripting, and all of the Open Web Application Security Project (OWASP) Top 10. Because these types of attack affect every server and website, no additional configuration steps are required – the features are active as soon as the WAF is enabled. However, this also means that attacks which are unique to your servers, such as repeated attempts to access your service from a competitor's IP address range, can't be catered for.
The anti-bot features detailed in this tutorial are specific to your installation, based on the type of attacks you're receiving and where they are coming from. You can configure them from the Alibaba Cloud console, and amend them whenever you like. The anti-bot features include blocking access to a server from IP addresses which are considered a threat, and restricting access to specific URLs if multiple requests beyond a specified threshold are coming from suspicious addresses.
To learn more about the out-of-the-box features of the WAF you may find it simpler to start with the Web Application Firewall tutorial at this link . If you don't currently need the additional ability to configure your individual WAF installation to protect against bot attacks, the tutorial is particularly relevant.
Software bots which emulate a web browser are often used by criminals to harvest large amounts of data from websites. They can also abuse websites in other ways, such as by mass-posting adverts or malicious links in comment forms or forums, or by placing large numbers of reservations within, say, an airline booking system in order to prevent legitimate customers from making a booking.
In addition to the out-of-the-box features of the WAF which prevent the type of attacks that affect everyone who subscribes to the service, you can also create your own specific rules and policies to block bot attacks that you are receiving, or that you fear you may receive.
For example, you can create a rule which will block access to the password reset request page on your website if multiple attempts are made from the same IP address within a short time. Because these rules are specific to your servers, rather than being rules which apply to everyone who uses the WAF, they require some additional setup steps. This tutorial explains those steps.
To follow this tutorial you'll need an Alibaba Cloud account and you'll need to subscribe to the Web Application Firewall service.
The WAF requires a monthly subscription, and is available in three versions known as Pro, Business and Enterprise. Pricing starts at USD $299 per month, which covers one top-level domain and up to nine additional sub-domains. To follow the examples used in this tutorial you need only the Pro subscription level.
Before you start, it will help if you have already subscribed to the WAF and configured it to protect at least one top-level domain.
If you don't already have an Alibaba Cloud account then you can sign up at www.alibabacloud.com and this will also get you $300 of free credit, $250 of which can be used towards a WAF subscription. The other $50 can be used to create a server or website for the WAF to protect.
Log into your Alibaba Cloud account and head to the main console screen, which will look something like this.
From the Security section, choose Web Application Firewall.
If your existing WAF is not for the Mainland China region, then you'll see the following screen. In this case, click the region selection and change it to International in order to see your existing WAF setup.
From the WAF screen, on the left-hand side under Management, click on Website Configuration to see the details of the site that your WAF is currently protecting.
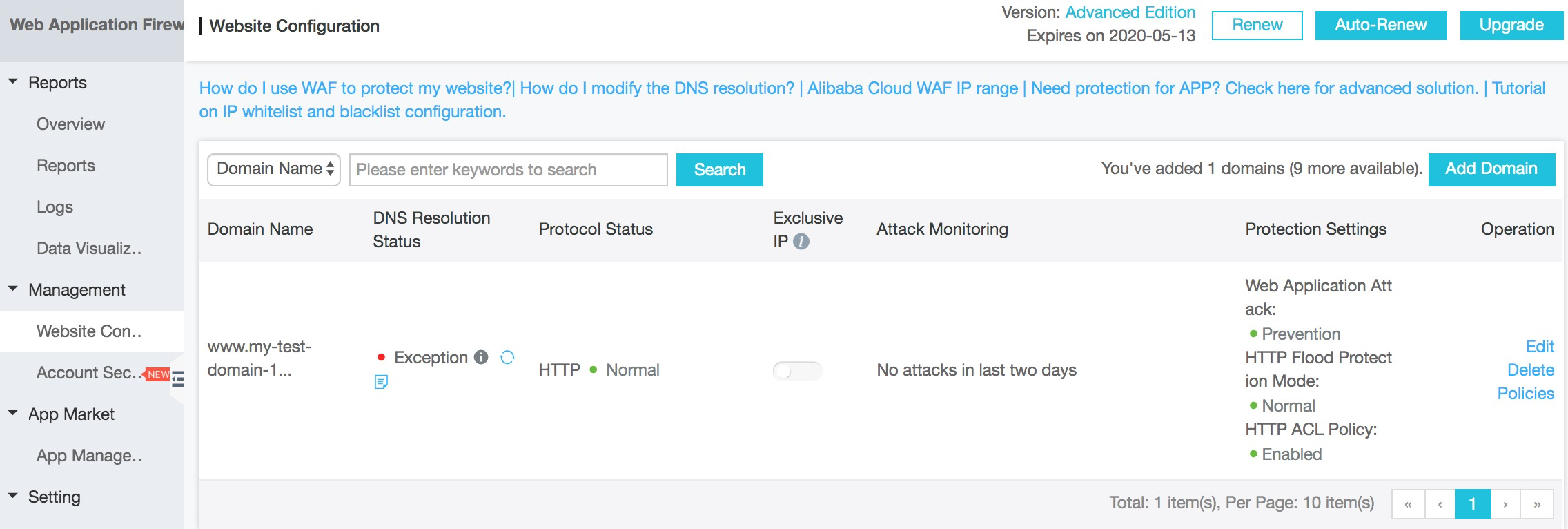
Let's look more closely at the current default settings, which are shown on the right hand side of the screen.
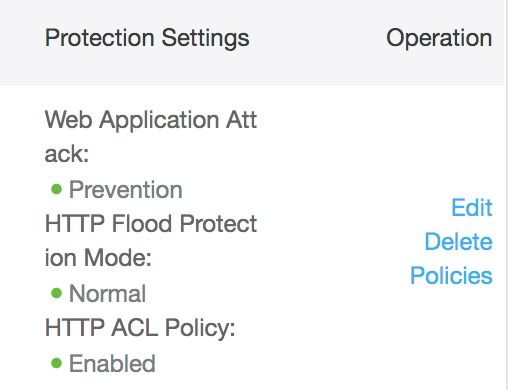
Firstly, we can see that Web Application Attack Protection is turned on. This covers attacks such as database injections, cross-site scripting, and other common attack types which constitute the well-known OWASP Top 10 list (see the Open Web Application Security Project at www.owasp.org to learn more). This feature works straight out of the box and is enabled by default, and you shouldn't change it.
We can also see that HTTP Flood Protection Mode is enabled and set to Normal. This will help to protect the server from HTTP Flood and DDoS attacks and you should leave it at the default setting.
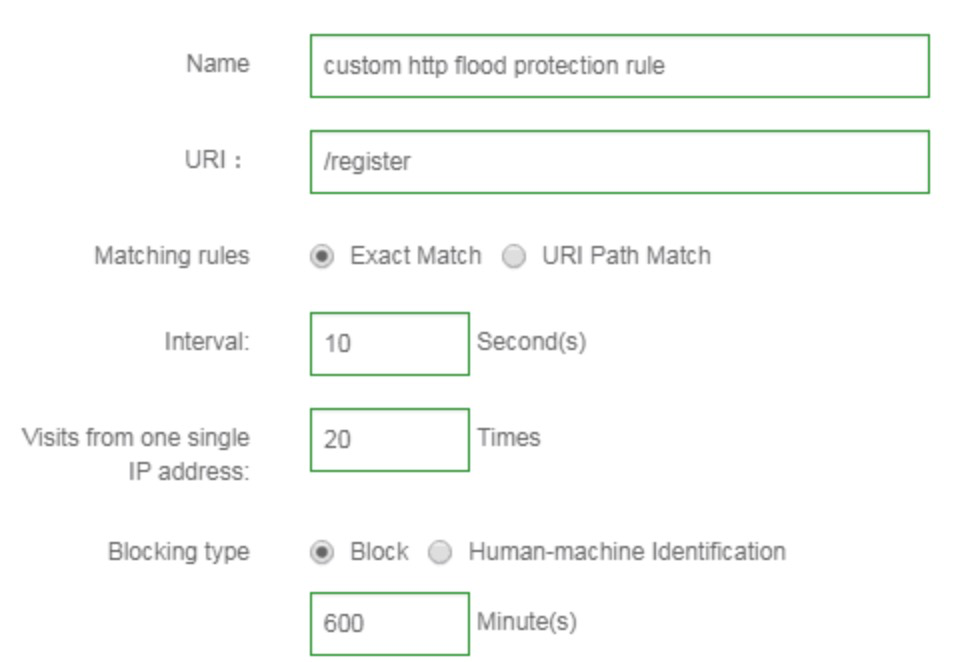
If you subscribe to the Business or Enterprise level of the WAF then you can enhance and customize the HTTP flood protection settings by creating your own additional rules. For example, you can specify that multiple attempts from an individual IP address to your user account registration page should be blocked if there are more than twenty visits within ten seconds. In the example shown below, we have specified that the IP address should be blocked for ten hours.
Click on the Policies link to view some additional WAF options that will help to keep your server safe. The screen will look like this:
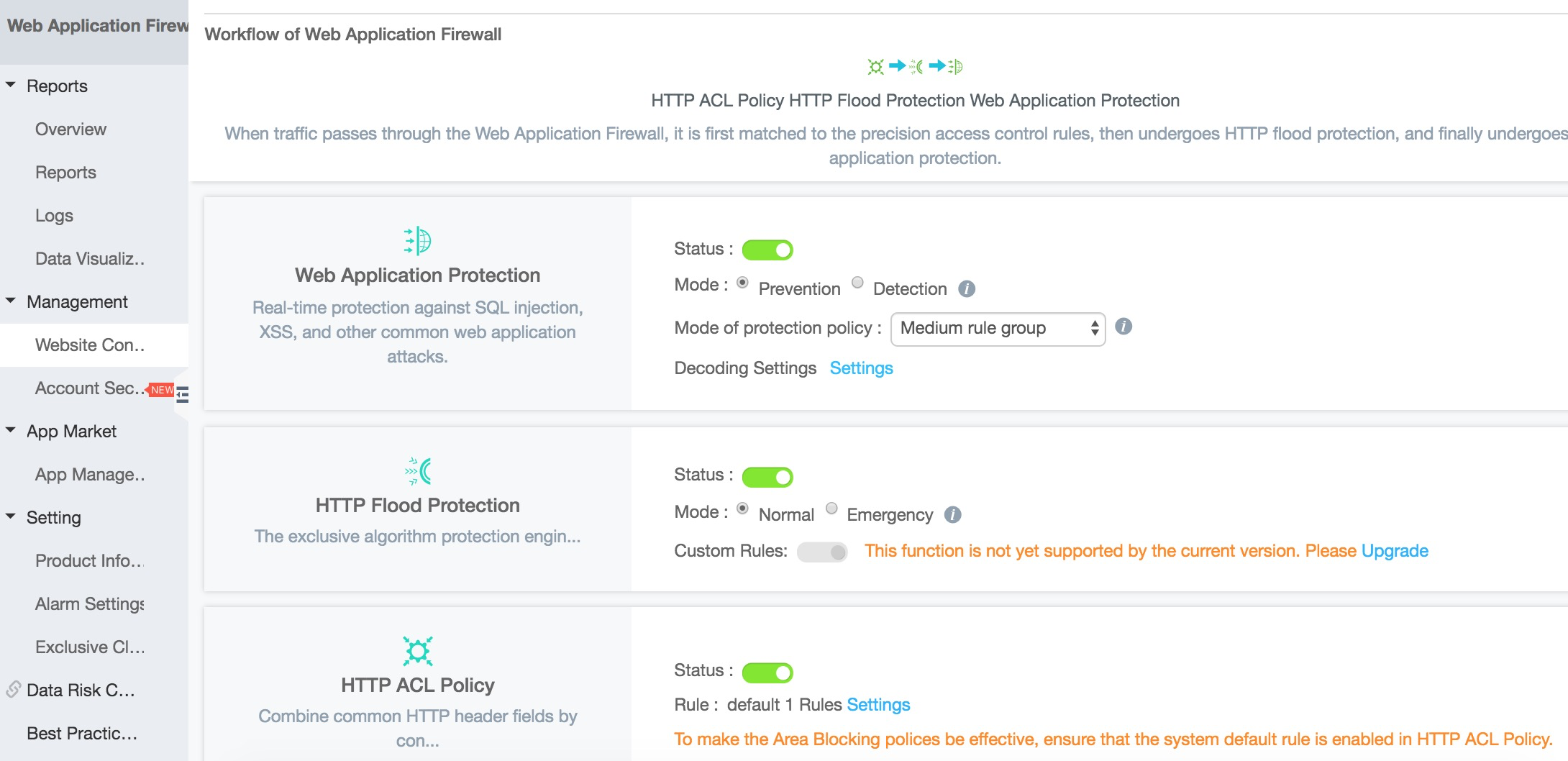
The Malicious IP Penalty feature is powered by Alibaba Cloud's huge threat intelligence database of more than 4 billion IP addresses.
The database holds details of each IP address, its location, whether it has recently been used to generate attacks, whether those attacks were man- or machine-generated, how often they occurred, and so on.
The list of malicious IP addresses is updated all the time. For example, if a attacker anywhere in the world begins running a program which automatically scans multiple servers protected by Alibaba Cloud WAF in search of one that is vulnerable to attack, his or her IP address will be added to the threat database within just a few seconds so that all servers that use the Malicious IP Penalty feature will be automatically protected from that current attack.
To turn on the Malicious IP Penalty feature just click the switch so that it turns green.
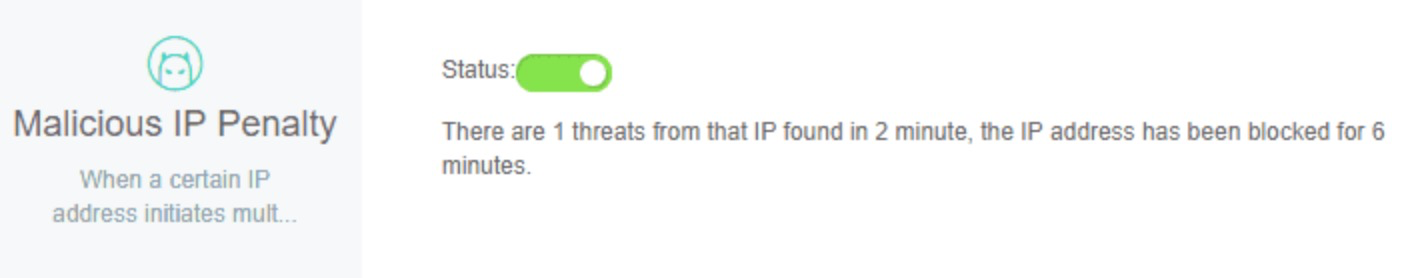
Now, if multiple connections are made from any suspicious IP address to your server, that IP address will automatically be blocked for the standard default period of six minutes.
The other useful feature for protecting your website and server from bots is the HTTP ACL, which again is available in all editions of the Web Application Firewall. To turn it on, just click its status switch so that it turns green.
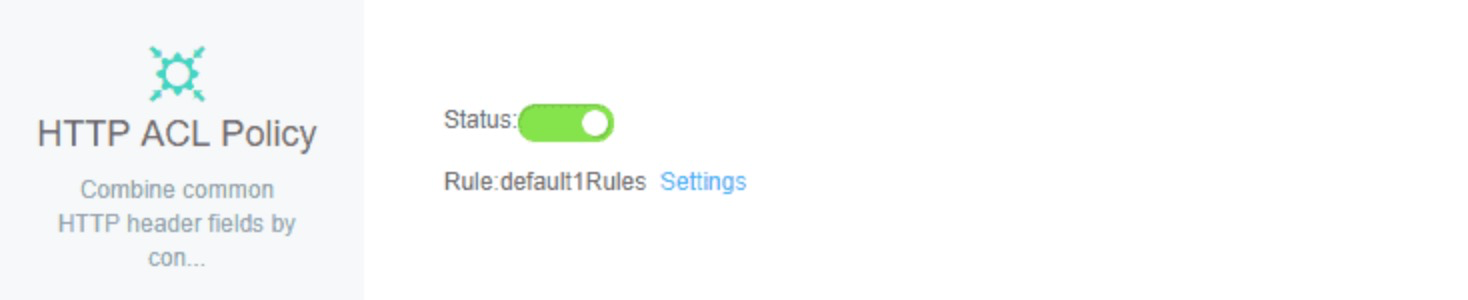
HTTP is the communications protocol that web browsers (or other user agents such as bots) use to communicate with web servers. An ACL is an Access Control List. The HTTP ACL feature allows you to set up rules which block malicious requests. By default, the HTTP ACL feature is enabled. Click on the Settings link and you'll see something like this:
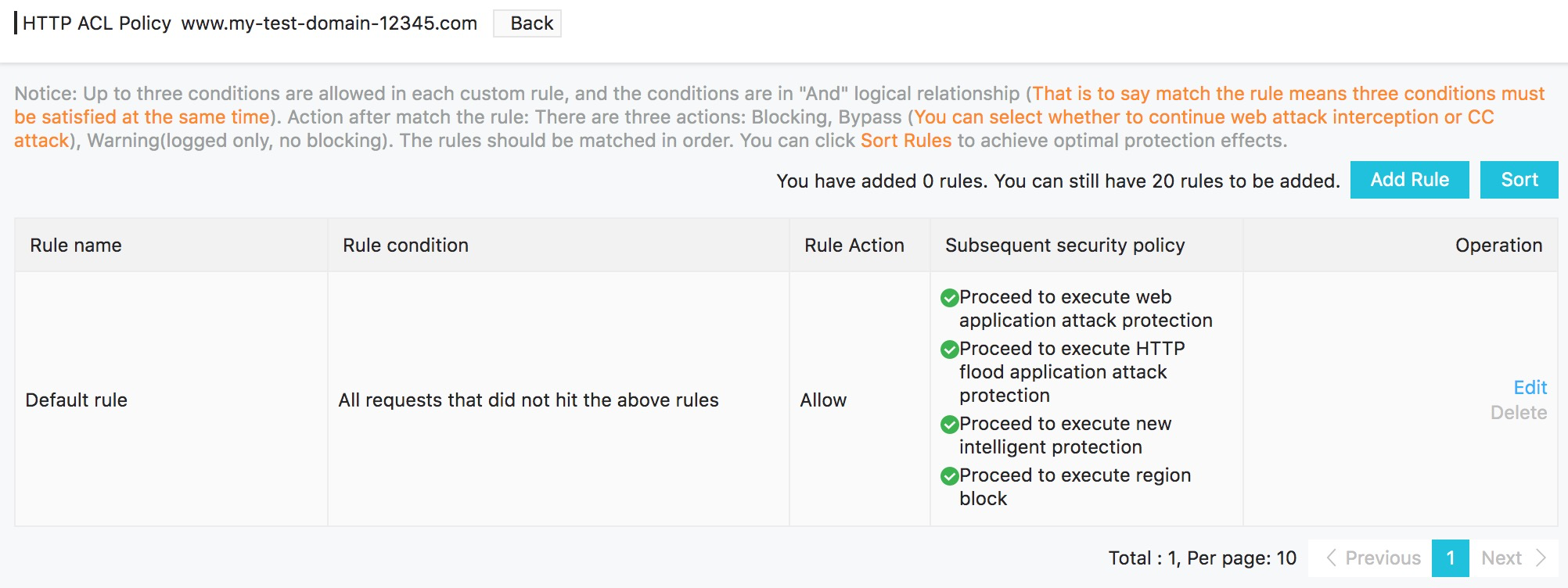
You'll see that the standard protection features mentioned earlier are enabled.
You can create your own additional custom HTTP ACL rules. In the Pro edition of the Web Application Firewall you can create up to fifty. The Business and Enterprise versions allow up to fifty and 100 respectively.
It's important to note that everything covered in this tutorial so far is an automatic feature which protects all sites and servers equally, and needs no configuration apart from being enabled.
The HTTP ACL policy lets you create more detailed rules, specific to your individual circumstances. The precise nature of the rules that you create will depend on the nature of your website or server, the URLs of the pages you want to protect, the degree of protection required, and the types of attacks that you are facing.
While such rules obviously take a little more time to set up, and may need tweaking if they subsequently turn out to be blocking some legitimate traffic too, we still recommend that you consider using this important feature of the Web Application Firewall in order to provide a true multi-layered security approach.
To add a new ACL rule, click on the Add Rule button. Assign your new rule a name, then click on the Add Rule link to start adding details. You can click on the Add Rule link to add up to 3 conditions in a rule, and the rule will be considered satisfied if all of them are true.
In this example we block access from IP address 11.22.33.44 if the target URL is change_password.php.
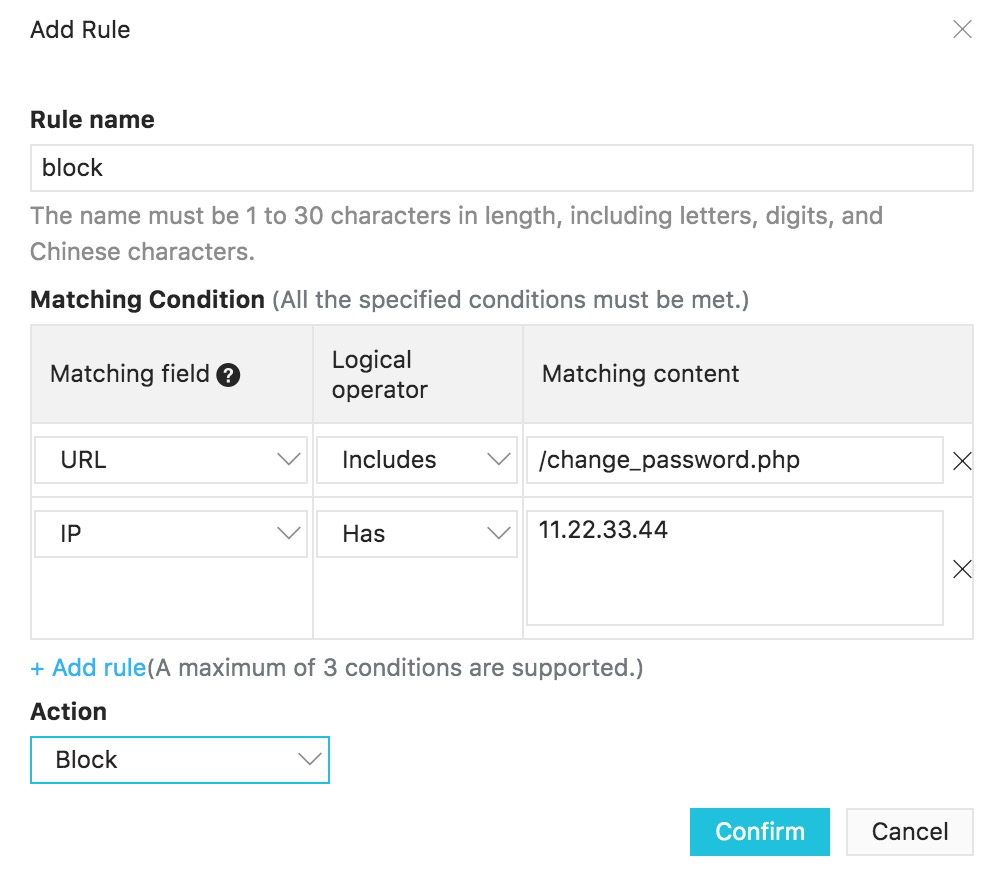
IP addresses can be single addresses, or blocks in CIDR notation. For example, 10.20.30.40/24 covers 10.20.30.1 to 10.20.30.255.
To view details about the various matching fields that you can use, hover your mouse over the "i" icon to reveal a helpful graphic, as shown below.
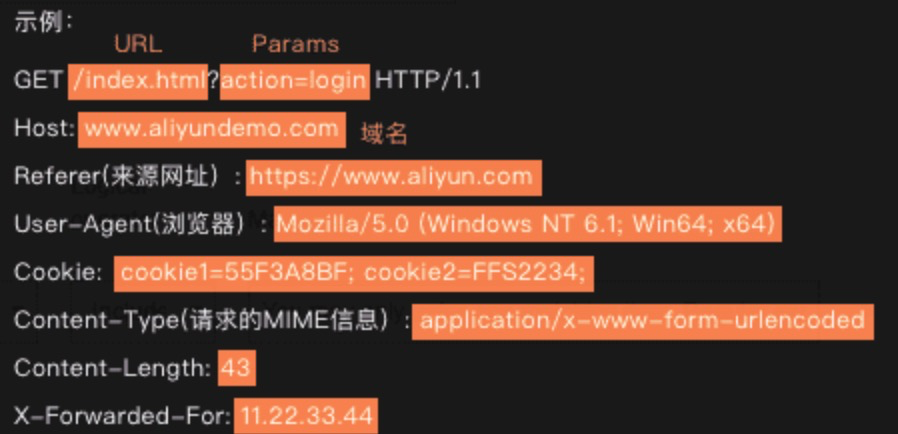
When you're matching against a URL, the general rule is that "URL" matches any text which occurs before the question mark, and "Params" (parameters) is for matching text after the question mark. So, in the example shown in the image above, attempting to match "login" by specifying it as part of the target URL will not work as it needs to be specified as a parameter.
There are three Action types, which allow you to specify what action the WAF should take if a match is found. These are block, warn or allow. "Warn" means that the access will be allowed, but will be logged. If you're not sure whether blocking a certain string will have an adverse effect on legitimate visitors to your server or site, start by logging instead of blocking, and then examine the logs to see whether the incoming traffic appears to be malicious in nature.
This is the left-hand side of the WAF screen. However, note that the log search feature is only available in the Enterprise version of the Web Application Firewall, and activity which occurred before you enabled the log feature will not have been stored and thus cannot be searched.
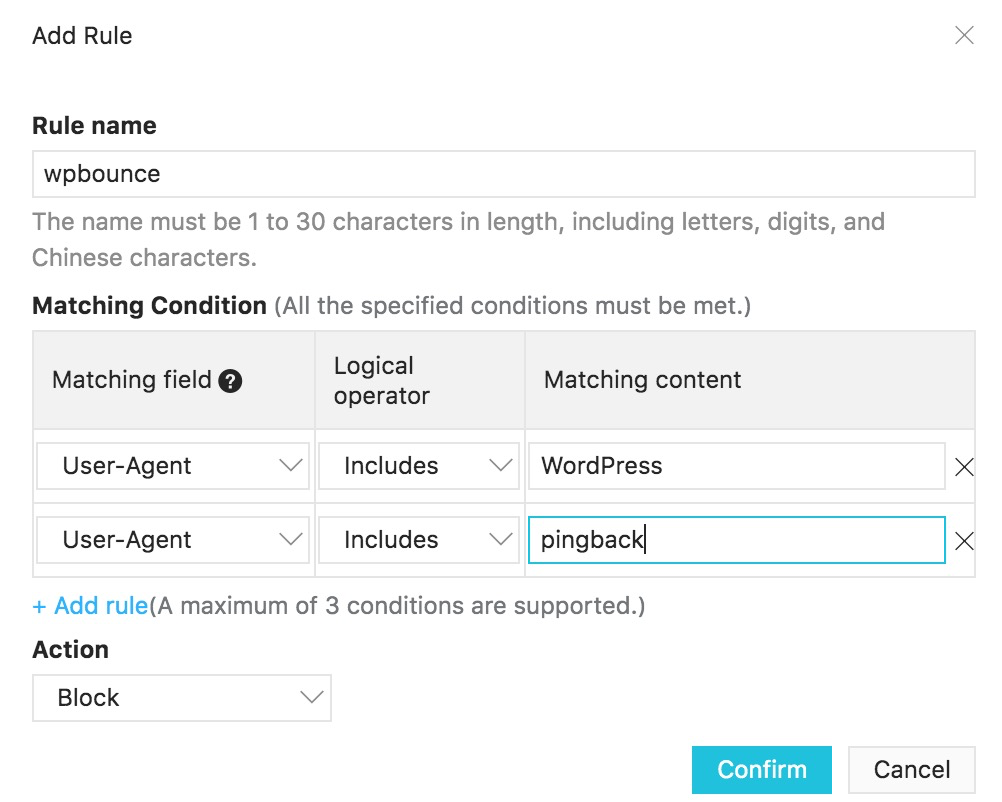
If your server is running WordPress and you use the pingback feature to allow users to be notified when someone replies to their blog comment, you are vulnerable to what's known as a pingback or bounce attack. By abusing the pingback feature, an attacker can cause a WordPress site to slow down or crash.
If you were to look in the server logs of a WordPress site suffering such an attack you'd see something like this in the list of user agents that have been accessing your site.

As you can see, all of the malicious traffic has a user agent string that contains the words "WordPress" and "pingback". We can use this to construct a simple WAF rule to protect our site from such attacks.
Images and videos on websites require a significant amount of bandwidth to host. Consequently, it is common for selfish website operators to link to graphical content on other people's sites instead of hosting the files locally on their own server. This means that, whenever someone views a page of the selfish operator's site, one or more images or videos might be loaded from elsewhere because the URL of the image points to somewhere other than the selfish operator's server.
If you discover that a particular website is leeching images or other content from your site, you can create a WAF rule to block it. For example, if you find that www.selfish-site.com is referencing images from your company's site, set up a rule as follows. The requests will then be blocked, and users of the selfish operator's site will receive an error saying that the required image can't be found.
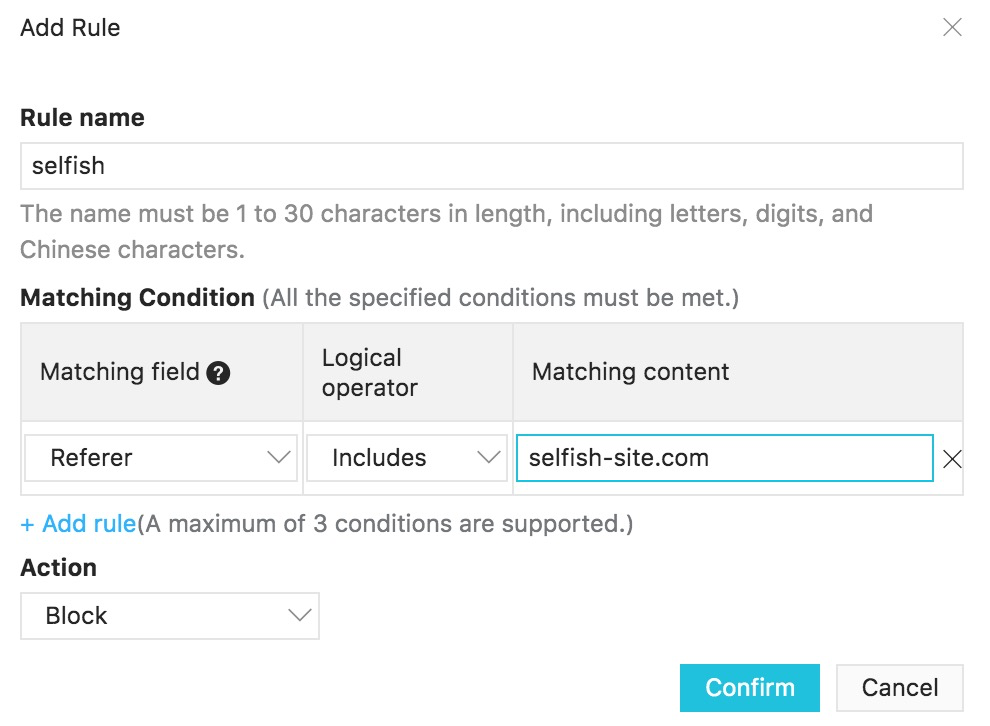
Note how we use the Referer matching field in this instance.
In this tutorial we have examined some of the anti-bot technology that's built into the Alibaba Cloud Web Application Firewall, which you can configure in order to protect a server or website from being targeted by malicious user agents or web browser software.
The Alibaba Cloud Web Application Firewall is available on a simple monthly subscription starting at $299, and can be used to protect servers hosted with Alibaba Cloud or with any other organization. All that's required is a DNS change in order to route incoming traffic via the WAF, where it is then filtered and passed on to the server that is being protected.
You can find more details at www.alibabacloud.com/product/waf
Protect Your Apps and Websites with Web Application Firewall

2,593 posts | 792 followers
FollowAlibaba Clouder - July 11, 2019
Alibaba Clouder - July 12, 2019
Alibaba Clouder - July 12, 2019
Alibaba Clouder - January 15, 2021
Alibaba Cloud Security - December 12, 2019
Alibaba Clouder - July 10, 2019

2,593 posts | 792 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More CloudMonitor
CloudMonitor
Automate performance monitoring of all your web resources and applications in real-time
Learn MoreMore Posts by Alibaba Clouder