To avoid security vulnerabilities and stability risks associated with outdated software, it's essential to upgrade your cluster in a timely manner. A cluster upgrade consists of two main phases: control plane upgrade and node pool upgrade.
Before proceeding, review the full process in Upgrade a cluster to learn about the available methods, compatibility requirements, and best practices.
Upgrade procedure
You can upgrade the control plane first, followed by the node pools. However, ensure that the kubelet and container runtime versions on your nodes are compatible with the target control plane version to avoid failures or service disruptions.
Example:
If your control plane is at version 1.32 and your nodes are at 1.31, you must first upgrade the nodes to 1.32 before upgrading the control plane to 1.33.
Steps
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left navigation pane, choose .
On the Upgrade Cluster page, select a Target Version for the upgrade and follow the on-screen instructions to complete the upgrade.
Step 1: Upgrade the control plane
1. Precheck
Before upgrading, run a precheck to identify potential risks. This includes:
Use of deprecated APIs
Component compatibility
Overall cluster health
For clusters running Kubernetes 1.20 or later, the system checks for deprecated APIs. While this doesn't block the upgrade, we recommend resolving any issues beforehand to ensure smooth operations post-upgrade.
How to run precheck
On the Upgrade Cluster page, click Precheck.
After the scan completes, view the results in the Precheck Result section.
Example:
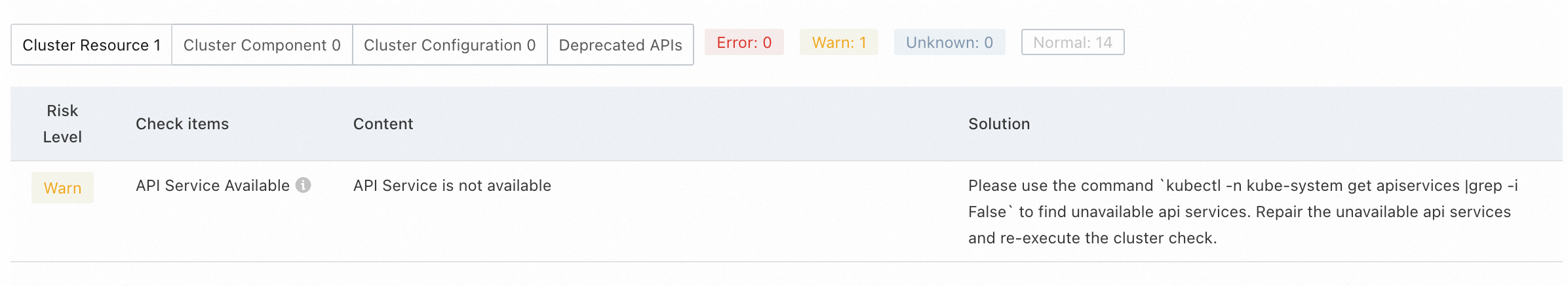
Result | Action |
Normal | Proceed with the upgrade. |
Abnormal | Address issues using the console guidance or refer to Cluster check items and remediation solutions. |
2. Perform the upgrade
Duration:
ACK managed and ACK Serverless clusters: Upgrade is fast and highly available.
ACK dedicated clusters: Master nodes are upgraded one by one, taking about 8 minutes per node.
Once precheck issues are resolved:
Click Upgrade Now.
Follow the prompts to complete the control plane upgrade.
After the upgrade, new nodes added during scaling will automatically use the upgraded version.

3. Post-upgrade verification
After the control plane is upgraded, verify the following:
Check item | Expected outcome |
Cluster version | Updated to the target version on the Clusters page. |
API server & core components | Status is Normal. |
Business applications | Running as expected. |
Pod creation | New pods can be created successfully. |
Node addition | New nodes can be added without issues. |
Step 2: Upgrade a node pool
After the control plane is upgraded, upgrade the node pool during off-peak hours to minimize impact.
A node pool upgrade updates the kubelet and container runtime on each node.
1. Precheck
The precheck evaluates:
Node status
System resources
Disk health
Network environment
How to run precheck
On the Node Pool Upgrade page, find the target node pool and click Upgrade in the Actions column.
Click Precheck at the bottom of the page.
Review results in the Precheck Result section.

Result | Action |
Normal | Proceed with the upgrade. |
Abnormal | Address issues using the console guidance or refer to Cluster check items and remediation solutions. |
2. Configure upgrade policy and start
Duration:
In-place upgrade: about 5–10 minutes per batch.
System disk replacement (no snapshots): about 8 minutes per batch.
Time to drain nodes also affects total duration.
If snapshots are enabled, upgrade starts only after snapshot creation (time varies with data volume).
Upgrade configuration
Configuration item | Description |
Version Information | Shows current and available versions for kubelet and container runtime. |
Nodes To Upgrade | Choose to upgrade all nodes, or upgrade a subset first and validate before upgrading the rest. |
Upgrade Method |
|
Batch Upgrade Policy |
|
Click Upgrade Now and follow the prompts to start.
3. Post-upgrade verification
After the node pool upgrade, verify the following:
Check item | Expected outcome |
Node versions | On the node details page, kubelet and containerd versions match the target. |
Pod scheduling | Pods are scheduled normally. |
Business applications | Function as expected. |
References
Release notes for ACK: Kubernetes version support policy
Automatically upgrade a cluster: Reduce O&M effort with auto-upgrades
Starting with Kubernetes 1.24, Docker is no longer supported as a container runtime. When upgrading to 1.24+, you must migrate the container runtime of nodes from Docker to containerd.
Starting with Kubernetes 1.30, CentOS and Alibaba Cloud Linux 2 are no longer supported. Use a supported operating system.