You can grant required permissions to RAM users to follow the principle of least privilege and prevent multiple users from sharing your Alibaba Cloud account or AccessKey pair. This helps reduce access security risks for enterprises. This topic describes how to grant permissions to RAM users by using your Alibaba Cloud account and describes each permission.
Background
Resource Access Management (RAM) is a permission management system provided by Alibaba Cloud.
RAM is used to control the permissions of accounts.
You can create RAM users within your Alibaba Cloud account and grant them different permissions on Hologres. For example, you can grant RAM users the permissions to purchase or delete instances, upgrade or downgrade instance specifications, change the network types of instances, and view instance details.
A RAM user must take note of the following items:
To view or manage instances in the Hologres console, they need relevant permissions granted by the Alibaba Cloud account.
The development permissions on a Hologres instance allows for using development tools to develop data, even if they cannot manage instances in the Hologres console. For more information, see Grant the development permissions on a Hologres instance to a RAM user.
Grant permissions on Hologres to a RAM user
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
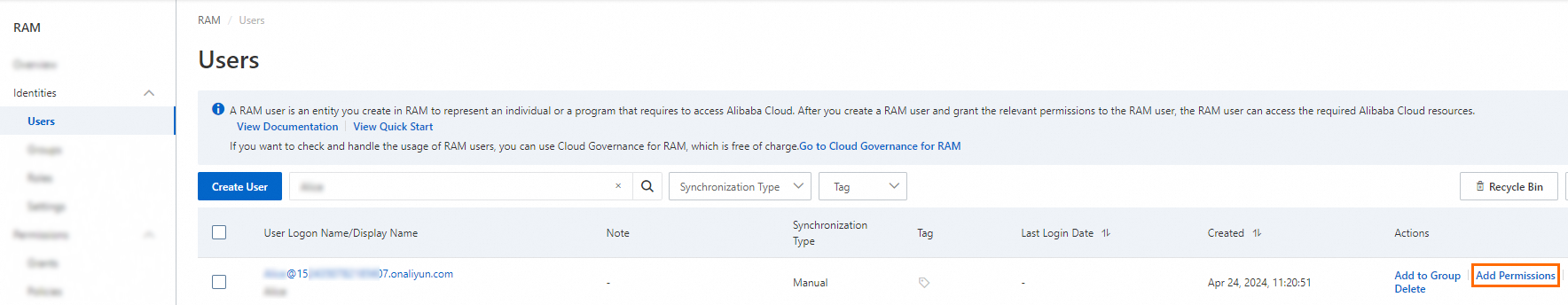
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
Grant permissions to the RAM user.
In the Add Permissions panel, configure the parameters that are described in the following section.
NoteLogging on to and using HoloWeb via a resource group are not supported because HoloWeb does not belong to a resource group.
This section covers granting permissions on HoloWeb. To manage Hologres instance permissions, go to the instance details page for authorization. For more information, see Grant the development permissions on a Hologres instance to a RAM user.
Set Resource Scope.
Account: The authorization takes effect on the current Alibaba Cloud account.
ResourceGroup: The authorization takes effect for a specific resource group.
ImportantIf you select ResourceGroup for the Resource Scope parameter, ensure your cloud service and resource type support resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Set Principal.
Select a RAM user to grant permissions. The current RAM user is automatically selected.
Set Policy.
A policy contains a set of permissions. Policies can be system or custom policies. You can select multiple policies at a time.
System policies: policies created and managed by Alibaba Cloud. You can use but cannot modify these policies. For more information, see Services that work with RAM.
NoteRAM tags high-risk system policies, such as
AdministratorAccessandAliyunRAMFullAccess. Grant these policies cautiously.The following table describes the system policies of Hologres. Attaching a system policy to a RAM user grants them all the permissions defined in the policy.
Policy
Description
AliyunHologresFullAccessGrants full access to managing Hologres.
NoteFor a RAM user to use an instance, a superuser must add a user in HoloWeb and maps the user to a RAM identity. For more information, see FAQ about permissions on using instances.
Permissions include:
View instances, instance details, and metrics.
Perform operations that incur costs, such as creating, renewing, stopping, deleting, and scaling instances.
Log on to and use the HoloWeb console.
Take note of the following:
An instance creator automatically becomes the instance's superuser with all permissions on the instance. An Alibaba Cloud account is a superuser of all instances within the account.
To access data in an instance created by an Alibaba Cloud account, a RAM user must be granted data development permissions by the Alibaba Cloud account in the Hologres instance. See Grant the development permissions on a Hologres instance to a RAM user.
To query all user permissions on the page in the HoloWeb console, a RAM user needs the
AliyunRAMReadOnlyAccesspolicy (which includes theListUserpermission).
AliyunHologresWarehouseFullAccessGrants full access to managing Hologres virtual warehouses.
NoteFor a RAM user to use an instance, a superuser must add a user in HoloWeb and maps the user to a RAM identity. For more information, see FAQ about permissions on using instances.
This policy includes the following permissions:
Create, delete, scale, scale, stop, and restore virtual warehouses.
Schedule scaling.
Log on to and use the HoloWeb console.
AliyunBSSOrderAccessGrants permissions to view, pay for, and cancel orders in the Billing Management console.
Attaching this policy to a RAM user allows it to scale and renew instances in the Hologres console.
AliyunRAMReadOnlyAccessGrants read-only permissions on RAM.
Attaching this policy to a RAM user allows it to list RAM identities in the account when adding users on the page in the HoloWeb console.
AliyunHologresReadOnlyAccessGrants read-only permissions on Hologres.
This policy includes the following permission set:
List instances and view instance details information in the Hologres console.
Connect to and use HoloWeb.
It does not include the following permissions:
Perform operations that incur charges, such as creating and scaling instances.
Perform operations on instances.
List RAM identities within the Alibaba Cloud account.
NoteThe creator of a Hologres instance automatically becomes its superuser. Additionally, an Alibaba Cloud account is a superuser for all instances within that account.
For instances created by an Alibaba Cloud account, RAM users must obtain necessary permissions from the account to use the instance.
Custom policies: policies managed and updated by you. For more information, see Create custom policies.
ImportantWhen assigning custom policies to a RAM user, ensure you attach at least the
AliyunRAMReadOnlyAccesspolicy. This is necessary for the RAM user to access the Hologres console.In the RAM console, navigate to and click Create Policy. On the Create Policy page, switch to the JSON tab, and configure the custom policy in the code editor. For more information, see Create custom policies.
Example:
ImportantDelete the comments from the following sample code before you run the code.
{ "Statement": [ { // Perform all operations. If you enter this configuration, you do not need to enter the following configurations. "Effect": "Allow", "Action": "hologram:*",// The permissions to perform all operations. "Resource": "acs:hologram:*:<Alibaba Cloud account ID>:instance/*"// The permissions apply to all instances in all regions. <The asterisk (*) cannot be replaced with an instance ID.> }, { // Allow the user to perform any action on any Hologres instance in a region. "Effect": "Allow", "Action": "hologram:*", "Resource": "acs:hologram:cn-<region >:<Alibaba Cloud account ID>:instance/*" }, { // Delete instances. "Effect": "Allow", "Action": "hologram:DeleteInstance", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Create instances. "Effect": "Allow", "Action": "bss:PayOrder", "Resource": "acs:hologram:cn-<region >:<Alibaba Cloud account ID>:instance/*" }, { // View instance details. "Effect": "Allow", "Action": "hologram:GetInstance", "Resource": "acs:hologram:cn-<region >:<Alibaba Cloud account ID>:instance/*" //<The asterisk (*) can be replaced with an instance ID.> }, { // View the instance list. "Effect": "Allow", "Action": "hologram:ListInstances", "Resource": "acs:hologram:cn-<region >:<Alibaba Cloud account ID>:instance/*"//<The asterisk (*) cannot be replaced with an instance ID.> }, { // Stop instances. "Effect": "Allow", "Action": "hologram:StopInstance", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Resume instances. "Effect": "Allow", "Action": "hologram:ResumeInstance", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Change the network types of instances. "Effect": "Allow", "Action": "hologram:UpdateInstanceNetworkType", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }. { // Access HoloWeb. "Effect": "Allow", "Action": "hologram:HoloWebAccess", "Resource": "*" } ], "Version": "1" }The following table describes the parameters in the syntax.
Parameter
Description
<region>
The region in which the Hologres instance resides. Example: beijing.
<Alibaba Cloud account ID>
The ID of your Alibaba Cloud account.
*
The IDs of all Hologres instances within your Alibaba Cloud account. You can also replace the asterisk (*) with the ID of a specific Hologres instance.
Sample statement:
acs:hologram:cn-beijing:4322xxxxx:instance/hhhgggxxxxImportantThe asterisk (
*) ininstance/*in the following configurations cannot be replaced with a specific instance ID:{ "Statement": [ { // Perform all operations. If you enter this configuration, you do not need to enter the following configurations. "Effect": "Allow", "Action": "hologram:*",// The permissions to perform all operations. "Resource": "acs:hologram:*:<Alibaba Cloud account ID>:instance/*"// The permissions apply to all instances in all regions. }, { // Allow the user to perform any action on any Hologres instance in a resgion. "Effect": "Allow", "Action": "hologram:*", "Resource": "acs:hologram:cn-<region >:<Alibaba Cloud account ID>:instance/*" }, { // Delete instances. "Effect": "Allow", "Action": "hologram:DeleteInstance", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Create instances. "Effect": "Allow", "Action": "bss:PayOrder", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // View instances. "Effect": "Allow", "Action": "hologram:ListInstances", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Stop instances. "Effect": "Allow", "Action": "hologram:StopInstance", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Resume instances. "Effect": "Allow", "Action": "hologram:ResumeInstance", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // View monitoring metrics of instances. "Effect": "Allow", "Action": "cms:DescribeMetricList", "cms:QueryMetricList" "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" }, { // Change the network types of instances. "Effect": "Allow", "Action": "hologram:UpdateInstanceNetworkType", "Resource": "acs:hologram:cn-<region>:<Alibaba Cloud account ID>:instance/*" } ], "Version": "1" }
Click Grant permissions and click Close.
FAQ about permissions on the Hologres console
To access the Hologres console, a user needs necessary RAM and development permissions. There are answers to some frequently asked questions:
Why am I unable to view instances as a RAM user?
Symptom
A RAM user cannot view existing instances in a selected region, often with a message about missing the
hologram:ListInstancespermission.Cause
The RAM user lacks the required permissions to list instances in the Hologres console.
Solution
Log on to the RAM console using an Alibaba Cloud account and attach the AliyunHologresReadOnlyAccess policy to the RAM user.
Why am I unable to manage instances as a RAM identity with a superuser role?
Symptom
A RAM user with the superuser role cannot create or scale an instance, or convert the billing method from pay-as-you-go to subscription. An error message says: An error occured while performing RAM authorization.

Cause
Permissions on billing-related operations are controlled by Alibaba Cloud accounts. Without necessary permission granted, a RAM user cannot create or scale instances, or change the billing method.
Solution
Log on to the RAM console using an Alibaba Cloud account and attach the
AliyunHologresFullAccessorAliyunBSSOrderAccesspolicies to the RAM user.
FAQ about permissions on using instances
Why am I unable to connect to HoloWeb or use Hologres instances as a RAM user?
Symptom
You are unable to connect to and use Hologres instances as a RAM user, receiving an error message similar to:
role "<role_name>" does not exist.Cause
RAM users, other than the one who created the instance, are not automatically instance users. They need explicit permissions from a superuser (the instance creator or the Alibaba Cloud account) to access the instance.
Solutions
NoteTo view the superusers of the current instance, execute the
select * from pg_user;command.On in the HoloWeb console, add users and grant the required permissions to the users. For more information, see Manager users.
Connect to the instance and run the
create user "<role_name>"statement. For more information, see Overview.
Why am I unable to view any information on the User Management and Database Authorization page?
Symptom
When logging on as a RAM user, you cannot view information on the User Management and Database Authorization pages, and get an error message similar to
you do not have the permissions and need to ask the superuser to grant permissions on the instance to your account.Cause
The current RAM user does not have the development permissions on the instance.
Solution
Ask a superuser to grant you the development permissions. For more information, see Grant the development permissions on a Hologres instance to RAM users.
What do I do if I incorrectly delete superusers?
Symtom
All superusers in an instance are incorrectly changed to regular users.
WarningThis prevents you from performing user management and most instance-related operations.
Solution
Join the Hologres DingTalk group for technical support. For more information, see Obtain online support for Hologres.