本文为您介绍在初次使用数据传输服务DTS(Data Transmission Service)时,如何进行授权,以便DTS能够访问当前云账号下的云资源。
背景信息
为什么要授权
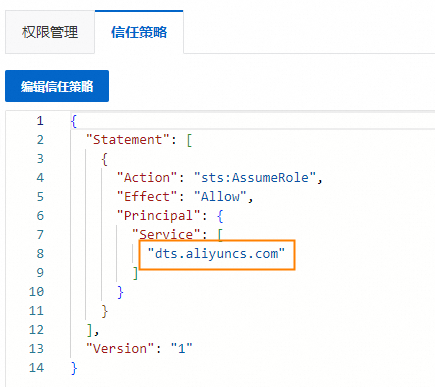
当您使用DTS时,需要创建名称为AliyunDTSDefaultRole的默认角色,并将系统权限策略AliyunDTSRolePolicy授权给该角色。经过授权后,DTS才可以访问当前云账号下的RDS、ECS等云资源,以便在配置DTS任务时调用相关云资源信息。否则,将会因权限问题导致报错,从而无法正常使用DTS配置任务。
若您未正确授予DTS访问云资源的权限,则DTS控制台会有如下错误提示:
错误码:Abnormal.RamCheckUserRole
报错信息:您尚未授权DTS系统默认角色“AliyunDTSDefaultRole”,如果您的账号有写RAM的权限可以自助前往RAM授权,否则需要您的主账号前往RAM进行角色授权后,再刷新本页面
权限策略说明
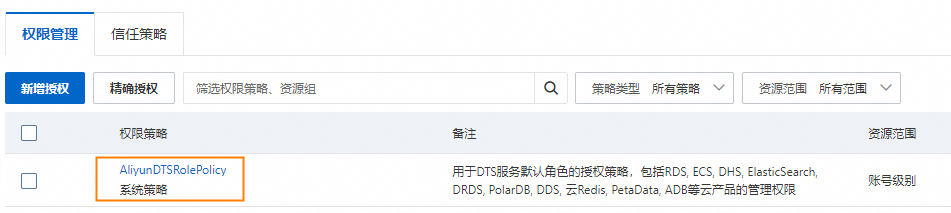
DTS服务默认角色AliyunDTSDefaultRole的系统权限策略AliyunDTSRolePolicy,包含RDS、ECS、PolarDB、MongoDB、Redis、PolarDB-X、DataHub、Elasticsearch等云资源的部分管理权限。具体权限定义,请参见AliyunDTSRolePolicy。
更多关于权限策略的信息,请参见权限策略语法和结构。
授权操作
方式一:通过RAM快捷入口授权(推荐)
使用阿里云账号(主账号)访问快速授权页面,单击确认授权。
若在执行完授权操作后,页面出现错误提示EntityAlreadyExists.Role和EntityAlreadyExists.Role.Policy,则表明当前阿里云账号已授予DTS访问云资源的权限,您可以返回控制台配置DTS任务。

方式二:通过提示框进行授权
使用阿里云账号(主账号),登录数据传输控制台。
在弹出的错误提示对话框中,单击前往RAM授权。
在弹出访问控制快速授权页面,单击确认授权。
等待授权完成后,返回控制台继续操作。

方式三:在RAM访问控制进行授权
查找默认角色。
在搜索结果中,单击目标RAM角色名称(AliyunDTSDefaultRole)。
为目标RAM角色精确授权。
在权限管理页签,单击精确授权。
可选:在精确授权面板中,将策略类型选择为系统策略。
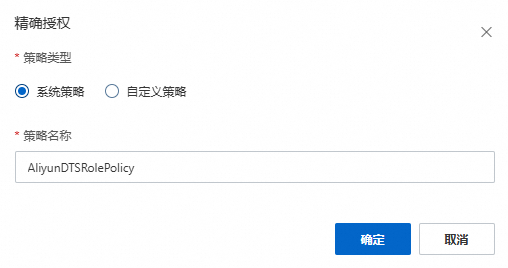
在策略名称文本框,填入AliyunDTSRolePolicy。
单击确定。
您可以在权限管理页签中的右侧,单击
 按钮以刷新页面,查看是否精确授权成功。
按钮以刷新页面,查看是否精确授权成功。
精确授权成功后,单击关闭。
查看授权结果
您可以通过此步骤,查看默认角色的授权结果。
使用阿里云账号(主账号),登录RAM访问控制台。
可选:在左侧导航栏,选择。
在创建角色右侧的文本框,输入AliyunDTSDefaultRole并搜索。
在搜索结果中,单击目标RAM角色名称(AliyunDTSDefaultRole)。
查看角色AliyunDTSDefaultRole的详细信息。