By Shantanu Kaushik
Cloud computing and security go hand-in-hand when it comes to a stable and reliable solution. Identity and access management plays an important role in managing different resource access, user groups, and permissions. Granting or denying privileges is the basis of maintaining a hierarchy within an organization.
Identity and Access Management is an essential security practice for any organization. User and user group credentials are one of the most important and critical resources for an enterprise. Identity and Access Management plays an important part in day-to-day business productivity and continuity.
Enterprises have to enable identity and access management to safeguard information and resources against compromised access possibilities. Threats like phishing, spyware, ransomware, and other types of malicious attacks can cripple an organization’s productivity and reputation.
A reliable and active identity and access management suite can prevent attacks and maintain a protection layer over resources that account for application functionality by maintaining user access. A centralized system can further the productivity of any business. If this solution is deeply integrated with other products deployed within an organization, it is considered a plus for security and reliability.
Alibaba Cloud Resource and Access Management (RAM) allows you to manage different user identities and assign permissions for resource access. The core operation of Alibaba Cloud RAM is to assign and maintain an access lifecycle by maintaining digital identities for any product deployment for an organization. This article will give an overview of Alibaba Cloud Resource and Access Management (RAM).
Let’s start by looking at the user account management and permission allocation of Alibaba Cloud RAM:
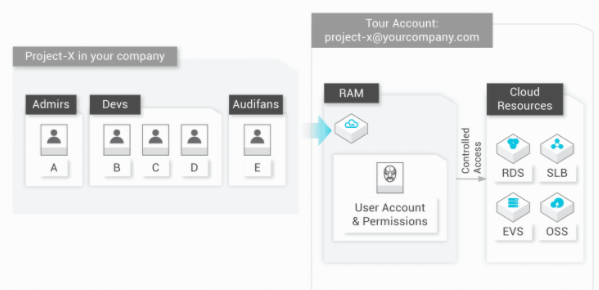
Alibaba Cloud RAM for an enterprise IT solution manages and defines different roles and manages the access of resources for different users or user groups across applications and products. Roles and responsibilities can be directly proportional to the level of access granted or denied by Alibaba Cloud RAM.
Let’s imagine that there are different organizational user groups, such as administration, IT, management, and general staff. Then, there are customers. An enterprise might define multi-tier user groups and access lifecycles based on how deeply integrated and interactive the service roles are.
Alibaba Cloud RAM provides administrators with the tools and resources to define, manage, and change user roles. Administrators can track user activities and generate detailed reports indicating different access times, resource usage, and any other defined or required detail. A properly configured RAM can ensure compliance with corporate or government rules and regulations.
Alibaba Cloud RAM provides a comprehensive solution for Identity and Access Management. It can provide your organization with an edge to the overall functioning. It could be the scenarios that require external user access or access to a customer base. Alibaba Cloud RAM can enable such access while maintaining a balance between security and resource efficiency.
With Alibaba Cloud RAM, you can:
Enable (MFA) Multi-Factor Authentication for Users
Set Access Keys
Use Security Token Service for Mobile Clients
Apply Independent Password Policy Management
Set Execution Permission
Set Group Permissions
Multi-Tier Access Management
Use Version Management
Pay Nothing
Any Identity and Access Management system works with different layers. The RAM system stores personal data that is utilized to define users (identity management.) Another layer is set up to maintain this data and manage it (lifecycle management.) Organizations expand and user base changes. Adding, deleting, and changing access levels must be the service that RAM provides.
The third layer or stage is authorization and access control. In this layer, different access levels and resource allocation is set for different users or user groups. Auditing and report generation takes place here. The system is managed and regulated based on security and compliance standards that your enterprise or the government has put in place.
Several authentication scenarios are put in place, with different authorization and access protocols to ensure proper resource usage. All of these layers coming together make up the Alibaba Cloud RAM system.
With Alibaba Cloud RAM, you can easily extend access to your system for an outside cloud application or an on-premise application resource. You can extend access without worrying about security and authorization on mobile applications or Software as a Service (SaaS) resources. Another aspect is to allow collaboration between teams. Granting temporary access to a resource based on time or select teams enables a far greater collaboration scenario within an enterprise.
In Part 2 of this series on Alibaba Cloud Resource and Access Management (RAM), we will discuss the real-world challenges that enterprises face with Identity and Access Management and how to overcome these challenges using Alibaba Cloud RAM. In Part 3 of this series, we will list all of the usage scenarios related to Alibaba Cloud RAM. We will also list all of the cloud services that support RAM integration and present a how-to article on using Alibaba Cloud RAM to maintain security.
Alibaba Cloud RAM – Part 2: Overcoming IAM Challenges with Alibaba Cloud RAM

2,593 posts | 791 followers
FollowAlibaba Clouder - November 26, 2020
Alibaba Clouder - December 23, 2020
Alibaba Clouder - December 23, 2020
Wladi Mitzel - December 10, 2024
Alibaba Cloud Community - August 12, 2024
ClouderLouder - August 10, 2020

2,593 posts | 791 followers
Follow Resource Management
Resource Management
Organize and manage your resources in a hierarchical manner by using resource directories, folders, accounts, and resource groups.
Learn More RAM(Resource Access Management)
RAM(Resource Access Management)
Secure your cloud resources with Resource Access Management to define fine-grained access permissions for users and groups
Learn More IDaaS
IDaaS
Make identity management a painless experience and eliminate Identity Silos
Learn More Cloud Shell
Cloud Shell
A Web browser-based admin tool that allows you to use command line tools to manage Alibaba Cloud resources.
Learn MoreMore Posts by Alibaba Clouder