By Hitesh Jethva, Alibaba Cloud Community Blog author. The Blog is a community-driven platform whose aim is to demonstrate Alibaba Cloud's technical capabilities, brand message, and thought leadership through relevant, compelling content.
OSSEC, which stands for Open Source HIDS SECurity, is a free and open-source host-based intrusion detection system that can be used to monitor anywhere from one to thousands of servers in a server/agent mode. It performs log analysis, rootkit detection, time-based alerting, integrity checking and active response, essentially allowing you to be able to centrally manage and multiple multiple systems from one area.
In this tutorial, you will learn how to install OSSEC server and OSSEC agent on Alibaba Cloud Elastic Compute Service (ECS) instances installed with Ubuntu 16.04.
To install the OSSEC server and agent on ECS instances, follow these steps:
First, log on to your Alibaba Cloud ECS Console and create two ECS instances with Ubuntu 16.04 as the operating system and with at least 2GB RAM. Connect to your ECS instance, and log on as the root user. After you are logged on to your ECS instances installed with Ubuntu 16.04, run the following command to update your base system with the latest available packages.
apt-get update -yBefore starting, you will need to install some dependencies required by OSSEC. You can install all of them by running the following command:
apt-get install build-essential gcc make apache2 libapache2-mod-php7.0 php7.0 php7.0-cli php7.0-common apache2-utils unzip wget sendmail-bin sendmail inotify-tools -yAfter all the packages are installed, you can proceed to the next steps.
First, you will need to download the latest version of OSSEC from Git repository. You can download it by running the following command:
wget https://github.com/ossec/ossec-hids/archive/3.1.0.tar.gzAfter the download is complete, extract the downloaded file with the following command:
tar -xvzf 3.1.0.tar.gzNext, change the directory to the ossec-hids-3.1.0:
cd ossec-hids-3.1.0Install OSSEC by running the install.sh file:
sh install.shDuring the installation, you will need to answer a few questions.
Select your language and press Enter:
(en/br/cn/de/el/es/fr/hu/it/jp/nl/pl/ru/sr/tr) [en]: enThe following output is displayed:
OSSEC HIDS v3.1.0 Installation Script - http://www.ossec.net
You are about to start the installation process of the OSSEC HIDS.
You must have a C compiler pre-installed in your system.
- System: Linux Node1 4.4.0-45-generic
- User: root
- Host: Node1
-- Press ENTER to continue or Ctrl-C to abort. --Press Enter to continue. The following output will be displayed:
1- What kind of installation do you want (server, agent, local, hybrid or help)? serverChoose server and press Enter. Then, the following output will be displayed:
- Server installation chosen.
- Installation will be made at /var/ossec .Next, choose your installation location and press Enter. The following output is displayed:
3- Configuring the OSSEC HIDS.
3.1- Do you want e-mail notification? (y/n) [y]: yPress Y and press Enter to get e-mail notification. The following output is displayed:
- What's your e-mail address? root@localhost
- We found your SMTP server as: 127.0.0.1
- Do you want to use it? (y/n) [y]: Press y and press Enter. The following output is displayed:
--- Using SMTP server: 127.0.0.1
3.2- Do you want to run the integrity check daemon? (y/n) [y]:
- Running syscheck (integrity check daemon).
3.3- Do you want to run the rootkit detection engine? (y/n) [y]: Press Enter for integrity check daemon. YThe following output is displayed:
- Running rootcheck (rootkit detection).
3.4- Active response allows you to execute a specific
command based on the events received. For example,
you can block an IP address or disable access for
a specific user.
More information at:
http://www.ossec.net/en/manual.html#active-response
- Do you want to enable active response? (y/n) [y]: Press y to enable active response. The following output is displayed:
- Active response enabled.
- By default, we can enable the host-deny and the
firewall-drop responses. The first one will add
a host to the /etc/hosts.deny and the second one
will block the host on iptables (if linux) or on
ipfilter (if Solaris, FreeBSD or NetBSD).
- They can be used to stop SSHD brute force scans,
portscans and some other forms of attacks. You can
also add them to block on snort events, for example.
- Do you want to enable the firewall-drop response? (y/n) [y]: Press y and press Enter to enable the firewall-drop response. The following output is displayed:
- firewall-drop enabled (local) for levels >= 6
- Default white list for the active response:
- 172.20.10.1
- Do you want to add more IPs to the white list? (y/n)? [n]: Press n and press enter. The following output is displayed:
3.5- Do you want to enable remote syslog (port 514 udp)? (y/n) [y]:
- Remote syslog enabled.Press Enter to enable remote syslog. The following output is displayed:
3.6- Setting the configuration to analyze the following logs:
-- /var/log/auth.log
-- /var/log/syslog
-- /var/log/dpkg.log
-- /var/log/apache2/error.log (apache log)
-- /var/log/apache2/access.log (apache log)
- If you want to monitor any other file, just change
the ossec.conf and add a new localfile entry.
Any questions about the configuration can be answered
by visiting us online at http://www.ossec.net .
--- Press ENTER to continue ---Finally, press Enter to start the installation. After the installation is complete, you will see the following output:
- System is Debian (Ubuntu or derivative).
- Init script modified to start OSSEC HIDS during boot.
- Configuration finished properly.
- To start OSSEC HIDS:
/var/ossec/bin/ossec-control start
- To stop OSSEC HIDS:
/var/ossec/bin/ossec-control stop
- The configuration can be viewed or modified at /var/ossec/etc/ossec.conf
Thanks for using the OSSEC HIDS.
If you have any question, suggestion or if you find any bug,
contact us at contact@ossec.net or using our public maillist at
ossec-list@ossec.net
( http://www.ossec.net/main/support/ ).
More information can be found at http://www.ossec.net
--- Press ENTER to finish (maybe more information below). ---
- In order to connect agent and server, you need to add each agent to the server.
Run the 'manage_agents' to add or remove them:
/var/ossec/bin/manage_agents
More information at:
http://www.ossec.net/en/manual.html#maNext, start OSSEC control service with the following command:
/var/ossec/bin/ossec-control startYou should see the following output:
Starting OSSEC HIDS v3.1.0 (by Trend Micro Inc.)...
Started ossec-maild...
Started ossec-execd...
Started ossec-analysisd...
Started ossec-logcollector...
Started ossec-remoted...
Started ossec-syscheckd...
Started ossec-monitord...
Completed.The default OSSEC configuration file is located at /var/ossec/etc/ossec.conf. By default, OSSEC does not send an e-mail alert when a new file is added to the server. You can do this by editing the ossec.conf file:
nano /var/ossec/etc/ossec.confFind the following lines:
<syscheck>
<!-- Frequency that syscheck is executed - default to every 22 hours -->
<frequency>79200</frequency> And replace them with these following lines:
<syscheck>
<!-- Frequency that syscheck is executed - default to every 60 seconds -->
<frequency>60</frequency>
<alert_new_files>yes</alert_new_files>By default, OSSEC does not send real-time alerts. To enable this setting, find the following lines:
<!-- Directories to check (perform all possible verifications) -->
<directories check_all="yes">/etc,/usr/bin,/usr/sbin</directories>
<directories check_all="yes">/bin,/sbin</directories>And replace them with these following lines:
<directories report_changes="yes" realtime="yes" check_all="yes">/etc,/usr/bin,/usr/sbin</directories>
<directories report_changes="yes" realtime="yes" check_all="yes">/var/www,/bin,/sbin</directories>When finished, save and close the file. Next, you will need to edit the rules file local_rules.xml and add a rules for new file added to the system.
nano /var/ossec/rules/local_rules.xmlAdd the following rules between the ... section:
<rule id="554" level="7" overwrite="yes">
<category>ossec</category>
<decoded_as>syscheck_new_entry</decoded_as>
<description>File added to the system.</description>
<group>syscheck,</group>
</rule>Save the file. Then, restart OSSEC control service to apply all the changes:
/var/ossec/bin/ossec-control restartYou will need to modify the files in /etc/ directory and check whether OSSEC gives an email alert or not. To do so, open /etc/rc.local file:
nano /etc/rc.localAdd the following lines:
#sh test.shSave and close the file. Then, after a minute or so (following the system to process the file), check your mail with the following command:
mailYou should receive an e-mail alert saying that something changed to your system:
[-- Message 10 -- 31 lines, 945 bytes --]:
From ossecm@Node1 Tue Nov 6 19:53:46 2018
Message-Id: <201811061423.wA6ENklc001332@Node1>
To: <root@Node1>
From: OSSEC HIDS <ossecm@Node1>
Date: Tue, 06 Nov 2018 19:53:46 +0530
Subject: OSSEC Alert - Node1 - Level 7 - Integrity checksum changed again (2nd time).
OSSEC HIDS Notification.
2018 Nov 06 19:53:31
Received From: Node1->syscheck
Rule: 551 fired (level 7) -> "Integrity checksum changed again (2nd time)."
Portion of the log(s):
Integrity checksum changed for: '/etc/rc.local'
Old md5sum was: '8097e30bbf5e47a94a521d57542df6fc'
New md5sum is : '2900a119d7ac9729accdc09c6d614b5c'
Old sha1sum was: '07e325e5adce9277f6aee83c76c24e84fe4c4773'
New sha1sum is : 'a946cbd1b674d43c4865b7eb488dfaf2194043f7'You will need to download the OSSEC web UI source from the Git repository. You can download it by running the following command:
wget https://github.com/ossec/ossec-wui/archive/master.zipAfter the download is complete, extract the downloaded file with the following command:
unzip master.zipNext, copy the extracted directory to the Apache web root directory:
cp -r ossec-wui-master /var/www/html/ossecNext, change the directory to the ossec one by installing OSSEC UI with the following command:
cd /var/www/html/ossec
./setup.shThe output is as follows:
trap: SIGHUP: bad trap
Setting up ossec ui...
Username: ossecadmin
New password:
Re-type new password:
Adding password for user ossecadmin
Enter your web server user name (e.g. apache, www, nobody, www-data, ...)
www-data
You must restart your web server after this setup is done.
Setup completed successfully.Next, restart the Apache service to apply all the changes:
systemctl restart apache2Now, open your web browser and type the URL http://your-server-ip/ossec. You will be redirected to OSSEC web interface in the following image:
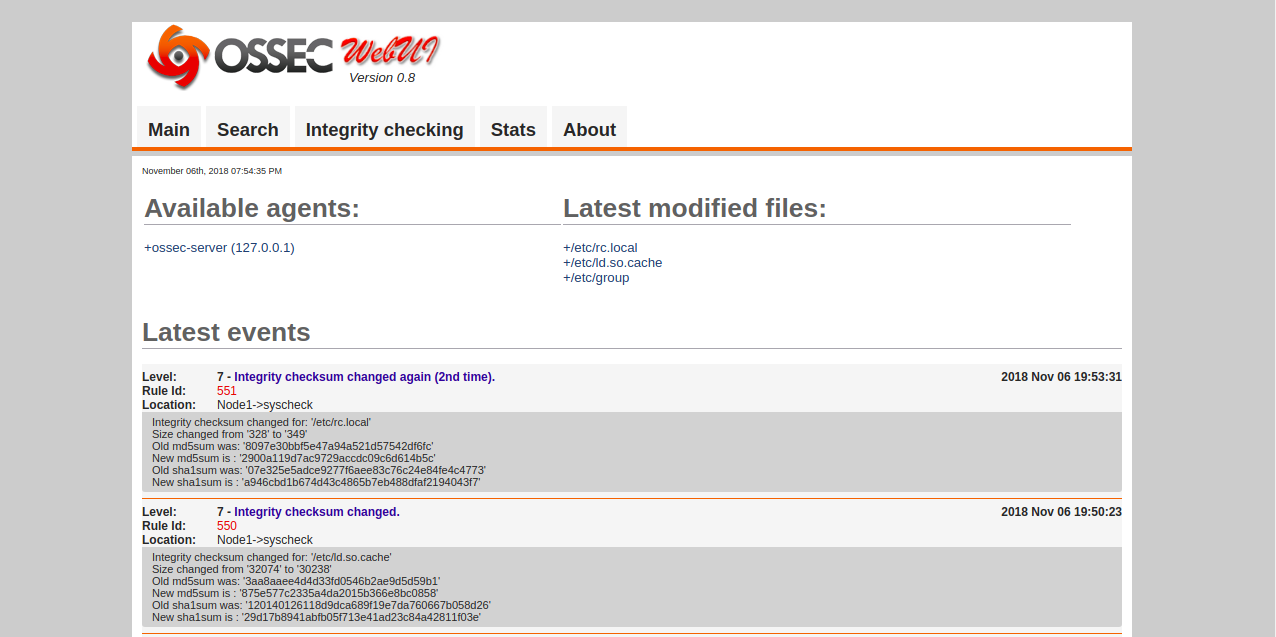
Now that OSSEC server is now running, it's time install OSSEC agent and add it to the OSSEC server. First, log on the OSSEC agent instance and install required dependencies with the following command:
apt-get install build-essential -yNext, download OSSEC source from the Git repository by running the following command:
wget https://github.com/ossec/ossec-hids/archive/3.1.0.tar.gzNext, extract the downloaded file with the following command:
tar -xvzf 3.1.0.tar.gzChange the directory to ossec-hids-3.1.0:
cd ossec-hids-3.1.0Next, install OSSEC client by running the install.sh file:
sh install.shDuring the installation, you will need to answer some questions.
Select your language and press Enter:
(en/br/cn/de/el/es/fr/hu/it/jp/nl/pl/ru/sr/tr) [en]: enThe following output is displayed:
OSSEC HIDS v3.1.0 Installation Script - http://www.ossec.net
You are about to start the installation process of the OSSEC HIDS.
You must have a C compiler pre-installed in your system.
- System: Linux Node2 4.4.0-45-generic
- User: root
- Host: Node2
-- Press ENTER to continue or Ctrl-C to abort. --Next, press Enter to continue. You will see the following output:
1- What kind of installation do you want (server, agent, local, hybrid or help)? agentChoose agent and press Enter. The following output is displayed:
- Agent(client) installation chosen.
2- Setting up the installation environment.
- Choose where to install the OSSEC HIDS [/var/ossec]:
- Installation will be made at /var/ossec .Next, choose your installation location and press Enter. You should see the following output:
3- Configuring the OSSEC HIDS.
3.1- What's the IP Address or hostname of the OSSEC HIDS server?: 192.168.43.192Next, provide your OSSEC server IP address and press Enter. You should see the following output:
- Adding Server IP 192.168.43.192
3.2- Do you want to run the integrity check daemon? (y/n) [y]: Press Enter for integrity check daemon. You should see the following output:
- Running syscheck (integrity check daemon).
3.3- Do you want to run the rootkit detection engine? (y/n) [y]: yPress Enter for the rootkit detection engine. You should see the following output:
- Running rootcheck (rootkit detection).
3.4 - Do you want to enable active response? (y/n) [y]: yPress y to enable active response. You should see the following output:
3.5- Setting the configuration to analyze the following logs:
-- /var/log/auth.log
-- /var/log/syslog
-- /var/log/dpkg.log
-- /var/log/apache2/error.log (apache log)
-- /var/log/apache2/access.log (apache log)
- If you want to monitor any other file, just change
the ossec.conf and add a new localfile entry.
Any questions about the configuration can be answered
by visiting us online at http://www.ossec.net .
--- Press Enter to Continue ---
- System is Debian (Ubuntu or derivative).
- Init script modified to start OSSEC HIDS during boot.
- Configuration finished properly.
- To start OSSEC HIDS:
/var/ossec/bin/ossec-control start
- To stop OSSEC HIDS:
/var/ossec/bin/ossec-control stop
- The configuration can be viewed or modified at /var/ossec/etc/ossec.conf
Thanks for using the OSSEC HIDS.
If you have any question, suggestion or if you find any bug,
contact us at contact@ossec.net or using our public maillist at
ossec-list@ossec.net
( http://www.ossec.net/main/support/ ).
More information can be found at http://www.ossec.net
--- Press ENTER to finish (maybe more information below). ---
- You first need to add this agent to the server so they
can communicate with each other. When you have done so,
you can run the 'manage_agents' tool to import the
authentication key from the server.
/var/ossec/bin/manage_agents
More information at:
http://www.ossec.net/en/manual.html#maYou will need to add OSSEC agent on the OSSES Server. First, log on to your OSSEC server instance and run the following command:
/var/ossec/bin/manage_agentsThe following output is displayed:
* OSSEC HIDS v3.1.0 Agent manager. *
* The following options are available: *
****************************************
(A)dd an agent (A).
(E)xtract key for an agent (E).
(L)ist already added agents (L).
(R)emove an agent (R).
(Q)uit.
Choose your action: A,E,L,R or Q: ASelect A and press Enter to add a new agent. You should see the following output:
- Adding a new agent (use '\q' to return to the main menu).
Please provide the following:
* A name for the new agent: Node2
* The IP Address of the new agent: 192.168.43.193
* An ID for the new agent[001]: 001Next, provide IP address of Agent and press Enter. You will see the following output:
Agent information:
ID:001
Name:Node2
IP Address:192.168.43.193
Confirm adding it?(y/n): yPress Y to confirm adding agent. You will see the following output:
Agent added.
****************************************
* OSSEC HIDS v3.1.0 Agent manager. *
* The following options are available: *
****************************************
(A)dd an agent (A).
(E)xtract key for an agent (E).
(L)ist already added agents (L).
(R)emove an agent (R).
(Q)uit.
Choose your action: A,E,L,R or Q: ENext, select E to Extract key for an agent and press Enter. You will see the following output:
Available agents:
ID: 001, Name: Node2, IP: 192.168.43.193
Provide the ID of the agent to extract the key (or '\q' to quit): 001
Agent key information for '001' is:
MDAxIE5vZGUyIDE5Mi4xNjguNDMuMTkzIDJiOGNlNGYyOTU5ZGZkYTNmMDFjNzY5YjUxODRhZmYyNGY1ZjQzYTA3NmFlMWFiNTBkZDU1MmU1MjU3YTRkZmM=Next, press Q to quit.
Next, you will need to import the agent's key extracted on the server to the OSSEC agent machine. First, log on to the OSSEC agent instance and run the following command:
/var/ossec/bin/manage_agentsYou should see the following output:
****************************************
* OSSEC HIDS v3.1.0 Agent manager. *
* The following options are available: *
****************************************
(I)mport key from the server (I).
(Q)uit.
Choose your action: I or Q: ISelect I to import the key from the server. You will see the following output:
* Provide the Key generated by the server.
* The best approach is to cut and paste it.
*** OBS: Do not include spaces or new lines.
Paste it here (or '\q' to quit): MDAxIE5vZGUyIDE5Mi4xNjguNDMuMTkzIDJiOGNlNGYyOTU5ZGZkYTNmMDFjNzY5YjUxODRhZmYyNGY1ZjQzYTA3NmFlMWFiNTBkZDU1MmU1MjU3YTRkZmM=Paste the key generated on the server and press Enter. The following output is displayed:
Agent information:
ID:001
Name:Node2
IP Address:192.168.43.193
Confirm adding it?(y/n): yPress y and press Enter to confirm key. After this, your OSSEC server and agent is now configured to communicate with each other. Next, restart OSSEC service on both instance to effect the changes:
/var/ossec/bin/ossec-control restartOn the OSSEC server instance, you can list the active agents by running the following command:
/var/ossec/bin/list_agents -cYou should see the following output:
Node2-192.168.43.193 is active.Now, open your web browser and type the URL http://your-server-ip/ossec. You will be redirected to the OSSEC web interface in the following page:
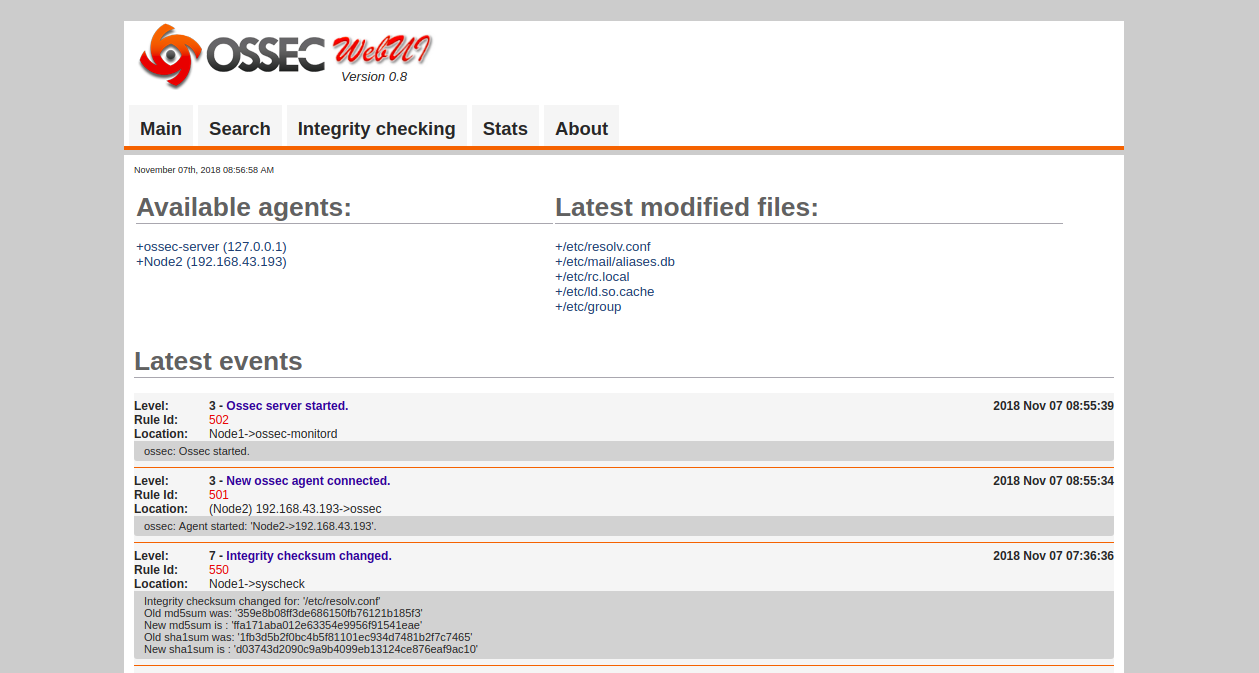

2,605 posts | 747 followers
FollowDikky Ryan Pratama - May 16, 2023
francisndungu - May 29, 2019
Alibaba Clouder - June 18, 2019
Dikky Ryan Pratama - May 5, 2023
Alibaba Clouder - February 13, 2018
Alibaba Clouder - April 23, 2019

2,605 posts | 747 followers
Follow Marketplace
Marketplace
Marketplace is an online market for users to search and quickly use the software as image for Alibaba Cloud products.
Learn More ECS(Elastic Compute Service)
ECS(Elastic Compute Service)
Elastic and secure virtual cloud servers to cater all your cloud hosting needs.
Learn MoreMore Posts by Alibaba Clouder