Saat pertama kali masuk ke konsol Cloud Firewall, Anda harus mengotorisasi Cloud Firewall untuk mengakses sumber daya cloud yang diperlukan guna menggunakan layanan yang disediakan oleh Cloud Firewall. Topik ini menjelaskan cara mengotorisasi akses ke sumber daya cloud menggunakan peran terkait layanan Cloud Firewall AliyunServiceRoleForCloudFW, serta cara menghapus AliyunServiceRoleForCloudFW.
Prasyarat
Anda memiliki akun Alibaba Cloud atau pengguna Resource Access Management (RAM) yang memiliki izin untuk membuat dan menghapus peran terkait layanan. Untuk informasi selengkapnya tentang cara memberikan izin yang diperlukan kepada pengguna RAM, lihat FAQ.
Informasi latar belakang
Cloud Firewall menyediakan fitur seperti kontrol akses, pemantauan traffic, dan analisis traffic. Untuk menggunakan fitur-fitur tersebut, Cloud Firewall harus mengakses sumber daya Anda di layanan Alibaba Cloud lainnya, termasuk Elastic Compute Service (ECS), Virtual Private Cloud (VPC), Server Load Balancer, Simple Log Service, Bastionhost, Cloud Enterprise Network (CEN), Security Center, dan ApsaraDB RDS. Anda dapat memberikan izin yang diperlukan melalui peran terkait layanan AliyunServiceRoleForCloudFW, yang secara otomatis dibuat untuk Cloud Firewall. Anda tidak perlu membuat atau memodifikasi peran terkait layanan ini secara manual. Untuk informasi selengkapnya, lihat Peran terkait layanan.
Prosedur
Langganan
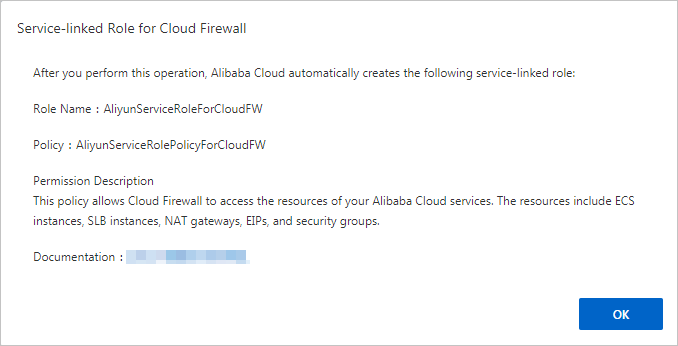
Masuk ke Konsol Cloud Firewall.
Pada kotak dialog Service-Linked Role For Cloud Firewall, klik OK.
CatatanJika Anda telah membuat peran AliyunServiceRoleForCloudFW, kotak dialog ini tidak akan muncul. Anda dapat langsung menggunakan Cloud Firewall di konsol.
Pay-as-you-go
Buka halaman pembelian Cloud Firewall, lalu atur Product Type menjadi Pay-as-you-go 2.0.
Pada bagian Service-linked Role, klik Create Service-Linked Role.
Setelah otorisasi selesai, Alibaba Cloud secara otomatis membuat peran terkait layanan AliyunServiceRoleForCloudFW untuk Cloud Firewall.
Di halaman Roles pada konsol RAM, Anda dapat melihat peran terkait layanan yang dibuat secara otomatis untuk Cloud Firewall. Setelah peran terkait layanan AliyunServiceRoleForCloudFW dibuat, instans Cloud Firewall Anda dapat mengakses sumber daya layanan Alibaba Cloud terkait, seperti Elastic Compute Service (ECS), Virtual Private Cloud (VPC), Server Load Balancer (SLB), Simple Log Service (SLS), Bastionhost, Cloud Enterprise Network (CEN), Security Center, dan ApsaraDB RDS.
Izin AliyunServiceRoleForCloudFW
Secara default, peran terkait layanan AliyunServiceRoleForCloudFW diberikan izin dari Kebijakan sistem AliyunServiceRolePolicyForCloudFW. Kode berikut menunjukkan izin yang didefinisikan dalam Kebijakan AliyunServiceRolePolicyForCloudFW.
{
"Version": "1",
"Statement": [
{
"Action": [
"ecs:DescribeInstances",
"ecs:DescribeTags",
"ecs:JoinSecurityGroup",
"ecs:LeaveSecurityGroup",
"ecs:AuthorizeSecurityGroupEgress",
"ecs:DescribeRegions",
"ecs:DescribeVpcs",
"ecs:RevokeSecurityGroupEgress",
"ecs:ModifySecurityGroupAttribute",
"ecs:DeleteSecurityGroup",
"ecs:RevokeSecurityGroup",
"ecs:DescribeSecurityGroupAttribute",
"ecs:CreateSecurityGroup",
"ecs:AuthorizeSecurityGroup",
"ecs:DescribeSecurityGroups",
"ecs:DescribeSecurityGroupReferences",
"ecs:ModifySecurityGroupPolicy",
"ecs:ModifySecurityGroupRule",
"ecs:ModifySecurityGroupEgressRule",
"ecs:CreateNetworkInterface",
"ecs:DeleteNetworkInterface",
"ecs:DescribeNetworkInterfaces",
"ecs:CreateNetworkInterfacePermission",
"ecs:DescribeNetworkInterfacePermissions",
"ecs:DeleteNetworkInterfacePermission",
"ecs:AttachNetworkInterface",
"ecs:DetachNetworkInterface",
"ecs:ModifyNetworkInterfaceAttribute",
"ecs:DescribePrefixLists",
"ecs:ListTagResources",
"ecs:ImportImage",
"ecs:ModifyInstanceSpec",
"ecs:CreateImage"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"vpc:DescribeVpcs",
"vpc:DescribeNatGateways",
"vpc:DescribeSnatTableEntries",
"vpc:DescribeForwardTableEntries",
"vpc:DescribeBandwidthPackages",
"vpc:GetNatGatewayAttribute",
"vpc:ModifyNatGatewayAttribute",
"vpc:DescribeEipAddresses",
"vpc:DescribeRouterInterfaces",
"vpc:DescribeRouteTableList",
"vpc:DescribeRouteTables",
"vpc:DescribeVSwitches",
"vpc:CreateRouteEntry",
"vpc:DeleteRouteEntry",
"vpc:CreateVpc",
"vpc:DeleteVpc",
"vpc:CreateVSwitch",
"vpc:DeleteVSwitch",
"vpc:DescribeZones",
"vpc:CreateVirtualBorderRouter",
"vpc:ConnectRouterInterface",
"vpc:ModifyRouterInterfaceAttribute",
"vpc:DeleteRouterInterface",
"vpc:CreateRouterInterface",
"vpc:DeleteVirtualBorderRouter",
"vpc:DeactivateRouterInterface",
"vpc:DescribeVirtualBorderRouters",
"vpc:DescribePhysicalConnections",
"vpc:ModifyVirtualBorderRouterAttribute",
"vpc:DescribeVpcAttribute",
"vpc:DescribeVSwitchAttributes",
"vpc:DescribeHaVips",
"vpc:DescribeVpnConnections",
"vpc:DescribeVpnRouteEntries",
"vpc:DescribeVpnPbrRouteEntries",
"vpc:DescribeVpnGateways",
"vpc:DescribeSslVpnServers",
"vpc:AssociateEipAddress",
"vpc:UnassociateEipAddress",
"vpc:CreateRouteTable",
"vpc:DeleteRouteTable",
"vpc:AssociateRouteTable",
"vpc:UnassociateRouteTable",
"vpc:CreateSnatEntry",
"vpc:DeleteSnatEntry",
"vpc:DescribeSnatTableEntries",
"vpc:DescribeRouteEntryList",
"vpc:DescribeIpv6Addresses",
"vpc:ListVpcPeerConnections",
"vpc:CreateRouteEntries",
"vpc:DeleteRouteEntries",
"vpc:ModifyRouteEntry",
"vpc:DescribeRegions",
"vpc:CheckCanAllocateVpcPrivateIpAddress",
"vpc:CreateTrafficMirrorFilterRules",
"vpc:UpdateTrafficMirrorFilterAttribute",
"vpc:AddSourcesToTrafficMirrorSession",
"vpc:GetTrafficMirrorServiceStatus",
"vpc:ListTrafficMirrorFilters",
"vpc:CreateTrafficMirrorFilter",
"vpc:DeleteTrafficMirrorFilter",
"vpc:UpdateTrafficMirrorSessionAttribute",
"vpc:DeleteTrafficMirrorFilterRules",
"vpc:ListTrafficMirrorSessions",
"vpc:CreateTrafficMirrorSession",
"vpc:RemoveSourcesFromTrafficMirrorSession",
"vpc:DeleteTrafficMirrorSession",
"vpc:OpenTrafficMirrorService",
"vpc:UpdateTrafficMirrorFilterRuleAttribute"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"slb:DescribeRegions",
"slb:DescribeLoadBalancers",
"slb:DescribeLoadBalancerAttribute",
"slb:DescribeLoadBalancerUDPListenerAttribute",
"slb:DescribeLoadBalancerTCPListenerAttribute",
"slb:DescribeLoadBalancerHTTPListenerAttribute",
"slb:DescribeLoadBalancerHTTPSListenerAttribute",
"slb:DescribeHealthStatus",
"slb:DescribeAccessControlListAttribute"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"alb:DescribeRegions",
"alb:ListLoadBalancers",
"alb:GetLoadBalancerAttribute",
"alb:ListListeners",
"alb:GetListenerAttribute",
"alb:GetListenerHealthStatus",
"alb:ListAcls",
"alb:ListAclEntries"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"nlb:DescribeRegions",
"nlb:ListLoadBalancers",
"nlb:GetLoadBalancerAttribute",
"nlb:ListListeners",
"nlb:GetListenerAttribute",
"nlb:GetListenerHealthStatus"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"log:PostLogStoreLogs",
"log:GetProject",
"log:ListProject",
"log:GetLogStore",
"log:ListLogStores",
"log:CreateLogStore",
"log:CreateProject",
"log:DeleteProject",
"log:GetLogStoreLogs",
"log:GetIndex",
"log:CreateIndex",
"log:UpdateIndex",
"log:CreateDashboard",
"log:ClearLogStoreStorage",
"log:UpdateLogStore",
"log:UpdateDashboard",
"log:CreateSavedSearch",
"log:UpdateSavedSearch",
"log:DeleteLogStore",
"log:DeleteSavedSearch",
"log:GetSavedSearch",
"log:ListSavedSearch",
"log:DeleteDashboard",
"log:GetDashboard",
"log:ListDashboard",
"log:GetLogStoreHistogram"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"yundun-bastionhost:DescribeInstance",
"yundun-bastionhost:DescribeRegions",
"yundun-bastionhost:DescribeInstances",
"yundun-bastionhost:DescribeInstanceBastionhost",
"yundun-bastionhost:DescribeInstanceAttribute"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"cen:DescribeCens",
"cen:DescribeCenAttachedChildInstances",
"cen:DescribeCenAttachedChildInstanceAttribute",
"cen:AttachCenChildInstance",
"cen:DetachCenChildInstance",
"cen:PublishRouteEntries",
"cen:WithdrawPublishedRouteEntries",
"cen:DescribePublishedRouteEntries",
"cen:DescribeCenRegionDomainRouteEntries",
"cen:ModifyCenAttribute",
"cen:CreateCenRouteMap",
"cen:DeleteCenRouteMap",
"cen:ModifyCenRouteMap",
"cen:DescribeCenRouteMaps",
"cen:DescribeCenChildInstanceRouteEntries",
"cen:CreateCenChildInstanceRouteEntryToCen",
"cen:DeleteCenChildInstanceRouteEntryToCen",
"cen:ListTransitRouters",
"cen:CreateTransitRouter",
"cen:DeleteTransitRouter",
"cen:ListTransitRouterAttachments",
"cen:CreateTransitRouterVpcAttachment",
"cen:DeleteTransitRouterVpcAttachment",
"cen:UpdateTransitRouterVpcAttachmentAttribute",
"cen:UpdateTransitRouterPeerAttachmentAttribute",
"cen:CreateTransitRouterVbrAttachment",
"cen:DeleteTransitRouterVbrAttachment",
"cen:ListTransitRouterPeerAttachments",
"cen:ListTransitRouterVpcAttachments",
"cen:ListTransitRouterVbrAttachments",
"cen:ListTransitRouterAvailableResource",
"cen:CreateTransitRouterRouteTable",
"cen:UpdateTransitRouterRouteTable",
"cen:DeleteTransitRouterRouteTable",
"cen:ListTransitRouterRouteTables",
"cen:CreateTransitRouterRouteEntry",
"cen:DeleteTransitRouterRouteEntry",
"cen:ListTransitRouterRouteEntries",
"cen:ListTransitRouterRouteTableAssociations",
"cen:AssociateTransitRouterAttachmentWithRouteTable",
"cen:DissociateTransitRouterAttachmentFromRouteTable",
"cen:ListTransitRouterRouteTablePropagations",
"cen:EnableTransitRouterRouteTablePropagation",
"cen:DisableTransitRouterRouteTablePropagation",
"cen:ModifyCenUserQuota",
"cen:ReplaceTransitRouterRouteTableAssociation",
"cen:CheckTransitRouterService",
"cen:ListTransitRouterPrefixListAssociation"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"netana:DescribeNetworkQuotas",
"netana:DescribeNetworkQuotaRequestResult",
"netana:CreateNetworkQuotaRequest"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"privatelink:CheckProductOpen",
"privatelink:OpenPrivateLinkService",
"privatelink:CreateVpcEndpoint",
"privatelink:DeleteVpcEndpoint",
"privatelink:ListVpcEndpoints",
"privatelink:ListVpcEndpointZones",
"privatelink:AddZoneToVpcEndpoint",
"privatelink:RemoveZoneFromVpcEndpoint",
"privatelink:ListVpcEndpointServicesByEndUser"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"yundun-sas:DescribeVulList",
"yundun-sas:DescribeVulDetails",
"yundun-sas:DescribeCloudCenterInstances"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"yundun-cert:DescribeCACertificateList",
"yundun-cert:GetUserStatus",
"yundun-cert:CreateTestOrder",
"yundun-cert:CreateRootCACertificate",
"yundun-cert:CreateSubCACertificate"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"cs:DescribeUserQuota",
"cs:DescribeClusterNodes",
"cs:DescribeClusterNodePools",
"cs:DescribeClusterNodePoolDetail",
"cs:DescribeUserClusterNamespaces",
"cs:DescribeClustersV1",
"cs:DescribeClusterUserKubeconfig",
"cs:DescribeClusterResources",
"cs:DescribeClusterDetail",
"cs:GetClusters",
"cs:DescribeUserPermission",
"cs:UpdateUserPermissions",
"cs:GrantPermissions",
"cs:CleanClusterUserPermissions"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"rds:DescribeDBInstances"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:CreateServiceLinkedRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"ram:ServiceName": "cen.aliyuncs.com"
}
}
},
{
"Action": [
"resourcemanager:ListAccounts"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"cms:QueryMetricList",
"cms:QueryMetricData",
"cms:QueryMetricLast"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "yundun-aegis:DescribeAccesskeyLeakList",
"Resource": "*",
"Effect": "Allow"
},
{
"Action": "ram:DeleteServiceLinkedRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"ram:ServiceName": "cloudfw.aliyuncs.com"
}
}
},
{
"Action": "ram:CreateServiceLinkedRole",
"Resource": "*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"ram:ServiceName": "privatelink.aliyuncs.com"
}
}
}
]
}Untuk informasi selengkapnya tentang sintaks kebijakan akses, lihat Elemen kebijakan.
Hapus peran terkait layanan
Jika Anda tidak lagi memerlukan Cloud Firewall, Anda dapat menghapus peran terkait layanan Cloud Firewall AliyunServiceRoleForCloudFW. Peran ini hanya dapat dihapus setelah instans Cloud Firewall Anda kedaluwarsa dan secara otomatis dirilis. Untuk informasi selengkapnya, lihat Hapus peran RAM.
FAQ
Mengapa Pengguna RAM saya tidak dapat secara otomatis membuat peran terkait layanan Cloud Firewall AliyunServiceRoleForCloudFW?
Pengguna RAM memerlukan izin tertentu untuk secara otomatis membuat atau menghapus AliyunServiceRoleForCloudFW. Jika Pengguna RAM tidak dapat secara otomatis membuat AliyunServiceRoleForCloudFW, Anda dapat menyambungkan kebijakan akses berikut ke Pengguna RAM tersebut. Untuk informasi selengkapnya, lihat Berikan izin kepada Pengguna RAM.
{
"Statement": [
{
"Action": [
"ram:CreateServiceLinkedRole"
],
"Resource": "acs:ram:*:ID of your Alibaba Cloud account:role/*",
"Effect": "Allow",
"Condition": {
"StringEquals": {
"ram:ServiceName": [
"cloudfw.aliyuncs.com"
]
}
}
}
],
"Version": "1"
}