The Vulnerability Prevention page displays information about the vulnerabilities that can be exploited by cyberattacks. The vulnerabilities are automatically detected by Security Center and synchronized to Cloud Firewall. On this page, you can enable the firewalls of Cloud Firewall and configure the protection rules of the intrusion prevention system (IPS) module to prevent the vulnerabilities from being exploited. This way, your assets are protected. This topic describes the types of vulnerabilities that can be detected by Cloud Firewall and how to perform vulnerability prevention.
Supported vulnerability types
Cloud Firewall only synchronizes network scan-based vulnerabilities. The supported vulnerability types displayed in the console shall prevail.
If an asset on which a vulnerability is detected is not attacked or if no vulnerability is detected on an asset, Cloud Firewall does not display the vulnerability prevention statistics of the asset.
Cloud Firewall synchronizes the types of vulnerabilities that are detected by Security Center and displays the types on the Vulnerability Prevention page. When a vulnerability is detected in a protected asset, Cloud Firewall analyzes exploit behavior based on attack traffic and protects the asset.
If you use Cloud Firewall Enterprise Edition or Ultimate Edition, you can click Configure in the section to view the types of vulnerabilities that are supported by Cloud Firewall. For more information, see Use the prevention configuration feature.
Limits
Cloud Firewall that uses the subscription or pay-as-you-go billing method supports vulnerability prevention. Cloud Firewall Free Edition does not support vulnerability prevention.
Vulnerability scans on the Vulnerability Prevention page are automatically started. You cannot manually start the scans.
NoteIf you want to manually start a vulnerability scan, go to the Vulnerabilities page in the Security Center console. For more information, see Scan for vulnerabilities.
Only threat intelligence blocking is supported by Server Load Balancer (SLB) instances that are deployed in the classic network.
The IPS module of Cloud Firewall cannot parse the traffic that is encrypted by using SSL or Transport Layer Security (TLS). Therefore, this type of traffic cannot be detected or protected.
Prerequisites
Threat Engine Mode on the Prevention Configuration page is set to Block Mode.
If Threat Engine Mode is not set to Block Mode, the protection status of all vulnerabilities on the Vulnerability Prevention page is Alert Only. In this case, Cloud Firewall generates alerts on and records detected vulnerabilities, but does not block the attacks that exploit the vulnerabilities. For more information about threat engine modes, see Working modes of the threat detection engine.
Procedure
Log on to the Cloud Firewall console.
In the left-side navigation pane, choose .
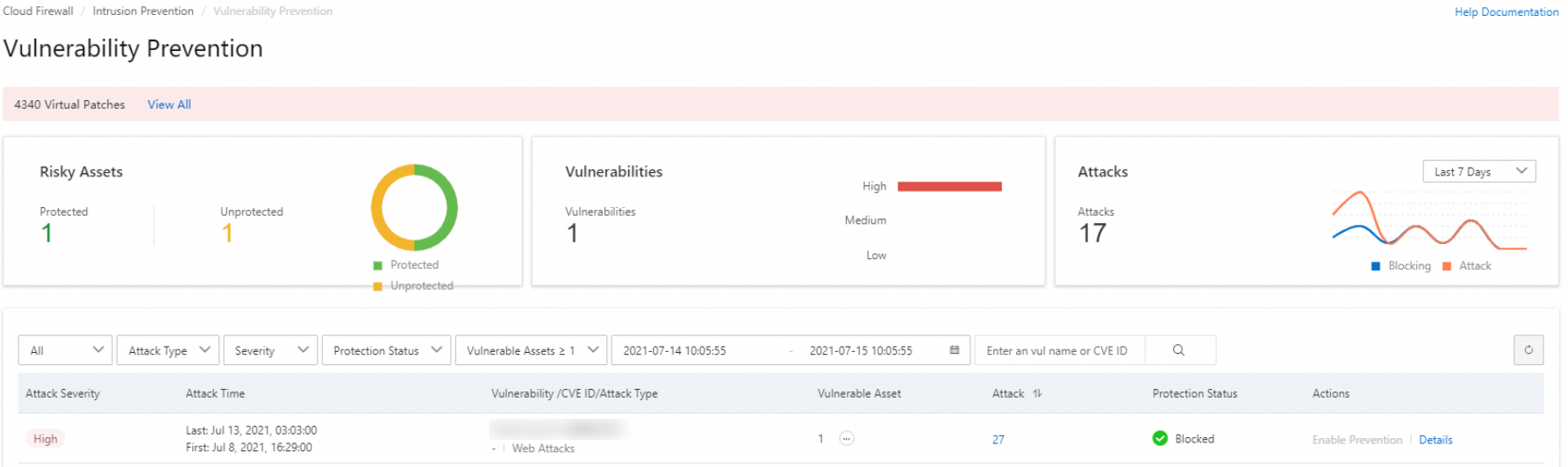
On the Vulnerability Prevention page, view the results of vulnerability scans performed by Cloud Firewall on your assets.
The Vulnerability Prevention page displays the results of vulnerability scans from the last one month, one day, or seven days.
Move the pointer over the
 icon in the Vulnerable Assets column. Then, you can view the IP addresses of servers on which the vulnerability is detected.
icon in the Vulnerable Assets column. Then, you can view the IP addresses of servers on which the vulnerability is detected.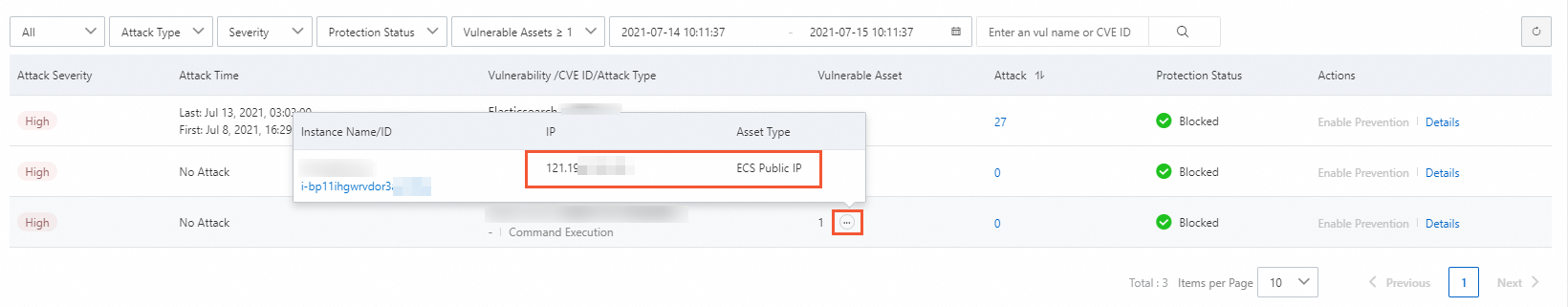
Attack: the total number of attacks that exploit the vulnerability on your assets.
Protection Status: the method that Cloud Firewall uses to handle the attacks exploiting the vulnerability. The following states are supported:
Blocked: The attacks that exploit vulnerabilities are blocked by Cloud Firewall.
Alert Only: Cloud Firewall detects a vulnerability and generates alerts on the vulnerability. Cloud Firewall does not block the attacks that exploit the vulnerability.
Partial Protection: Specific Elastic Compute Service (ECS) instances are protected by Cloud Firewall.
Details: Click Details to go to the Vulnerability and Protection Details page. On this page, you can view the details of the vulnerability, such as the name, CVE ID, risk level, and affected assets.
On the Vulnerability Prevention page, search for the vulnerabilities that are in the Alert Only state. Then, click Enable Protection in the Actions column of a vulnerability.
If the server on which the vulnerability is detected is not protected by Cloud Firewall, the Internet firewall is enabled for the server after you click Enable Protection. If Cloud Firewall is enabled for the server on which the vulnerability is detected, the blocking mode of Threat Engine Mode on the IPS Configuration page is enabled for the server after you click Enable Protection. It requires 1 to 2 minutes for the protection status of vulnerabilities to be updated.
NoteAfter the vulnerability prevention feature is enabled, existing access control policies take effect on the assets on which firewalls are newly enabled. Make sure that the traffic on the external ports of these assets is allowed on the Inbound tab of the Internet Border page.
What to do next
You can use the prevention configuration feature of Cloud Firewall to configure the working mode of the threat detection engine. You can also configure the threat intelligence, basic protection, intelligent defense, and virtual patching features to effectively identify and block intrusion attempts. For more information, see Prevention configuration.
You can use the IPS module to proactively detect and block malicious traffic that is generated by attacks, exploits, brute-force attacks, worms, mining programs, trojans, and DoS attacks in real time. This protects enterprise information systems and network architectures on the cloud against attacks. For more information, see Overview and Use the intrusion prevention feature.