Container Compute Service (ACS)的授權體系包含對基礎計算資源的RAM授權和對ACS類型ACK叢集側RBAC授權,不同使用者角色在這兩個層面都具有不同的許可權要求。本文介紹針對企業資源管理人員,Kubernetes叢集管理員,以及叢集與應用營運人員、應用開發人員、許可權管理員五類對象的授權最佳實務。
ACS授權體系
ACS的授權體系包含對基礎資源層的RAM授權以及對ACS叢集層的RBAC授權。ACS授權體系如下圖所示。
RAM授權包括對叢集的營運操作,因為ACS叢集是 ACK 的一種 Serverless K8s 叢集類型,對ACS叢集的營運操作需要通過ACK OpenAPI執行,所以需要擷取ACK產品及其所依賴的阿里雲產品的OpenAPI操作許可權,主要包括以下操作:
叢集:建立、查看、刪除。
叢集RBAC授權管理。
叢集監控、日誌、事件。
RBAC授權對應的是運行於ACS叢集中Kubernetes應用的營運操作,需要擷取ACS叢集及其命名空間的操作許可權,主要包括對以下Kubernetes對象的增刪改查操作:
工作負載:Deployment、StatefulSet、Job、CronJob、Pod、ReplicaSet、HPA等。
網路:Service、Ingress、NetworkPolicy等。
儲存:PV、PVC、StorageClass等。
Namespace、ConfigMap、Secrets等。
系統預設授權策略
容器計算服務ACS預置以下系統授權策略,您可以通過給RAM使用者或RAM角色授權系統預設授權策略,完成快速授權。
系統預設授權策略授權範圍較大,可具有ACK、ACS所有OpenAPI的讀或寫入權限,請謹慎授權。
系統預設授權策略 | 授權策略描述 |
AliyunAccFullAccess | 管理容器計算服務ACS的許可權。 |
AliyunAccReadOnlyAccess | 唯讀訪問容器計算服務ACS的許可權。 |
AliyunCSFullAccess | 管理Container ServiceACK的許可權。 重要 可讀寫操作包括ACS類型在內的所有ACK叢集,請謹慎授權。 |
AliyunCSReadOnlyAccess | 唯讀訪問Container ServiceACK的許可權。 重要 可讀操作包括ACS類型在內的所有ACK叢集,請謹慎授權。 |
AliyunAccFullAccess授權策略
{
"Statement": [
{
"Effect": "Allow",
"Action": "acc:*",
"Resource": "*"
}
],
"Version": "1"
}AliyunAccReadOnlyAccess授權策略
{
"Version": "1",
"Statement": [
{
"Action": [
"acc:Describe*",
"acc:CheckServiceRole"
],
"Resource": "*",
"Effect": "Allow"
}
]
}AliyunCSFullAccess授權策略
{
"Version": "1",
"Statement": [
{
"Action": "cs:*",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:PassRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"acs:Service": "cs.aliyuncs.com"
}
}
}
]
}AliyunCSReadOnlyAccess授權策略
{
"Version": "1",
"Statement": [
{
"Action": [
"cs:CheckServiceRole",
"cs:Get*",
"cs:List*",
"cs:Describe*"
],
"Resource": "*",
"Effect": "Allow"
}
]
}授權最佳實務
當RAM使用者或RAM角色需要進行叢集營運和應用營運時,您需要依次對其進行RAM授權和RBAC授權。在進行RBAC授權之前,您需要先進行RAM授權。三種典型情境的授權操作如下:
如果授權對象為叢集與叢集內應用的營運人員,請參見情境一:授權對象為叢集與叢集內應用的營運人員。
如果授權對象為叢集內應用的開發人員,請參見情境二:授權對象為叢集內應用的開發人員。
如果授權對象為叢集內應用的許可權管理員,請參見情境三:授權對象為叢集內應用的許可權管理員。
情境一:授權對象為叢集與叢集內應用的營運人員
授權對象需要管理和營運ACS叢集所需的必要許可權,同時有ACS叢集內應用資來源物件的營運需求。因此授權流程包含RAM授權和RBAC授權。
RAM授權
Container ServiceACK在RAM側提供了AliyunCSFullAccess和AliyunCSReadOnlyAccess兩個系統策略。
AliyunCSFullAccess包含了Container ServiceACK全部OpenAPI的讀寫存取權限。
AliyunCSReadOnlyAccess包含了Container ServiceACK全部OpenAPI的唯讀存取權限。
重要以上兩個系統策略授權操作包括ACS類型在內所有ACK叢集的,請謹慎授權。
您需要登入Resource Access Management控制台,根據需要選擇綁定其中一個系統策略。具體操作,請參見為RAM使用者授權和為RAM角色授權。
如果您有細粒度許可權控制的需求,可以自訂授權策略。具體操作,請參見為RAM使用者或RAM角色授予RAM許可權。
此情境下,RAM授權策略樣本如下所示。
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": "ecs:DescribePrice", "Effect": "Allow", "Resource": "*" }, { "Action": "ram:GetRole", "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:CreateCluster", "cs:DescribeAddons", "cs:DescribeUserQuota", "cs:DescribeTasks", "cs:ListClusterAddonInstances" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "cs:GetClusters", "cs:DescribeClustersV1", "cs:DescribeClusterUserKubeconfig", "cs:DescribeClusterResources", "cs:DescribeUserQuota", "cs:DescribeClusterLogs", "cs:ModifyCluster", "cs:UpgradeCluster", "cs:GetUpgradeStatus", "cs:ResumeUpgradeCluster", "cs:PauseClusterUpgrade", "cs:CancelClusterUpgrade", "cs:InstallClusterAddons", "cs:UpgradeClusterAddons", "cs:DescribeClusterAddonsUpgradeStatus", "cs:UnInstallClusterAddons", "cs:DeleteCluster", "cs:DescribeClusterDetail", "cs:GetClusterAuditProject", "cs:DescribeClusterAddonsVersion", "cs:DescribeClusterTasks", "cs:DescribeClusterEvents", "cs:DescribeEvents", "cs:ListClusterReportSummary", "cs:GetClusterBasicInfo", "cs:ListReportTaskRule", "cs:CreateReportTaskRule", "cs:CheckControlPlaneLogEnable", "cs:CreateClusterCheck" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/<yourclusterID>" }, { "Action": [ "cs:CheckServiceRole", "cs:DescribeKubernetesVersionMetadata" ], "Effect": "Allow", "Resource": "acs:cs:*:*:cluster/*" }, { "Action": [ "log:ListProject" ], "Effect": "Allow", "Resource": "*" }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses", "vpc:DescribeVSwitches" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }上面樣本中
<yourclusterID>需要替換成實際ACS叢集ID。關於Container ServiceACK OpenAPI的更多說明,請參見【產品變更】Container ServiceOpenAPI鑒權最佳化公告和API概覽。
RBAC授權
完成RAM授權後,您還需要為RAM使用者或RAM角色授予對應叢集的RBAC許可權。Container ServiceACK在叢集層面提供了四種預置角色。
角色
叢集內RBAC許可權
管理員
對所有命名空間下所有資源有讀寫權限。
營運人員
對所有命名空間下控制台可見Kubernetes資源有讀寫權限,對叢集節點、儲存卷、命名空間、配額有隻讀許可權。
開發人員
對所有命名空間或所選命名空間下控制台可見Kubernetes資源有讀寫權限。
受限使用者
對所有命名空間或所選命名空間下控制台可見Kubernetes資源有隻讀許可權。
在容器計算服務控制台左側邊欄點擊授權管理頁面,然後在右側子帳號或RAM角色頁簽選擇授權對象,接著點擊系統管理權限。
在彈窗頁面中點擊+添加許可權,配置目的地組群和對應命名空間的許可權管理為營運人員,最後點擊提交授權完成配置。
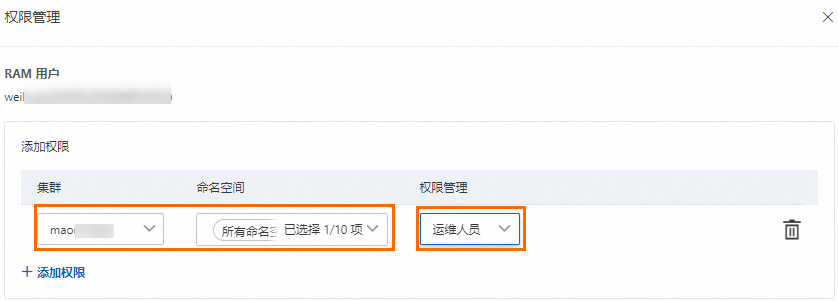
綁定預置角色後,ACS會自動在叢集中建立與被授權對象身份對應的ClusterRoleBinding執行個體。預置營運人員角色的RBAC許可權如下所示。
如果您有細粒度的RBAC許可權控制需求,可以參考RBAC建立自訂ClusterRole執行個體,然後在容器計算服務控制台授權管理頁面選擇自訂角色,再從下拉式清單中選擇自訂的ClusterRole名稱。具體操作,請參見自訂RBAC授權策略。
情境二:授權對象為叢集內應用的開發人員
授權對象只需要擁有ACS類型ACK叢集內Kubernetes資來源物件的操作許可權(即RBAC授權),無需雲上資源的存取權限。
在進行RBAC授權之前,授權對象需要至少具有目的地組群的Container Service唯讀許可權(即RAM授權)。授權Action及Resource “*” 代表授予RAM使用者或RAM角色包括ACS類型叢集在內所有ACK叢集的授權Action操作,所以請盡量不要將Resource置為“*”,除非您充分瞭解授權範圍及影響,有目的性地進行全部授權。
RAM授權
您需要在Resource Access Management控制台,新增自訂策略,並將該策略授權給目標RAM使用者或RAM角色。具體操作,請參見為RAM使用者或RAM角色授予RAM許可權。自訂策略內容如下所示:
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "cs:Get*", "cs:List*", "cs:Check*", "cs:Describe*" ], "Effect": "Allow", "Resource": [ "acs:cs:*:*:cluster/<yourclusterID>"。 ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }上面樣本中
<yourclusterID>需要替換成實際ACS叢集ID。說明如果您只需要為授權對象添加ACS類型ACK叢集的唯讀許可權,請務必通過該樣本指定ACS類型ACK叢集ARN,不可以為其添加Container ServiceACK提供的RAM系統策略
AliyunCSReadOnlyAccess,否則將會為授權對象添加除ACS類型以外所有ACK叢集的唯讀許可權。RBAC授權
在容器計算服務控制台左側邊欄點擊授權管理頁面,然後在右側子帳號或RAM角色頁簽選擇授權對象,接著點擊系統管理權限。
在彈窗頁面中點擊+添加許可權,配置目的地組群和對應命名空間的許可權管理為開發人員,最後點擊提交授權完成配置。
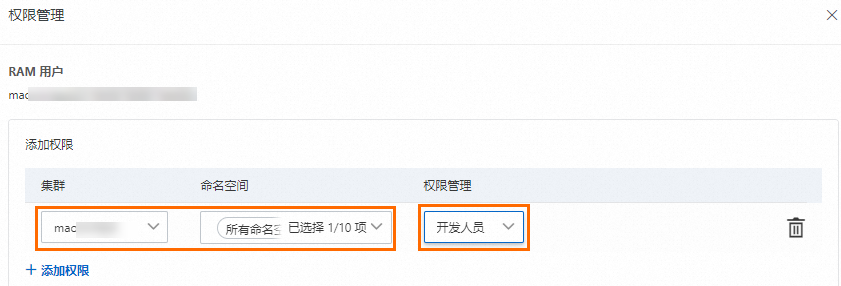
綁定預置角色後,ACS會自動在叢集中建立與被授權對象身份對應的ClusterRoleBinding執行個體。預置開發人員角色的RBAC許可權如下所示。
情境三:授權對象為叢集內應用的許可權管理員
授權對象需要管理其他RAM使用者或RAM角色的RBAC許可權。預設情況下,RAM使用者或RAM角色不具備對其他RAM使用者或RAM角色授權RBAC的許可權。當授權對象進入容器計算服務控制台授權管理頁面時,如果介面提示當前子帳號不具備授權系統管理權限,請聯絡主帳號或許可權管理員授權,則說明授權對象缺少必要的RAM授權或對叢集的RBAC管理員授權。
RAM授權
需要確保授權對象被授予必要的RAM許可權,策略內容需要包括:
列舉其他RAM使用者或RAM角色
給指定RAM使用者或RAM角色授予RAM權限原則
查看指定RAM使用者或RAM角色的Kubernetes RBAC許可權配置
Kubernetes RBAC授權能力
您需要登入Resource Access Management控制台,為指定RAM使用者或RAM角色授予相應的RAM許可權,具體操作,請參見為RAM使用者或RAM角色授予RAM許可權。RAM自訂策略內容樣本如下所示。
{ "Statement": [ { "Effect": "Allow", "Action": [ "acc:DescribeCommodityStatus", "acc:CheckServiceRole", "acc:DescribeCloudProducts", "acc:DescribeRegions", "acc:DescribeZones", "acc:GetInstancePrice", "acc:RecommendZones" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bssapi:GetPayAsYouGoPrice", "Resource": "*" }, { "Action": [ "ram:Get*", "ram:List*", "cs:GetUserPermissions", "cs:GetSubUsers", "cs:GrantPermission", "cs:CheckServiceRole" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "ram:AttachPolicyToUser", "ram:AttachPolicyToRole" ], "Effect": "Allow", "Resource": [ "acs:ram:*:*:policy/xxxx", # xxxx需要替換成您需要綁定的RAM策略名稱稱。如果您替換成*,表示授權對象擁有所有RAM策略的授權綁定能力。 "acs:*:*:*:user/*" ] }, { "Action": [ "vpc:ListEnhanhcedNatGatewayAvailableZones", "vpc:DescribeEipAddresses" ], "Effect": "Allow", "Resource": "*" } ], "Version": "1" }RBAC授權
在容器計算服務控制台左側邊欄點擊授權管理頁面,然後在右側子帳號或RAM角色頁簽選擇授權對象,接著點擊系統管理權限。
在彈窗頁面中點擊+添加許可權,配置目的地組群和對應命名空間的許可權管理為管理員或者自訂角色中的cluster-admin,最後點擊提交授權完成配置。
說明阿里雲帳號(即主帳號)和叢集建立者會預設綁定cluster-admin,擁有叢集內所有Kubernetes資來源物件的存取權限。

當您對授權對象完成了上述RAM授權和RBAC授權後,即可擁有對其他RAM使用者或RAM角色在指定許可權範圍內的RBAC授權管理能力。具體操作,請參見為RAM使用者或RAM角色授予RAM許可權。
鑒權Action說明
許可權名稱(Action) | 說明 |
acc:CheckServiceRole | 檢查帳號是否授權產品通過角色扮演,訪問其他雲資源帳號的ServiceRole。 |
acc:DescribeCommodityStatus | 檢查帳號是否已開通ACS產品。 |
許可權名稱(Action) | 說明 |
bssapi:GetPayAsYouGoPrice | 查詢後付費產品詢價服務。 |
ram:ListUserBasicInfos | 查詢所有RAM使用者的基本資料。 |
ram:ListRoles | 查詢所有RAM角色的基本資料。 |