This topic describes how to configure automatic rotation of customer master keys (CMKs) in Key Management Service (KMS).
Key versions
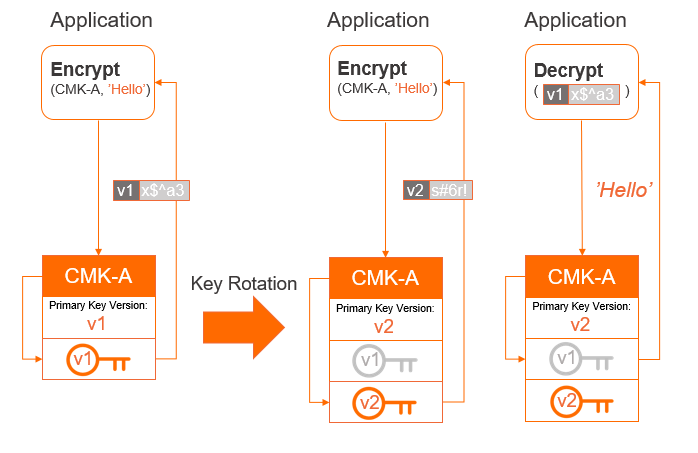
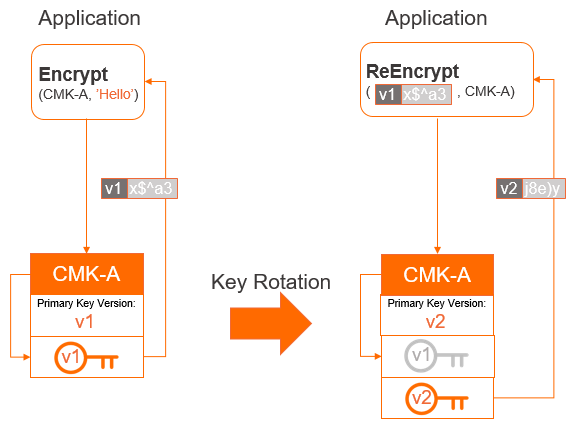
A CMK may have multiple key versions. Each key version represents an independently generated key. Key versions of the same CMK do not have any cryptographic relation to each other. KMS automatically rotates CMKs by generating new key versions.
Types of key versions
- Primary key version
- The primary key version of a CMK is an active encryption key. Each CMK has only one primary key version at any point in time.
- When you call an encryption operation such as GenerateDataKey or Encrypt, KMS uses the primary key version of a specified CMK to encrypt the plaintext.
- You can call the DescribeKey operation to query the PrimaryKeyVersion attribute.
- Non-primary key version
- A non-primary key version of a CMK is an inactive encryption key. Each CMK can have zero to many non-primary key versions.
- Each non-primary key version was a primary key version and acted as the active encryption key in the past.
- When a new primary key version is created, KMS does not delete or disable non-primary key versions because they need to be used to decrypt data.
Generation of key versions
- Create a CMK.
You can call the CreateKey operation to create a CMK. If you set the Origin parameter to Aliyun_KMS, KMS generates an initial key version and sets it as the primary key version.
- Execute an automatic rotation policy.
After you configure an automatic rotation policy for a CMK, KMS executes the policy on a regular basis to generate key versions.
Automatic rotation
Configure and query an automatic rotation policy
- EnableAutomaticRotation: specifies whether to enable automatic rotation.
- RotationInterval: the interval for automatic rotation.
- AutomaticRotation: indicates whether automatic rotation is enabled. For more information, see Impacts of CMK status on automatic rotation.
- Disabled: indicates that automatic rotation is disabled.
- Enabled: indicates that automatic rotation is enabled.
- Suspended: indicates that KMS suspends the execution of automatic rotation although automatic rotation is enabled.
- RotationInterval: the interval for automatic rotation.
Execute an automatic rotation policy
<NextRotationTime> = <LastRotationTime> + <RotationInterval>LastRotationTime: the time when the last key version was created. You can call the DescribeKey operation and check theLastRotationDateparameter to obtain the time.NextRotationTime: the time when KMS performs the next rotation task to create a key version. You can call the DescribeKey operation and check theNextRotationDateparameter to obtain the time.
Impacts of automatic rotation on encryption and decryption
Impacts of CMK status on automatic rotation
- If a CMK is in the Disabled or Pending Deletion state, do not call the UpdateRotationPolicy operation to update its automatic rotation policy.
- If a CMK enters the Disabled or Pending Deletion state after you enable automatic rotation for the CMK, KMS suspends the execution of automatic rotation. In this case, if you call the DescribeKey operation, the returned value of the AutomaticRotation parameter is Suspended. When the CMK enters the Enabled state again, its automatic rotation policy becomes active.
Limits
- Service-managed keys: the default keys managed by KMS for specific cloud services. These keys belong to the users of cloud services and are used to provide basic encryption protection for user data.
- Keys based on Bring Your Own Key (BYOK): the keys that you imported to KMS. The Origin attribute of these keys is EXTERNAL. KMS does not generate key material or initiate rotation tasks for these keys. For more information, see Import key material.
- Users have strong control over the persistence and lifecycle of BYOK-based keys. This makes management of the keys difficult and error-prone. For example, you must have on-premises key management facilities, data must be synchronized between on-premises facilities and the cloud, and no grace period is provided for key material deletion on the cloud. The complexity of maintaining multiple versions of BYOK-based keys makes key management much more risky.
- Both primary and non-primary key versions may become unavailable at different points in time. For example, if key versions are deleted by KMS or imported again when they expire, CMKs may not be synchronized and encrypted data may not be decrypted by using the correct CMK. This affects system integrity.