Service Mesh (ASM) allows you to route traffic to different versions of a service based on the specified ratio. This feature is applicable to many scenarios such as canary release and A/B testing. This topic describes how to use Istio resources to route traffic to different versions of a service.
Prerequisites
The Bookinfo application is deployed in the ASM instance. For more information, see Deploy an application in an ACK cluster that is added to an ASM instance.
Step 1: Create an Istio gateway
An Istio gateway defines a load balancer that works at the edge of a service mesh to receive inbound or outbound HTTP/TCP traffic. The following section describes how to create an Istio gateway and bind it to an ingress gateway.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose . On the page that appears, click Create.
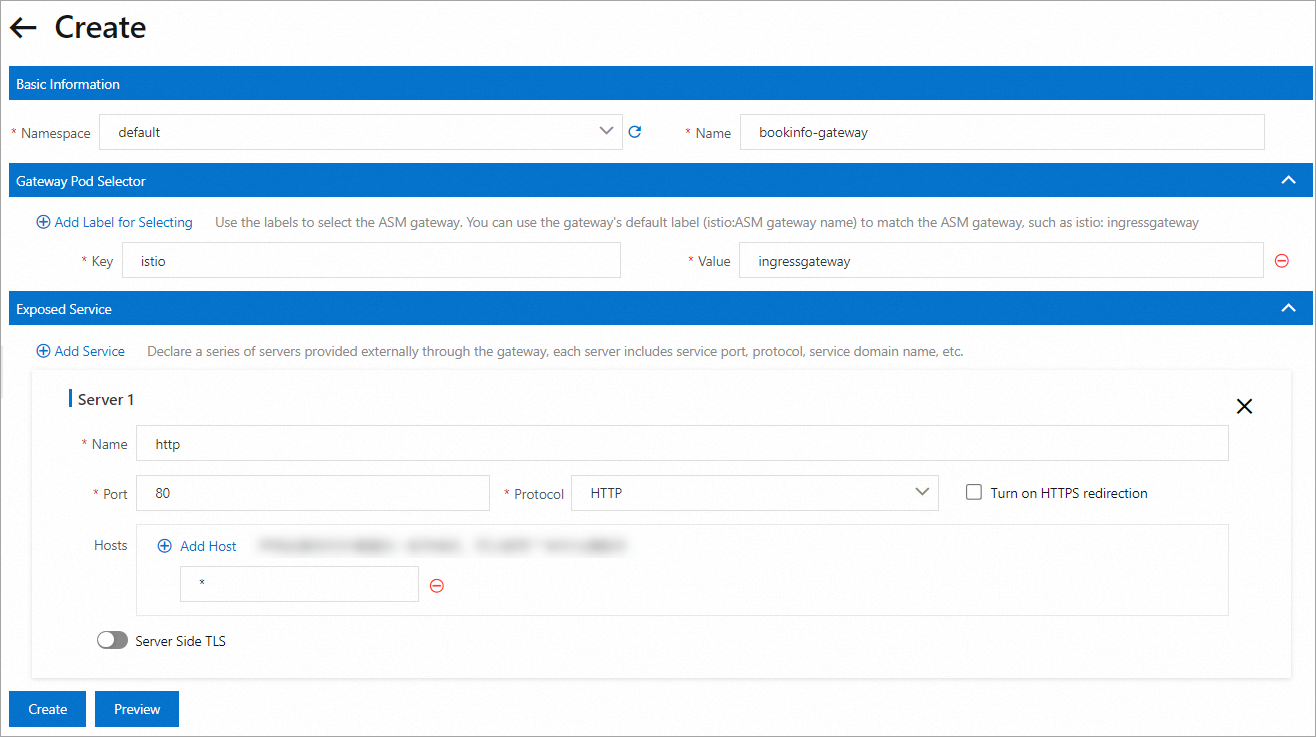
On the Create page, configure the following parameters and then click Create.
For more information about the parameters, see Gateway.
Parameter
Description
Basic Information
Set Namespace to default and Name to bookinfo-gateway.
Gateway Pod Selector
For this example, set Key to istio and Value to ingressgateway.
Exposed Service
Set Name to http, Port to 80, Protocol to HTTP, and Service to *.
The following YAML code shows the Istio gateway that corresponds to the preceding configurations.
Step 2: Create a virtual service
A virtual service defines traffic routing rules and request forwarding policies. After you create a virtual service, you can use the following paths to access the Bookinfo application: /productpage, /static, /login, /logout, and /api/v1/products.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose . On the page that appears, click Create.
On the Create page, configure the following parameters and then click Create.
For more information about the parameters, see Virtual Service.
Parameter
Description
Basic Information
Namespace
In this example, default is selected.
Name
Specify a name for the virtual service.
Gateways
Turn on the Apply To specific Gateways switch and click Select the name of the Gateway.
In the Select the name of the Gateway dialog box, select bookinfo-gateway, click the
 icon, and then click OK.
icon, and then click OK. Turn off the Apply To All Sidecars switch.
Hosts
Click Select the gateway domain name which VirtualService belongs to. In the Select the gateway domain name which VirtualService belongs to dialog box, select *, click the
 icon, and then click OK.
icon, and then click OK. HTTP Route
Name
Click the HTTP Route tab, click Add Route, and then enter a route name in the Name field.
Request matching rules
Click Add Request Matching Rule repeatedly to configure the following five rules:
Turn on Matching request URI, set Method to Exact and Content to /productpage.
Turn on Matching request URI, set Method to Prefix and Content to /static.
Turn on Matching request URI, set Method to Exact and Content to /login.
Turn on Matching request URI, set Method to Exact and Content to /logout.
Turn on Matching request URI, set Method to Prefix and Content to /api/v1/products.
Route destination
Click Add Route Destination. Set Host to productpage and Port to 9080.
The following YAML code shows the virtual service that corresponds to the preceding configurations.
Step 3: Access the Bookinfo application
Obtain the IP address of the ingress gateway.
Method 1: by using the ASM console
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Ingress Gateway page, obtain Service address.
Method 2: by using the ACK console
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, find the cluster that you want to manage and click its name. In the left-side pane, choose .
On the Services page, select istio-system from the Namespace drop-down list. In the External IP column, view the IP address of port 80 for the istio-ingressgateway.
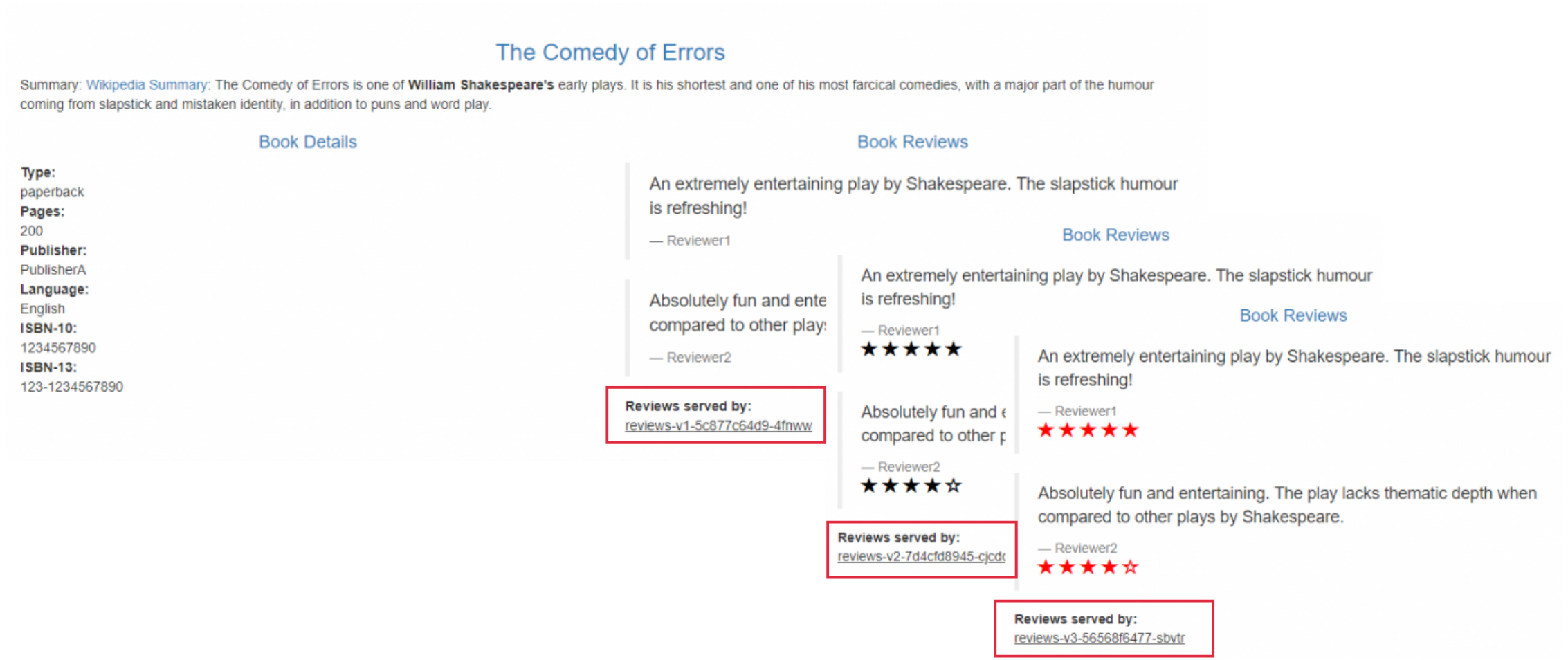
In the address bar of your browser, enter http://{IP address of the ingress gateway}/productpage and refresh the page 10 times to access the Bookinfo application.
The Bookinfo application accesses the v1, v2, and v3 versions of the reviews service. You can see that the ratio of requests to the three versions of the reviews service is close to 1:1:1.
Step 4: Create routing rules for different versions of a service
Create a destination rule and group instances of the reviews service by version. In this example, the instances of the reviews service include the v1, v2, and v3 subsets.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose . On the page that appears, click Create.
On the Create page, configure the following parameters and click Create.
For more information about the parameters, see Destination Rule.
Parameter
Description
Basic Information
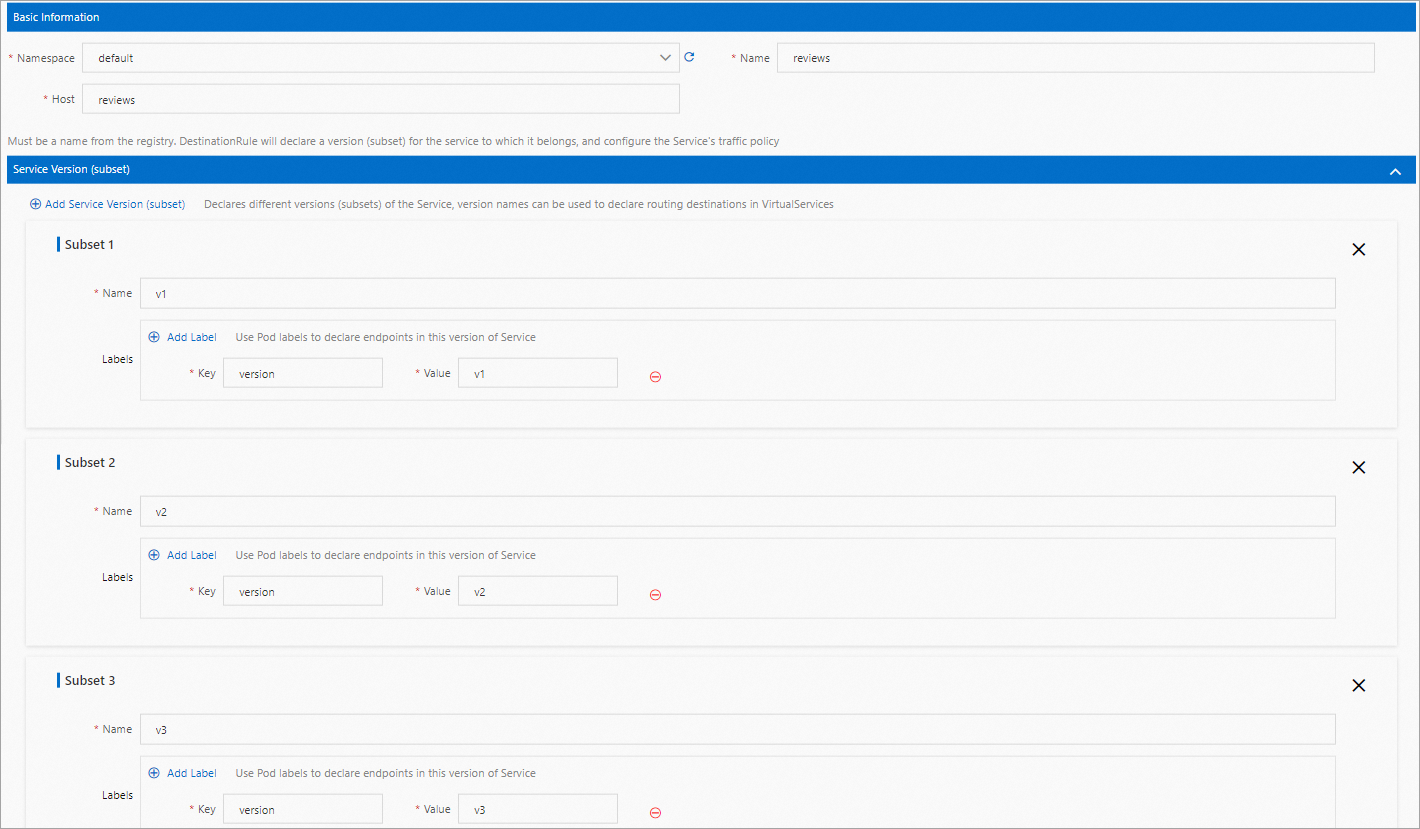
Set Namespace to default, specify a Name for the destination rule, and set Host to reviews.
Service Version (subset)
Click the Service Version (subset) tab. Then, click Add Service Version (subset) repeatedly to configure the following three subsets:
Subset 1: Set Name to v1. Click Add Label, and set Key to version and Value to v1.
Subset 2: Set Name to v2. Click Add Label, and set Key to version and Value to v2.
Subset 3: Set Name to v3. Click Add Label, and set Key to version and Value to v3.
The following YAML code shows the destination rule that corresponds to the preceding configurations.
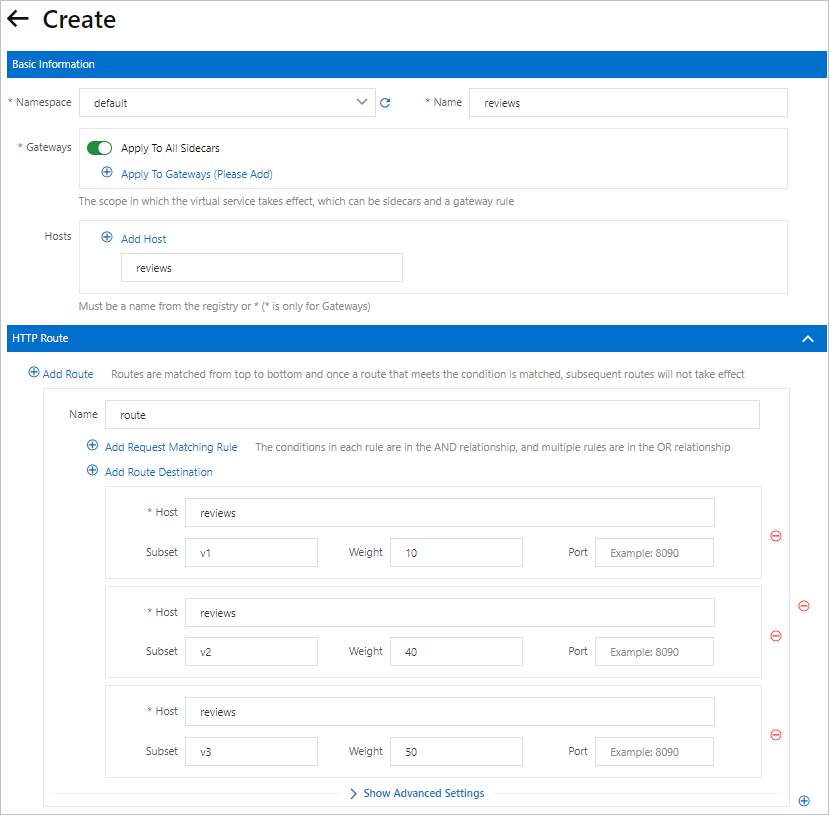
Create a virtual service to route 10% of the traffic to the v1 version of the reviews service, 40% of the traffic to the v2 version of the reviews service, and 50% of the traffic to the v3 version of the reviews service.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose . On the page that appears, click Create.
On the Create page, configure the following parameters and click Create.
Parameter
Description
Basic Information
Namespace
For this example, select default.
Name
Specify a name for the virtual service.
Gateways
Turn on Apply To All Sidecars.
Hosts
Click Add Host. In the Add Host dialog box, set Namespace to default. In the Add Host section, select reviews, click the
 icon, and then click OK.
icon, and then click OK. HTTP Route
Name
Click the HTTP Route tab. Click Add Route, and then enter a route name in the Name field.
Route destination
Click Add Route Destination repeatedly to configure the following three route destinations:
Set Host to reviews, Subset to v1, and Weight to 10.
Set Host to reviews, Subset to v2, and Weight to 40.
Set Host to reviews, Subset to v3, and Weight to 50.
The following YAML code shows the virtual rule that corresponds to the preceding configurations.
Step 5: Check whether the traffic routing settings take effect
In the address bar of your browser, enter http://{IP address of the ingress gateway}/productpage. Refresh the page 10 times.
If traffic routed to the v1, v2, and v3 versions of the reviews service appears at a ratio close to 1:4:5, the traffic routing settings take effect.