By Afzaal Ahmad Zeeshan, Alibaba Cloud Community Blog author.
Auditability and traceability are two of the most integral and useful concepts which help developers and ops to collaborate within teams productively and throughout the enterprise. Dealing with increasing workloads and large applications is challenging and critical, teams require a mechanism that can help them track changes and actions in a manageable way. A smart action monitoring and tracking system in any systematic process enable users to collect vital information to track and analyze security and compliance checks.
Similarly, the growing demand for cloud services and the control of adding customized features introduce an overhead towards security as well as action credibility, which are being performed at any point in time. Cloud action and activity trailing service help users to enable granular-level security, compliance, and risk auditing of all the cloud services to which the user is subscribed. In this article, we will explore how Alibaba Cloud ActionTrail service aims to help a live product to track the underlying details of an event, including the action taken by the user, user role, location, IP, port and time. Activities which are occurred in any of your cloud services, it will be recorded and stored to OSS buckets.
We study the ActionTrail product and its application to DevSecOps environments to introduce security and compliance to products. We will look at how ActionTrail can help a live product, that I deployed in one of the previous articles that I wrote on Alibaba Cloud blog to deploy a MariaDB TX on Alibaba Cloud¡ªto be tracked for changes.
As mentioned earlier, ActionTrail is an Alibaba Cloud service that records and stores all the actions happening on your Alibaba Cloud resources. This information is beneficial for the operations related to security analysis, change tracking, and compliance audits. It tracks all the API call records, which are even triggered from the console throughout your infrastructure. These records are stored in OSS buckets as per your customized settings and later can be archived using OSS provided archiving and data management features.
There are primarily two types of actions that happen in Alibaba Cloud for your subscription:
We will study the differences in these event types as well as their overall impact of these two types on our infrastructure.
All your actions are being recorded and documented daily to provide you with a thorough history of actions of your Alibaba Cloud resources. These records can be fetched using multiple parameters such as resource type, operation location, time, username, etc.
ActionTrail provides visibility and detailed information about all your Alibaba Cloud services. This information plays an integral role when there is a need for service roll-back and state restoration. You can view, search, store, and analyze the action trail logs related to the activities made across your Alibaba Cloud infrastructure. For instance, you can know who took what action and what are the responses by your services over the event.
ActionTrail keeps your actions in their own regions, so they are not grouped together in a single portal. You must visit the ActionTrail instance for each of the groups and review the actions being there. For example, actions taken for the resources in the Singapore region will not show up in the China region, and so on.
By default, you can view and query records for the last 30 days. However, if you require records for a more extended period, then you can create and specify either log service or OSS bucket intending to store your actions and records for a longer period.
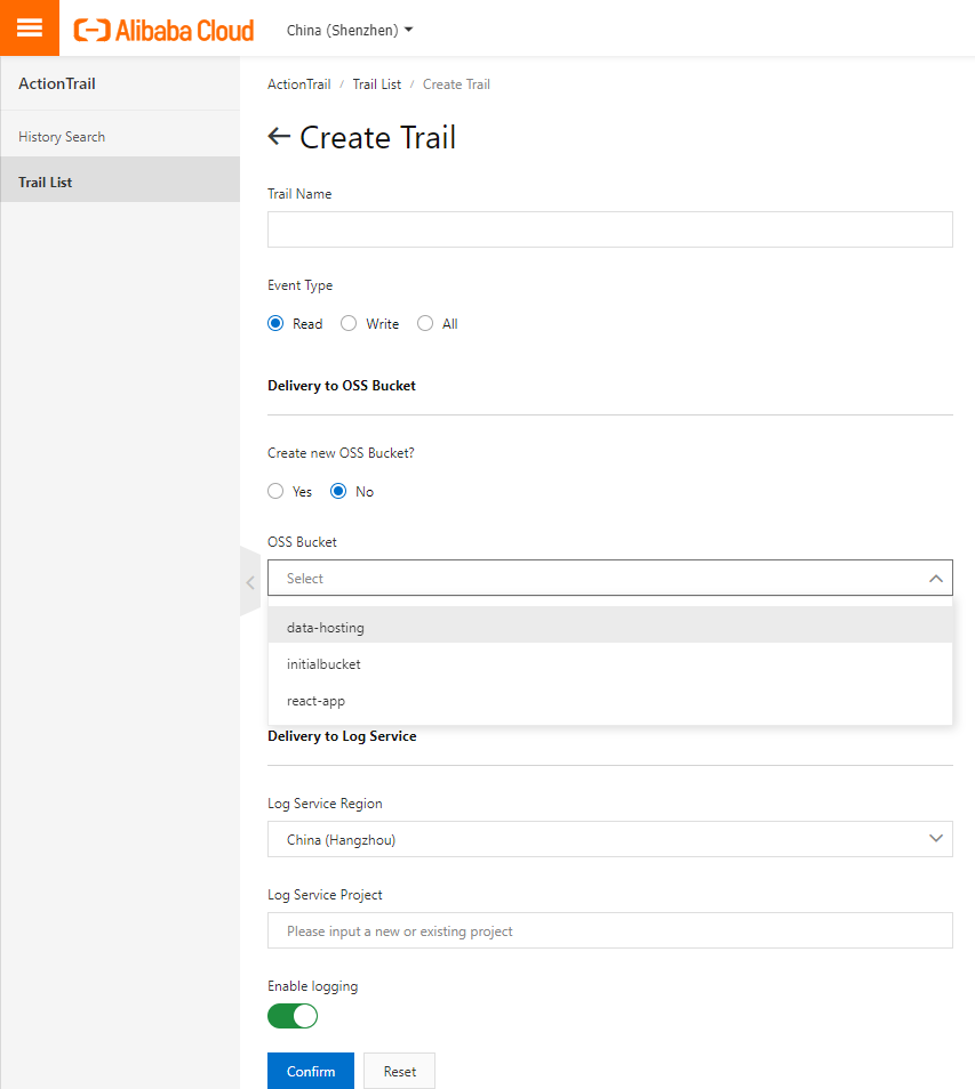
Creation is simple and follows many handy steps. After creating a trail, you specify the region (by default the selected region becomes the home region for the created trail) then you need to select either you want to store records in the Log Service or in the OSS bucket (which can be created on the go or you can use your existing bucket). Log service stores logs in a JSON format while in OSS buckets as compressed JSON records.
Almost all the major resources are supported by the ActionTrail; ECS, CDN, ApsaraDB RDS, Resources Access Management, and Server Load Balancer. If any instance stops working, you can refer to ActionTrail logs to track whether the reason was due to any human intervention. If ApsaraDB RDS instance is down; you can view which action is responsible; furthermore, you can know if that was an intentional action or happened mistakenly by investigating action IP, location, and username.
Here is a list of the actions that had taken place in my own subscription over the previous 30 days¡ªI have not added the Trail buckets to store the logs and actions so I am limited by 30 days, you can extend this to more days¡ªand that shows all the list of the actions.
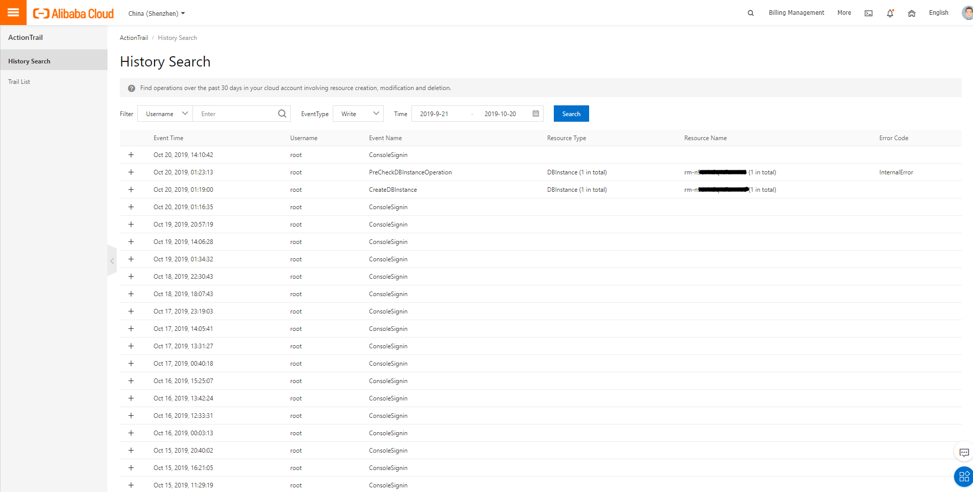
A couple of things to note are that these are only the write events. Write events are the type of events that change your infrastructure in any way. Read events are the kind of events that show when someone was reading about your infrastructure¡ªit might be a security risk if the user is not an intended user, you can read their username to see if they are. The read-only events can help you check who reviewed your products and services. For example, in the following list, you can see that the events returned are the type of service description and reviews.
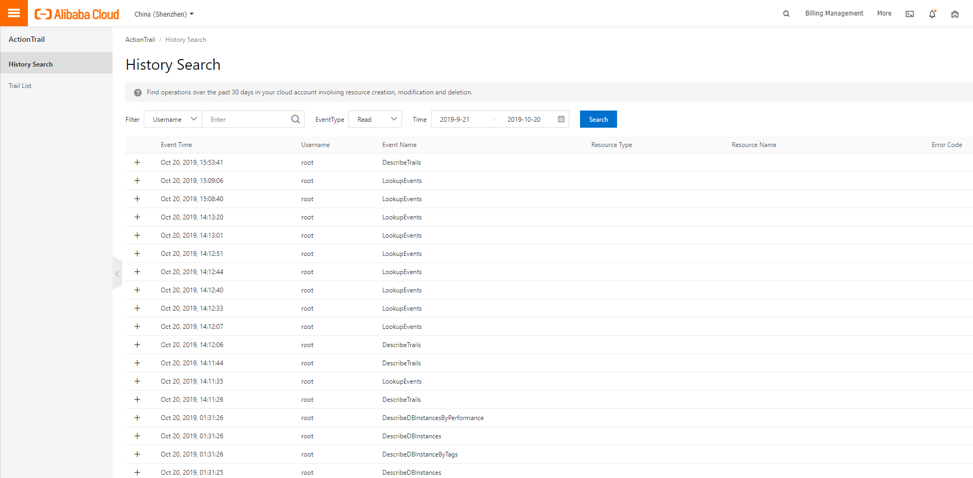
Expanding these individual items can further express the details about each action.
You can even further dig down and explore the event details by clicking on the button, "View event".
Moreover, you can audit your members' profiles using detailed records provided by ActionTrail and see each member who is either managed using Alibaba Cloud Resource Access Management or otherwise.
In the time of service failure, especially after some changes or upgrades by humans¡ªtypically an error involves human intervention¡ªthe very first step to take is reverting the production environment back to its previously functional point. In such events, having detailed and managed action logs are crucial to know the exact step, after which the instance crashed or fell in an abnormal state.
At times of disaster and service breakdown, one of the significant concerns which come into question is the system security; that if the responsible action has been taken by a privileged member or someone from outside the organization. If log says the contrary, then instead of fixing the issue, investigation about the security breach becomes the highest priority to ignore any further downplay this is one of the most important roles of ActionTrail.
One thing to note here is that ActionTrail itself does not perform any reverts for the actions, as ActionTrail only saves the logs for actions as they happen. It will be your responsibility to revert the actions, such as removing or creating the resource instances again. In this manner, ActionTrail is a perfect tool for post-mortem, but cannot prevent the actions from being taken¡ªfor which, RAM would be a great resource, and I will write about it in a later article.
To summarize quickly, here are all the top-tier features and benefits provided by Alibaba Cloud ActionTrail:
Although ActionTrail is just about the collection of the actions that take place in your infrastructure, they can still be helpful in several cases where you might want to explore how your infrastructure is being used.
From my personal experience, I can enlist a scenario where the client of one of my friends was using a cloud-hosted solution for their infrastructure needs. They discovered that their cloud infrastructure bill was at least 5-8 times more than what they were billed previously each week. They used a similar tool on that platform to identify the source IPs being used as well as the user accounts whose credentials have been exposed and were being used by the hackers to create resources on the cloud and causing them extra charges. Cloud vendor was happy to wave off the charges, and they were able to do so only because the client had the proof of the source IP addresses¡ªthat were not one of their own. In a similar fashion, you can also be saved from such actions that can cost you money or can potentially cause problems for your business.

9 posts | 1 followers
FollowAlibaba Cloud Community - August 12, 2024
Rupal_Click2Cloud - December 14, 2023
Rupal_Click2Cloud - September 8, 2023
Alibaba Cloud New Products - August 20, 2020
Alibaba Clouder - April 26, 2019
Alibaba Cloud Community - August 26, 2025

9 posts | 1 followers
Follow ActionTrail
ActionTrail
A service that monitors and records the actions of your Alibaba Cloud account, including the access to and use of Alibaba Cloud services using the Alibaba Cloud Management console, calling API operations, or SDKs.
Learn More Managed Service for Prometheus
Managed Service for Prometheus
Multi-source metrics are aggregated to monitor the status of your business and services in real time.
Learn More Application Real-Time Monitoring Service
Application Real-Time Monitoring Service
Build business monitoring capabilities with real time response based on frontend monitoring, application monitoring, and custom business monitoring capabilities
Learn More Resource Management
Resource Management
Organize and manage your resources in a hierarchical manner by using resource directories, folders, accounts, and resource groups.
Learn MoreMore Posts by afzaalvirgoboy