Workbench is a web-based remote connection tool provided by Alibaba Cloud. Workbench operates within a browser to allow you to connect to an Elastic Compute Service (ECS) instance without the need for additional software. You can connect to an ECS instance by using the public or private IP address assigned to the instance and perform O&M operations on the instance. This topic describes how to connect to a Linux instance over SSH by using Workbench.
Preparations
Before you connect to a Linux ECS instance over SSH by using Workbench, complete the following preparations:
Check the instance status. You can connect to the ECS instance only when the instance is in the Running state.
Complete permission-related operations for using Workbench: If permission issues occur, contact the Alibaba Cloud account owner or an administrator to grant the required permissions on Workbench. For more information, see the Workbench service-linked role section of the "Connect to an instance through Workbench" topic.
Configure security groups to which the instance is assigned. Add security group rules to the security groups to allow the IP addresses related to Workbench to access the ECS instance. The security group rules vary based on the network type of the instance. For more information, see the Security group settings related to Workbench section of the "Connect to an instance through Workbench" topic.
If no security group is specified, you can specify a security group as prompted in the Instance Login dialog box of Workbench. You can configure a security group as prompted
Check whether Cloud Assistant Agent is installed on the instance. If you use temporary SSH key pair-based authentication to connect to the instance, you must install Cloud Assistant Agent on the instance to which you want to connect. For more information, see Install Cloud Assistant Agent.
Procedure
In this example, an ECS instance running Alibaba Cloud Linux 3 is used. By default, port 22 is used for an SSH connection to the instance. If you want to use another SSH port to connect to the instance, see the Specify the SSH port section of this topic.
By default, a Workbench session persists for 6 hours. If no operation is performed for more than 6 hours in the session, the session is closed and you must reconnect to the instance by using Workbench.
In the ECS console, find the instance to which you want to connect and go to the Instance Login dialog box of Workbench.
Go to ECS console - Instance.
In the top navigation bar, select the region and resource group of the resource that you want to manage.

Click the ID of the instance to which you want to connect. On the Instance Details page, click Connect in the upper-right corner.
In the Remote connection dialog box, click Sign in now in the Workbench section.
In the Instance Login dialog box, configure the parameters.
Configure basic information about the instance.
NoteBy default, Workbench uses the default SSH port (22) when you connect to a Linux instance. For information about how to change the SSH port, see the Specify the SSH port section of this topic.
Parameter
Description
Instance
The information of the current instance is automatically populated. You can also enter the IP address or the name of another instance.
Connection
To connect to an instance that resides in a virtual private cloud (VPC), use the public or private IP address of the instance.
If a public IP address is assigned to an instance in the classic network, you can use only the public IP address to connect to the instance. Otherwise, you can use the internal IP address to connect to the instance.
For information about different network types, see Overview of VPC and IP addresses of ECS instances in the classic network.
Select an authentication method in the Authentication field.
The following table describes the different authentication methods.
Authentication method
Description
Password-based
Enter a username, such as root or ecs-user, and the logon password.
If you bind an SSH key pair to the instance, we recommend that you use SSH key pair-based authentication.
SSH Key Authentication
Enter a username, such as root or ecs-user, and enter the content of the private key in the Private Key field. If a passphrase is specified for the private key file, you must enter the passphrase in the Passphrase for Private Key field.
Credential-based
Credential-based authentication allows you to save the username and password or username and key pair as credentials. If you select this authentication method, select a credential in the Credential field, without the need to enter the username, password, or key pair. For information about how to create a credential, see the Use credential-based authentication section of this topic.
Temporary SSH Key-based
Enter a username, such as root or ecs-user. By default, the root username is used.
This feature is implemented based on Cloud Assistant Agent. For more information, see the How temporary SSH key pair-based authentication works section of this topic.
After you specify the preceding parameters, click OK.
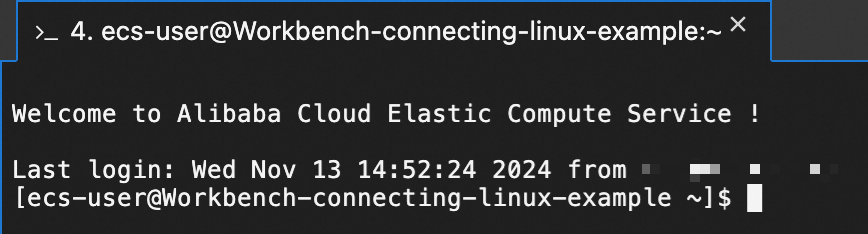
The following figure shows an example of a successful connection to the instance. If an error occurs during the connection, see the FAQ section of this topic.
More features
Specify the SSH port
To specify the SSH port, click More Options in the Instance Login dialog box, as shown in the following figure.
|
|
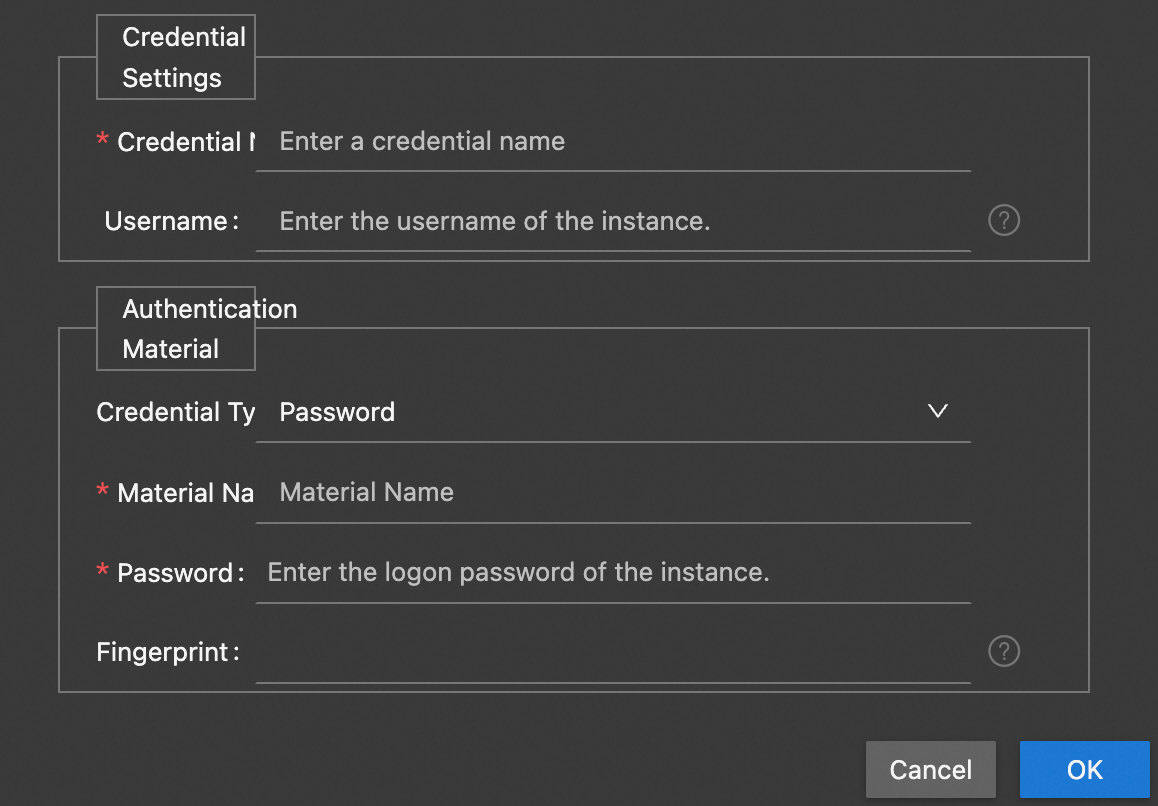
Use credential-based authentication
Credential-based authentication allows you to save the username and password or username and key pair as credentials. If you select this authentication method, select a credential in the Credential field, without the need to enter the username, password, or key pair. To create a credential, perform the following steps.
You cannot share the credential with other accounts. Only the credential creator can use the credential to connect to the instance.
|
|
|
|
How temporary SSH key pair-based authentication works
Temporary SSH key pair-based authentication is based on common commands of Cloud Assistant.
When you use Workbench to connect to a Linux instance, a temporary SSH key pair that has a validity period of 1 minute is generated.
Cloud Assistant calls the InvokeCommand operation to run the
ACS-ECS-EnableSshPublicKey-linux.shandACS-ECS-SendSshPublicKey-linux.shcommands to send the public key of the temporary SSH key pair to the Linux instance to which you want to connect. On the Linux instance, the public key is delivered to Cloud Assistant Agent.Then, you can use the temporary SSH key pair to connect to the Linux instance over Workbench.
Workbench does not store the temporary SSH key pair in a database. When the temporary SSH key pair expires 1 minute after being generated, you must reuse Workbench to generate another temporary SSH key pair to maintain the logon connection.
Issues
If you cannot connect to a Linux instance, troubleshoot the issue by following the procedure described in SSH connection issues.