Service Mesh (ASM) allows you to modify a sidecar proxy by adding resource annotations. This topic describes how to configure a sidecar proxy by adding resource annotations and setting ProxyConfig fields.
Prerequisites
The cluster is added to the ASM instance. For more information, see Add a cluster to an ASM instance.
An ingress gateway is deployed. For more information, see Create an ingress gateway.
Add resource annotations
ASM allows you to modify a sidecar proxy by adding resource annotations. This topic describes how to configure a sidecar proxy by adding resource annotations and setting ProxyConfig fields. For more information about other annotations, see Appendix 1: Istio resource annotations.
Enable automatic sidecar proxy injection for the default namespace. For more information, see Enable automatic sidecar proxy injection.
Deploy an application in the default namespace. For more information, see Deploy an application in an ASM instance.
Modify the minimum memory of the sidecar proxy.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and choose in the left-side navigation pane.
On the Deployments page, find the application that you want to modify and choose in the Actions column.
In the Edit YAML dialog box, add the following content under the
templateparameter. Then, click Update.annotations: sidecar.istio.io/proxyMemory: 14Mi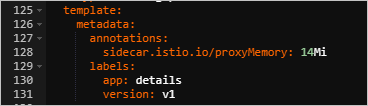
Check whether the memory of the sidecar proxy has been modified.
In the left-side navigation pane of the details page, choose .
On the Pods page, find the pod that you want to view and click View Details in the Actions column.
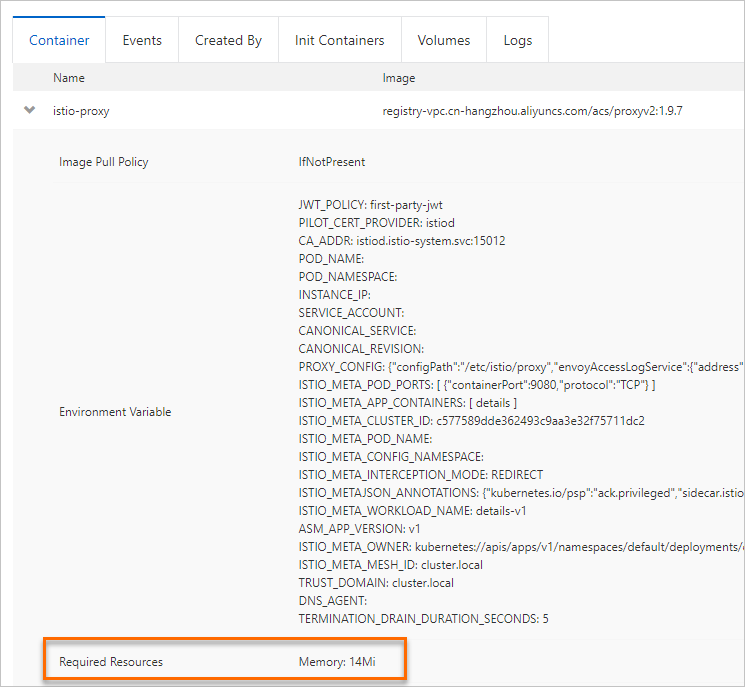
On the Container tab, click istio-proxy.
You can see that the required memory for the istio-proxy container is 14 MiB.
Set ProxyConfig fields
ASM allows you to configure a sidecar proxy by modifying ProxyConfig fields in a pod. For more information about ProxyConfig fields, see Appendix 2: ProxyConfig fields.
The value of the proxy.istio.io/config annotation is in the YAML format or JSON format.
The procedure for setting ProxyConfig fields is similar to that for adding resource annotations. For more information, see the steps described in the "Add resource annotations" section. In this example, common ProxyConfig fields are used.
Example 1: Set the termination drain duration
You can modify the termination drain duration by setting the terminationDrainDuration field. The termination drain duration indicates the amount of time that the istio-proxy container waits for before it is killed or shut down when the application container is terminated.
Add the following content to the YAML file of the application. When the application container is terminated, the istio-proxy container waits for 3 seconds.
annotations:
proxy.istio.io/config: |
terminationDrainDuration: 3s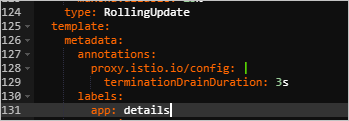
On the Pods page, find the pod that you want to view and click View Details in the Actions column. On the Container tab, click istio-proxy. You can see that the termination drain duration is 3 seconds.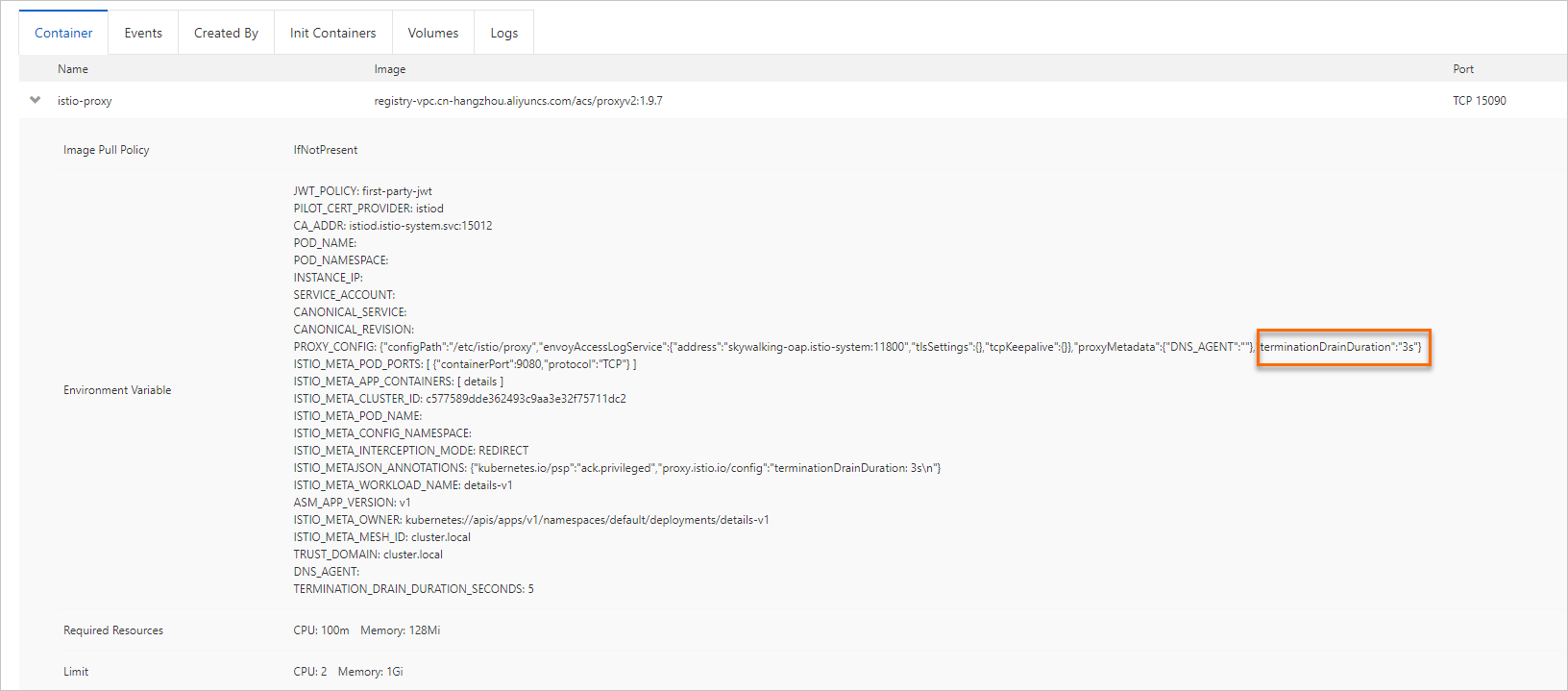
Example 2: Set the start sequence of the istio-proxy container
By default, the holdApplicationUntilProxyStarts field is set to true globally in ASM to ensure that the istio-proxy container has been started before the pod is started. If the istio-proxy container is not started when the pod is started, the pod fails to receive traffic.
holdApplicationUntilProxyStarts is used to control the start behavior of the application container after a sidecar proxy is injected. When the holdApplicationUntilProxyStarts is set to true, the Istio Container Network Interface (CNI) plug-in or the sidecar injector modifies the Kubernetes pod YAML to prevent the application container from starting until the istio-proxy container is ready to receive traffic. This ensures that all traffic goes through the istio-proxy container before the pod receives traffic, enabling traffic management, monitoring, and security policies to take effect immediately. In most cases, we recommend that you set holdApplicationUntilProxyStarts to true to ensure that network traffic is properly managed. In some special cases, setting holdApplicationUntilProxyStarts to false may be more appropriate.
On the Pods page, find the pod that you want to view and click View Details in the Actions column. Click the Events tab. Then, you can see that the istio-proxy container is started after the pod is started.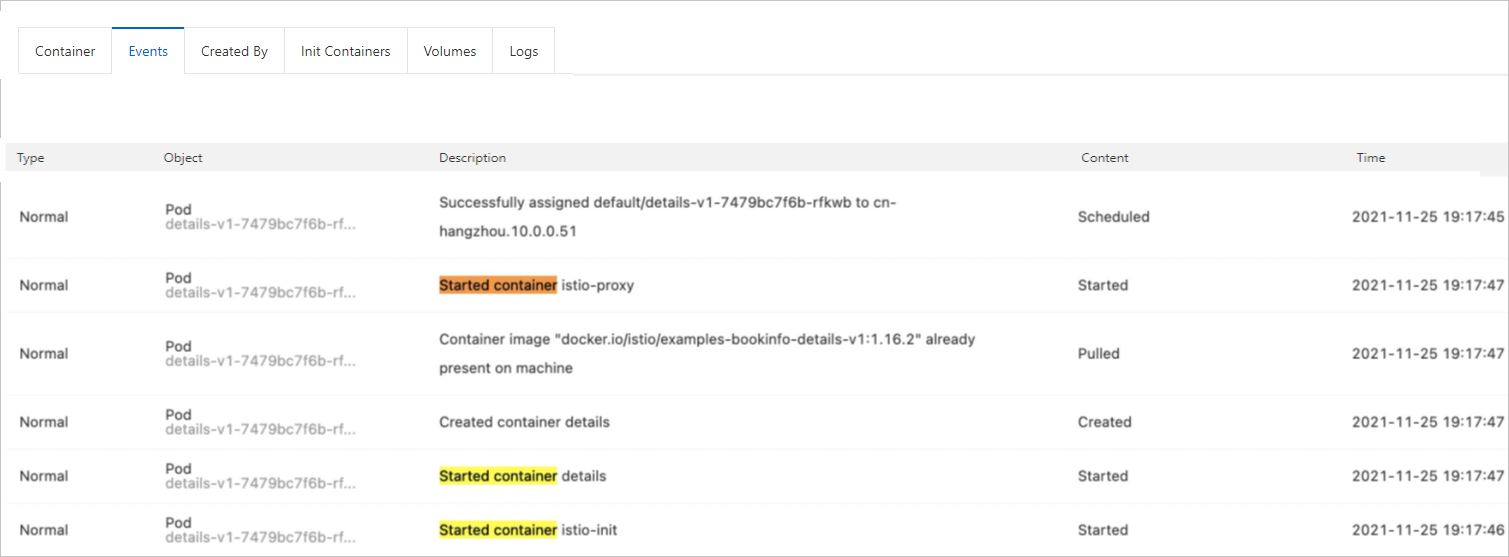
Appendix 1: Istio resource annotations
Annotation | Description |
proxy.istio.io/config | Overrides the proxy configuration. |
readiness.status.sidecar.istio.io/applicationPorts | Specifies the list of ports exposed by the application container. This annotation is used by a sidecar proxy readiness probe to determine whether the sidecar proxy is configured and ready to receive traffic. |
readiness.status.sidecar.istio.io/failureThreshold | Specifies the failure threshold for the sidecar proxy readiness probe. |
readiness.status.sidecar.istio.io/initialDelaySeconds | Specifies the initial delay for the sidecar proxy readiness probe. Unit: seconds. |
readiness.status.sidecar.istio.io/periodSeconds | Specifies the period for the sidecar proxy readiness probe. Unit: seconds. |
sidecar.istio.io/componentLogLevel | Specifies the component log level for the sidecar proxy. |
sidecar.istio.io/enableCoreDump | Specifies whether to enable core dump for the sidecar proxy. |
sidecar.istio.io/extraStatTags | The list of additional tags extracted from the in-proxy Istio telemetry. Each additional tag needs to be present in this list. |
sidecar.istio.io/inject | Specifies whether to enable automatic sidecar proxy injection. |
sidecar.istio.io/interceptionMode | Specifies the mode (REDIRECT or TPROXY) used to redirect inbound traffic to Envoy. |
sidecar.istio.io/logLevel | Specifies the log level for the sidecar proxy. |
sidecar.istio.io/proxyCPU | Specifies the requested CPU setting for the sidecar proxy. |
sidecar.istio.io/proxyCPULimit | Specifies the CPU limits for the sidecar proxy. |
sidecar.istio.io/proxyMemory | Specifies the requested memory setting for the sidecar proxy. |
sidecar.istio.io/proxyMemoryLimit | Specifies the memory limits for the sidecar proxy. |
sidecar.istio.io/rewriteAppHTTPProbers | Rewrites HTTP readiness and liveness probes to be redirected to the sidecar proxy. |
status.sidecar.istio.io/port | Specifies the HTTP status port of the sidecar proxy. If the port number is 0, the sidecar proxy does not provide status. |
traffic.sidecar.istio.io/excludeInboundPorts | The comma-separated list of inbound ports to be excluded from traffic redirection to the sidecar proxy. This annotation is valid only when all inbound traffic is redirected to the sidecar proxy. The wildcard (*) indicates any inbound port. |
traffic.sidecar.istio.io/excludeOutboundIPRanges | The comma-separated list of CIDR blocks to be excluded from outbound traffic redirection to the sidecar proxy. This annotation is valid only when all outbound traffic is redirected to the sidecar proxy. The wildcard (*) indicates any CIDR block. |
traffic.sidecar.istio.io/excludeOutboundPorts | The comma-separated list of outbound ports to be excluded from traffic redirection to the sidecar proxy. |
traffic.sidecar.istio.io/includeInboundPorts | The comma-separated list of inbound ports for which traffic is to be redirected to the sidecar proxy. The wildcard (*) indicates any inbound port. An empty list indicates that the redirection of all inbound traffic to the sidecar proxy is disabled. |
traffic.sidecar.istio.io/includeOutboundIPRanges | The comma-separated list of CIDR blocks to redirect outbound traffic to the sidecar proxy. The wildcard (*) indicates any CIDR block. An empty list indicates that the redirection of all outbound traffic to the sidecar proxy is disabled. |
traffic.sidecar.istio.io/includeOutboundPorts | The comma-separated list of outbound ports for which traffic is to be redirected to the sidecar proxy. |
traffic.sidecar.istio.io/kubevirtInterfaces | The comma-separated list of virtual interfaces whose inbound traffic is treated as outbound traffic. |
Appendix 2: ProxyConfig fields
Field | Type | Description |
configPath | String | Specifies the path to the directory of the configuration file. The proxy agent generates the actual configuration and stores it in this directory. |
statsdUdpAddress | String | Specifies the IP address and port of a StatsD UDP listener. |
proxyAdminPort | Int32 | Specifies the port on which Envoy listens for administrative commands. The default port is port 15000. |
controlPlaneAuthPolicy | AuthenticationPolicy | Specifies how the proxy is authenticated when it connects to the control plane. The default value is |
concurrency | Specifies the number of worker threads to run. If this field is not specified, the number is automatically determined based on CPU requests and limits. If this field is set to 0, all cores on the machine are used. The default value is 2. | |
interceptionMode | InboundInterceptionMode | Specifies the mode in which inbound traffic is redirected to the sidecar proxy. |
tracing | Tracing | Specifies the tracing configuration of the sidecar proxy. |
sds | SDS | Specifies the secret discovery service (SDS) configuration of the sidecar proxy. |
proxyMetadata | Map<string, string> | Specifies additional environment variables for the sidecar proxy. Variables whose names start with ISTIO_META_ are included in the generated bootstrap and sent to the XDS server. |
statusPort | Map<string, string> | Specifies the port on which the sidecar proxy should listen for administrative commands such as readiness probe. The default port is port 15020. |
terminationDrainDuration | Specifies the amount of time allowed for connections to complete on proxy shutdown. After SIGTERM or SIGINT is received, istio-agent tells the active Envoy to start draining, preventing new connections and allowing existing connections to complete. Then, istio-agent sleeps for the termination drain duration and then kills the remaining active Envoy processes. The default value is 5. Unit: seconds. | |
holdApplicationUntilProxyStarts | Specifies the Boolean flags for enabling or disabling the holdApplicationUntilProxyStarts behavior. This feature adds hooks to delay application startup until the pod proxy is ready to accept traffic, mitigating some startup race conditions. |