An Alibaba Cloud account has full operation permissions on all resources within the account. To ensure data security and implement fine-grained access control, you can create different Resource Access Management (RAM) users and attach system policies and custom policies to the RAM users. This topic describes how to authorize a RAM user to access Key Management Service (KMS) resources.
Prerequisites
RAM users are created. For information about how to create a RAM user, see Create a RAM user.
Attach system policies to a RAM user
Alibaba Cloud provides the following system policies for KMS resources. You can attach the policies to RAM users based on your business requirements. If the system policies cannot meet your business requirements, you can configure custom policies. For more information, see Attach custom policies to a RAM user.
System policies:
AliyunKMSFullAccess: full permissions on KMS resources
AliyunKMSReadOnlyAccess: the read-only permission on KMS resources
AliyunKMSCryptoAdminAccess: the permission to manage keys in KMS
AliyunKMSCryptoUserAccess: the permission to use KMS keys for cryptographic operations
AliyunKMSSecretUserAccess: the permission to retrieve secrets in KMS
AliyunKMSSecretAdminAccess: the permission to manage secrets in KMS
Log on to the RAM console by using your Alibaba Cloud account.
In the left-side navigation pane, choose .
On the Users page, find the RAM user and click Add Permissions in the Actions column.
In the Add Permissions panel, configure Authorized Scope and Principal.
Parameter
Description
Grant Permission On
The scope in which you want the permissions to take effect. KMS does not support the resource group feature. You must select Alibaba Cloud Account.
Principal
The RAM user to which you want to grant permissions. The Principal parameter is automatically set to a specific RAM user. You can specify a different RAM user.
Click System Policy, select system policies based on your business requirements, and then click OK.
Confirm the scope and policies for authorization and click Complete.
Attach custom policies to a RAM user
If the system policies cannot meet your business requirements, you can configure custom policies to implement fine-grained access control.
Log on to the RAM console with your Alibaba Cloud account.
Create a custom policy.
In the left-side navigation pane, choose .
On the Policies page, click Create Policy.
On the Create Policy page, click the JSON tab.
NoteRAM provides visual editing and document editing modes to create policies. When you create a custom policy for KMS resources, you must use the document editing mode. If you use the visual editing mode, you can select only all KMS resources and all operations.
Edit the policy document and click Next to edit policy information.
When you edit a KMS policy document, you must specify a custom authorization statement. A statement contains the following elements: Effect, Action, Resource, and Condition. The Condition element is optional. For more information, see RAM policies defined for KMS resources and Examples of RAM policies.
NoteFor more information about the syntax and structure of RAM policies, see Policy structure and syntax.
Specify the policy name and description. Then, check and optimize the policy document as prompted.
Click OK.
Attach custom policies to a RAM user.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user and click Add Permissions in the Actions column.
In the Add Permissions panel, configure Authorized Scope and Principal.
Parameter
Description
Grant Permission On
The scope in which you want the permissions to take effect. KMS does not support the resource group feature. You must select Alibaba Cloud Account.
Principal
The RAM user to which you want to grant permissions. The Principal parameter is automatically set to a specific RAM user. You can specify a different RAM user.
Click Custom Policy, select custom policies based on your business requirements, and then click OK.
Confirm the scope and policies for authorization and click Complete.
RAM policies defined for KMS resources
Resource
KMS defines the following resource types: key container, secret container, alias container, certificate container, key, secret, alias, and certificate. You can configure the Resource element in a RAM policy based on the Alibaba Cloud Resource Name (ARN) of your resource. To obtain the ARN of a resource, perform the following steps:
Log on to the KMS console. In the top navigation bar, select the required region. In the left-side navigation pane, click Keys.
On the Keys tab, find the key whose ARN you want to obtain and click Details in the Actions column. On the details page, you can view the ARN of the key.
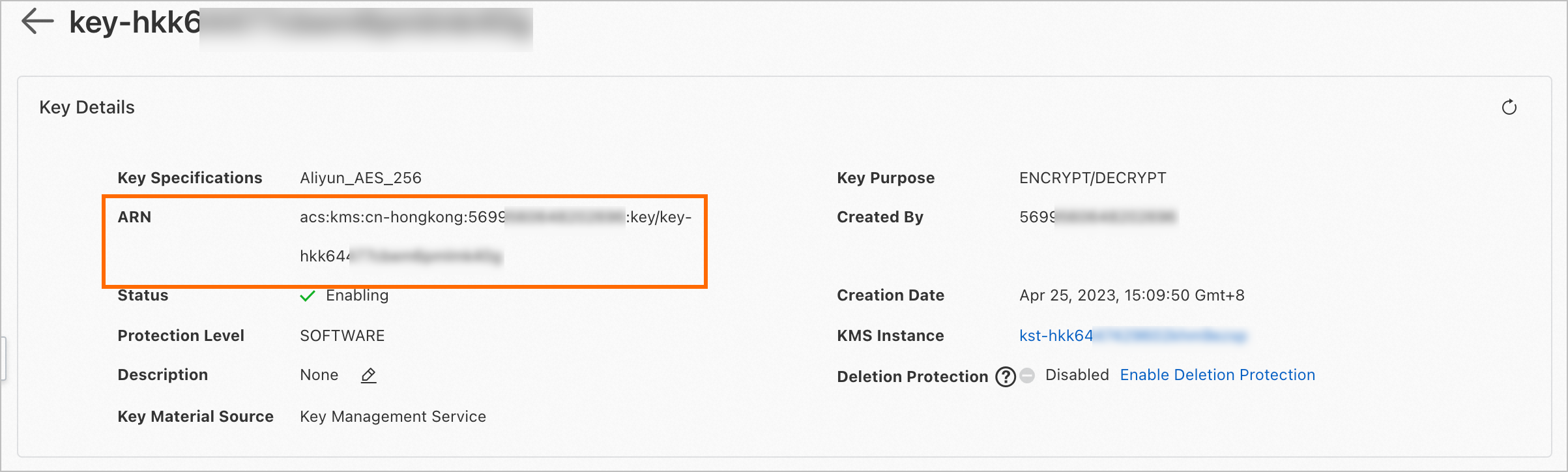 The following table describes the ARN formats for different resource types.
The following table describes the ARN formats for different resource types. Resource type
ARN
Key container
acs:kms:${region}:${account}:key
Secret container
acs:kms:${region}:${account}:secret
Alias container
acs:kms:${region}:${account}:alias
Key
acs:kms:${region}:${account}:key/${key-id}
NoteThe ARN of a key resource supports the wildcard character (*). Example:
acs:kms:${region}:${account}:key/*: specifies all keys in a region within an account.acs:kms:*:${account}:key/*: specifies all keys in all regions within an account.
Secret
acs:kms:${region}:${account}:secret/${secret-name}
NoteThe ARN of a secret resource supports the wildcard character (*).
acs:kms:${region}:${account}:secret/*: specifies all secrets in a region within an account.acs:kms:${region}:${account}:secret/prefix*: specifies all secrets that start withprefixin a region within an account.
Alias
acs:kms:${region}:${account}:alias/${alias-name}
Certificate
acs:kms:${region}:${account}:certificate/${id}
Action
KMS defines actions for each API operation that requires access control. In RAM policies, actions are in the kms:<api-name> format.
The DescribeRegions operation does not require access control. The operation can be called by Alibaba Cloud accounts, RAM users, or RAM roles after they pass RAM authentication.
The following tables describe the RAM actions and resource types that correspond to each API operation.
Key API operations
Operation
Action
Resource type
ARN
ListKeys
kms:ListKeys
Key container
acs:kms:${region}:${account}:key
CreateKey
kms:CreateKey
DescribeKey
kms:DescribeKey
Key
acs:kms:${region}:${account}:key/${key-id}
UpdateKeyDescription
kms:UpdateKeyDescription
EnableKey
kms:EnableKey
DisableKey
kms:DisableKey
ScheduleKeyDeletion
kms:ScheduleKeyDeletion
CancelKeyDeletion
kms:CancelKeyDeletion
GetParametersForImport
kms:GetParametersForImport
ImportKeyMaterial
kms:ImportKeyMaterial
DeleteKeyMaterial
kms:DeleteKeyMaterial
ListAliasesByKeyId
kms:ListAliasesByKeyId
CreateKeyVersion
kms:CreateKeyVersion
DescribeKeyVersion
kms:DescribeKeyVersion
ListKeyVersions
kms:ListKeyVersions
UpdateRotationPolicy
kms:UpdateRotationPolicy
Encrypt
kms:Encrypt
Decrypt
kms:Decrypt
ReEncrypt
kms:ReEncryptFrom
kms:ReEncryptTo
kms:ReEncrypt*
GenerateDataKey
kms:GenerateDataKey
GenerateDataKeyWithoutPlaintext
kms:GenerateDataKeyWithoutPlaintext
ExportDataKey
kms:ExportDataKey
GenerateAndExportDataKey
kms:GenerateAndExportDataKey
AsymmetricSign
kms:AsymmetricSign
AsymmetricVerify
kms:AsymmetricVerify
AsymmetricEncrypt
kms:AsymmetricEncrypt
AsymmetricDecrypt
kms:AsymmetricDecrypt
GetPublicKey
kms:GetPublicKey
ListAliases
kms:ListAliases
Alias container
acs:kms:${region}:${account}:alias
CreateAlias
kms:CreateAlias
Alias and key
Alias: acs:kms:${region}:${account}:alias/${alias-name}
Key: acs:kms:${region}:${account}:key/${key-id}
UpdateAlias
kms:UpdateAlias
DeleteAlias
kms:DeleteAlias
Secrets Manager API operations
Operation
Action
Resource type
ARN
CreateSecret
kms:CreateSecret
Secret container
acs:kms:${region}:${account}:secret
ListSecrets
kms:ListSecrets
DescribeSecret
kms:DescribeSecret
Secret
acs:kms:${region}:${account}:secret/${secret-name}
DeleteSecret
kms:DeleteSecret
UpdateSecret
kms:UpdateSecret
RestoreSecret
kms:RestoreSecret
GetSecretValue
kms:GetSecretValue
kms:Decrypt
NoteThe permissions on kms:Decrypt are required only when a self-managed key is specified as the encryption key for a generic secret.
PutSecretValue
kms:PutSecretValue
kms:GenerateDataKey
NoteThe permissions on kms:GenerateDataKey are required only if a self-managed key is specified as the encryption key for a generic secret.
ListSecretVersionIds
kms:ListSecretVersionIds
UpdateSecretVersionStage
kms:UpdateSecretVersionStage
GetRandomPassword
kms:GetRandomPassword
None
None
Certificates Manager API operations
Operation
Action
Resource type
ARN
CreateCertificate
kms:CreateCertificate
Certificate
acs:kms:${region}:${account}:certificate/${id}
UploadCertificate
kms:UploadCertificate
GetCertificate
kms:GetCertificate
DescribeCertificate
kms:DescribeCertificate
UpdateCertificateStatue
kms:UpdateCertificateStatue
DeleteCertificate
kms:DeleteCertificate
CertificatePrivateKeySign
kms:CertificatePrivateKeySign
CertificatePublicKeyVerify
kms:CertificatePublicKeyVerify
CertificatePublicKeyEncrypt
kms:CertificatePublicKeyEncrypt
CertificatePrivateKeyDecrypt
kms:CertificatePrivateKeyDecrypt
Tag management API operations
Operation
Action
Resource type
ARN
ListResourceTags
kms:ListResourceTags
Key
Key: acs:kms:${region}:${account}:key/${key-id}
Secret: acs:kms:${region}:${account}:secret/${secret-name}
UntagResource
kms:UntagResource
Key or secret
TagResource
kms:TagResource
Condition
The Condition element specifies the conditions that are required for a policy to take effect. This element is optional. You can add a condition key in RAM policies to control access to KMS. RAM authentication is successful only if the added conditions are met.
Use common condition keys: The condition key is in the
acs:<condition-key>format. For example, you can useacs:CurrentTimeto control the time period when a RAM policy is valid.For more information, see Policy elements.
Use tags as condition keys: The condition key is in the
kms:tag/<tag-key>format. You can use tags as condition keys to limit the use of cryptographic API operations, such as Encrypt, Decrypt, and GenerateDataKey.To query the tags of a key, you can use one of the following methods:
Use the KMS console
Log on to the KMS console. In the top navigation bar, select the required region. In the left-side navigation pane, click Keys.
On the Keys page, click the Software Key Management tab or Hardware Key Management tab based on the type of your KMS instance.
Click the name of the required instance. On the page that appears, find the key whose tags you want to view.
Click the name of the key. In the Tag section, view the tag keys and tag values of the key.
Call the ListResourceTags operation
Examples of RAM policies
Scenario | Policy document |
Access all KMS resources | Important To ensure data security, we recommend that you do not configure RAM policies that allow access to all KMS resources. |
Access all KMS resources from specified CIDR blocks or IP addresses | In the sample code, the CIDR block 192.168.0.0/16 and the IP address 172.16.215.218 are used. |
Query keys and use keys to encrypt data, decrypt data, and generate data keys | Note Replace |
Perform envelope encryption and envelope decryption, and generate data keys by using keys that have specified tags. | In the sample code, a tag whose tag key is Note Replace |
Query secrets and read the attributes of the secrets | Note Replace |
Query values of a secret by secret name | In the sample code, the example-secret secret encrypted by using a key whose ID is keyId-example is used. Note Replace |
Sign data and verify digital signatures by using specified certificates | |