VPN Gateway is an Internet-based service that allows you to connect enterprise data centers, office networks, or Internet-facing terminals to Alibaba Cloud Virtual Private Cloud (VPC) over encrypted tunnels. This topic describes how to connect a data center to a VPC by using the IPsec-VPN function.
Prerequisites
The gateway device of the data center operates as expected.
Alibaba Cloud VPN Gateway supports the standard IKEv1 and IKEv2 protocols. In this example, IKEv2 must be supported because multiple CIDR blocks are configured. The gateway device can be manufactured by Hillstone, Sangfor, Cisco ASA, Juniper, SonicWall, Nokia, IBM, or Ixia.
A static public IP address is configured for the gateway device of the data center.
The CIDR block of the data center does not overlap the CIDR block of the VPC.
Background information
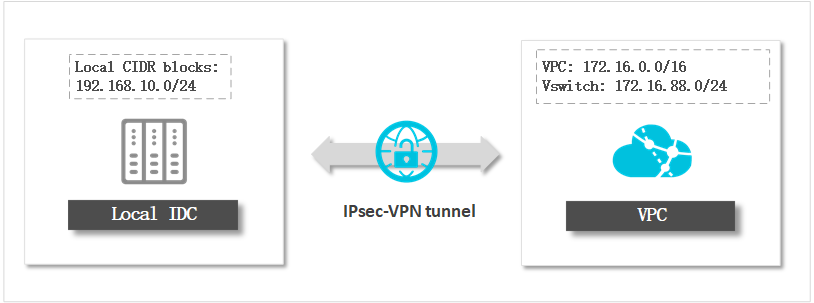
After the data center is connected to Alibaba Cloud VPC through IPsec-VPN, you can have a secure, fast, and stable network environment. You can specify a database that is deployed in the data center as a user-created database connected over Express Connect, VPN Gateway, or Smart Access Gateway. This is applicable when you use DTS for data migration, data synchronization, or change tracking.
Precautions
If the data center is already connected to Alibaba Cloud VPC, you can perform the following steps:
Add the CIDR blocks of DTS servers to the IPsec-VPN connection. For more information, see Modify an IPsec-VPN connection.
ImportantClick + Add CIDR Block and enter the CIDR blocks of DTS servers that reside in the corresponding region. For more information, see Add the CIDR blocks of DTS servers.
Configure an IPsec-VPN connection and a static route on the on-premises gateway.
Billing
You are charged for creating a VPN gateway. For more information, see Billing.
Step 1: Create a VPN gateway
Log on to the VPC console.
In the upper-left corner of the homepage, select the region.
In the left-side navigation pane, choose .
On the VPN Gateways page, click Create VPN Gateway.
Configure the VPN gateway based on your business requirements.
Parameter
Description
Region
Select the region to which the VPN gateway belongs.
ImportantThe VPN gateway must belong to the same region as the VPC.
VPC
Select the VPC to be connected.
Assign VSwitch
Optional. Specify whether to create the VPN gateway under a vSwitch.
Peak Bandwidth
Select the peak public bandwidth of the VPN gateway.
IPsec-VPN
Select Enable.
NoteThe IPsec-VPN function provides site-to-site connections. You can create an IPsec tunnel to connect a data center to a VPC, or connect two VPCs.
SSL-VPN
Select Disable.
NoteThe SSL-VPN function provides point-to-site connections. You can use the client to access the VPN without configuring a gateway for the client.
Billing Cycle
This parameter is set to AnalyticDB and cannot be changed.
Click Buy Now and follow the instructions to complete the payment.
Step 2: Create a customer gateway
Log on to the VPC console.
In the upper-left corner of the page, select the region to which the VPN gateway belongs.
In the left-side navigation pane, choose .
Click Create Customer Gateway.
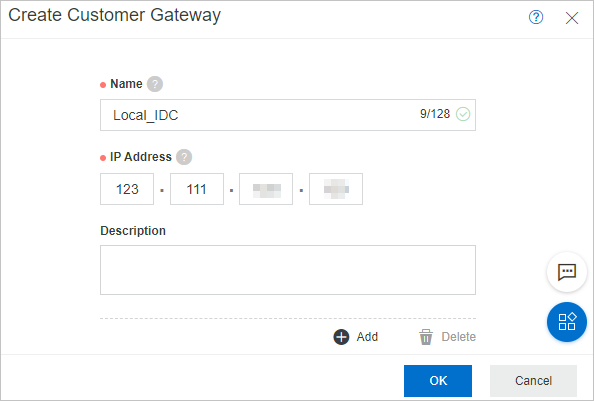
In the dialog box that appears, set the following parameters.
Parameter
Description
Name
Enter a name for the customer gateway. We recommend that you specify an informative name for easy identification.
ImportantThe name must start with a letter and can contain letters, digits, underscores (_), and hyphens (-).
The name must be 2 to 128 characters in length and can contain letters, digits, underscores (_), and hyphens (-).
IP Address
Enter the static public IP address of the gateway device of the data center.
Description
The description must be 2 to 256 characters in length and cannot start with
http://orhttps://.Click OK.
Step 3: Create an IPsec-VPN connection and configure a route
Log on to the VPC console.
In the upper-left corner of the page, select the region to which the VPN gateway belongs.
In the left-side navigation pane, choose .
Click Create IPsec Connection.
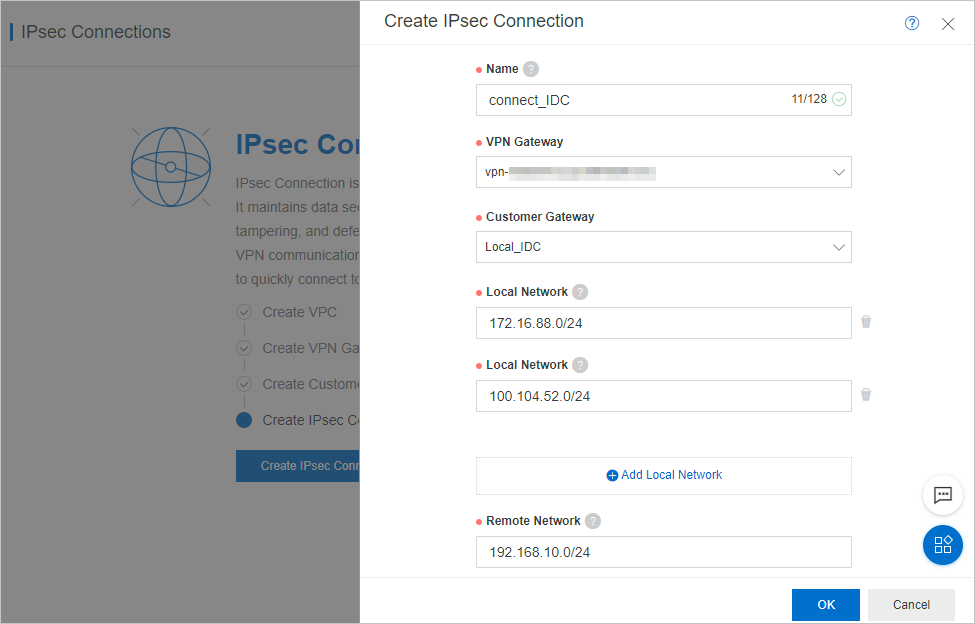
In the Create IPsec Connection pane, set the parameters described in the following table.
Parameter
Description
Name
Enter a name for the IPsec-VPN connection.
NoteThe name must be 2 to 128 characters in length and can contain letters, digits, underscores (_), and hyphens (-). It must start with a letter.
VPN Gateway
Select the VPN gateway to be connected through the IPsec-VPN connection. In this example, select the VPN gateway that is created in Step 1.
Customer Gateway
Select the customer gateway to be connected through the IPsec-VPN connection. In this example, select the customer gateway that is created in Step 2.
Local Network
Enter the CIDR block of the VPC that is connected to the data center. This parameter is used for phase two negotiations.
ImportantYou can enter the CIDR block of the VPC or a vSwitch in the VPC based on your business requirements. In this example, 172.16.88.0/24 is the CIDR block of a vSwitch in the VPC.
The CIDR block of the VPC cannot overlap the CIDR block of the data center.
+ Add CIDR Block
Enter multiple CIDR blocks of the VPC that is connected to the data center. In this example, enter the CIDR blocks of DTS servers. For more information, see Add the CIDR blocks of DTS servers.
ImportantWhen you add multiple CIDR blocks, set the version to ikev2 in Advanced Configuration.
Remote Network
Enter the CIDR block of the data center that is connected to the VPC. This parameter is used for phase two negotiations.
ImportantThe CIDR block of the data center cannot overlap the CIDR block of the VPC.
+ Add CIDR Block
Enter multiple CIDR blocks of the data center that is connected to the VPC.
ImportantWhen you add multiple CIDR blocks, set the version to ikev2 in Advanced Configuration.
Effective Immediately
Specify whether to start connection negotiations immediately.
Yes: Negotiate immediately after the configuration is complete.
No: negotiate when traffic is detected in the IPsec-VPN tunnel.
Advanced Configuration
For more information about the parameters, see Create an IPsec-VPN connection.
Health Check
Click OK.
In the Created dialog box, click OK to configure routing information for the VPN gateway.
The VPN Gateway page appears. On the Destination-based Routing tab, click Add Route Entry.
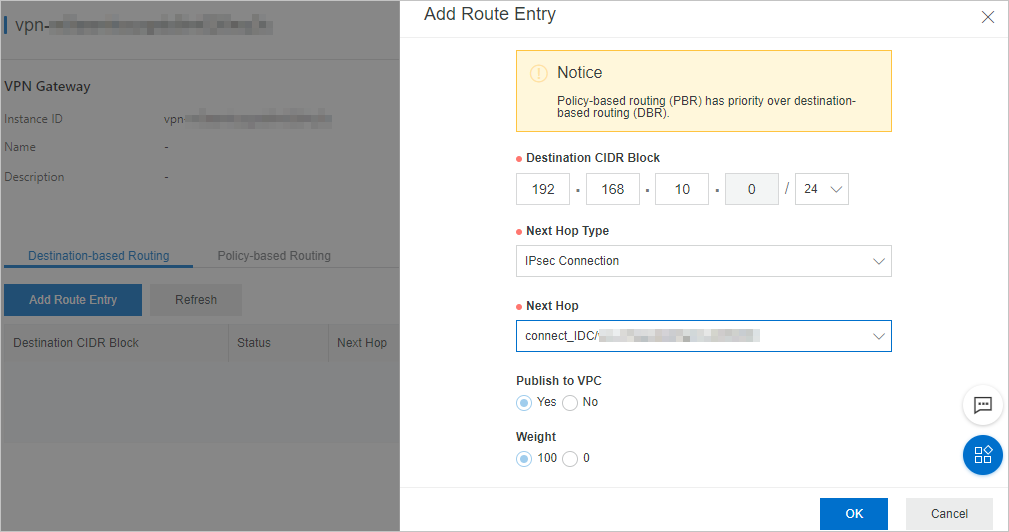
In the Add Route Entry pane, set the parameters described in the following table.
Parameter
Description
Destination CIDR block
Enter the private CIDR block of the data center. In this example, enter 192.168.10.0/24.
Next Hop Type
Select IPsec Connection.
Next Hop
Select the IPsec-VPN connection that you create.
Publish to VPC
Specify whether to publish the new route entry to the VPC routing table.
Yes(Recommended): publish the new route entry to the VPC routing table.
No: do not publish the new route entry to the VPC routing table.
ImportantIf you select No, you must publish the route entry to the destination-based routing table after you add the destination-based route entry.
Weight
Select a weight. Valid values:
100: The priority is high.
0: The priority is low.
ImportantIf two destination-based route entries have the same destination CIDR block, you cannot set the weight of both route entries to 100.
Step 4: Configure an IPsec-VPN connection and a static route on the on-premises gateway
Log on to the VPC console.
In the upper-left corner of the page, select the region to which the VPN gateway belongs.
In the left-side navigation pane, choose .
Find the IPsec-VPN connection. In the Actions column, choose .
In the IPsec Connection pane, the peer configuration is displayed.
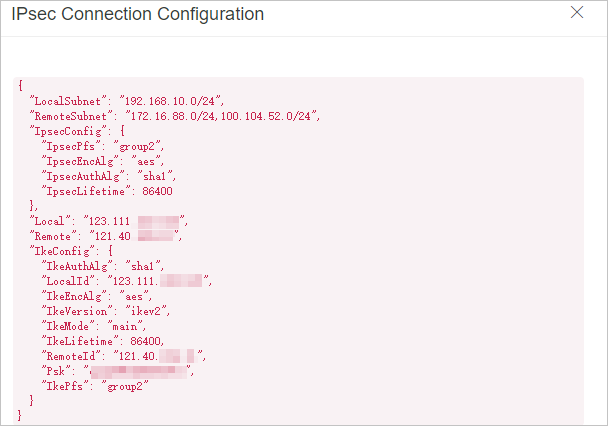
Add the peer configuration to the on-premises gateway device.
Add a static route entry to the on-premises gateway device. The destination addresses are the CIDR blocks of DTS servers. For more information, see Add the CIDR blocks of DTS servers. The next hop is the new IPsec-VPN tunnel interface.
References
For information about how to troubleshoot the issue if an IPsec connection fails, see FAQ about IPsec-VPN connections.