After you collect logs to a Logstore, you can configure an alert rule for the logs. This topic describes how to configure an alert rule and send alert notifications to a DingTalk group.
Procedure
In this example, an alert rule is configured and a DingTalk group is used to receive alert notifications. After logs are collected to a Logstore, the alert rule checks whether the Logstore contains data at 15-minute intervals. If the Logstore contains data, an alert is triggered and an alert notification is sent to the specified user by DingTalk.

Configure a notification recipient: Create a user named
Boband addBobto a user group.Configure an alert rule: Configure an alert rule that checks whether a Logstore contains data at 15-minute intervals. If the Logstore contains data, an alert is triggered.
Configure a notification policy: Use the built-in alert template of Simple Log Service to configure alert notifications and send alert notifications to a DingTalk group to notify
Bob.
Prepare data
Before you configure an alert rule, make sure that logs are collected to your Logstore.
Log on to the Simple Log Service console.
In the Projects section, click the project that you want to manage.
Click the
 icon. In the Logstores list, click the Logstore that you want to manage. Then, click Search & Analyze to view the collected logs.
icon. In the Logstores list, click the Logstore that you want to manage. Then, click Search & Analyze to view the collected logs. 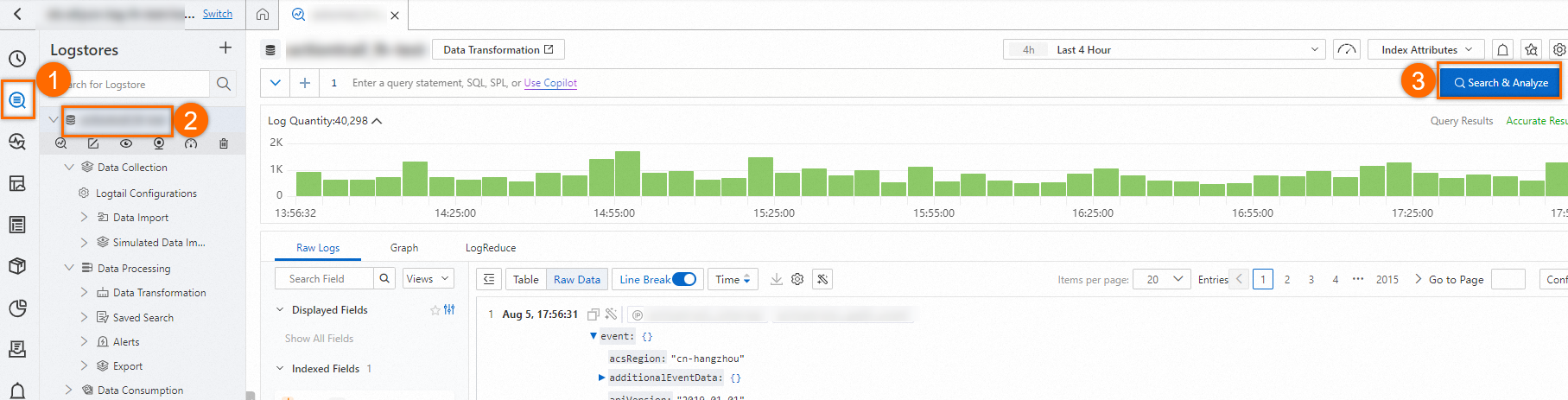
1. Configure a notification recipient
You can create users and user groups and specify them as the recipients of alert notifications.
1.1 Create a user
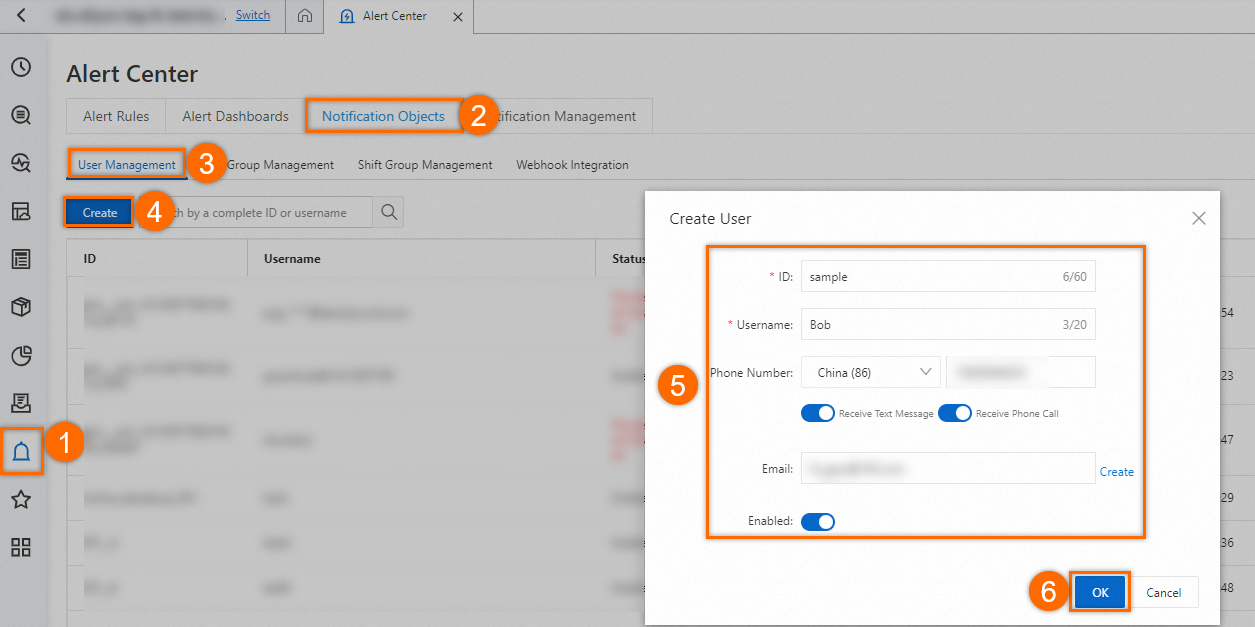
In the left-side navigation pane, click Alerts. On the Notification Objects tab of the Alert Center page, click the User Management tab and click Create. In the Create User dialog box, configure the parameters based on the following figure. For this example, set Username to Bob. Then, click OK.
1.2 Create a user group
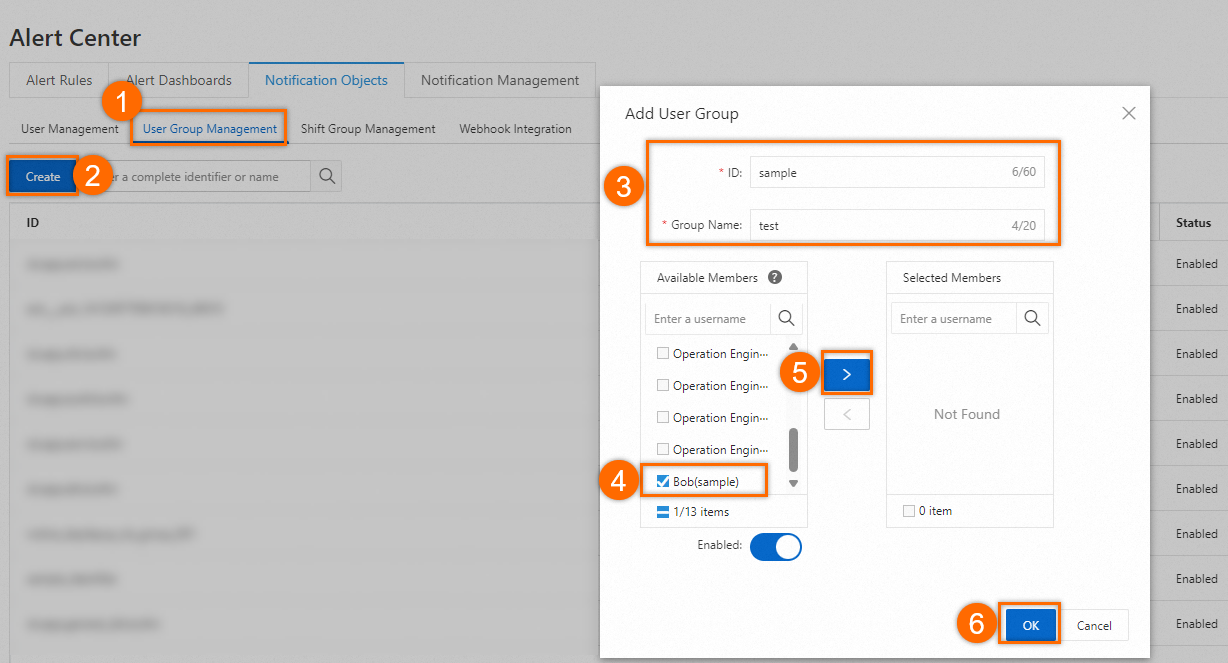
On the Notification Objects tab of the Alert Center page, click the User Group Management tab and click Create. In the Add User Group dialog box, add Bob to the test user group based on the following figure and click OK.
2. Configure an alert rule
Alert rules are used to monitor logs. In this example, an alert rule is configured to check whether a Logstore contains data at 15-minute intervals. If the Logstore contains data, an alert is triggered and an alert notification is sent to a DingTalk group.
2.1 Configure Query Statistics
On the page, click Create Alert.
In the Create Alert panel, find Query Statistics and click Create.
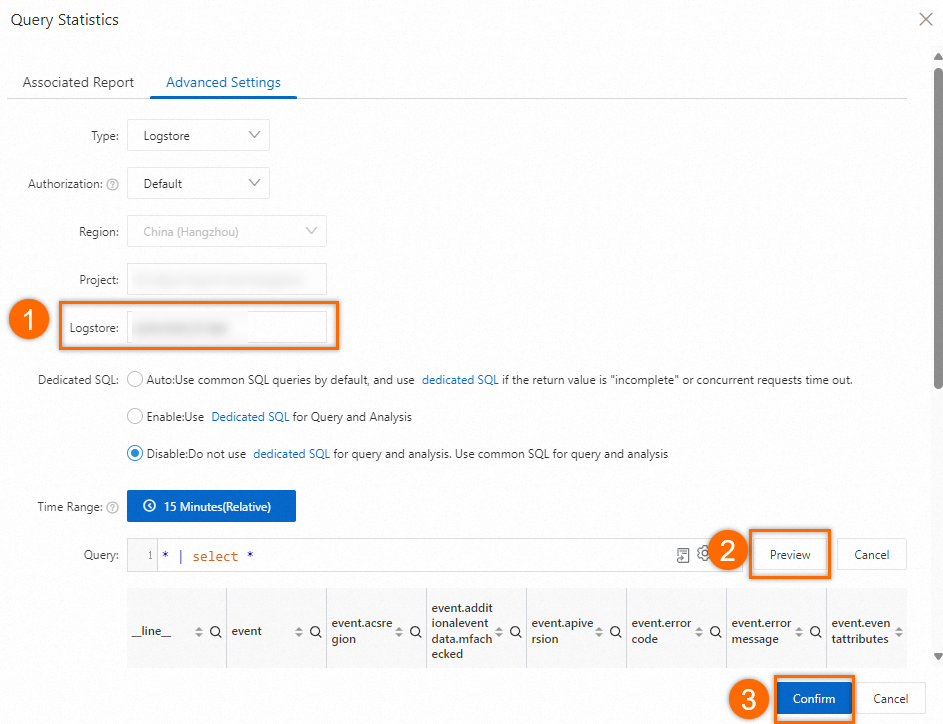
In the Query Statistics dialog box, select your Logstore from the Logstore drop-down list and click Preview to view the logs in the Logstore. Then, click Confirm.
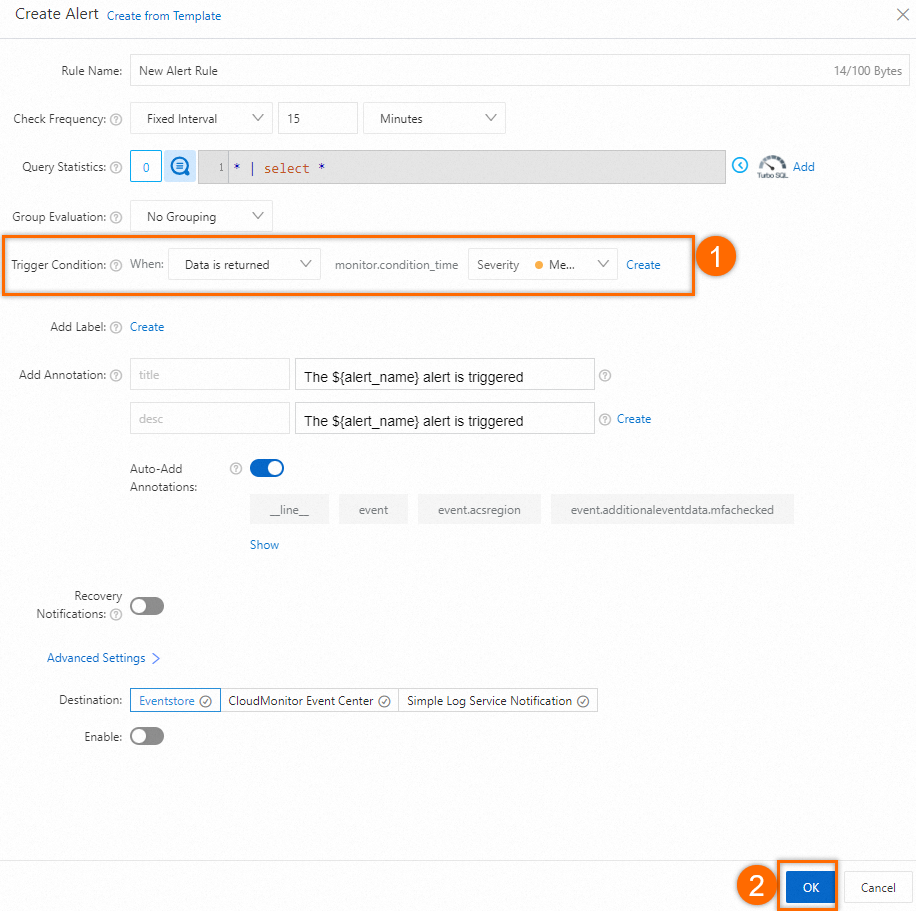
2.2 Configure Trigger Condition
In the Create Alert panel, set Trigger Condition to Data is returned and Severity to Medium. Then, click OK.
3. Configure a notification policy
3.1 Configure an alert template
Simple Log Service sends alert notifications based on the content that is specified in alert templates. For example, you can use the SLS built-in alert template to configure alert notifications by using DingTalk.
On the tab, find the SLS built-in alert template and click Edit in the Actions column.
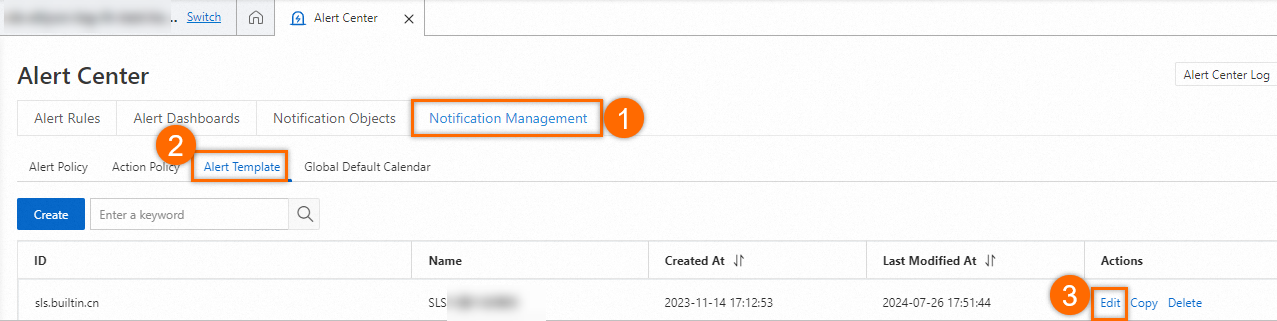
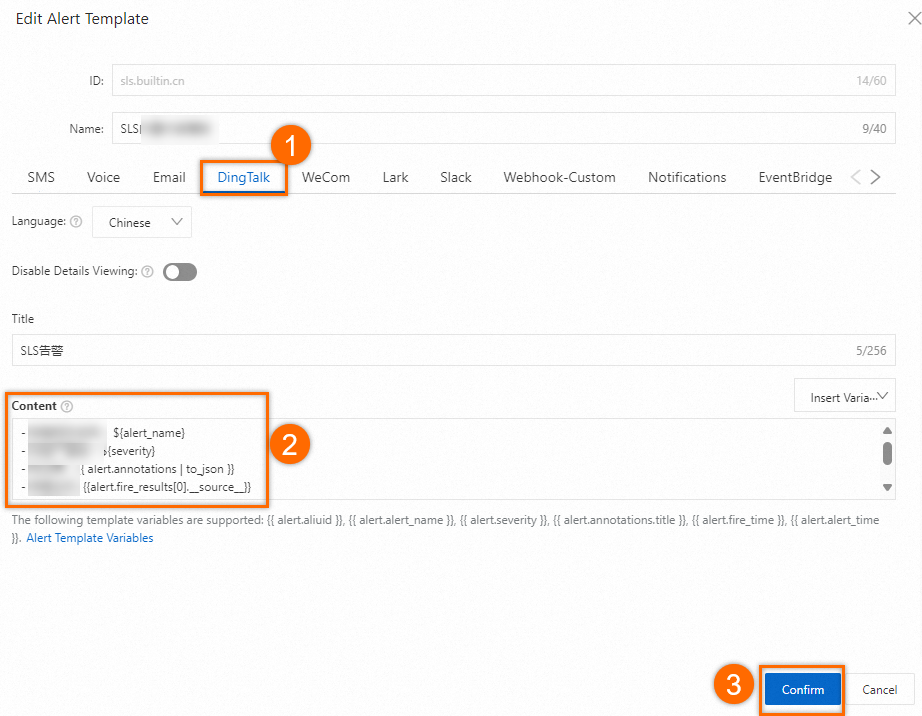
On the DingTalk tab of the Edit Alert Template dialog box, specify the content in the Content field.
3.2 Configure alert notification settings for Simple Log Service
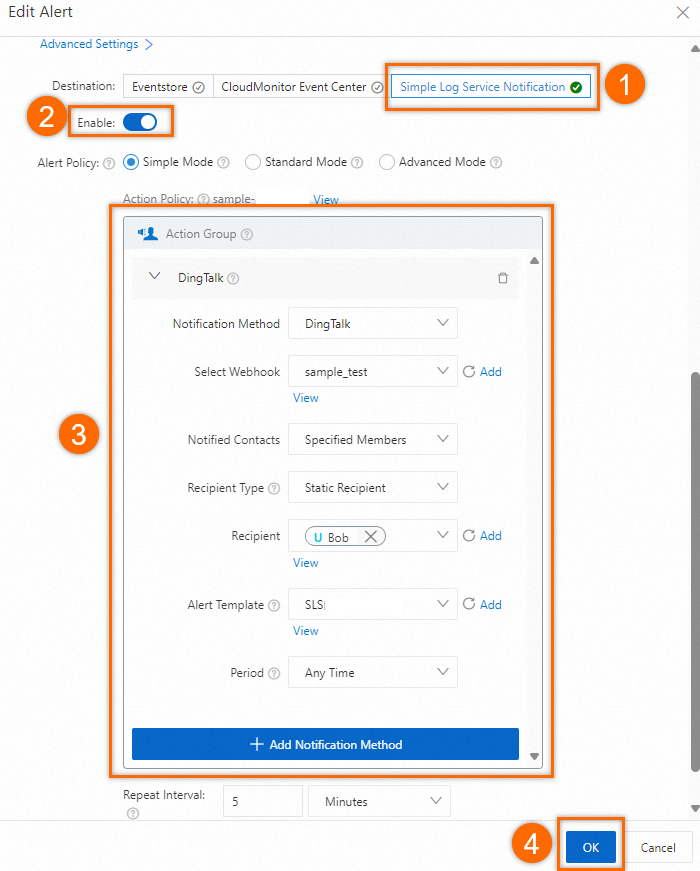
Simple Log Service sends alert notifications based on the alert notification method that you select. You can select a notification method when you set Destination to Simple Log Service Notification and Alert Policy to Simple Mode in the Advanced Settings section of the Create Alert panel. For example, you can set Notification Method to DingTalk. Then, Simple Log Service sends alert notifications by DingTalk.
Prerequisites
Before Simple Log Service can send alert notifications by using DingTalk, you must configure the following settings:
Create a DingTalk chatbot and set the message receiving mode of the chatbot to HTTP.
Open DingTalk and go to a DingTalk group. Click the Group Settings icon in the upper-right corner.
Choose .
Click Custom (Custom message services via Webhook). Then, click Add. Configure Chatbot name, set Security Settings to Custom Keywords and enter alert in the field below Custom Keywords, and then click Finished.
On the chatbot management page, view the created chatbot and copy the webhook URL of the chatbot.
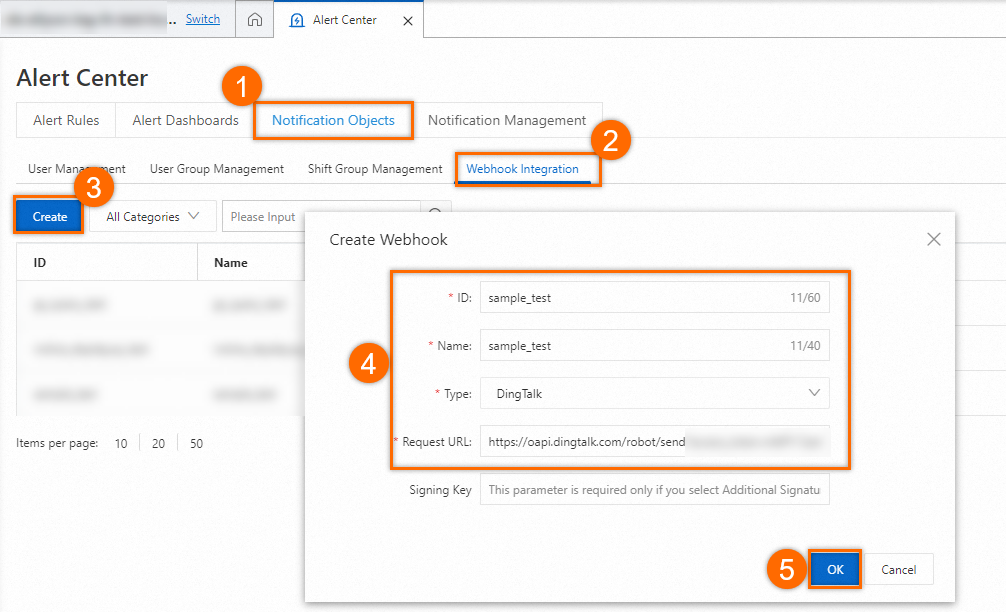
Configure a notification recipient
In the Create Webhook dialog box, specify the copied webhook URL for Request URL and configure other parameters based on the following figure. Then, click OK.
Configure an alert notification method
On the Alert Rules tab, select the alert rule that you created and click Edit in the Actions column.
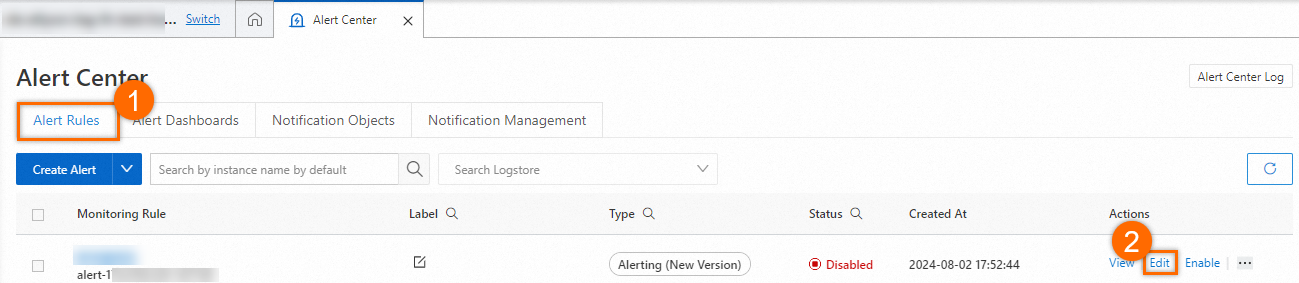
In the Edit Alert panel, configure the parameters based on the following figure and click OK.
View alert records
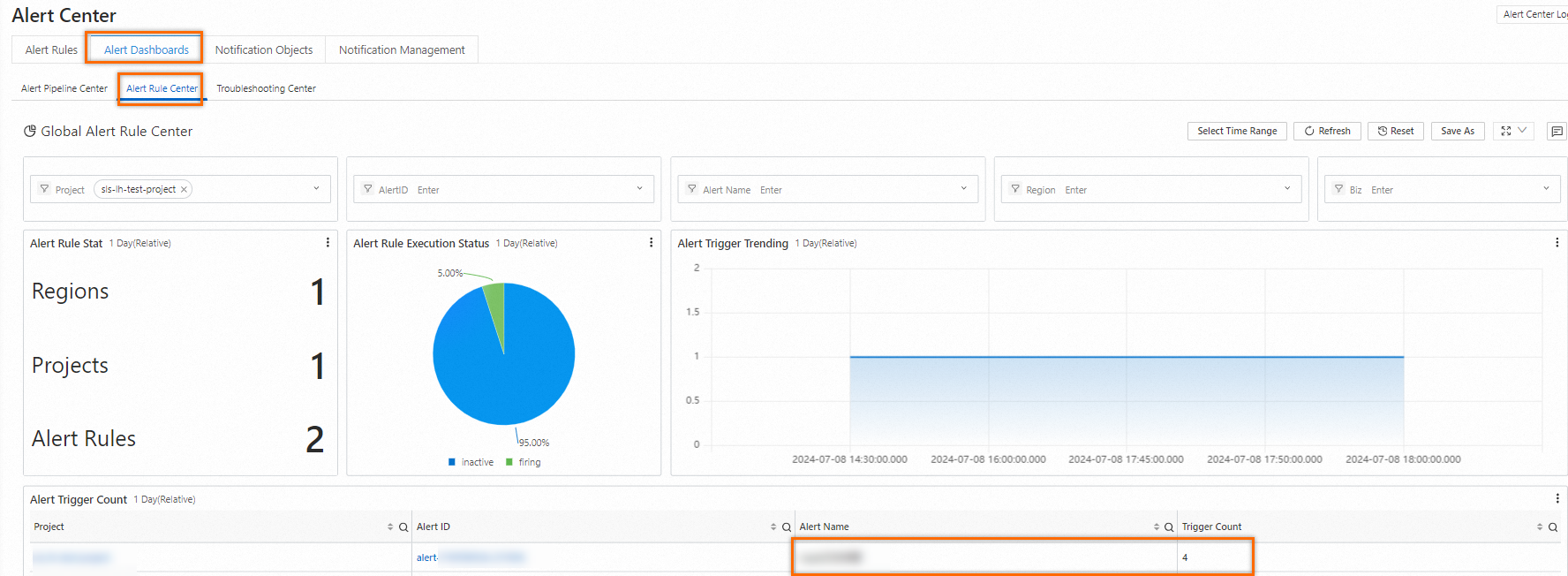
View the alert dashboard
On the page, view the number of times that alerts are triggered based on each alert rule.
View alert notification details
On the page, click the alert rule that you want to manage.
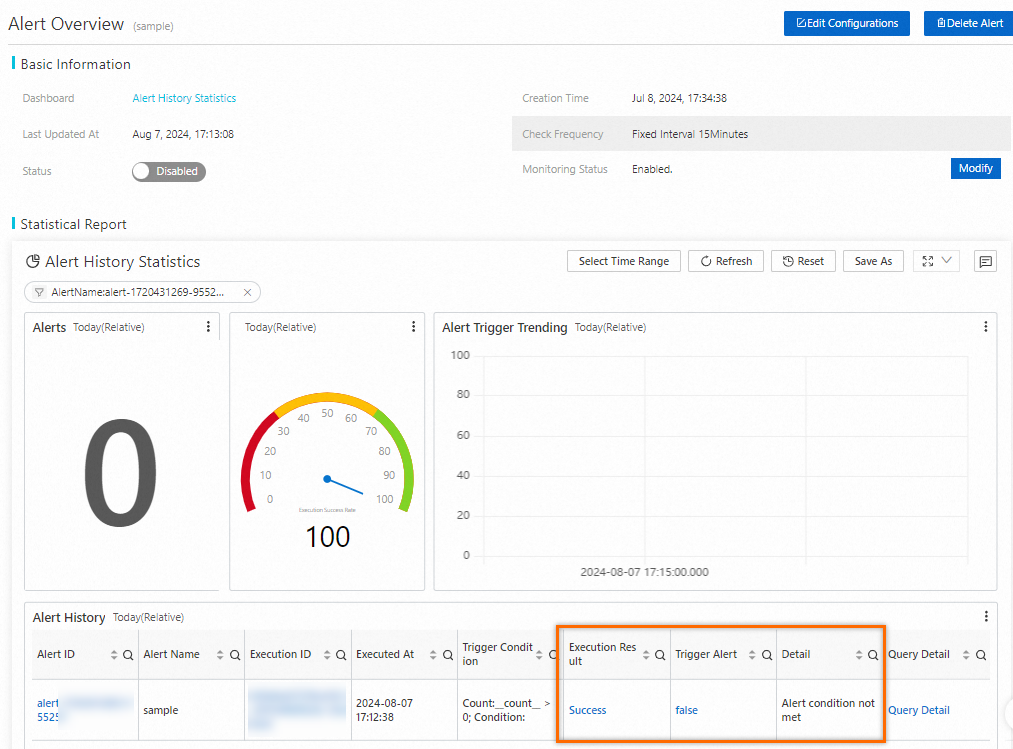
View alert details. If the value of Trigger Alert is true, alerts are triggered.
References
For more information about alert notification methods, see Notification methods.
You are charged for alert notifications only if the notifications are sent by text message or voice call. For more information, see Billing method.
For more information about alert attributes, see Alert attributes.
For more information about alert template variables, see Variables in alert templates (new version). For more information about how to create an alert template, see Create an alert template.