This topic describes how to use Alibaba Cloud Managed Service for Prometheus to monitor the metrics about Elastic Compute Service (ECS) instances deployed in a virtual private cloud (VPC), discard metrics, and configure alerting. To monitor the ECS instances, you need to enable a component named Host Monitor.
Workflow
Monitoring ECS instances requires the following steps:
Enable Host Monitor: Enable the Host Monitor component and select a VPC. Then, the open source exporters are automatically installed. This way, the managed Prometheus agent automatically collects data.
(Optional) Modify Host Monitor: Modify the configurations of the Host Monitor component, such as the service port, to fix errors or meet new business requirements.
(Optional) Discard metrics: Discard metrics that you do not need to refine metric collection and saves costs.
(Optional) Configure alerting: Configure alerting for specific metrics to detect changes and troubleshoot problems in a timely manner.

Prerequisites
A VPC is created. One or more ECS instances are created in the VPC. For more information, see Create and manage an ECS instance in the console (express version).
Alibaba Cloud Resource Center is activated. For more information, see Activate Resource Center.
NoteBefore you monitor ECS instances, you must activate Resource Center. This is because the service discovery capabilities of Managed Service for Prometheus rely on the VPC data and ECS data of the current account provided by Resource Center.
1. Enable Host Monitor
After you enable Host Monitor and select the VPC, Node Exporter and Process Exporter are installed for ECS instances in the VPC by default. Then, the managed Prometheus agent automatically collects data. You can store and visualize the data, and configure alerting for the data in a unified manner. About 1,000 metric entries are collected for each ECS instance at a time.
1.1 Enable the component
In the left-side navigation pane of the ARMS console, click Integration Center. In the Infrastructure section, click Host Monitor.
In the panel that appears, select the VPC and configure the parameters as required. For more information, see Monitor ECS instances.
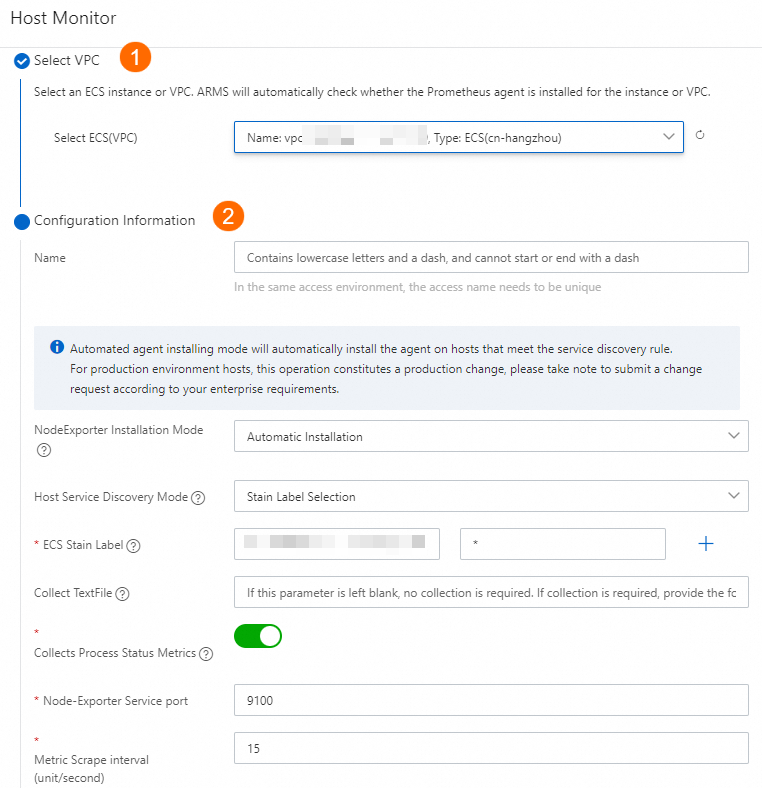
Click OK. Wait for 1 or 2 minutes.
1.2 View the dashboards
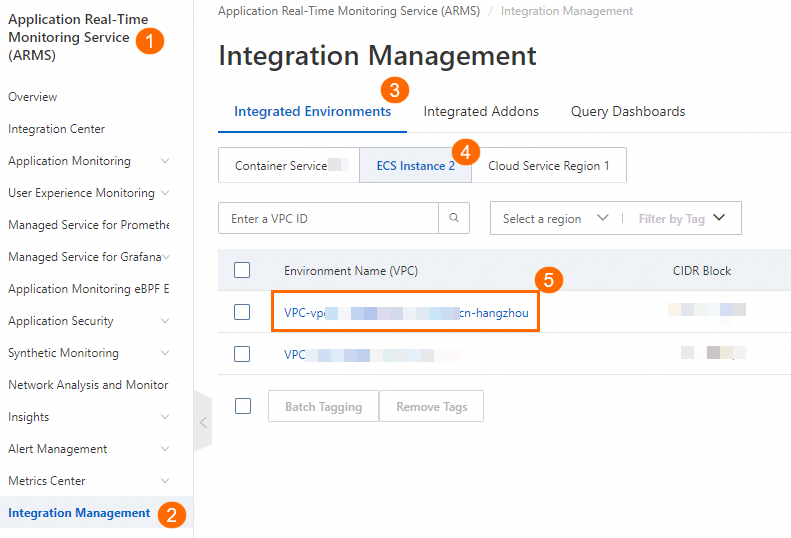
In the left-side navigation pane of the ARMS console, click Integration Management. On the Integrated Environments tab, click ECS Instance. Click the VPC ID and go to the environment details page.
On the Component Management tab, click Dashboards in the Addon Type section to view the built-in Grafana dashboards.
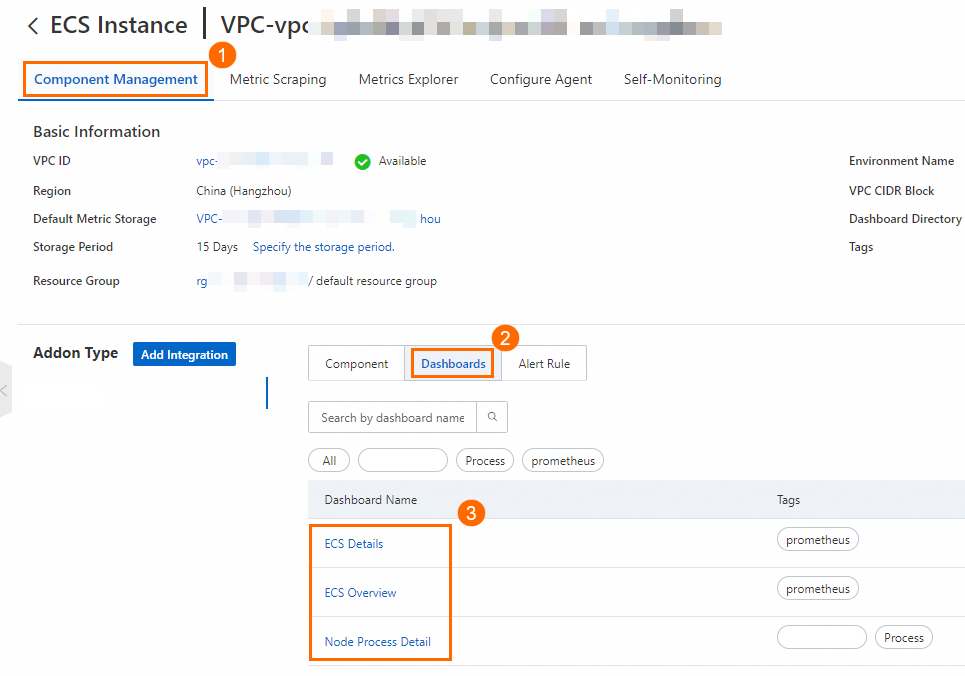
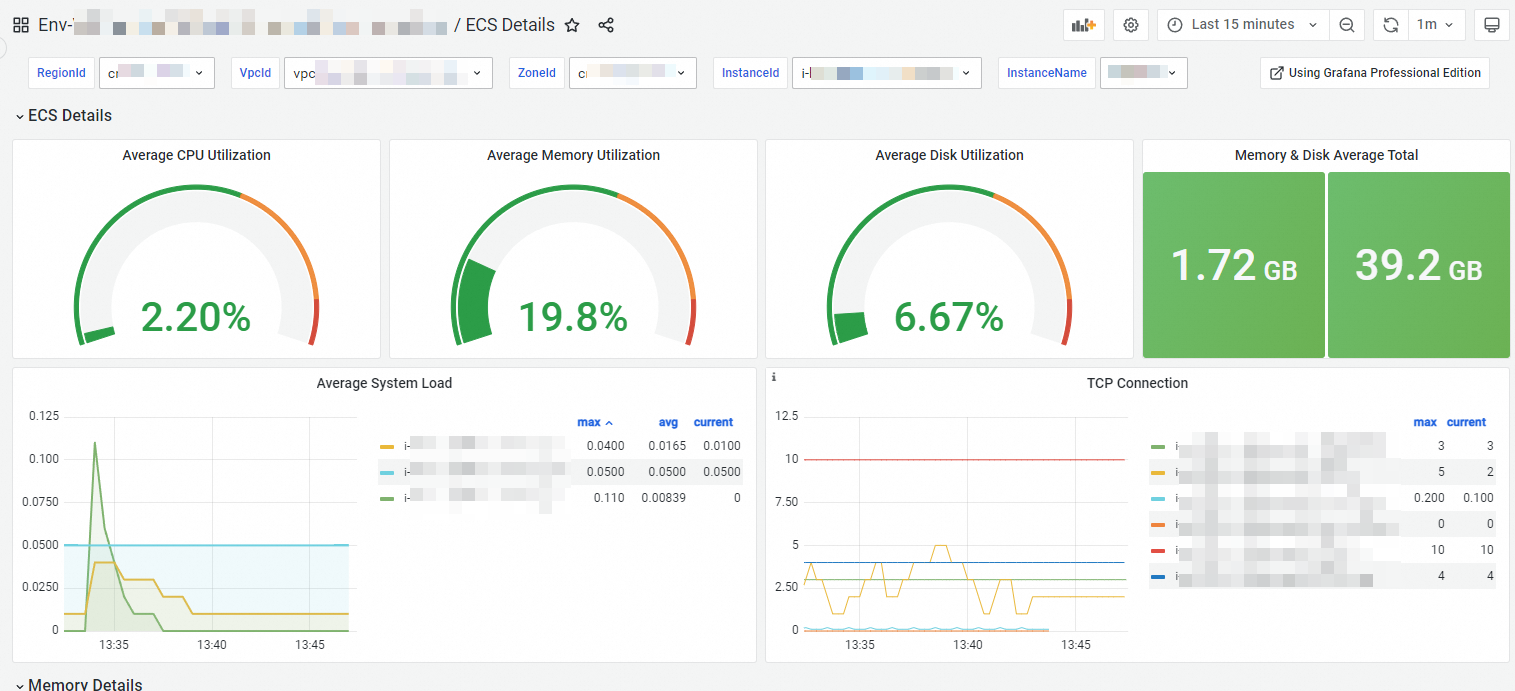 Note
NoteIf the dashboards have no data, check the security group settings. For more information, see Why do the dashboards have no data?
2. (Optional) Modify Host Monitor
You can modify the configurations of Host Monitor, such as the service discovery, service port, or the interval at which data is collected.
2.1 Procedure
In the left-side navigation pane of the ARMS console, click Integration Management. On the Integrated Environments tab, click ECS Instance. Click the VPC ID and go to the environment details page.

Find the exporter that you want to modify and click Settings.
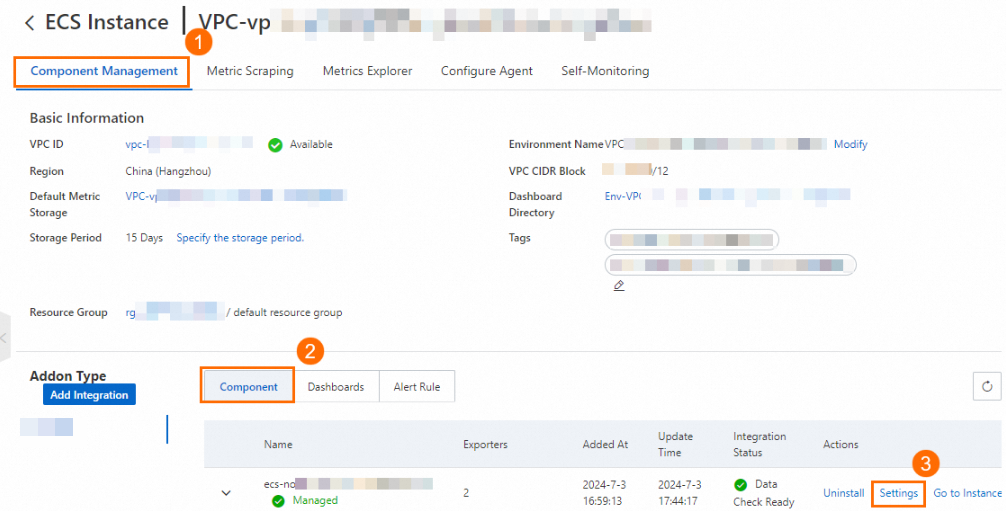
Modify the configurations based on your needs and click OK. For more information, see Monitor ECS instances.
2.2 Verification
Refresh the page and click Settings again to check whether the modification takes effect.
View the dashboards and check whether the data meets your expectations. For more information, see the 1.2 View the dashboards section.
3. (Optional) Discard metrics
You can discard metrics that you do not need to simplify data analysis and management.
3.1 Procedure
In the left-side navigation pane of the ARMS console, click Integration Management. On the Integrated Environments tab, click ECS Instance. Click the VPC ID and go to the environment details page.

In the Discard Metrics section of the tab, select the metrics that you want to discard and click Update. For information about metrics, see Metrics.
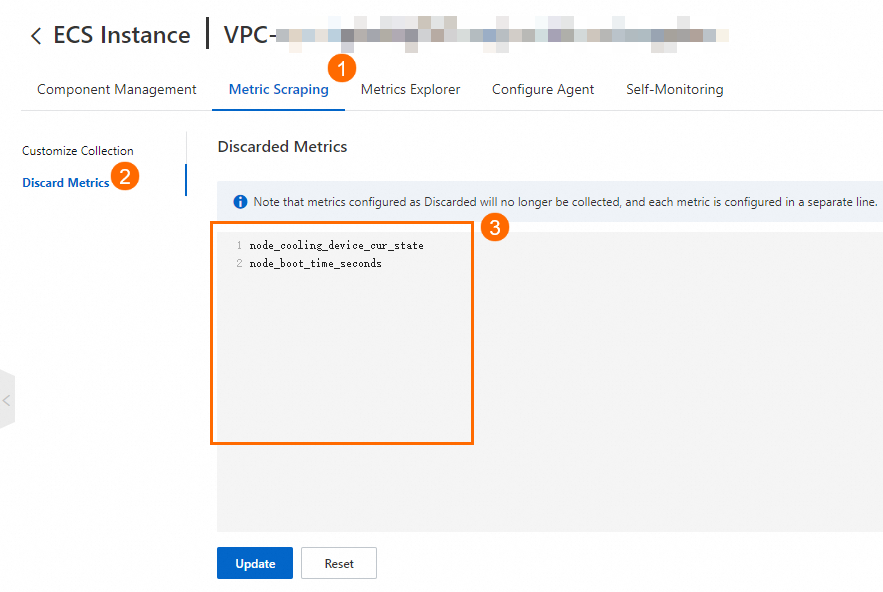 Note
NoteYou cannot discard the basic metrics about ACK clusters.
3.2 Verification
Click Update and refresh the page to check whether the modification takes effect.
View the dashboards and check whether the data meets your expectations. For more information, see the 1.2 View the dashboards section.
4. (Optional) Configure alerting
You can configure alert rules to monitor specific metrics. When an alert is triggered due to metric changes, you are notified in a timely manner. This facilitates routine maintenance and troubleshooting.
Managed Service for Prometheus provides built-in alert rules and custom alert rules. You can configure the built-in alert rules or existing custom alert rules, or add custom alert rules based on your business requirements.
4.1 Configure built-in alert rules
By default, the built-in alert rules generate alert events. You can manually configure alert notifications.
In the left-side navigation pane of the ARMS console, click Integration Management. On the Integrated Environments tab, click ECS Instance. Click the VPC ID and go to the environment details page.

In the Addon Type section of the Component Management tab, click Alert Rule. Click View Alert Event or Edit to view or modify an alert rule.
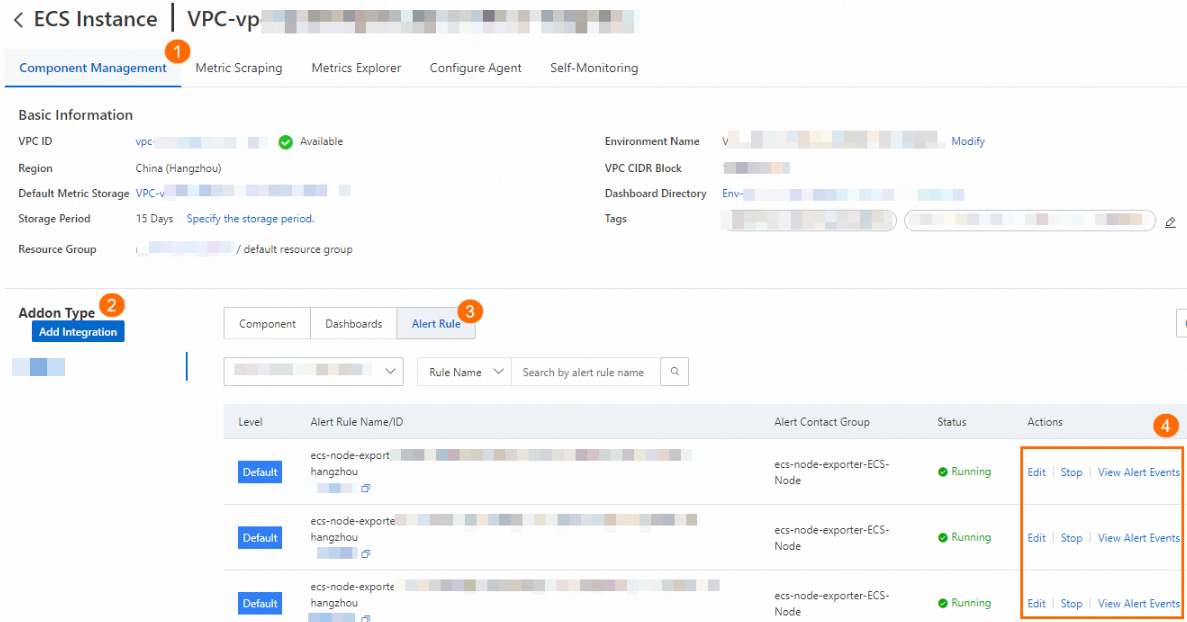
Modify the alert rule based on your needs and click OK. For more information, see Prometheus alert rules.
4.2 Configure custom alert rules
If the built-in alert rules cannot meet your business requirements, you can configure custom alert rules for the ECS instances.
In the left-side navigation pane of the ARMS console, click Integration Management. On the Integrated Environments tab, click ECS Instance. Click the VPC ID and go to the environment details page.

On the Component Management tab, click the VPC next to Default Metric Storage in the Basic Information section.
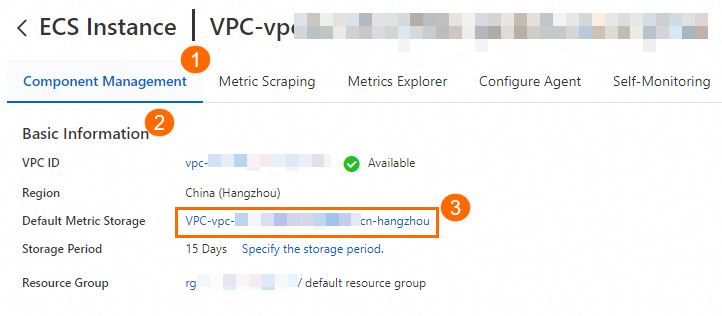
On the Alert rules page, you can create, modify, or view custom alert rules. For more information, see Prometheus alert rules.

4.3 Verification
Refresh the page to check whether the modification takes effect.
Configure an alert rule that is easy to be triggered and risk-free, and try to trigger the alert rule to check whether the alert rule meets your expectations.
NoteHow alert notifications are sent depends on the alert rule.