Dedicated Key Management Service (KMS) of the Standard edition supports user-side data encryption and encryption for hardware security module (HSM) clusters in Data Encryption Service. Dedicated KMS stores keys in your dedicated HSM cluster and supports native encryption capabilities of Alibaba Cloud services. Dedicated KMS of the Standard edition provides an optional component named Secrets Manager. You can use Secrets Manager to manage your secrets during their lifecycle and configure applications for access in a secure and efficient manner.
Scenarios
- Self-managed application integration
You can connect self-managed applications to your dedicated KMS instance of the Standard edition over a virtual private cloud (VPC). Then, you can encrypt and decrypt data at the application layer by using the capabilities provided by the instance.
- Third-party ISV application integration
Applications that are provided by third-party independent software vendors (ISVs) can call the cryptographic operations of a dedicated KMS instance of the Standard edition.
- Secrets management
You can manage and encrypt secrets to prevent your information and valuable assets from being leaked due to hard coded secrets. This helps improve application data security.
- Cloud service integration
You can authorize KMS to forward server-side encryption requests from cloud services to Dedicated KMS of the Standard edition.
Benefits
- Dedicated KMS of the Standard edition allows you to deploy a tenant-specific instance in the VPC of the tenant. This way, Dedicated KMS is accessible over the VPC.
- Dedicated KMS of the Standard edition uses a tenant-specific cryptographic resource pool to implement resource isolation and cryptographic isolation. This helps improve security. The resource pool is also called an HSM cluster.
- Dedicated KMS of the Standard edition provides stable, easy-to-use upper-layer key management features and cryptographic operations to simplify the management of HSMs.
- Dedicated KMS of the Standard edition allows you to seamlessly integrate your HSMs into Alibaba Cloud services. This way, the data encryption of Alibaba Cloud services becomes more secure and manageable. For more information, see Alibaba Cloud services that can be integrated with KMS.
Architecture
Dedicated KMS of the Standard edition is independently deployed and is offered as instances. The following figure shows the architecture of Dedicated KMS of the Standard edition.
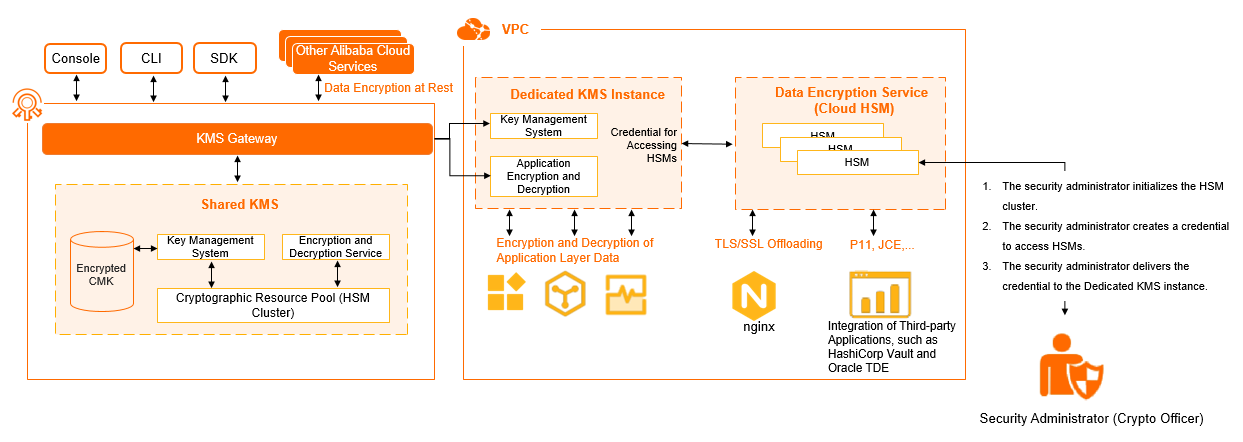
Dedicated KMS includes the following components:
- Cryptographic resource pool
A cryptographic resource pool refers to a tenant-specific HSM cluster that can be managed in Data Encryption Service. The HSM cluster is a group of security devices that are used for key storage and cryptographic operations.
For more information about Data Encryption Service, see Data Encryption Service.
- Key management system
The key management system allows you to manage the lifecycle of keys in your custom dedicated HSM cluster.
- Cryptographic operation service
Dedicated KMS of the Standard edition provides an easy-to-use API to allow you to schedule cryptographic operations. The keys that are used during cryptographic operations must be stored in an HSM cluster.
- Secrets Manager (optional for purchase)
Dedicated KMS of the Standard edition provides Secrets Manager to allow you to manage your secrets during their lifecycle, and configures applications for access in a secure and efficient manner. This helps prevent your information from being leaked due to hard coded secrets.
Limits
| Item | Upper limit |
|---|---|
| The maximum number of customer master keys (CMKs) that can be created for an instance | 1,000 |
| The maximum number of secrets that can be created for an instance | 10,000,000 |
| The maximum queries per second (QPS) that is supported by an instance | 2,000 |
Supported region
Dedicated KMS of the Standard edition is available in the following regions: China (Hangzhou), China (Shanghai), China (Beijing), China (Shenzhen), China (Hong Kong), Malaysia (Kuala Lumpur), and Singapore (Singapore).
Billing
Dedicated KMS of the Standard edition uses the subscription billing method. For more information, see Billing of Dedicated KMS.