Disclaimer: This article may contain information about third-party products. Such information is for reference only. Alibaba Cloud does not make any guarantee, express or implied, with respect to the performance and reliability of third-party products, as well as potential impacts of operations on the products.
Problem description
When the origin server uses CDN for acceleration, a 503 error is returned for the requested domain name.
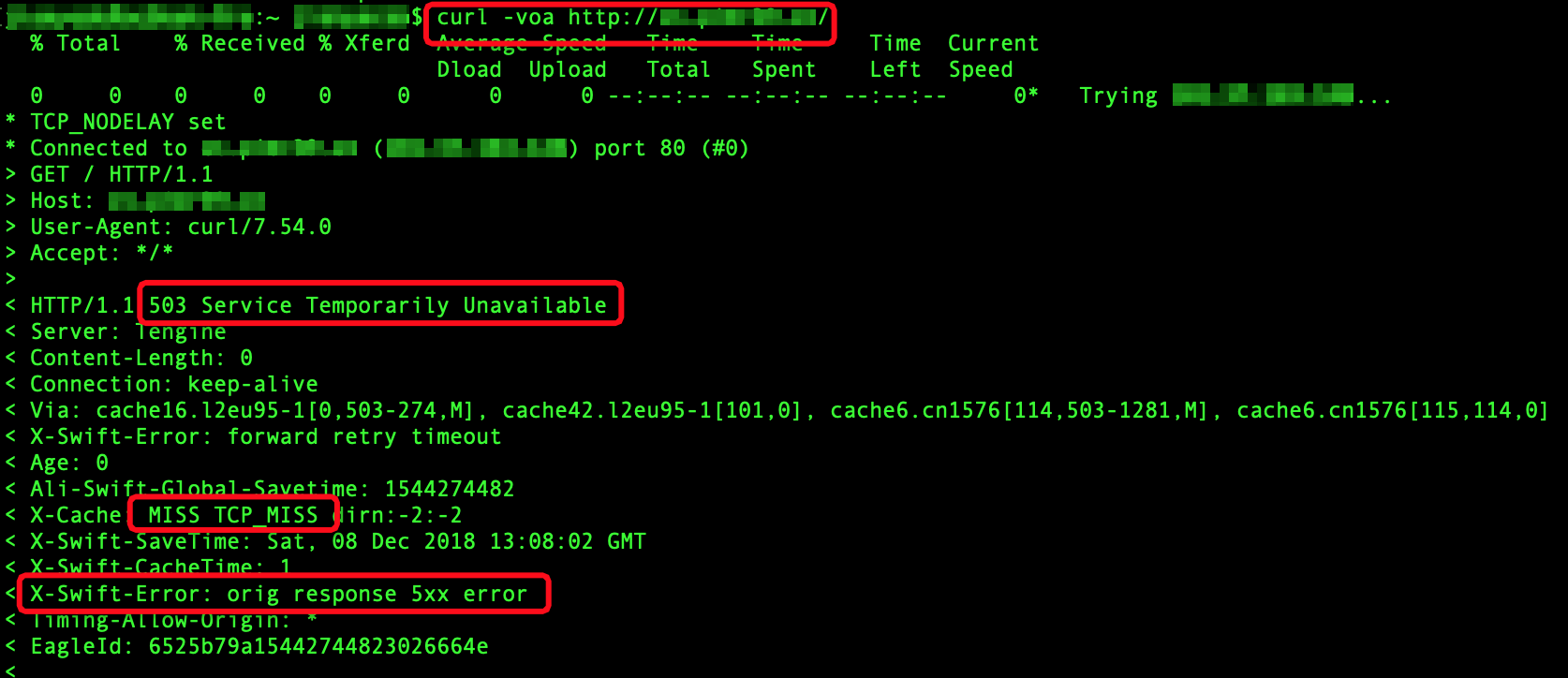
Cause
- Security group rules restrict access.
- The server is configured with a single IP address limit on the number of accesses.
- The Web service is abnormal or the server is overloaded.
- Security policies such as cloud lock, dongle, and firewall block the back-to-origin IP addresses of CDN.
Solution
This topic uses an ECS instance whose origin server is Linux and the Nginx service provides Web services as an example. The following solutions are provided.
CDN read data
The entire process from CDN to read data is as follows:
Client-> CDN L1 layer-> CDN L2 layer-> origin site
When a client requests a resource on your origin server, the client will first request the resource from the CDN L1 node and then from the CDN L2 node. If the CDN L2 node cannot serve the requested resource, the client then requests the resource from the origin server. The origin server synchronizes the requested resource to the CDN L2 node. The CDN L2 node synchronizes the resource to the CDN L1 node. Then, the CDN L1 node returns the resource to the client. For the origin site, the L2 node of CDN is the client.
The IP address of the Origin node.
To prevent the origin server from being attacked, some customers want CDN to provide the IP addresses of back-to-origin nodes and then set an IP address whitelist for the origin server. Only back-to-origin nodes can access the origin server. However, different CDN nodes are intelligently allocated to access your origin server during the back-to-origin process each time. IP addresses of the back-to-origin CDN nodes are not fixed. Therefore, we do not recommend you set the back-to-origin policy of the origin server to a fixed IP address list. This may cause back-to-origin failure.
If you need to configure a whitelist for protection software such as dongle on the origin server, call DescribeL2VipsByDomain to obtain the IP addresses of CDN back-to-origin nodes and add them to the whitelist, so as not to affect the resource retrieval. However, this API only supports calls from users whose daily peak bandwidth is greater than 1 Gbit /s. If you meet the requirements, open a ticket to apply for the API call permission.
Security Group rule restrictions
- Log on to the ECS console.
- On the instance list page, click manage at the right of an instance.
- Click the instance security groups tab, and click security group list.
- View the rule table that is in use, click configure rules, and add or modify security group rules as needed. For more information about how to determine whether an IP address is the IP address of a CDN node, see CDN read data. For more information about how to obtain the IP address of the CDN node, see obtain the IP address of the Origin node.
Maximum number of accesses from a single IP address
- Connect to the Linux instance.
- Check the Nginx configuration file and modify
ngx_http_limit_conn_moduleandngx_http_limit_req_moduleconfiguration items. This example usesngx_http_limit_req_moduleas an example. An example of the configuration file is as follows.http {
limit_req_zone $binary_remote_addr zone=perip:10m rate=10r/s;
...
server {
...
limit_req zone=perip burst=5 nodelay;
}ngx_http_limit_conn_moduleis used to limit the number of connections per defined key, especially the number of connections per IP address. Use thelimit_conn_zoneandlimit_conncommands.- The
ngx_http_limit_req_modulemodule is used to limit the request processing rate for each defined key, especially the request processing rate from a single IP address. Use thelimit_req_zoneandlimit_reqcommands. limit_req_zone $binary_remote_addr zone=perip:10m rate=10r/s;configuration items defines a limit_req_zone to store sessions, with a size of 10 MB of memory, with $binary_remote_addr as Key, limiting the average number of requests per second to 10.limit_req zone=perip burst=5 nodelay;configuration items enable nodelay options, strictly controlling the average rate limit of more than meet the delayed processing.
Web service exception
- Connect to the Linux instance.
- Check the Nginx logs, and troubleshoot the errors accordingly.
- Run the following command to restart the Nginx service:
Note: this operation will affect the business. Use this function with caution.
service restart nginx
Security policy interception
Set the interception policy of each security product and allow the back-to-source IP address of CDN.
Application scope
- CDN