Alibaba Cloud Container Registry (ACR) is a platform that provides secure hosting and efficient distribution for cloud-native artifacts that comply with Open Container Initiative (OCI) standards, such as container images and Helm charts. ACR Enterprise Edition provides end-to-end acceleration capabilities, including global synchronization, large-scale distribution of large images, and multi-source code building. It seamlessly integrates with ACK to help enterprises reduce delivery complexity and create a one-stop solution for cloud-native applications.
Product type
Container Registry Enterprise Edition
Container Registry Enterprise Edition is designed for enterprise customers. It is an enterprise-level management platform for cloud-native application artifacts. It provides lifecycle management for OCI-compliant artifacts, such as container images and Helm charts. It supports efficient distribution of large-scale application artifacts across multiple regions and in various scenarios. The service seamlessly integrates with ACK to help enterprises reduce delivery complexity.
Container Registry Personal Edition
Container Registry Personal Edition is designed for individual developers. It provides basic container image services, including application image hosting, a stable image building service, and convenient image authorization. This allows users to perform full lifecycle management of images.
Features
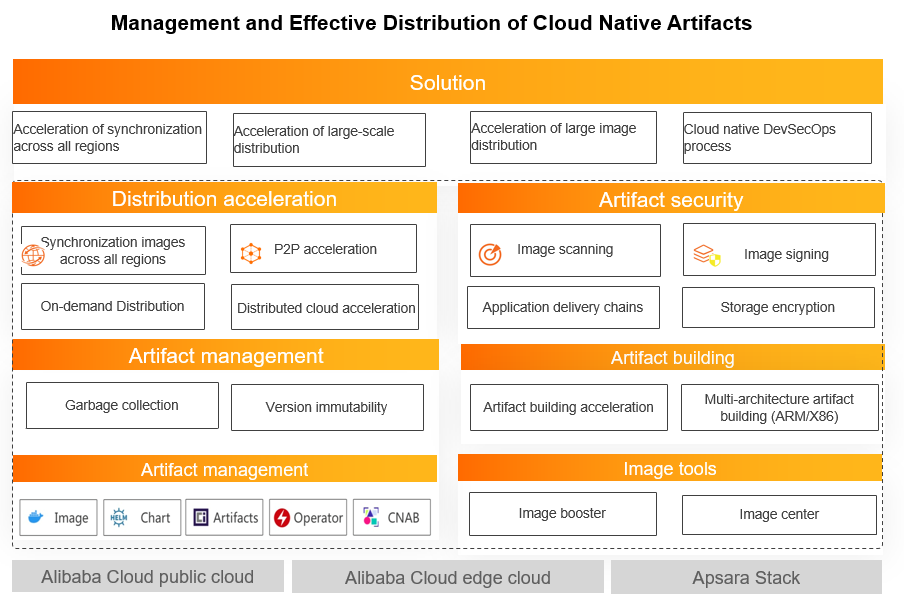
Features of Container Registry Enterprise Edition
Feature | Description |
Hosting of diverse OCI artifacts | Supports multi-architecture container images (such as Linux, Windows, and Arm), Helm Chart v2/v3, and management of OCI-compliant artifacts. |
Accelerated application distribution | Supports global synchronization across multiple regions to improve container image distribution efficiency. Provides a P2P distribution acceleration method. |
Multi-dimensional security | Encrypts cloud-native artifacts for storage. Supports image security scanning and multi-dimensional vulnerability reports to ensure storage and content security. Provides network access control for container images and Helm charts, and fine-grained audits to ensure artifact access security. |
Efficient cloud-native application delivery | Provides a cloud-native application delivery chain feature that is observable, traceable, and configurable. Supports policy-based automatic blocking. This enables automated global delivery across multiple scenarios with a single application change, improving the efficiency and security of cloud-native application delivery. |
Features of Container Registry Personal Edition
Feature | Description |
Flexible region selection |
|
Service architecture
The following figure shows the service architecture of ACR. For more information about the features in the figure, see the related documents.
Specifications
The following tables describe the specifications of Container Registry Personal Edition and Enterprise Edition.
Container Registry Personal Edition is designed for individual developers. Alibaba Cloud does not provide an SLA guarantee or compensation for SLA violations. This edition also has usage limits. Do not use Container Registry Personal Edition in production environments.
To learn how to select the edition that meets your business requirements and configure disaster recovery solutions, refer to the instance edition features and differences. Then follow the disaster recovery instructions to prepare a cross-zone disaster recovery solution, cross-region disaster recovery solution, and data backup solution.
Module | Feature | Personal Edition instance | Enterprise Edition instance | ||||
Basic Edition instance | Advanced Edition instance | ||||||
Disaster recovery | Instance | Cross-zone disaster recovery | None. | By default, multi-zone regions support this feature. | |||
Cross-region disaster recovery | None. | You must create multiple Container Registry instances in different regions to implement this feature. For more information, see Best practices for geo-disaster recovery of Container Registry Enterprise Edition instances. | |||||
Instance storage | Cross-zone disaster recovery | None. | You must use the zone-redundant storage (ZRS) feature of Object Storage Service (OSS) to implement this feature. For more information, see Create a zone-redundant storage bucket. | ||||
Cross-region backup | None. | You must use the cross-region replication (CRR) feature of OSS to implement this feature. For more information, see CRR. | |||||
Service guarantee | - | SLA | None. | 99.95% | 99.95% | ||
Feature category | Feature | Personal Edition | Enterprise Edition | ||
Basic Edition | Premium Edition | ||||
Artifact management | Container image | Hosting |
|
|
|
Namespace quota | 3 | 15 | 50 | ||
Public repository quota | 300 | 1000 | 5000 | ||
Private repository quota | |||||
VPC access control quota |
| Purchase separately | |||
Helm Chart | Hosting |
|
|
| |
Namespace quota |
| 15 | 50 | ||
Public repository quota |
| 1000 | 5000 | ||
Private repository quota | |||||
OCI Artifact |
|
|
| ||
Version immutability |
|
|
| ||
Tag management (automatic cleanup) |
|
|
| ||
Artifact building | Concurrent build quota | 1 | 3 | 10 | |
Intelligent acceleration |
|
|
| ||
Multi-architecture image building |
|
|
| ||
Artifact security | Multi-engine scan |
|
|
| |
Vulnerability fixing |
|
|
| ||
Threat blocking |
|
|
| ||
Signing and signature verification |
|
|
| ||
Network access control |
|
|
| ||
ActionTrail |
|
|
| ||
Artifact distribution | Distribution performance (pull QPS) | Not guaranteed | 250 | 1000 | |
P2P distribution |
|
|
| ||
On-demand distribution |
|
|
| ||
Global synchronization |
|
|
| ||
Artifact subscription |
| 5 | 30 | ||
Synchronization rule |
|
| 60 | ||
Artifact delivery | Event notification |
|
|
| |
Password-free pull |
|
|
| ||
Cloud-native application delivery chain |
|
|
| ||
Instance management | Custom domain name |
|
|
| |
Fast image import from Harbor |
|
|
| ||
Use ACR
Click Try ACR now.