Workbench is a browser-based remote connection tool from Alibaba Cloud. It lets you connect to Linux Elastic Compute Service (ECS) instances without a password and log on to instances that lack a Public IP Address.
Prerequisites
Instance status: The instance must be in the Running state and the Health Status must be Normal.
RAM permissions: A RAM user must have the required permissions to use Workbench.
Method 1: Use a password-free logon (Recommended)
By default, Password-free Logon connects to your instance using Session Manager. If Session Manager is not enabled, the connection uses a temporary SSH key pair.
Log on to the ECS console. At the top of the page, select a resource group and a region.
Find the target instance, click Connect, and select Workbench and click Sign in now.
On the Workbench Instance Login page, select Password-Free, enter a Username, and click Log In.
A successful connection looks like the following image:

A Workbench remote connection session remains active for up to 6 hours. If a session is idle for more than 6 hours, it automatically disconnects, and you must reconnect. To prevent your tasks from being interrupted by the session timeout, run long-running tasks in the background.
Method 2: Use a terminal connection (SSH)
Log on to the ECS console. At the top of the page, select a resource group and a region.
Find the target instance, click Connect, and select Workbench and click Sign in now.
On the Workbench Instance Login page, complete the following configuration, and then click Log In.
Configuration item
Description
Instance
Workbench automatically fills in the current instance's information.
Connection Method
Select Terminal. This method uses the SSH protocol to connect to the instance.
Authentication
ImportantSSH Key Pair Authentication is more secure than Password Authentication. For better security, bind a key pair and use this method to log on.
SSH key pair authentication
Username: The default username for a Linux instance is
root.If you set the logon name to
ecs-userwhen you created the instance, enterecs-user.Private Key: Paste your private key. If your private key has a passphrase, you must also enter the Passphrase.
To avoid re-entering your username and private key for each logon, you can save the key.
SSH Port (Optional): The default SSH port is 22. You can change it by clicking .
Password authentication
Username: The default username for a Linux instance is
root.If you set the logon name to
ecs-userwhen you created the instance, enterecs-user.Password: If you have forgotten or have not set a password, you must first reset the password.
To avoid re-entering your username and password for each logon, you can save the password.
SSH Port (Optional): The default SSH port is 22. You can change it by clicking .
After you click Log In, the system may prompt you to add a security group rule to allow access from Workbench IP address ranges to the instance's RDP port (default: 3389). Click One-click Add to quickly configure the security group. The console displays the specific security group rule that is required.
A successful connection looks like the following image:

A Workbench remote connection session remains active for up to 6 hours. If a session is idle for more than 6 hours, it automatically disconnects, and you must reconnect. To prevent your tasks from being interrupted by the session timeout, run long-running tasks in the background.
FAQ
How to save a password or private key?
To avoid re-entering your credentials for each logon, you can save them for future use.
This credential cannot be shared and can only be used by its creator.
Save a logon credential
When you log on to the instance, select the Save logon credential checkbox. After a successful logon, Workbench saves the credential.

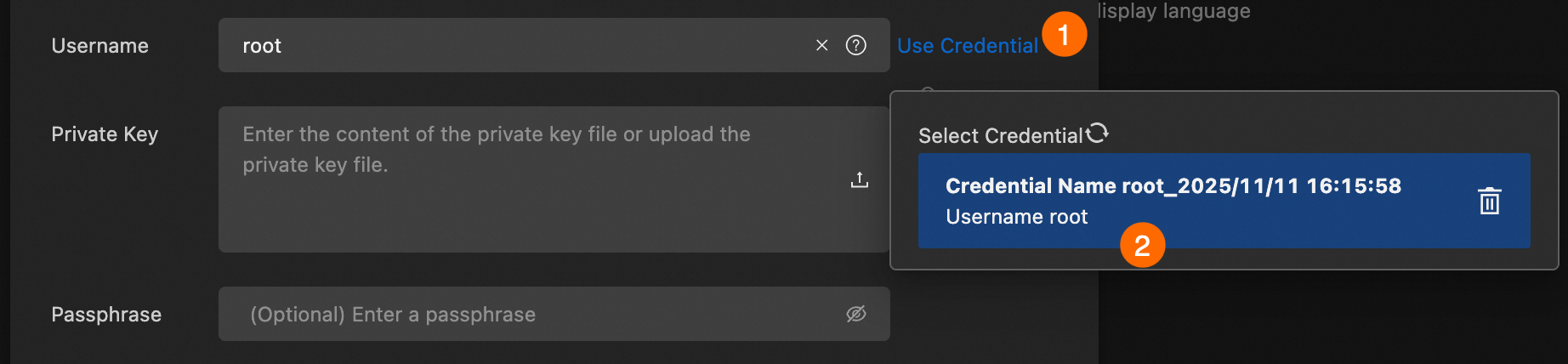
Use a credential to log on to an instance
When you log on to the instance, you can use a saved credential by selecting the Use Credential option.
How does password-free logon work?
By default, Password-free Logon connects to your instance using Session Manager. If Session Manager is not enabled, the connection uses a temporary SSH key pair.
How does Workbench connect to an instance over a private network?
When Workbench connects to an instance using a Private IP Address, it automatically creates a reverse access rule in the instance's VPC to establish a secure, two-way communication channel. You can view or manage this configuration in .
What is the default logon name for a Linux instance?
The default logon name for a Linux instance is root. If you selected ecs-user as the logon name when you created the instance, the logon name is ecs-user.
What is the default password for an instance?
Instances do not have a default or initial password. If you need to set a password, you can reset the password.
Troubleshoot remote connection failures
If you cannot connect to your instance, first use the self-service diagnostic tool to troubleshoot the issue. For manual troubleshooting steps, see Troubleshoot connection errors to a Windows instance.
Click to go to self-service troubleshooting page, and switch to the target region.
Under Instance Cannot Connect, click Intiate Diagnosis. Follow the on-screen instructions to select the affected instance and click Intiate Diagnosis.

After the diagnosis is complete, follow the prompts to resolve the issue.
 > Private Links
> Private Links