本文將為您介紹在Container Registry使用自訂OSS Bucket時的RAM存取控制配置。
背景說明
預設OSS Bucket
當使用Container Registry的預設OSS Bucket時,您需為帳號授權Container Registry訪問雲端服務資源,這樣Container Registry才能建立OSS Bucket並初始化ACR執行個體。
自訂OSS Bucket
當您需要使用自訂OSS Bucket,則需要為帳號添加RAM角色,並授予該角色對OSS Bucket操作許可權,以確保Container Registry能夠正常訪問該Bucket。
步驟一:建立RAM角色
Container Registry訪問自訂OSS Bucket時,需要為阿里雲帳號建立的角色名稱為AliyunContainerRegistryCustomizedOSSBucketRole。
使用Resource Access Management員登入RAM控制台。
在左側導覽列,選擇。
在角色頁面,單擊建立角色。
在建立角色頁面,選擇信任主體類型為雲端服務,然後選擇Container Registry,最後單擊確定。
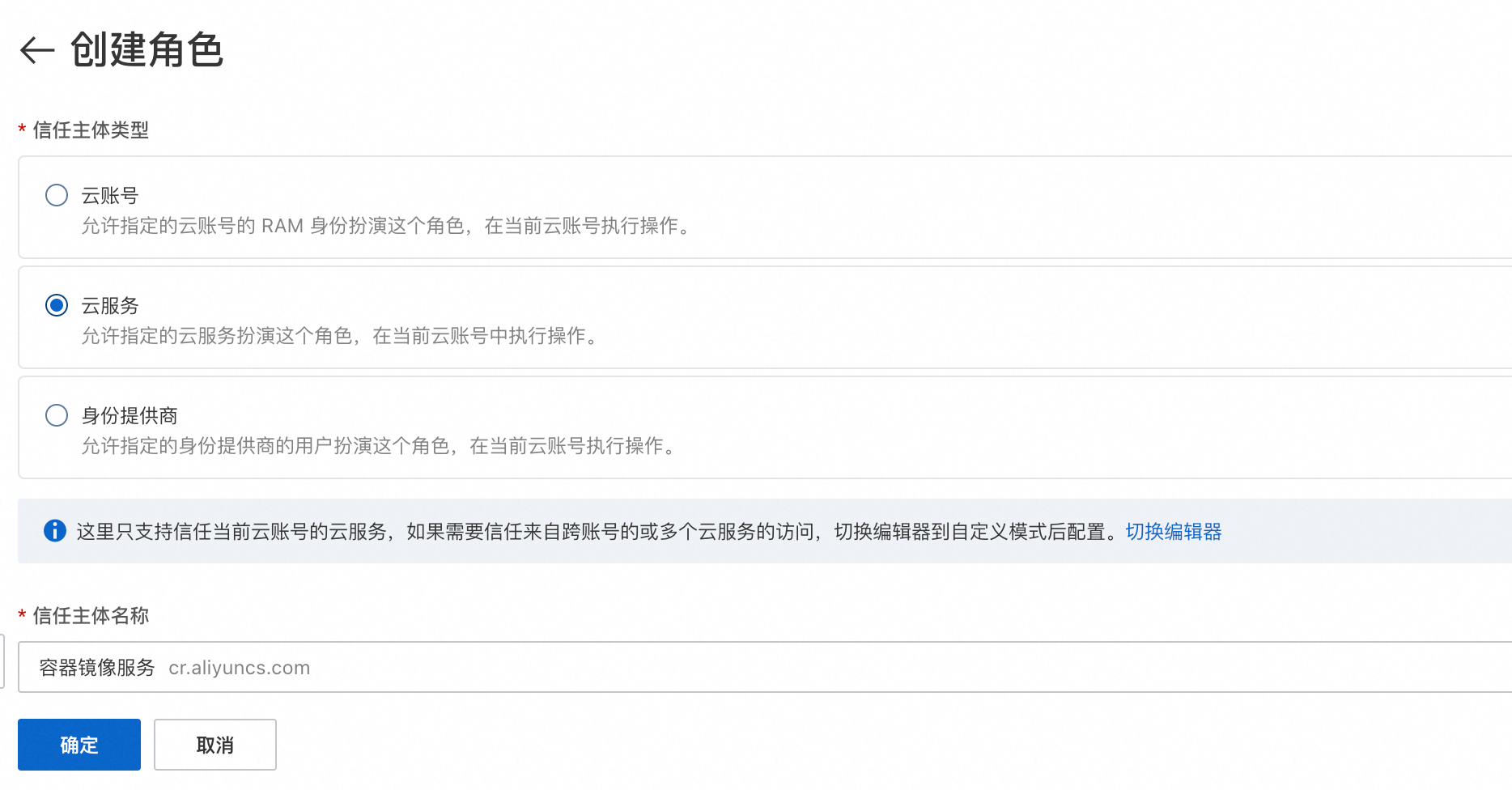
在角色名稱中輸入
AliyunContainerRegistryCustomizedOSSBucketRole,然後單擊確定。
步驟二:配置RAM角色的權限原則
配置該RAM角色的策略,使其擁有對指定的OSS Bucket資源讀取容器鏡像倉庫資訊的許可權,RAM角色的權限原則名為AliyunContainerRegistryCustomizedOSSBucketRolePolicy。當需要擷取多個自訂OSS Bucket資訊時,可向Resource中添加多個OSS Bucket值。
{
"Version": "1",
"Statement": [
{
"Action": [
"oss:GetObject",
"oss:PutObject",
"oss:DeleteObject",
"oss:ListParts",
"oss:AbortMultipartUpload",
"oss:InitiateMultipartUpload",
"oss:CompleteMultipartUpload",
"oss:DeleteMultipleObjects",
"oss:ListMultipartUploads",
"oss:ListObjects",
"oss:DeleteObjectVersion",
"oss:GetObjectVersion",
"oss:ListObjectVersions",
"oss:PutObjectTagging",
"oss:GetObjectTagging",
"oss:DeleteObjectTagging"
],
"Resource": [
"acs:oss:*:*:cri-*",
"acs:oss:*:*:cri-*/*",
"acs:oss:*:*:<YOUR_BUCKET_NAME>", # 請將<YOUR_BUCKET_NAME>替換為您實際需要授權的Bucket名稱。
"acs:oss:*:*:<YOUR_BUCKET_NAME>/*" # 請將<YOUR_BUCKET_NAME>替換為您實際需要授權的Bucket名稱。
],
"Effect": "Allow",
"Condition": {
}
},
{
"Action": [
"oss:PutBucket",
"oss:GetBucket",
"oss:GetBucketLocation",
"oss:PutBucketEncryption",
"oss:GetBucketEncryption",
"oss:PutBucketAcl",
"oss:GetBucketAcl",
"oss:PutBucketLogging",
"oss:GetBucketReferer",
"oss:PutBucketReferer",
"oss:GetBucketLogging",
"oss:PutBucketVersioning",
"oss:GetBucketVersioning",
"oss:GetBucketLifecycle",
"oss:PutBucketLifecycle",
"oss:DeleteBucketLifecycle",
"oss:GetBucketTransferAcceleration"
],
"Resource": [
"acs:oss:*:*:cri-*",
"acs:oss:*:*:cri-*/*",
"acs:oss:*:*:<YOUR_BUCKET_NAME>", # 請將<YOUR_BUCKET_NAME>替換為您實際需要授權的Bucket名稱。
"acs:oss:*:*:<YOUR_BUCKET_NAME>/*" # 請將<YOUR_BUCKET_NAME>替換為您實際需要授權的Bucket名稱。
],
"Effect": "Allow",
"Condition": {
}
},
{
"Effect": "Allow",
"Action": "oss:ListBuckets",
"Resource": [
"acs:oss:*:*:*",
"acs:oss:*:*:*/*"
],
"Condition": {
}
},
{
"Action": [
"vpc:DescribeVpcs"
],
"Resource": "acs:vpc:*:*:vpc/*",
"Effect": "Allow",
"Condition": {
}
},
{
"Action": [
"cms:QueryMetricLast",
"cms:QueryMetricList"
],
"Resource": "*",
"Effect": "Allow"
}
]
}