Relive the best moments of the Apsara Conference 2019 at https://www.alibabacloud.com/apsara-conference-2019.
"With development of the digital economy, an increasing number of enterprises are migrating their business to the cloud. With this move, enterprises are building next-generation enterprise-level security architecture designs based on cloud-native security technologies, upgrading from a flat architecture to a three-dimensional architecture. With this move, the benefits of cloud-native security technologies will be maximized," said Xiao Li, Senior Director of Cloud Computing Security Department, Alibaba Cloud Intelligence, at the Cloud Security Summit on September 27, 2019 during the Apsara Conference.
During the summit, Xiao Li stressed that cloud-native security technologies will be embedded in every module of the enterprise security architecture, which will help to improve the overall security of the system.

Pictured above is Xiao Li, Senior Director of Cloud Computing Security Department.
At the summit, Xiao Li released the Alibaba Cloud Security White Paper 4.0, in which the core capabilities required for the next-generation enterprise security architecture designs from the perspective of five horizontal systems and two vertical systems were described.
From the horizontal perspective, users need to build five systems. These five systems form a bottom-up security architecture that is tailored towards users' business requirements. The security of the Cloud platform serves as the base layer, upon which the basic security, data security, application security, and business security layers on the user side are stacked on top of each other. Cloud-native security technologies can be implemented in each module of this architecture in the form of product functions or security services, allowing enterprises to enjoy various advantages, such as higher performance, stronger scalability, and more intelligent defense, of cloud-native security technologies.
From the vertical perspective, users need to build two systems: account security and operations security systems. These two systems cover all aspects and nodes. In this case, enterprises can thoroughly transform the flat security architecture to a three-dimensional security architecture. The vertical systems are essential for the cloud security architectures of all enterprises.
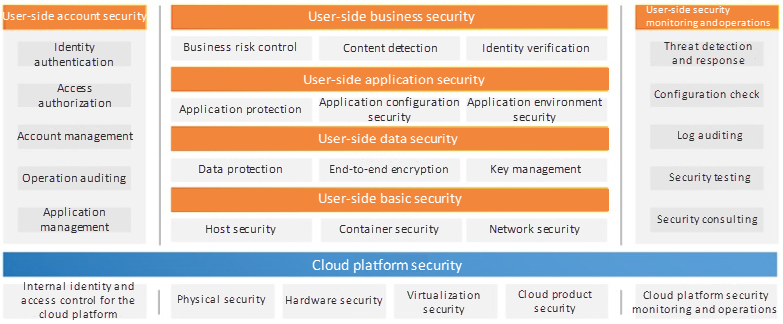
Next-generation enterprise security architecture
In the whitepaper, Xiao Li demonstrated the cloud security best practices provided by Alibaba Cloud to users. His intention is to help enterprises build systems of higher-level security. These best practices include unified account authentication, network access control, data security, threat detection and response, and global security defense.
The growth of cloud-native security brings about boundless benefits to the public and enterprise users alike, making the "unified" security model an inescapable trend. In response to this trend, Alibaba Cloud has applied cloud-native security technologies in their products and services that are provided to cloud-based enterprises, and recommends such best practices to the industry.
In addition to introducing the next-generation enterprise security architecture, Xiao Li also introduced three flagship products based on cloud-native security technologies.
The first is the hybrid cloud security solution. This solution is based on cloud-native security capabilities such as cloud threat intelligence, big data analytics, and automated operations and maintenance. The solution effectively solves the operational challenges such as split security management, different underlying architectures, and inconsistent security tools in a hybrid cloud environment. It helps enterprises implement consistent security policies through one console. At present, it has been applied in fields such as government, tobacco, technology, and finance, and several best practices have been generated.
The second is a trusted solution for cloud platforms. This solution is applicable to both public and private clouds. Alibaba Cloud ensures that the key code and data of business systems and applications on the cloud cannot be tampered with, ensuring the systems and applications are running in a trusted environment. This way, cloud security is ensured at source. The solution has been applied in public clouds.
Data security is the core competency of cloud platforms. The protection of customer privacy has always been the top priority of Alibaba Cloud. The Internal Operation Transparency service was launched during the summit. This service enables users to view operation-related logs in a console. Internal Operation Transparency is currently available to Alibaba Cloud customers in China on an invitational basis. In addition, reliable end-to-end data encryption is provided, and the key is owned and completely controllable only by users, helping users to build a full stack data protection system on the cloud.
"In the future, security management and operations will no longer be burdens for enterprises, but rather capabilities built into infrastructure. Alibaba Cloud will join hands with its ecosystem partners to create a more complete security plan for end users so to bring higher level security capabilities to every cloud-based enterprise", said Xiao Li, in closing the speech.
Solr Dataimport Vulnerability Becomes a New Attack Method for Mining Organizations
Learn the Strategies and Tactics of Cryptocurrency Mining Trojans

32 posts | 15 followers
FollowAlibaba Cloud Community - March 19, 2024
Alibaba Clouder - July 14, 2020
Alibaba Cloud Community - October 21, 2021
Apache Flink Community - March 26, 2025
Alibaba Clouder - February 19, 2021
Alibaba Clouder - December 28, 2020

32 posts | 15 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by Alibaba Cloud Security