You can configure an instance policy to restrict the IP addresses, virtual private clouds (VPCs), and TLS versions that can be used to access a Tablestore instance. This topic describes how to configure an instance policy.
Syntax
An instance policy consists of the following basic elements: effect, action, resource, and condition.
Elements
The following table describes the elements of an instance policy.
Element | Description |
Effect | Specifies whether the policy result is an explicit allow or an explicit deny. Valid values: Allow and Deny. |
Action | The operations that are allowed or denied. The value is All Actions (*) and cannot be modified. |
Resource | The objects on which the operations are performed. The value is All Resources (*) and cannot be modified. |
Condition | The conditions that are required for the policy to take effect. For more information about the conditions that can be configured, see the Conditions section of this topic. For more information about common configuration examples, see the Sample policies section of this topic. |
Conditions
You can configure Tablestore-specific conditions and common conditions in an instance policy. The following table describes the conditions. An asterisk (*) indicates all actions. For more information about common conditions, see Policy elements.
Type | Condition key | Action | Description |
Tablestore-specific conditions |
|
| The condition that specifies whether to create or update only encrypted tables. Valid values: true and false. Example: |
| * | The condition that specifies whether to allow access from the trusted proxy, which is the Tablestore console. Valid values: true and false. Example: | |
|
| The condition that specifies whether to create only instances that cannot be accessed over the Internet. Valid values: true and false. Example: | |
| * | The TLS versions that can be used to access the Tablestore instance. If you specify this condition, users can access the Tablestore instance only over HTTPS. Valid values: 1.1, 1.2, and 1.3. You can specify multiple TLS versions in each condition. If multiple TLS versions are specified, a client can access the Tablestore instance by using one of the specified TLS versions. | |
Common conditions |
| * | The source IP addresses or CIDR blocks that are allowed or denied if requests are not sent from VPCs. Valid values include IPv4 addresses, IPv6 addresses, and CIDR blocks. You can specify specific IP addresses and CIDR blocks at the same time in a single condition. |
| * | The source VPCs that are allowed or denied. Specify valid VPC IDs for this condition. You can configure multiple VPC IDs in a single condition. |
Sample policies
You can allow or deny access to a Tablestore instance by configuring instance policies. You can configure instance policies to restrict TLS versions, source IP addresses, and source VPCs. Configure instance policies based on your business requirements.
Restrict the TLS versions that can be used to access a Tablestore instance
You can configure an instance policy to restrict access to a Tablestore instance only by using specified TLS versions. This enhances Tablestore access security.
The following sample policy allows access to a Tablestore instance only by using TLS 1.2 and TLS 1.3. In this example, the Condition Key parameter is set to ots:TLSVersion, the Operator parameter is set to StringEquals, and the Condition Value is set to 1.2 and 1.3.
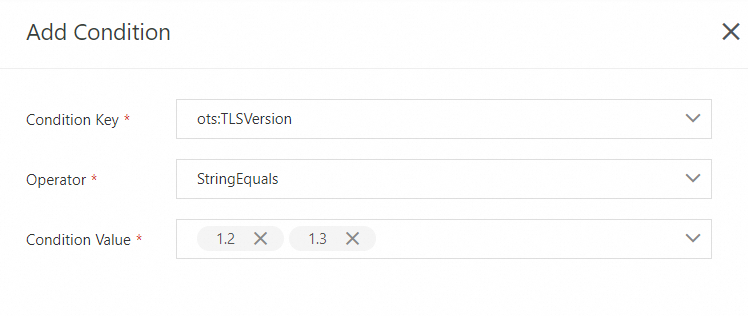
Sample script:
{
"Action": [
"ots:*"
],
"Resource": [
"acs:ots:*:13791xxxxxxxxxxx:instance/myinstance*"
],
"Principal": [
"*"
],
"Effect": "Allow",
"Condition": {
"StringEquals": {
"ots:TLSVersion": [
"1.2",
"1.3"
]
}
}
}Restrict the IP addresses or CIDR clocks that can be used to access a Tablestore instance
You can configure an instance policy to allow users to access a Tablestore instance only from specified CIDR blocks or IP addresses.
The following sample policy allows only requests from the IP address 10.10.XX.XX or CIDR block 10.10.XX.XX/24.
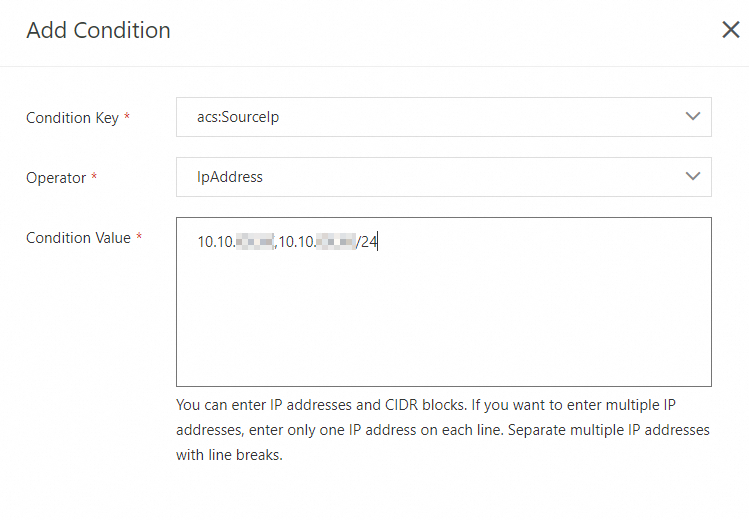
Sample script:
{
"Action": [
"ots:*"
],
"Resource": [
"acs:ots:*:13791xxxxxxxxxxx:instance/myinstance*"
],
"Principal": [
"*"
],
"Effect": "Allow",
"Condition": {
"IpAddress": {
"acs:SourceIp": [
"10.10.XX.XX",
"10.10.XX.XX/24"
]
}
}
}Restrict the VPCs that can be used to access a Tablestore instance
You can configure an instance policy to restrict the VPCs that can be used to access a Tablestore instance.
The following sample policy allows only requests from the specified VPC.
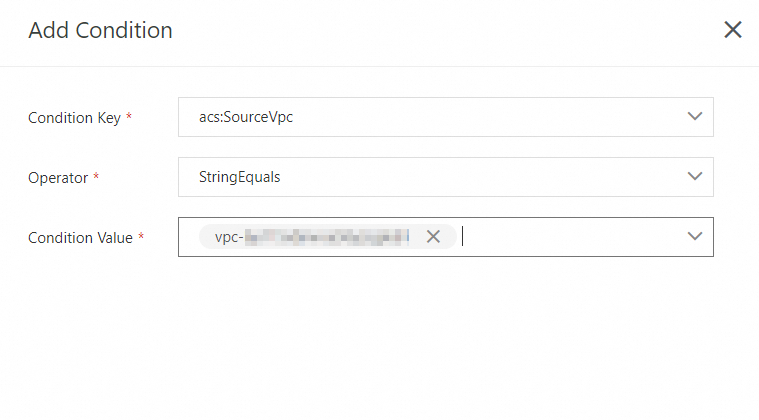
Sample script:
{
"Action": [
"ots:*"
],
"Resource": [
"acs:ots:*:13791xxxxxxxxxxx:instance/myinstance*"
],
"Principal": [
"*"
],
"Effect": "Allow",
"Condition": {
"StringEquals": {
"acs:SourceVpc": [
"vpc-bp1gri6xxxxxxxxxxx"
]
}
}
}Typical scenarios
Based on the preceding examples, you can configure instance policies in the following typical scenarios.
Scenario 1: Allow only users from a specific CIDR block to access a Tablestore instance only by using the specified TLS versions
To configure an instance policy to allow only users from the 10.10.XX.XX/24 CIDR block to access the Tablestore instance named myinstance only by using TLS 1.2 and TLS 1.3, perform the following steps:
Go to the Create Policy panel.
Log on to the Tablestore console.
On the Overview page, select a region and click the instance name myinstance.
On the instance details page, click the Security Policy tab. On the Security Policy tab, click Authorize.
In the Create Policy panel, click the Visualized Policy tab. On the Visualized Policy tab, set the Effect parameter to Allow.
Add the conditions.
Click Add Condition and then click Edit for the condition. In the Add Condition panel, set the Condition Key parameter to
acs:SourceIp, the Operator parameter to IpAddress, and the Condition Value parameter to10.10.XX.XX/24. Then, click Yes.Click Add Condition and then click Edit for the condition. In the Add Condition panel, set the Condition Key parameter to
ots:TLSVersion, the Operator parameter to StringEquals, and the Condition Value parameter to 1.2 and 1.3. Then, click Yes.
Click Yes.
Scenario 2: Allow users to access a Tablestore instance only from the specified VPC
To configure an instance policy to allow users that use IP addresses 10.10.XX.XX to access a Tablestore instance named myinstance only from the specified VPC, perform the following steps:
Go to the Create Policy panel.
Log on to the Tablestore console.
On the Overview page, select a region and click the instance name myinstance.
On the instance details page, click the Security Policy tab. On the Security Policy tab, click Authorize.
In the Create Policy panel, click the Visualized Policy tab. On the Visualized Policy tab, set the Effect parameter to Allow.
Add the conditions.
Click Add Condition and then click Edit for the condition. In the Add Condition panel, set the Condition Key parameter to
acs:SourceIp, the Operator parameter to IpAddress, and the Condition Value parameter to10.10.XX.XX. Then, click Yes.Click Add Condition and then click Edit for the condition. In the Add Condition panel, set the Condition Key parameter to
acs:SourceVpc, the Operator parameter to StringEquals, and the value of the Condition Value parameter to the ID of the specified VPC. Then, click Yes.
Click Yes.