By Francis Ndungu, Alibaba Cloud Tech Share Author. Tech Share is Alibaba Cloud's incentive program to encourage the sharing of technical knowledge and best practices within the cloud community.
Multi-factor Authentication (MFA) is a process of confirming the identity of a user in a system by validating two or more pieces of login information. While MFA is commonly used in GUI-based systems, it works pretty well on Linux servers.
MFA can strengthen the security of your Linux server by compensating weaknesses associated with a single form of authentication e.g. passwords that can be broken by brute-force or other methods.
MFA relies on the fact that there is no perfect authentication method and 3 basic elements are therefore used:
Any server holding classified information (e.g. financial data), should implement MFA for compliance purposes and to minimize threats from hackers.
In this article, we will show you how to enable Multi-factor Authentication on your Ubuntu 16.04 server running on Alibaba Cloud Elastic Compute Service (ECS).
We will use Google Authenticator (Pluggable Authentication Module) PAM module to accomplish the task.
Locate the Public IP address associated with your Alibaba ECS instance and login to your server via an SSH client.
Google Authenticator PAM module is a software that offers authentication verification using One Time Password (OTP). The module works hand in hand with a mobile-based OTP generator available for iOS, Android and Blackberry phones.
So, before you install the module on your Linux server, download the app from App store, PlayStore or BlackBerry World depending on the Operating System of your mobile phone.
Next, we need to install the PAM module on the server. It is available on the Ubuntu software repository and we can install it using apt command. Before we do this, let's update the package information index:
$ sudo apt-get updateThen, run the command below to install the software:
$ sudo apt-get install libpam-google-authenticatorPress Y and hit Enter when prompted to continue.
We can now go ahead and create secret keys for users using a helper app that comes with PAM module.
Please note, this is not a system wide key, you must generate a new key for each user that requires multi-factor authentication.
While logged as the user that you want to enable MFA for, run the command below:
$ google-authenticatorThe helper app will ask you if you want authentication tokens to be time-based. Press Y and hit Enter.
Do you want authentication tokens to be time-based (y/n) yNext, a new secret key and a QR code will be generated as shown below. You can either enter this key manually on your phone or scan the QR code with your Google Authenticator app that you downloaded earlier.
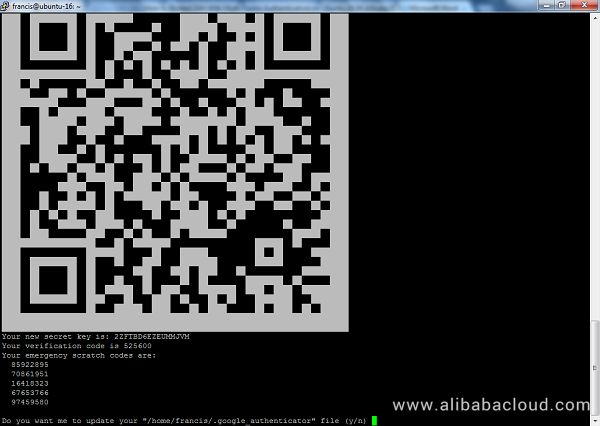
5 emergency scratch codes are provided. Keep them in a secure place because you can use them to gain access to your system should you lose your Google App. The scratch codes can only be used once.
Then, press Y and hit Enter to answer the question below:
Do you want me to update your "/home/<username>/.google_authenticator" file (y/n) yThe above will allow the module to save the key on the google_authenticator file associated with the current logged in user.
Next, answer Y on the below question to force automatic expiration of a code once it is used. This will prevent a replay attack in case a previously used code gets to the wrong hands.
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases
your chances to notice or even prevent man-in-the-middle attacks (y/n) yNext answer n in order to allow only 3 valid codes for a 1:30min window period:
By default, tokens are good for 30 seconds and in order to compensate for
possible time-skew between the client and the server, we allow an extra
token before and after the current time. If you experience problems with poor
time synchronization, you can increase the window from its default
size of 1:30min to about 4min. Do you want to do so (y/n)nTo limit users to only 3 login attempts in a time span of 30 seconds, answer Y on the below question. This will prevent brute-force attacks:
If the computer that you are logging into isn't hardened against brute-force
login attempts, you can enable rate-limiting for the authentication module.
By default, this limits attackers to no more than 3 login attempts every 30s.
Do you want to enable rate-limiting (y/n) yThe Google PAM module is now configured for the current user.
Next, we are going to configure SSH to support MFA. First, we are going to edit the file /etc/pam.d/sshd using a nano editor. Run the command below:
$ sudo nano /etc/pam.d/sshdThen, add the below line at the bottom of the file:
auth required pam_google_authenticator.so nullokThe value nullok allows users without the Google Verification App to login. You should delete this value once you have completely setup MFA for all users on your Ubuntu 16.04 server to make it mandatory for them to use the verification code when logging in.
The line will look like this without the value:
$ auth required pam_google_authenticator.so Press CTRL+X, Y and Enter to save the file:
Next, we will configure the SSH daemon to accept Google PAM authentication:
$ sudo nano /etc/ssh/sshd_configFind ChallengeResponseAuthentication and change its value from no to yes:
ChallengeResponseAuthentication yesRestart the SSH daemon for the changes to take effect:
$ sudo systemctl restart sshdYou can now open another terminal window and try to SSH to your Ubuntu 16.04 server. Now, apart from the password prompt, you will be required to enter a verification code which you must obtain from your Google Authenticator app (2 forms of authentication).
Please note, if you have not created an SSH key for the user (You can refer to this guide under the section about creating authentication key pair for logging to your Ubuntu 16.04 server), you will not be prompted to enter a password or a verification code. This is because the SSH key overrides all other authentication methods.
To disable this default behaviour, open the /etc/ssh/sshd_config file again.
$ sudo nano /etc/ssh/sshd_configAt the bottom of the file, add the below line:
AuthenticationMethods publickey,password publickey,keyboard-interactiveThis tells SSH that we need all 3 forms of authentication: public key, password and keyboard-interactive.
Restart SSH daemon again:
$ sudo systemctl restart sshdNow, if you try to login again, you will be authenticated using your public key but you will still be prompted to enter your Password and Verification Code from the Google Authenticator app.
That is, 3 forms of authentication:
Example:
Using username "johndoe".
Authenticating with public key "johndoe"
Further authentication required
Using keyboard-interactive authentication.
Password: <enter password>
Using keyboard-interactive authentication.
Verification code: <enter verification code>If you don't want to supply a password during authentication, open the PAM configuration file /etc/pam.d/sshd again:
$ sudo nano /etc/pam.d/sshdComment the line @include common-auth by adding a pound (#) symbol at the beginning:
#@include common-authSave and close the file by pressing CTRL+X, Y and Enter.
If you SSH to your Ubuntu 16.04 server again, you will be authenticated using the public key and the verification code only (2 factor authentication).
That's all when it comes to setting up MFA on your Ubuntu 16.04 server.
In this guide, we have taken you through the steps of securing your Ubuntu 16.04 Alibaba ECS with multi-factor authentication. We have shown you how to setup the Google PAM module and helper program to create secret codes for each user that requires MFA.
Depending on the security level that you want on your server, you can enable all 3 forms of authentication (public key, password and verification code), or just 2 forms (public key and verification code).
We believe this guide will help you to add another layer of security to your Ubuntu 16.04 ECS instance.

31 posts | 8 followers
Followfrancisndungu - May 29, 2019
Alibaba Clouder - June 11, 2018
Alibaba Clouder - June 13, 2019
Alibaba Clouder - April 19, 2018
Alibaba Clouder - June 11, 2019
- November 14, 2017

31 posts | 8 followers
Follow Alibaba Cloud Linux
Alibaba Cloud Linux
Alibaba Cloud Linux is a free-to-use, native operating system that provides a stable, reliable, and high-performance environment for your applications.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by francisndungu