NGINX was initially designed as a reverse proxy server. However, with continuous development, NGINX also serves as one of the options to implement the forward proxy. The forward proxy itself is not complex, the key issue it addresses is how to encrypt HTTPS traffic. This article describes two methods for using NGINX as the forward proxy for HTTPS traffic, as well as their application scenarios and principal problems.
To begin with, let's take a closer look at the classification of the forward proxy.
Note: In this case, the client actually obtains the self-signed certificate of the proxy server in the TLS handshake process, and verification of the certificate chain is unsuccessful by default. The Root CA certificate among the proxy self-signed certificates must be trusted on the client. Therefore, the client is aware of the proxy in this process. A transparent proxy is achieved if the self-signed Root CA certificate is pushed to the client, which is implemented in the internal environment of an enterprise.
While serving as a reverse proxy, the proxy server usually terminates HTTPS encrypted traffic and forwards it to the backend instance. Encryption, decryption, and authentication of HTTPS traffic occur between the client and the reverse proxy server.
On the other hand, when acting as a forward proxy and processing the traffic sent by the client, the proxy server doesn't see the target domain name in the URL requested by the client since the HTTP traffic is encrypted and encapsulated in TLS/SSL, as shown in the following figure. Therefore, unlike HTTP traffic, HTTPS traffic requires some special processing during proxy implementation.
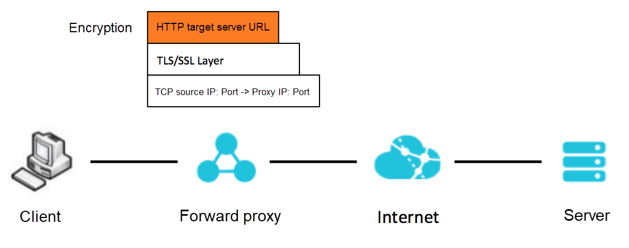
You can refer to How to Use NGINX as an HTTPS Forward Proxy Server, and get more NGINX solution
In this tutorial, we will be installing a NAXSI firewall with Nginx on an Alibaba Cloud ECS Ubuntu 16.04 instance.
Naxsi (Nginx Anti XSS & SQL Injection) is a free, open source and high-performance web application firewall for Nginx. Naxsi is a third party Nginx module that comes with a small subset of rules containing 99% of known patterns involved in website vulnerabilities. The main difference between Naxsi and other firewalls is that it filters only GET and POST requests. You will also need to add a whitelist for the target website to work properly.
If you want to protect your web application from SQL Injection, Cross-Site Scripting (XSS) and Cross-Site Request Forgery, then Naxsi is the best choice for you.
In this tutorial, we will be installing a NAXSI firewall with Nginx on an Alibaba Cloud Elastic Compute Service (ECS) Ubuntu 16.04 instance.
Once you are logged into your Ubuntu 16.04 instance, run the following command to update your base system with the latest available packages.
apt-get update -yIn this article, we will be installing Nginx with RTMP for media streaming on an Alibaba Cloud ECS CentOS 7.
RTMP (Real Time Messaging Protocol) is a high-performance protocol for streaming of data, audio, and video through the internet. In this guide, we will be installing Nginx with RTMP module which is a media streamer based on Nginx. It provides RTMP, HLS, and MPEG-DASH live streaming capabilities. Nginx RTMP module has a lot of features some of them are listed below:
It is recommended that you should install any new packages on a freshly updated server.
First of all, upgrade all the available packages and update the system using the following command.
Elastic and secure virtual cloud servers to cater all your cloud hosting needs.
A single server-based service for application deployment, security management, O&M monitoring, and more
Learn about Alibaba Cloud's security products line and their design strategy. So this course aims to help you better understand the transition from traditional IT infrastructure to cloud infrastructure including current information security best practices and trends. You will get a clear understanding of how to use cloud platform to reduce security risks.
For the security measures of the host on the cloud, we need to consider more factors, such as the configuration of the firewall inside the host, as well as various settings related to operating system user management and privilege management. Only by understanding and correctly configuring the security settings inside these hosts you can better cooperate with various cloud security products. This course is designed to help you better understand these security setup and learn how to properly configure them to maximize the security hardening of hosts on the cloud.
NGINX provides a built-in status page to help you monitor the status of NGINX, similar to PHP-FPM, Docker, and Apache. This topic describes how to use the Logtail feature of Log Service to collect NGINX status information. The topic also describes how to query and analyze the collected status information, create dashboards, and customize alerts to monitor your NGINX cluster.
To use Nginx + FPM in Container Service, we recommend that you use the image https://github.com/ngineered/nginx-php-fpm as the base image, which has both Nginx and FPM in one image.
This image can be used to create a container for Nginx and PHP-FPM. The created container can pull website codes from Git, and push or pull the code changes to or from Git. The container can also update the orchestration file by using the variables passed to Docker so as to update your codes and settings.
This image also supports Let’s Encrypt SSL configurations, customizing Nginx configurations, modifying Nginx/PHP configurations, X-Forwarded-For headers, and UID mapping (support local data volumes).
This image is built with Ubuntu16.04 64bit and bundled with following popular software for web service solution. In order to display web pages to our site visitors, we employ Nginx, a modern, efficient web server. Optimized to add your security concern.
LabEx delivers Alibabacloud labs using live Alibabacloud accounts and resources that help to learn Cloud Computing and how to work with Alibabacloud services. https://labex.io/alibaba
5-Point Approach for Developers when Developing and Deploying Cloud Ready Apps (Part 2)
Cloud Computing Made Really Easy, with SAS from Alibaba Cloud

2,593 posts | 793 followers
FollowWilliam Pan - February 6, 2020
Hiteshjethva - October 31, 2019
Alibaba Clouder - December 3, 2019
Alibaba Clouder - March 6, 2019
Alibaba Container Service - July 28, 2021
Alibaba Clouder - May 29, 2018

2,593 posts | 793 followers
Follow Server Load Balancer
Server Load Balancer
Respond to sudden traffic spikes and minimize response time with Server Load Balancer
Learn More CDN(Alibaba Cloud CDN)
CDN(Alibaba Cloud CDN)
A scalable and high-performance content delivery service for accelerated distribution of content to users across the globe
Learn MoreMore Posts by Alibaba Clouder