To monitor data across projects, regions, or Alibaba Cloud accounts based on an alert rule, Simple Log Service must assume a Resource Access Management (RAM) role to access the required Logstores or Metricstores. In this case, you must grant the required permissions to the RAM role.
Scenarios
Authorization method | Scenario |
Use the default authorization method | If you use an alert rule that is configured for a project to monitor data in different Logstores and Metricstores of the project, you can use the default authorization method. |
Use a built-in role | If you use an alert rule that is configured for a project to monitor data in the Logstores and Metricstores of a different project within the same Alibaba Cloud account, you can assign a built-in role to Simple Log Service. |
Use a custom role | If you use an alert rule to monitor data across Alibaba Cloud accounts, you can assign a custom role to Simple Log Service. In this case, you can grant fine-grained permissions to the RAM role. |
Step 1: Configure authorization
Specify a query statement. For more information, see Create an alert rule.
Configure an authorization method.
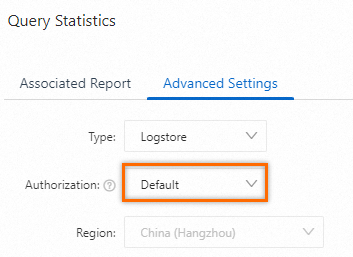
Use the default authorization method
If you use an alert rule that is configured for a project to monitor data in different Logstores and Metricstores of the project, you can use the default authorization method.
On the Advanced Settings tab, select Default from the Authorization drop-down list.
Use a built-in role
If you use an alert rule to monitor data in different Logstores and Metricstores across multiple projects within an Alibaba Cloud account, you can assign a built-in role to Simple Log Service.
On the Advanced Settings tab, select Built-in Role from the Authorization drop-down list. If this is your first time to configure authorization, you must use an Alibaba Cloud account to complete authorization on the Cloud Resource Access Authorization page. For more information, see Cloud Resource Access Authorization. After the authorization is complete, Simple Log Service creates a RAM role named
AliyunSLSAlertMonitorRole. Then, Simple Log Service can assume the RAM role to read data from the specified Logstores.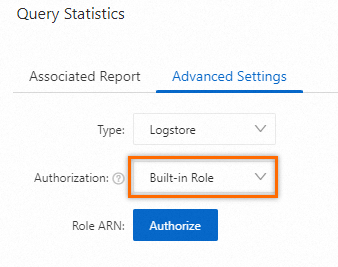
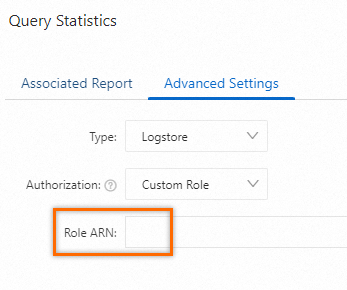
Use a custom role (within an Alibaba Cloud account)
If you use an alert rule to monitor data in different Logstores or Metricstores across multiple projects within an Alibaba Cloud account, you can assign a custom role to Simple Log Service.
Create a RAM role whose trusted entity is an Alibaba Cloud service. Select Log Service from the Select Trusted Service drop-down list. For more information, see Create a RAM role for a trusted Alibaba Cloud service.
Create a custom policy. On the JSON tab of the Create Policy page, replace the existing script in the code editor with the following policy document. For more information, see Create a custom policy on the JSON tab.
ImportantReplace Project name based on your business requirements. You can modify the custom policy to grant fine-grained permissions to the RAM role. For example, if you want to grant the role the permissions to create an alert rule only in a specific project, you can specify the project in the
Resourceelement of the custom policy. Example:acs:log:*:*:project/my-project.{ "Statement": [ { "Action": [ "log:ListProject" ], "Effect": "Allow", "Resource": [ "acs:log:*:*:*" ] }, { "Action": [ "log:ListLogStores", "log:GetLogStoreLogs", "log:GetIndex" ], "Effect": "Allow", "Resource": [ "acs:log:*:*:project/Project name/*" ] } ], "Version": "1" }Attach the created custom policy to the RAM role. For more information, see Grant permissions to a RAM role.
What to do next
Obtain the Alibaba Cloud Resource Name (ARN) of the RAM role. For more information, see View the information about a RAM role.
Enter the ARN of the RAM role to assign the role to Simple Log Service. For more information, see Create an alert rule.
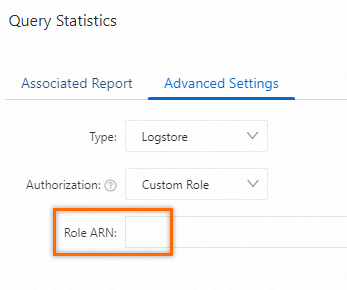
Use a custom role (across multiple Alibaba Cloud accounts)
If you use an alert rule to monitor data in different Logstores or Metricstores across multiple Alibaba Cloud accounts, you can assign a custom role to Simple Log Service. For example, you can use Alibaba Cloud Account A to create an alert rule and use the alert rule to monitor data in the Logstores or Metricstores of Alibaba Cloud Account B.
Use Alibaba Cloud Account B to perform the following operations:
Create a RAM role whose trusted entity is an Alibaba Cloud service. Select Log Service from the Select Trusted Service drop-down list. For more information, see Create a RAM role for a trusted Alibaba Cloud service.
Modify the trust policy of the RAM role. For more information, see Edit the trust policy of a RAM role.
ImportantReplace
ID of Alibaba Cloud Account Abased on your business requirements. You can view the ID of your Alibaba Cloud account in the account center.{ "Statement": [ { "Action": "sts:AssumeRole", "Effect": "Allow", "Principal": { "Service": [ "ID of Alibaba Cloud Account A@log.aliyuncs.com", "log.aliyuncs.com" ] } } ], "Version": "1" }Create a custom policy. On the JSON tab of the Create Policy page, replace the existing script in the code editor with the following policy document. For more information, see Create a custom policy on the JSON tab.
ImportantReplace the existing script in the code editor with the following policy document. Replace Project name based on your business requirements. You can modify the custom policy to grant fine-grained permissions to the RAM role. For example, if you want to grant the role the permissions to create an alert rule only in a specific project, you can specify the project in the
Resourceelement of the custom policy. Example:acs:log:*:*:project/my-project.{ "Statement": [ { "Action": [ "log:ListProject" ], "Effect": "Allow", "Resource": [ "acs:log:*:*:*" ] }, { "Action": [ "log:ListLogStores", "log:GetLogStoreLogs", "log:GetIndex" ], "Effect": "Allow", "Resource": [ "acs:log:*:*:project/Project name/*" ] } ], "Version": "1" }Attach the created custom policy to the RAM role. For more information, see Grant permissions to a RAM role.
Obtain the Alibaba Cloud Resource Name (ARN) of the RAM role. For more information, see View the information about a RAM role.
What to do next
Obtain the Alibaba Cloud Resource Name (ARN) of the RAM role. For more information, see View the information about a RAM role.
When you use Alibaba Cloud Account A to create an alert rule, select Custom Role from the Authorization drop-down list and enter the ARN of the RAM role that is created for Alibaba Cloud Account B. For more information, see Create an alert rule.
Step 2: Grant permissions to a RAM user
After you assign a built-in or custom role to Simple Log Service, you must use your Alibaba Cloud account to attach the following policy to the RAM user that you want to use to query data in Metricstores or Logstores. For more information, see Grant permissions to a RAM user.
{
"Action": "ram:PassRole",
"Effect": "Allow",
"Resource": "acs:ram::ID of Alibaba Cloud Account:Role ARN"
}