This topic describes the common scenarios in which service providers use Compute Nest, and the benefits when Compute Nest is used in these scenarios.
Efficient and automated application delivery and deployment
In traditional solutions, you need to perform manual or semi-automated operations to create cloud resources and deploy applications. This process is complex and requires expert knowledge of cloud services. You can use Compute Nest to deploy services in the following scenarios:
Applications are associated with a large number of cloud services, such as Virtual Private Cloud (VPC), Elastic Compute Service (ECS), ApsaraDB RDS, Server Load Balancer (SLB), ApsaraDB for Redis, and File Storage NAS (NAS).
Service deployment involves complex operations. For example, you need to configure Java Development Kit (JDK) and servers before you deploy services.
Service deployment requires skilled technical support personnel. If the personnel is not familiar with the deployment procedure, errors such as invalid ports and version errors may occur. New technical support personnel must be familiar with the deployment procedure before the personnel makes an attempt to deploy the service.
Service management involves complex operations. After you create cloud resources for services, you need to manage each resource in the related console. For example, before you scale in or scale out clusters, you need to view the resource status in the related consoles.
The following flowchart walks you through the deployment process of a traditional solution.
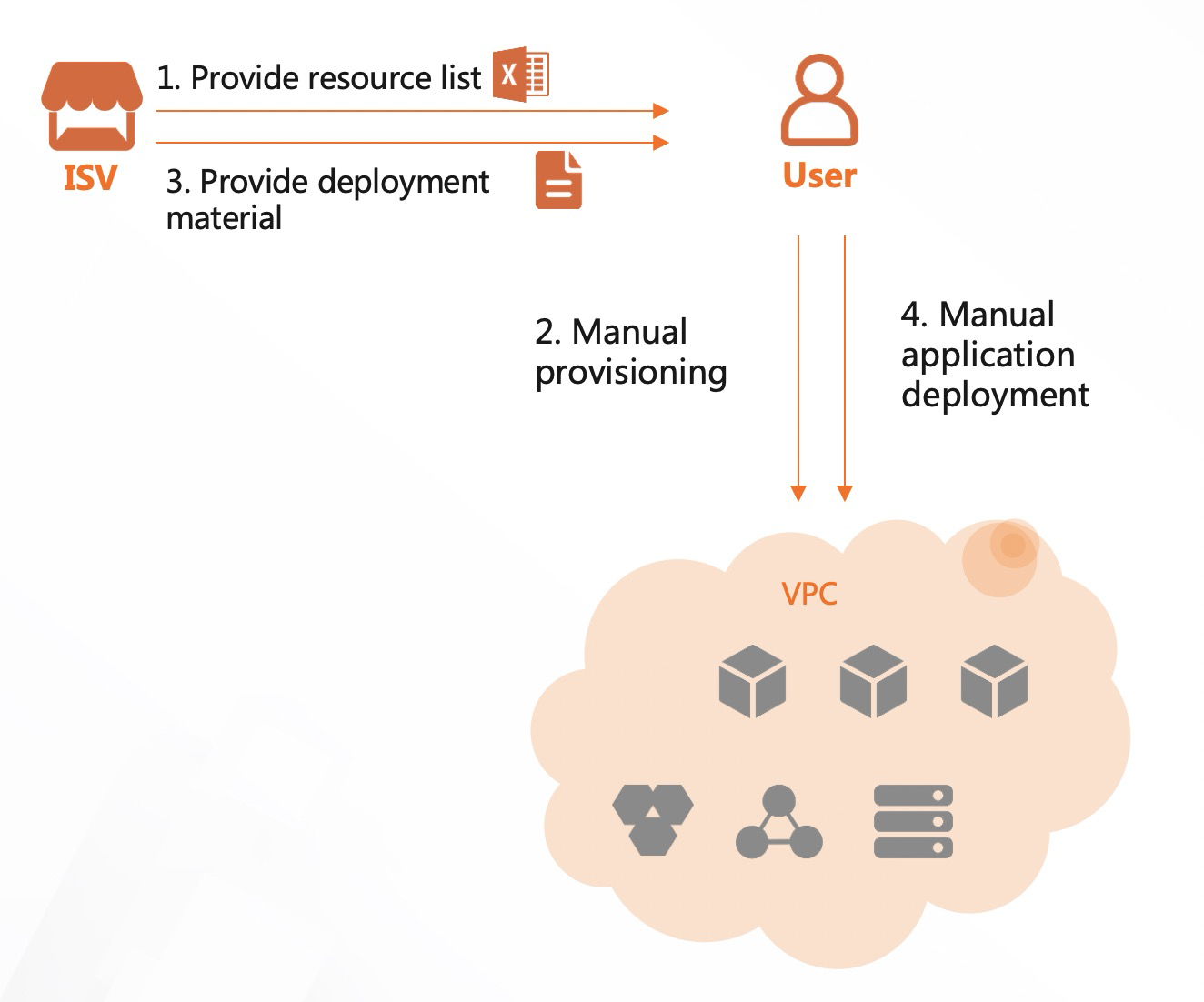
Compute Nest automates application delivery so that you can deliver and deploy applications in an intelligent and efficient manner. Compute Nest also automates service deployment. After Alibaba Cloud users subscribe to services, Compute Nest deploys the services. Compared with traditional solutions, Compute Nest simplifies the deployment procedure and reduces costs. For more information, see Benefits.
Secure and efficient application O&M
In traditional O&M solutions, you need to perform complex operations to implement O&M for services and cannot trace the operations on the services. In this case, data security cannot be ensured. You can use Compute Nest to implement O&M for services in the following scenarios:
You need a long period of time to detect faults based on the feedback from customers. If you are not familiar with the resource and application platforms, cross-platform troubleshooting cannot be performed in time. As a result, the services are interrupted for a long period of time.
Your customers and you need to modify security and network configurations, and enable or disable the O&M channel during O&M. This requires complex operations. As a result, network and security may be affected due to improper operations.
You need to log on to the servers of customers. However, you must obtain the logon permissions from your customers and exchange the logon credentials with your customers in plaintext. Incidents or improper management may cause security breaches that are related to customer credentials. As a result, you cannot ensure data security for customers.
You cannot trace and record the operations that are performed on services. When errors occur in the services, your customers and you cannot determine the causes of the errors.
The following flowchart walks you through the O&M process of a traditional solution.
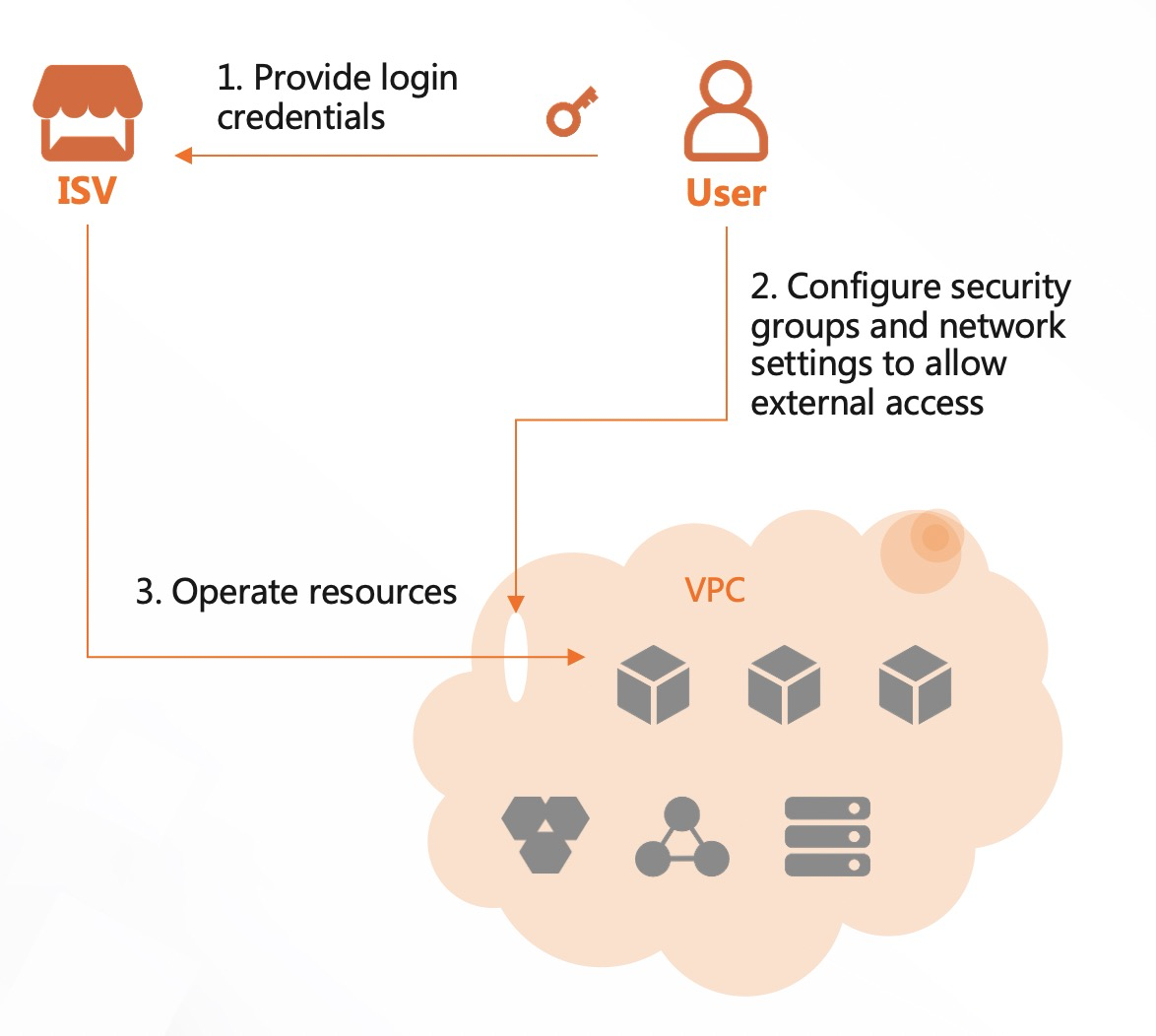
Compute Nest establishes a secure O&M channel between your customers and you based on a secure authorization and automatic authentication mechanism. In addition, Compute Nest generates logs and screen recordings to record the entire O&M process to prevent disputes. For more information, see Benefits.