Data Security Center (DSC)檢測響應增值服務支援資料泄露檢測、訪問溯源及自建情報錄入。本文介紹資料泄露概覽查看、資產授權和自建情報錄入等操作。
前提條件
已購買資料資訊安全中心,併購買檢測響應額度(在增值服務中單獨購買或購買企業版擷取預設額度)。如果您未開通檢測響應服務功能或配額不足,您可以進行版本執行個體升級。
確保執行個體所在地區支援檢測響應功能。詳細資料,請參見支援的地區。
資料泄露統計概覽
概覽頁通過多種可視化形式,全面展示了近一年內的資料泄露情況,包括不同類型的泄露事件、發生頻率、風險等級、受影響資產等詳細資料,協助您快速掌握整體安全態勢。
登入資料資訊安全中心控制台。
在左側導覽列,選擇。
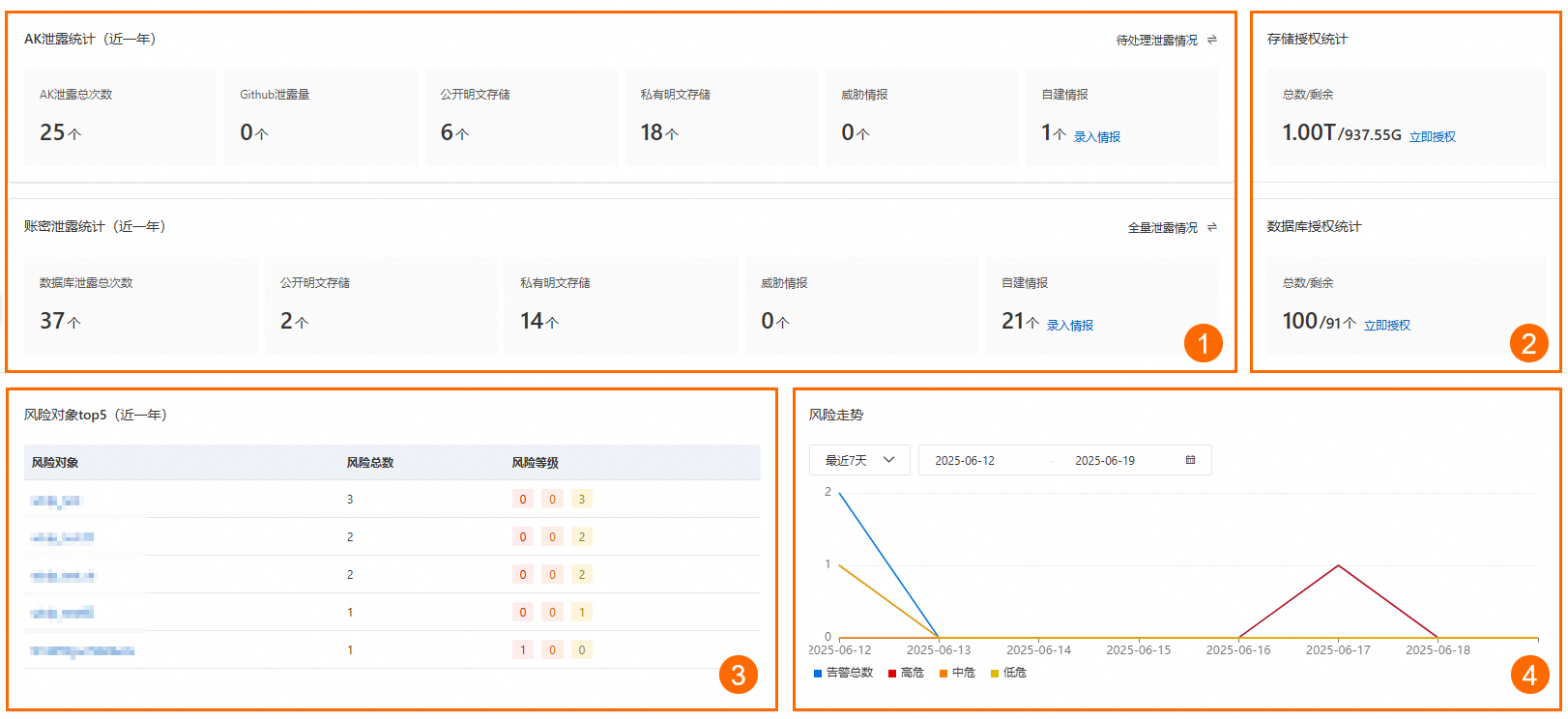
在概覽頁查看資料泄露事件統計資訊及相關操作。
功能區
說明
可執行操作
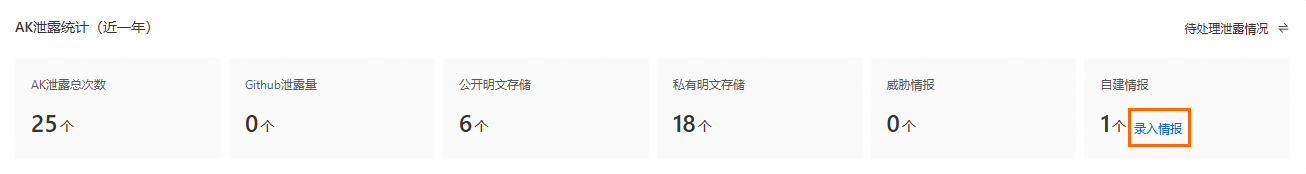
AK泄露及賬密泄露統計(圖示①)
統計全量泄露情况及待处理泄露情况的AK泄露总次数和数据库泄露总次数,其中包括Github泄露量、公开明文存储、私有明文存储、威脅情報及自建情报渠道的泄露次數。
單擊功能區右上方的
 ,查看全量泄露情况和待处理泄露情况。
,查看全量泄露情况和待处理泄露情况。單擊录入情报,自訂AK泄露和賬密泄露情報。
單擊統計的數字,可跳轉至安全事件頁面中風險詳情及處置。
資產授權統計(圖示②)
展示您購買的OSS防護量和資料庫執行個體數的資源容量及使用方式。
單擊立即授權,跳轉至資產授權配置面板,完成資產授權。
風險對象top5(圖示③)
統計風險事件總數Top 5的風險對象和風險等級。
單擊風險對象名稱可跳轉至安全事件頁面中查看該資產的全部類型的風險事件。
風險走勢(圖示④)
通過折線圖直觀地展示警示總數及各風險等級(高危、中危、低危)的個數變化趨勢,以便更好地分析安全態勢。
支援按照最近1天、最近7天、最近15天、最近30天及自定義方式篩選資料。
資產授權
為了檢測OSS Bucket和資料庫執行個體中的潛在資料泄露風險,請按照以下步驟完成資產授權:
登入資料資訊安全中心控制台。
在左側導覽列,選擇。
在概覽頁簽中的存储授权统计和数据库授权统计地區,單擊對應資產的立即授權。
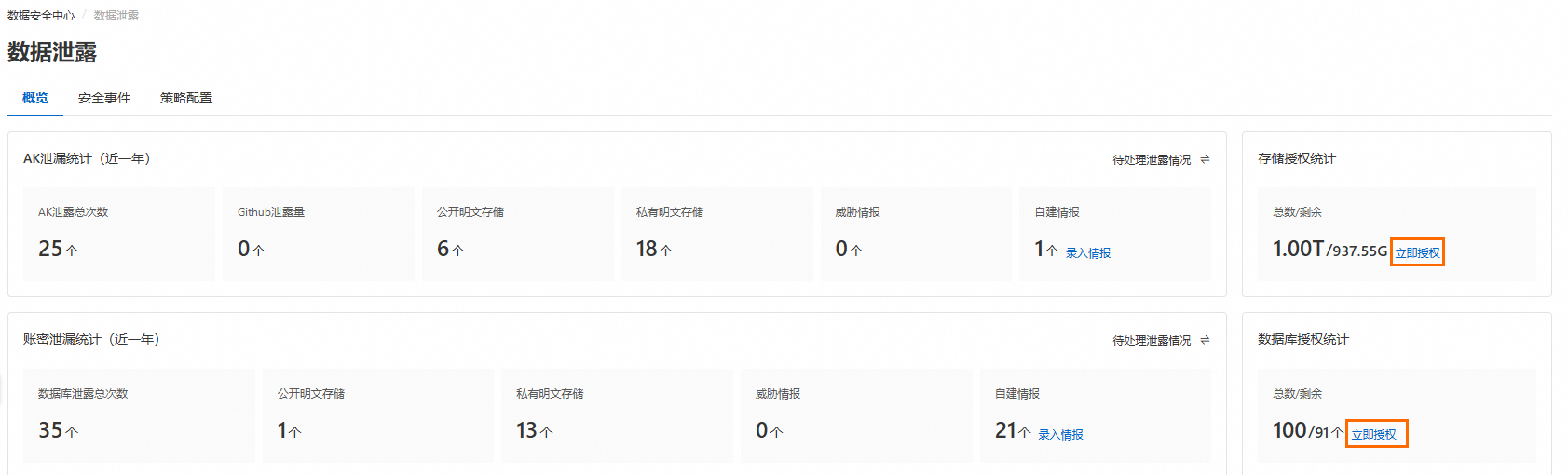
在資產授權配置面板中未授權頁簽完成對目標資產的授權。
 重要
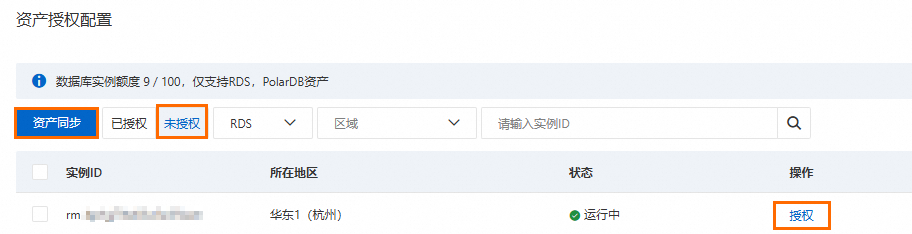
重要目前僅支援RDS和PolarDB資產授權。
如果您未找到需要授權的資產,可以單擊資產同步,等待資產同步完成後再次嘗試。
完成資產授權後,您才可以查看DSC檢測到的風險事件詳細資料。
自建情報錄入
如果已知或懷疑某些AK或資料庫執行個體資訊可能存在泄露風險,可將其相關資訊(包括AK、資料庫執行個體名稱及帳號)統一錄入DSC。後續資料檢測響應服務將對異常AK訪問授權Bucket的行為以及資料庫執行個體的訪問活動進行持續跟蹤,檢測其訪問的檔案和資料庫資訊,並提供即時警示,協助您及時發現並處置資料泄露風險。
AK泄露情報錄入
若在GitHub和已授權Bucket檔案中未檢測到AK泄露,則即使存在AK訪問已授權Bucket的行為,也不會觸發風險事件。因此,如您需查看此類AK訪問行為的事件資訊,需自行建立情報並錄入目標AK資訊。
在AK泄露统计(近一年)地區中,單擊录入情报。
在情报管理面板中,單擊新建情报。
選擇以下方式錄入AK資訊。
單個手動錄入
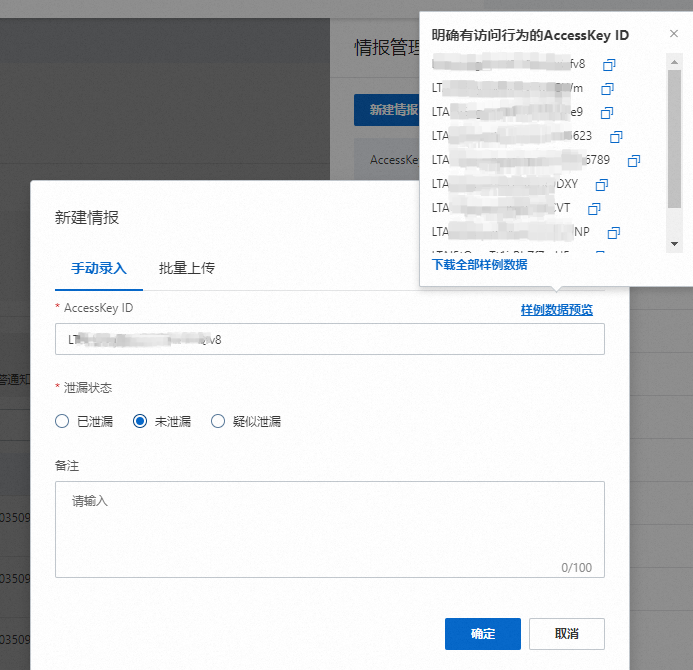
在手动录入頁簽,輸入AccessKey ID,選擇泄露状态(已泄露、未泄露、疑似泄露),輸入備註資訊後,單擊確定。
說明若您已完成目標Bucket授權並在授權成功後至少完成一次檢測,DSC將記錄檢測到的訪問已授權Bucket的AK資訊,並匯總產生範例資料,您可以單擊样例数据预览,複製這些AK資訊用於後續錄入。
批量上傳
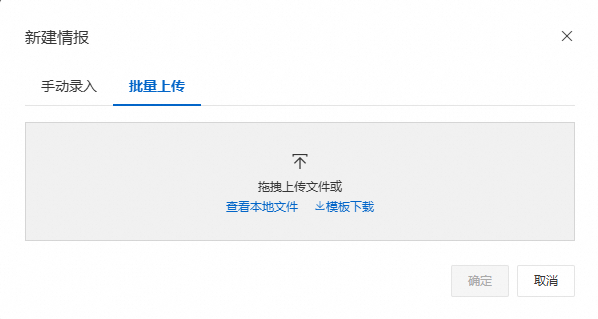
在批量上传頁簽,單擊模板下载,擷取模板檔案(.xlsx),按照格式輸入AccessKeyId(AccessKey ID)、Status(泄露状态:已泄露、未泄露、疑似泄露)和Comment(備註)。
在此之前,如果您已經完成了目標Bucket授權且授權成功後至少完成了一次檢測,DSC會記錄下檢測到的訪問已授權Bucket的AK資訊,並匯總為範例資料寫入模板檔案,如下表所示。
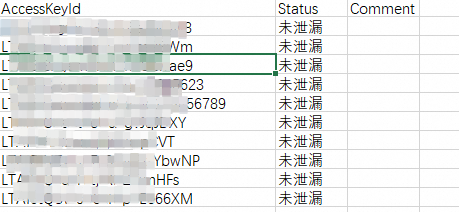
在AK資訊檔中輸入需要錄入的AK資訊,然後儲存。
返回批量上传頁簽,單擊查看本地文件或上傳
 表徵圖,匯入已儲存的.xlsx檔案。
表徵圖,匯入已儲存的.xlsx檔案。單擊確定。
錄入完成後可以在情报管理面板中查看已建立的情報資訊,並支援刪除操作。
賬密泄露情報錄入
對於存在疑似泄露、已泄露或潛在資料泄露風險的資料庫,以及需查看訪問詳情的資料庫,建議將其資訊錄入資料檢測響應的自建情報中,以便進行持續監控與風險分析。
只有完成資料庫執行個體的授權,才能將目標資料庫執行個體錄入自建情報中。
在账密泄露统计(近一年)地區中,單擊录入情报。

在情报管理面板中,單擊新建情报。
在新建情报對話方塊中設定資料庫情報資訊後,並單擊確定。
配置項
說明
資產類型
選擇資產類型。僅支援RDS和PolarDB。
数据库实例
選擇已授權資料庫執行個體。
數據庫賬號
選擇該資料庫執行個體的帳號。
泄露状态
配置泄露狀態。支援選擇已泄露、未泄露或疑似泄露。
備註
輸入備忘資訊。
錄入完成後可以在情报管理面板中查看已建立的情報資訊,並支援刪除操作。
後續操作
您也可以在風險詳情及處置中查看風險事件詳情並對相關風險進行處置。