This topic describes how to resolve HTTPS access exceptions that are caused by Server name indication (SNI) compatibility issues between clients after the related web services are added to Web Application Firewall (WAF).
Background
Virtual hosting is introduced to address the challenge of IP address shortage. Virtual hosting allows a single HTTP or HTTPS server to host multiple domain names by sharing the same IP address. In this case, each domain name serves as a virtual host. The server can allocate requests to different virtual hosts based on the Host headers carried in client requests. For example, before a browser can access an HTTPS website hosted on a web server on which virtual hosting is enabled, the browser must establish an SSL connection with the server and request the required server certificate. However, the server cannot identify which domain name is accessed and cannot return the required certificate.
SNI is an SSL/TLS extension designed to resolve this issue. Before an SSL connection is established with the server, the browser sends the hostname that specifies the domain name to access to the server. Then, the server identifies and returns the certificate for the domain name.
Most operating systems and browsers support SNI. OpenSSL 0.9.8 supports built-in SNI. New version of NGINX servers also support SNI.
Problem description
If your website encounters HTTPS access exceptions after the website is added to WAF, the related clients may not support SNI.
If a browser that does not support SNI is used to access a WAF-protected website, WAF cannot identify the specific domain name that is requested or obtain the required certificate for the domain name to interact with the browser. In this case, WAF uses the default certificate to complete the handshake process with the browser, and the browser reports the "Certificate not trusted" error.
If a client does not support SNI, the following issues may occur:
If the client is a mobile app that runs on iOS, the access is successful. If the client is a mobile app that runs on Android, the access fails.
If the client is a browser, the "Certificate not trusted" error is reported.
Solution
Capture SSL handshake packets on the client side to determine whether the client supports SNI. In this example, the Chrome browser is used to access the official website of Alibaba Cloud.
If SNI information is included in the Client Hello packet, the client supports SNI.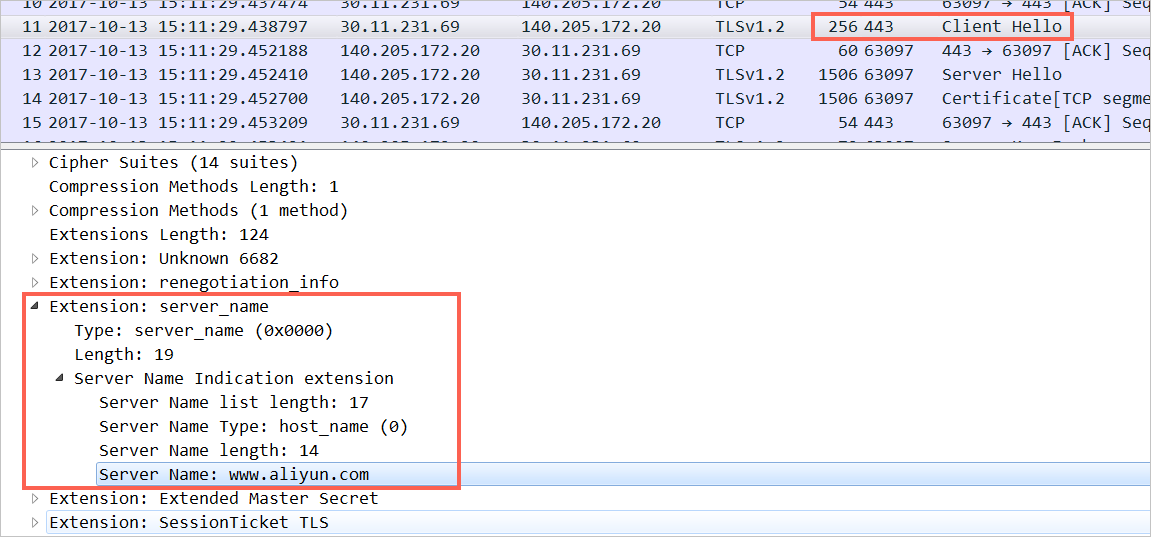
Otherwise, the client does not support SNI. Recommendations:
Upgrade your browser or use the latest version of browser, such as Chrome and Firefox.
In third-party callback scenarios such as WeChat or Alipay callback, use the IP address of the origin server to bypass WAF.
SNI compatibility
SNI is compatible with TLS1.0 and later versions but not supported by SSL.
SNI supports the following desktop browsers:
Chrome 5 and later versions
Chrome 6 and later versions (Windows XP)
Firefox 2 and later versions
IE 7 and later versions (on Windows Vista/Server 2008 and later versions, excluding IE of any version on Windows XP)
Konqueror 4.7 and later versions
Opera 8 and later versions
Safari 3.0 on Windows Vista/Server 2008 and later versions or Mac OS X 10.5.6 and later versions
SNI supports the following libraries:
GNU TLS
Java 7 and later versions (serving as the client only)
HTTP client 4.3.2 and later versions
libcurl 7.18.1 and later versions
NSS 3.1.1 and later versions
OpenSSL 0.9.8j and later versions
OpenSSL 0.9.8f and later versions (flags required)
QT 4.8 and later versions
Python3, Python 2.7.9, and later versions
SNI supports the following mobile browsers:
Android Browser on 3.0 Honeycomb and later versions
iOS Safari on iOS 4 and later versions
Windows Phone 7 and later versions
SNI supports the following servers:
Apache 2.2.12 and later versions
Apache Traffic Server 3.2.0 and later versions
HAProxy 1.5 and later versions
IIS 8.0 and later versions
lighttpd 1.4.24 and later versions
LiteSpeed 4.1 and later versions
Nginx 0.5.32 and later versions
SNI supports the following command line interfaces:
cURL 7.18.1 and later versions
wget 1.14 and later versions