By Hitesh Jethva, Alibaba Cloud Community Blog author.
Penetration testing, sometimes shortened to pen testing, is one of the most important tasks for an administrator to find the vulnerability of server. OpenVAS, short for Open Vulnerability Assessment System, is a well-known open-source vulnerability scanner that allows you to scan your system for thousands of known vulnerabilities. OpenVas is a powerful tool that is capable of scanning remote machines as well as local machine, and it provides lots of plugins written in the Nessus Attack Scripting Language that can be used to extend the functionality of OpenVas scanner. OpenVAS is divided into three parts OpenVAS Scanner, OpenVAS Manager, and OpenVAS CLI. OpenVAS is an alternative to other commercial security scanners like Nessus and QualysGuard.
OpenVas comes with Greenbone Security Assistant, which is a web-based interface used to manage OpenVas through a web interface.
Now that we are on the same page, let's discuss what we will do in this tutorial. So you'll be installing Openvas on two Alibaba Cloud Elastic Compute Service (ECS) instances with Ubuntu 16.04 installed.
For this tutorial, you will need the following items:
For reference, see create a new ECS instance and connect to your instance. Also, once you are logged into your Ubuntu 16.04 instance, you can run the apt-get update -y command to update your base system with the latest available packages.
By default, OpenVas is not available in the Ubuntu 16.04 default repository. So, you will need to add the OpenVas repository to your system. To do so, follow these steps:
You can add it with the add-apt-repository ppa:mrazavi/openvas command.nce the repository is added, update the repository and install OpenVas with the following command:
apt-get update -y
apt-get install openvas9 -yDuring the installation, you will be asked to configure Redis database for OpenVas as shown below:
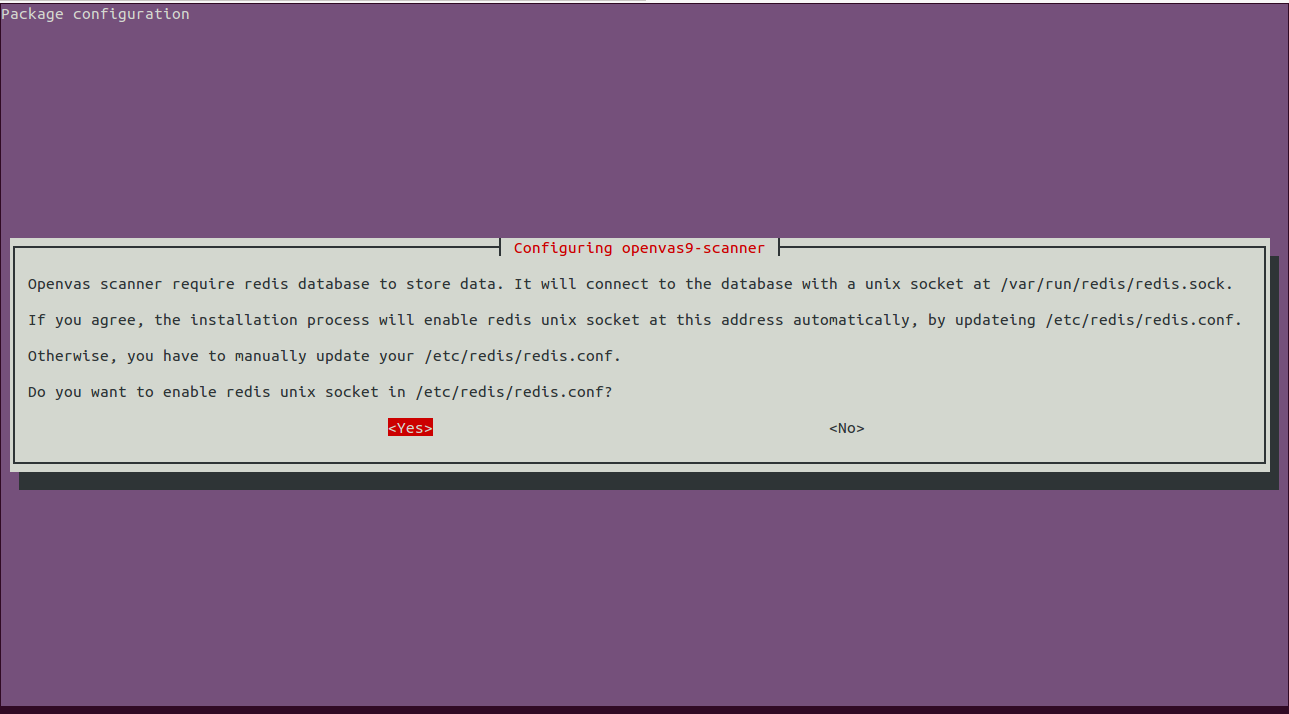
Click on the Yes button to finish the installation.
Next, you will need to install SQLite 3 database package to store the Common Vulnerabilities and Exposures (CVE) data and some other packages for the PDF report to work. You can install all of them by running the following command:
apt-get install texlive-latex-extra --no-install-recommends -y
apt-get install texlive-fonts-recommended sqlite3 -yNext, you will need to download the Network Vulnerability Tests from OpenVAS Feed with the following command:
greenbone-nvt-syncNext, sync security content automation protocol data and cert vulnerability data by running the following command:
greenbone-scapdata-sync
greenbone-certdata-syncNow, restart the OpenVAS scanner, OpenVas GSA and OpenVAS Manager with the following command:
service openvas-scanner restart
service openvas-manager restart
service openvas-gsa restartYou can check the status of OpenVas scanner with the service openvas-scanner status command. The output looks like the following:
● openvas-scanner.service - LSB: remote network security auditor - scanner
Loaded: loaded (/etc/init.d/openvas-scanner; bad; vendor preset: enabled)
Active: active (running) since Mon 2018-12-10 07:46:03 IST; 4s ago
Docs: man:systemd-sysv-generator(8)
Process: 27614 ExecStop=/etc/init.d/openvas-scanner stop (code=exited, status=0/SUCCESS)
Process: 27650 ExecStart=/etc/init.d/openvas-scanner start (code=exited, status=0/SUCCESS)
CGroup: /system.slice/openvas-scanner.service
├─27663 /usr/sbin/openvassd
├─27664 openvassd (Loading Handler
└─27665 /usr/sbin/openvassd
Dec 10 07:46:02 Node1 systemd[1]: Starting LSB: remote network security auditor - scanner...
Dec 10 07:46:03 Node1 systemd[1]: Started LSB: remote network security auditor - scanner.Also, check the status of OpenVas Manager with the service openvas-manager status command. The output looks like this:
● openvas-manager.service - LSB: remote network security auditor - manager
Loaded: loaded (/etc/init.d/openvas-manager; bad; vendor preset: enabled)
Active: active (running) since Mon 2018-12-10 07:46:35 IST; 4s ago
Docs: man:systemd-sysv-generator(8)
Process: 27686 ExecStop=/etc/init.d/openvas-manager stop (code=exited, status=0/SUCCESS)
Process: 27698 ExecStart=/etc/init.d/openvas-manager start (code=exited, status=0/SUCCESS)
CGroup: /system.slice/openvas-manager.service
└─27707 openvasmd: Initializing
Dec 10 07:46:35 Node1 systemd[1]: Starting LSB: remote network security auditor - manager...
Dec 10 07:46:35 Node1 systemd[1]: Started LSB: remote network security auditor - manager.Finally, rebuild the OpenVAS database, so the manager can access the NVT data downloaded previously with the openvasmd --rebuild --progress command. Next, you will need to change the default password of admin user to prevent unauthorized access. You can do this with the following command:
openvasmd --user=admin --new-password=admin@123OpenVas is now installed and configured, so it's time to use it to scan your OpenVas server for vulnerabilities. To do so, follow these steps:
Open your web browser and type the address https://172.20.10.6:4000. You will be redirected to the following page:
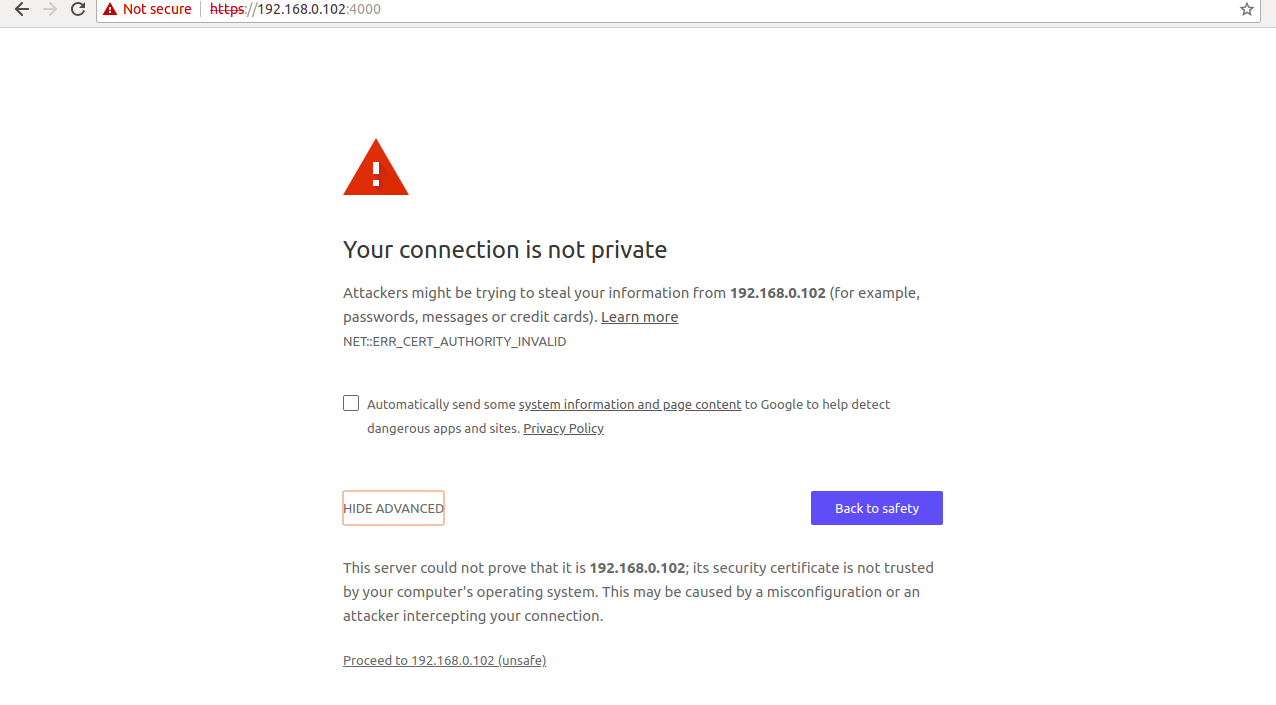
Here, you will need to verify the OpenVAS self-signed SSL certificate. After verifying the certificate, you will be redirected to the following page:
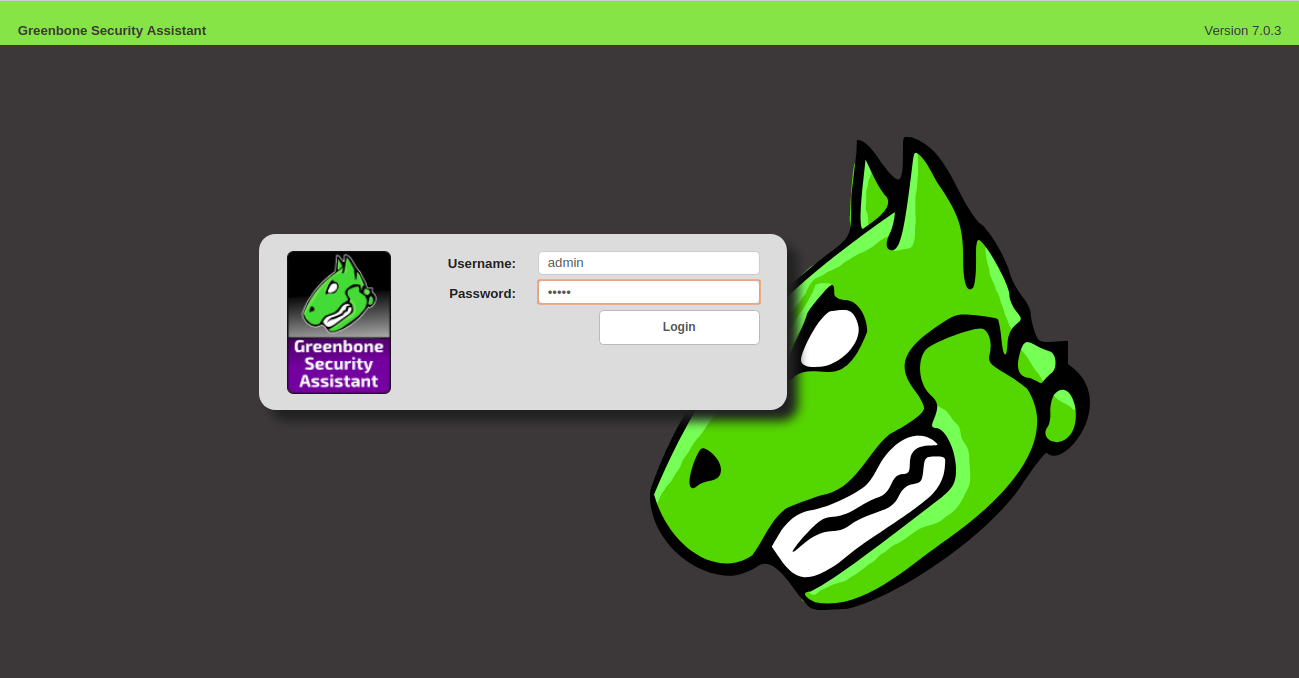
Here, provide your admin username and password, then click on the Login button. You should see the OpenVas dashboard in the following page:
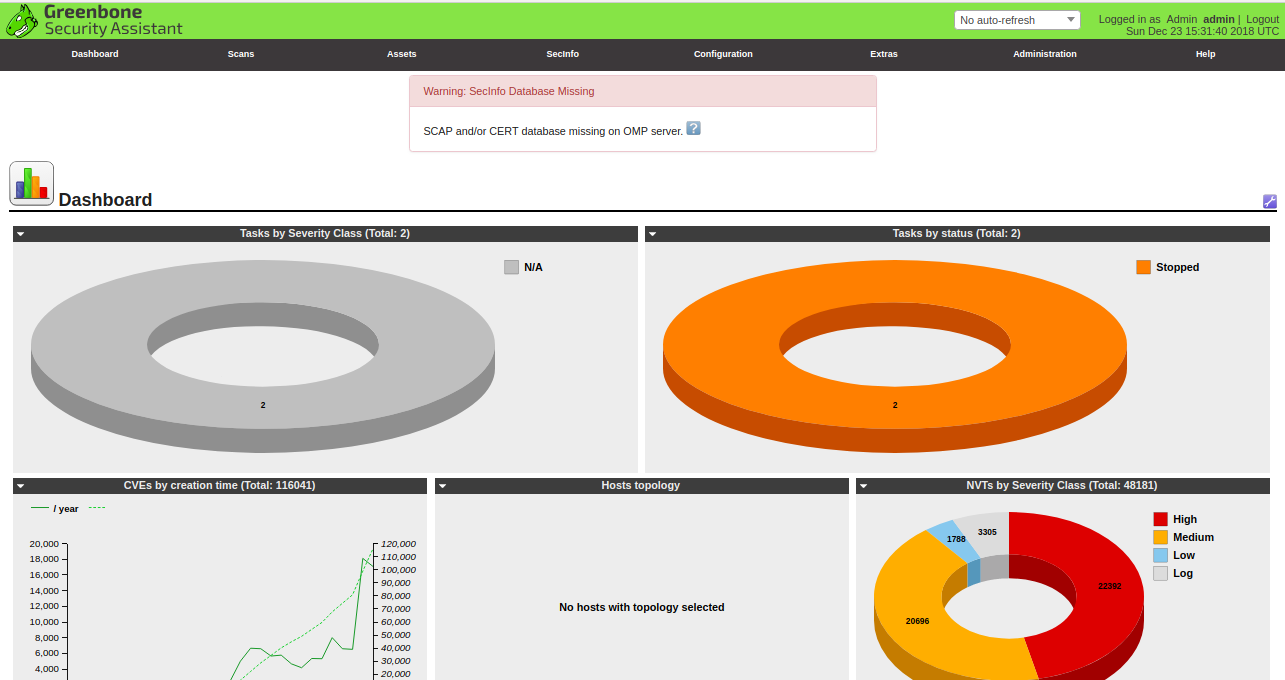
Next, you will need to create and configure a target for scan.
To do so, go to the Configuration menu and click on the Targets. You should see the following page:
Next, click on the blue icon in the left pane and click on the new target button. You should see the following page:
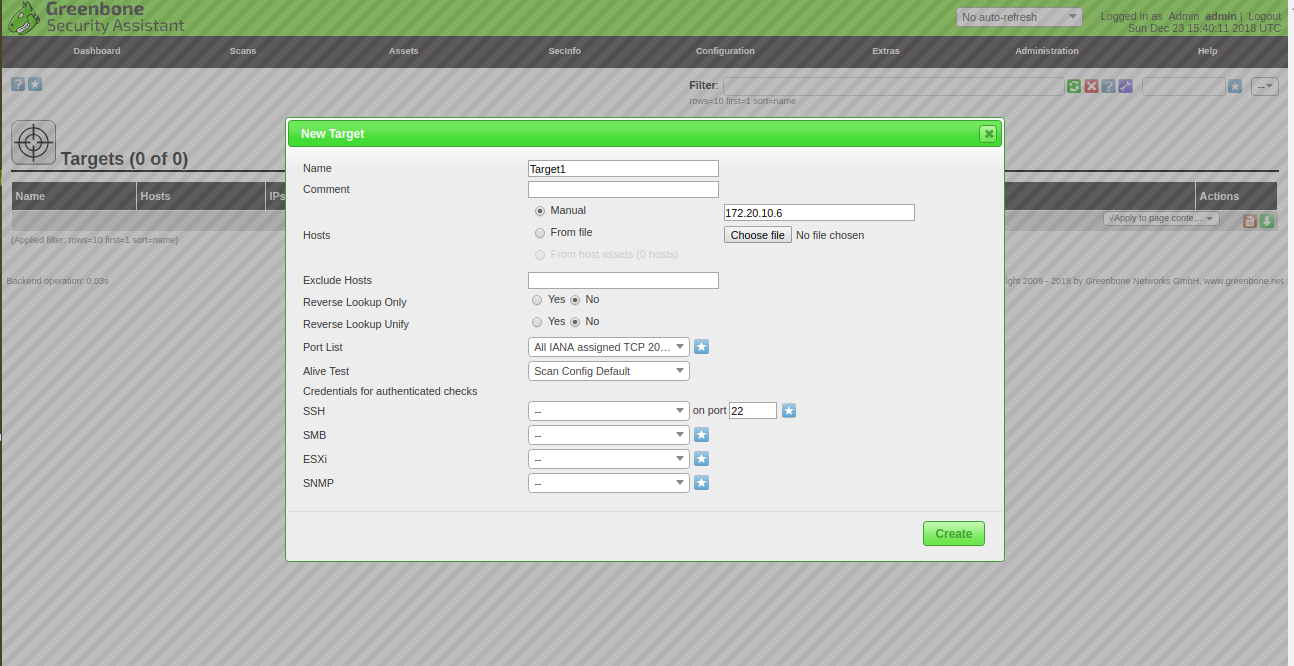
Here, provide your target name, IP address of OpenVas host and other details, then click on the Create button. You should see the newly created target in the following page:
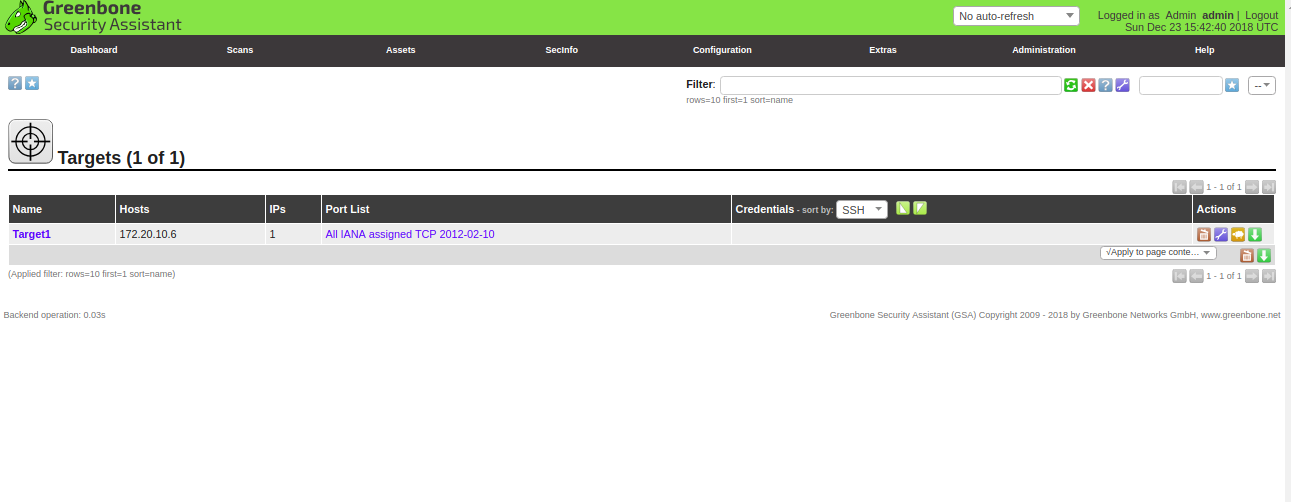
Next, you will need to create a new scanning task to scan the target1 for vulnerabilities.
To create a new scan task, go to Scans menu and click on the Tasks. You should see the following page:
Next, click on the blue icon on the left pane and click on the new scan button. You should see the following page:
Here, provide your task name, scan targets, tick the schedule once checkbox and click on the Create button. You should see the newly created task in the following page:
Now, you are ready to scan the newly created task. Click on the green start button to start the scan as shown below:
The scan task is now executed against the target. The full scan may take some time to complete.
Once the scan task is finished, you should see the status changes to Done as shown below:
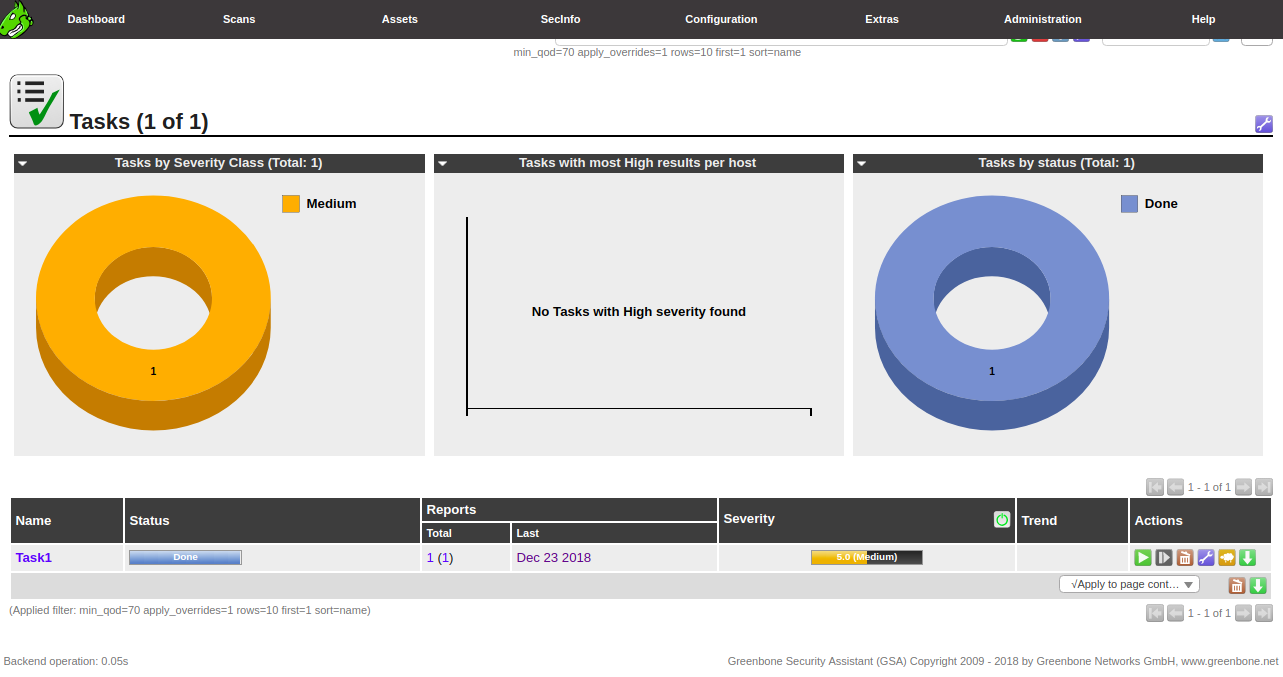
Now, go to the Scans menu and click on the Reports. You should see the report for the completed scanning task in the following page:
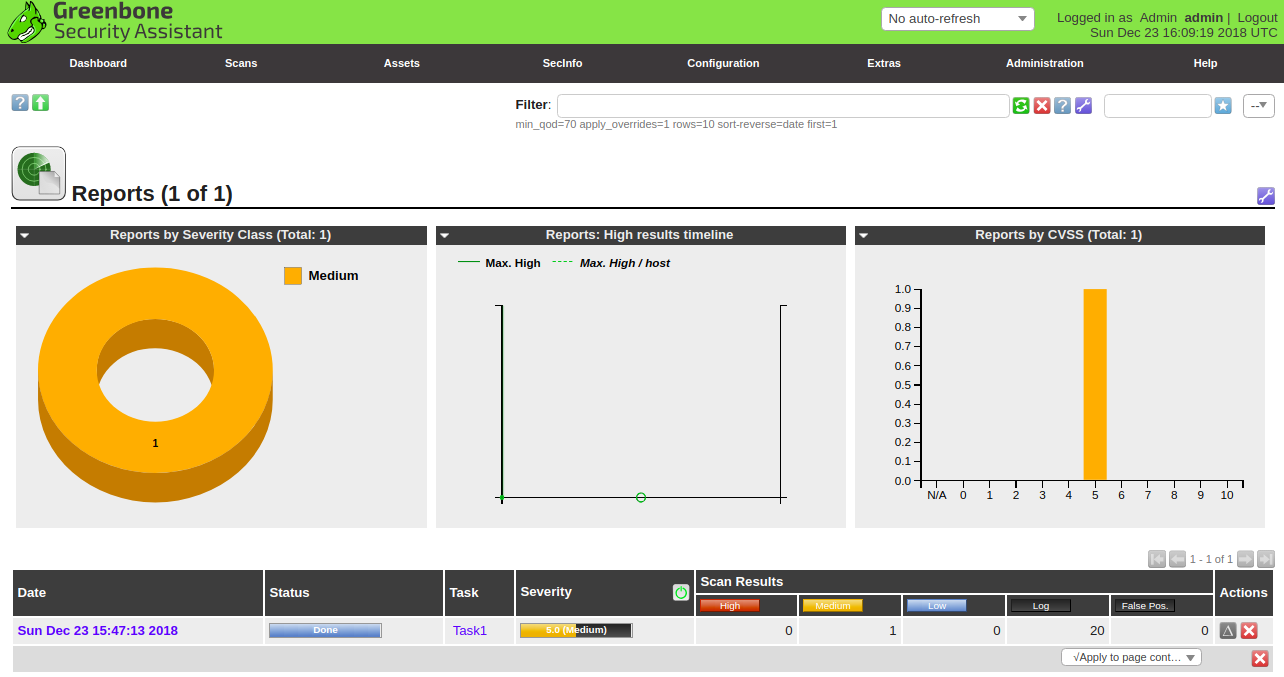
Now, click on the report name. You should see the overview of all discovered vulnerabilities on the target1 host.
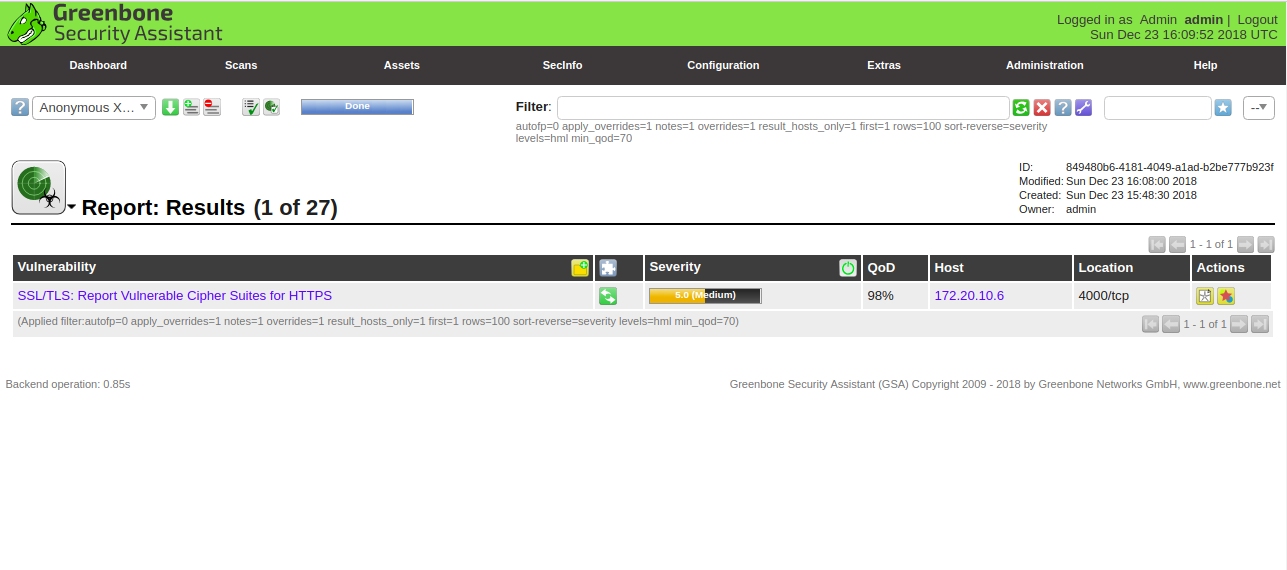
Now, click on the vulnerability name. You should see the detailed overview of the vulnerability as shown in the following page:
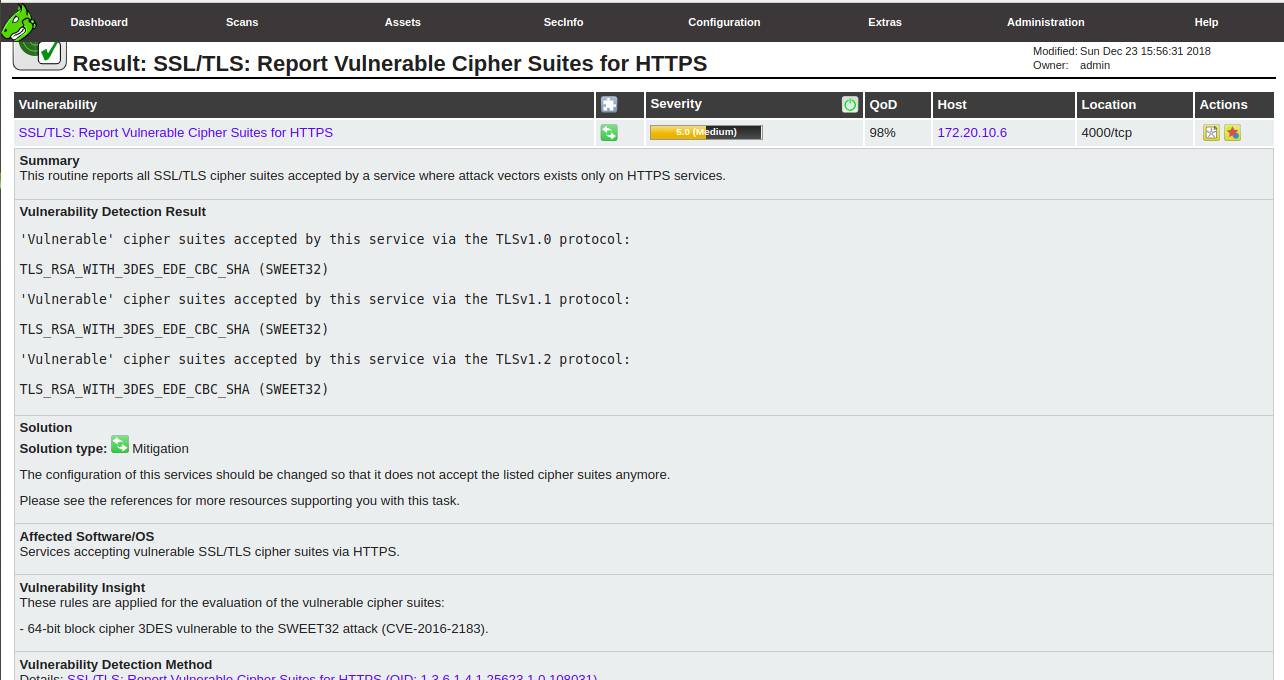
Your local vulnerability scan is now successfully completed. Next, we will scan the remote system (172.20.10.3) by supplying credentials in the target configuration. So, OpenVas can also check for local vulnerabilities such as security issues in kernels and installed software.
To create a credential target, go to the Configuration menu and click on the Targets, click on the blue icon in the left pane and click on the new target button. You should see the following page:
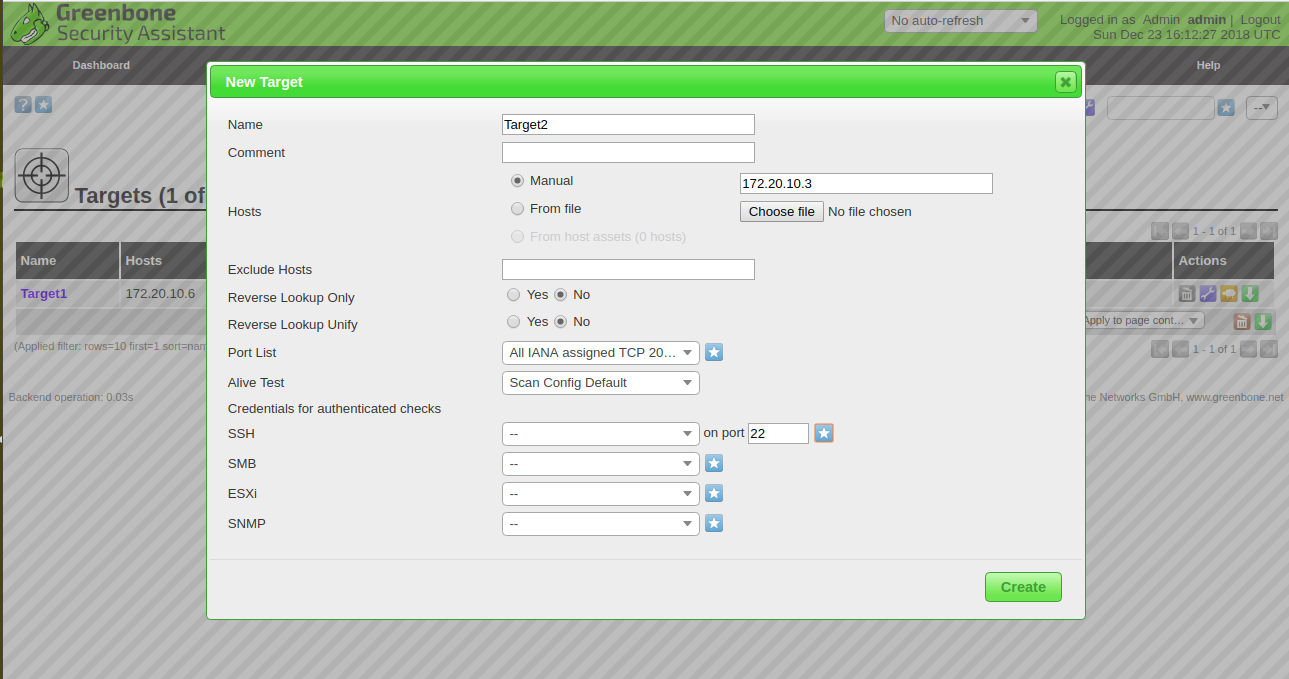
Here, provide your target name, IP address of the remote host, other details and click on the star icon beside SSH box. You should see the following page:
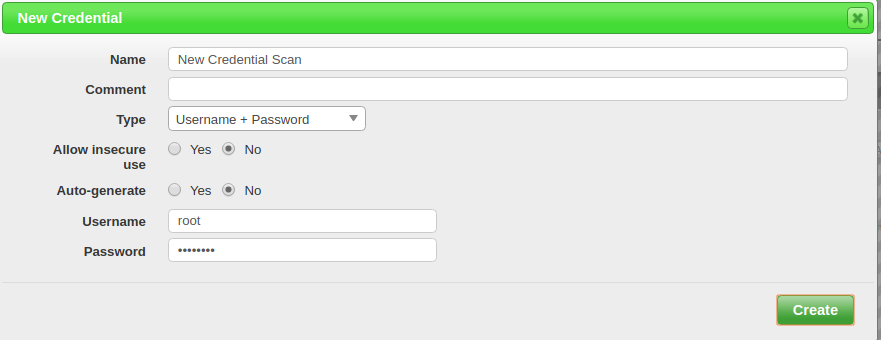
Here, provide credential name, username and password of the remote host. Then, click on the Create button. You should see the newly created target in the following page:
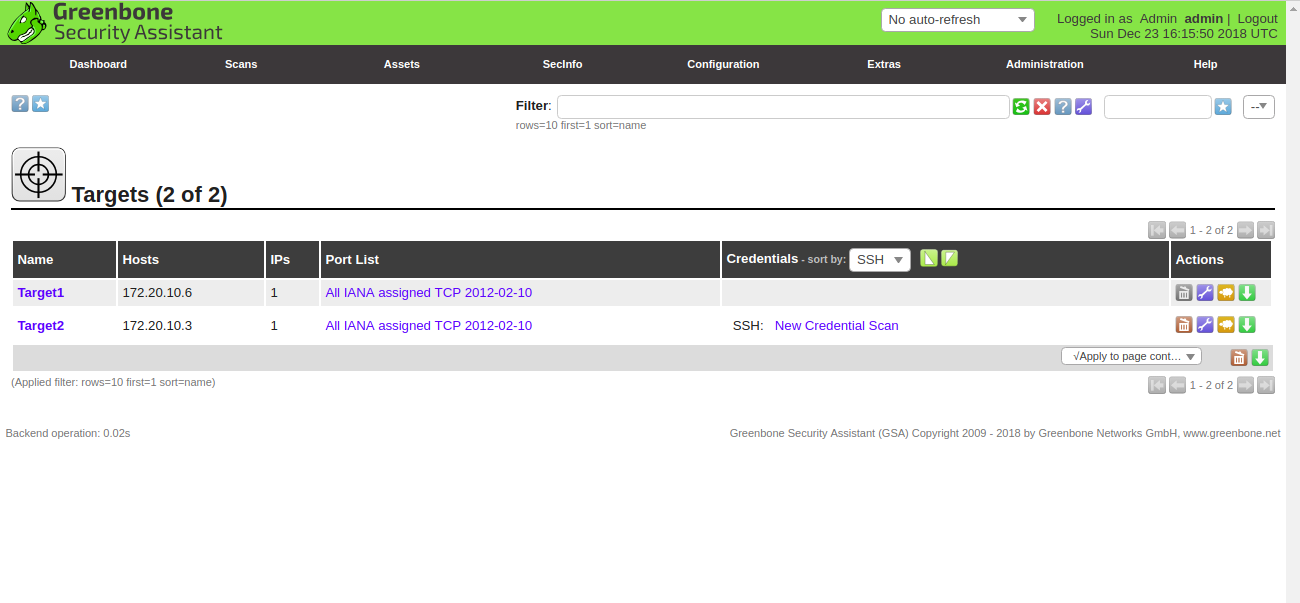
Next, you will need to create a new scanning task to scan the target2 for vulnerabilities.
To create a new scan task, go to Scans menu and click on the Tasks, click on the blue icon on the left pane and click on the new scan button. You should see the following page:
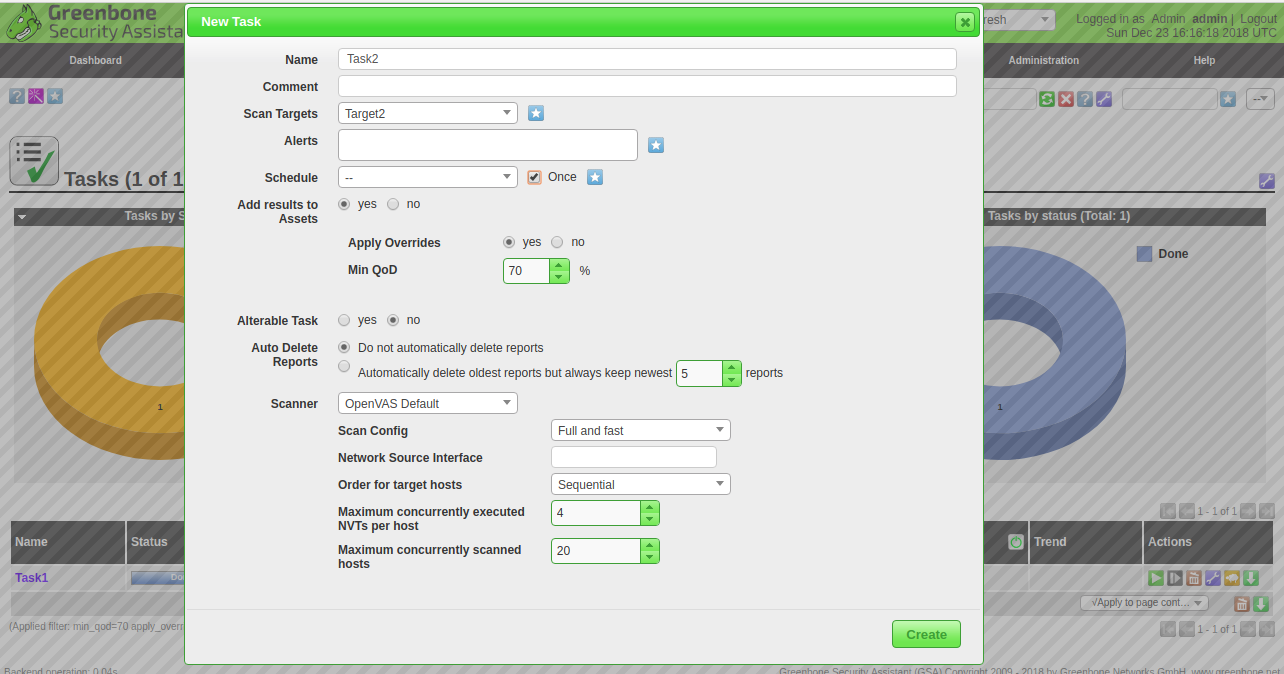
Here, provide your task name, scan targets, tick the schedule once checkbox and click on the Create button. You should see the newly created task in the following page:
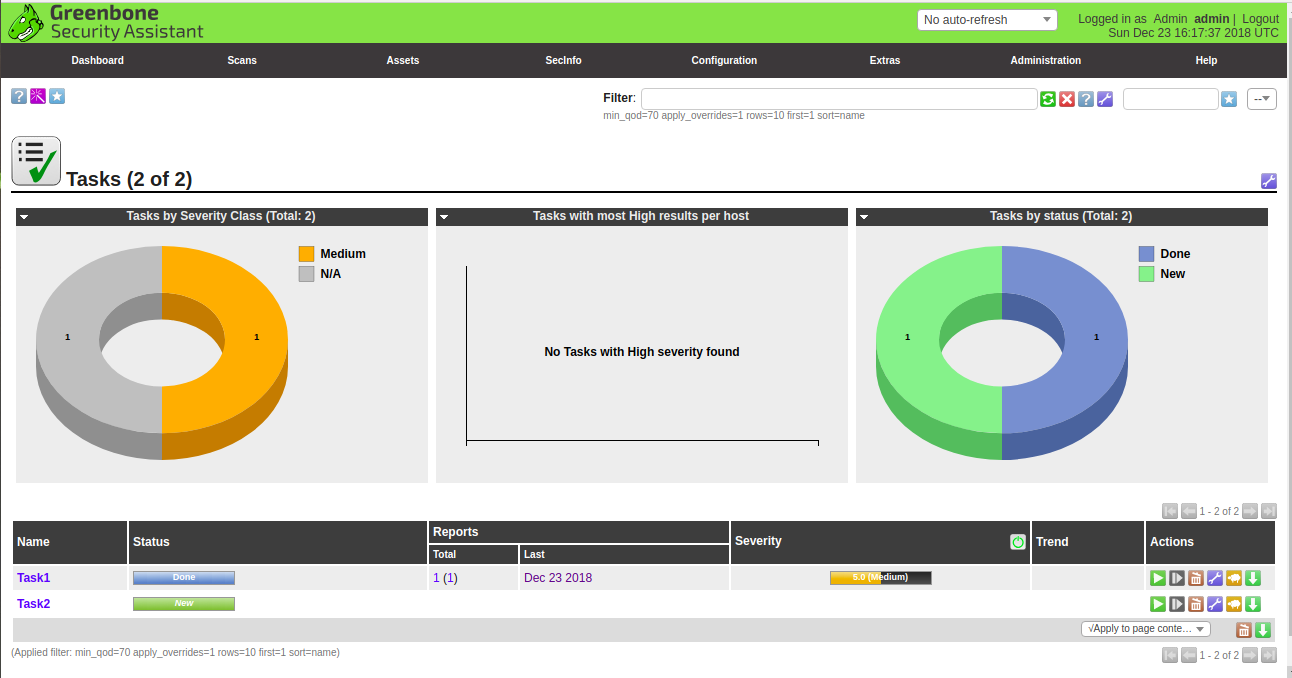
Now, click on the green star button to start the scan. Once the scan task is finished, you should see the status changes to Done as shown below:
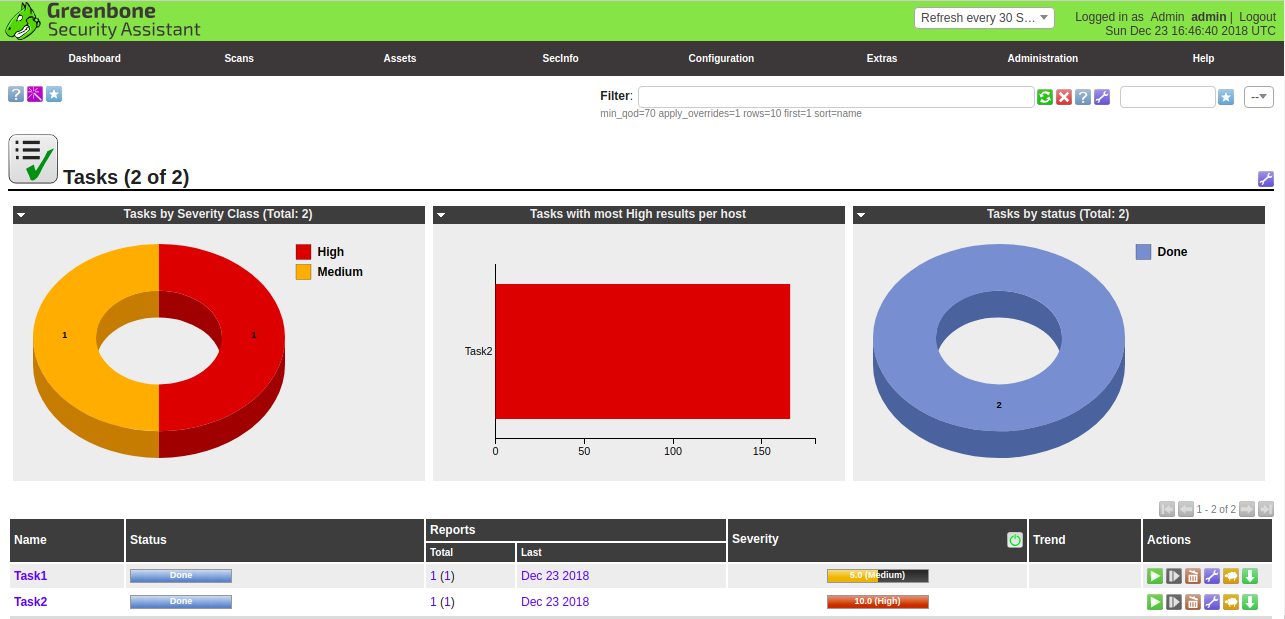
Now, go to the Scan menu and click on the Reports button. You should see the newly created scan report in the following page:
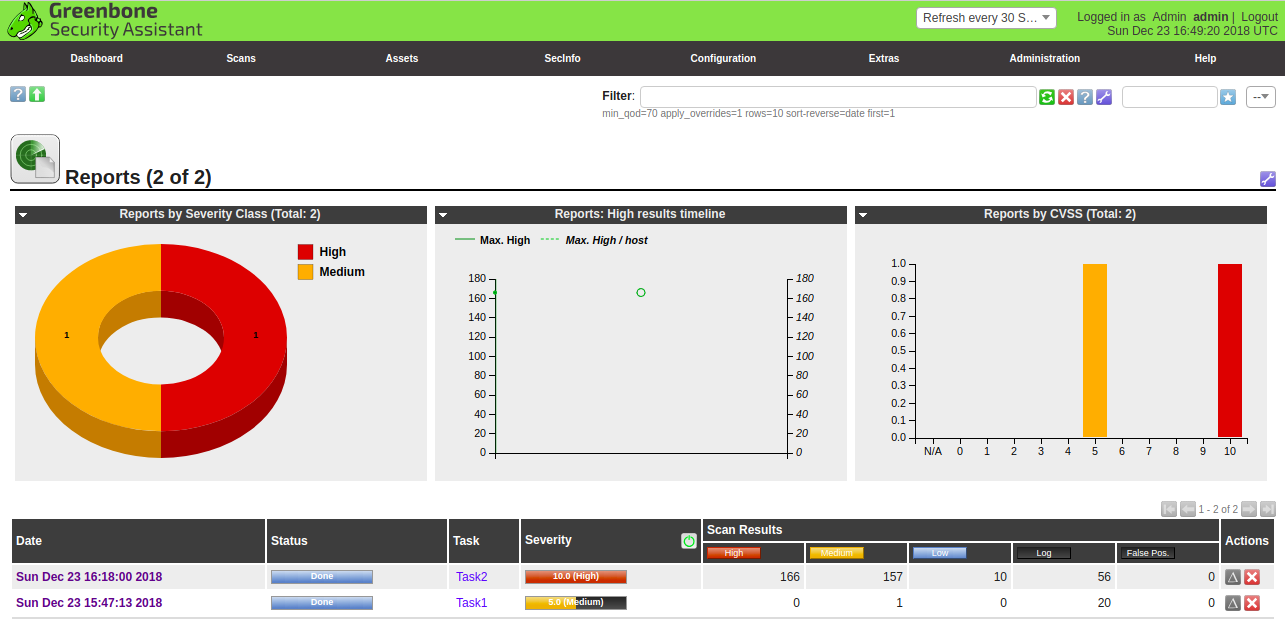
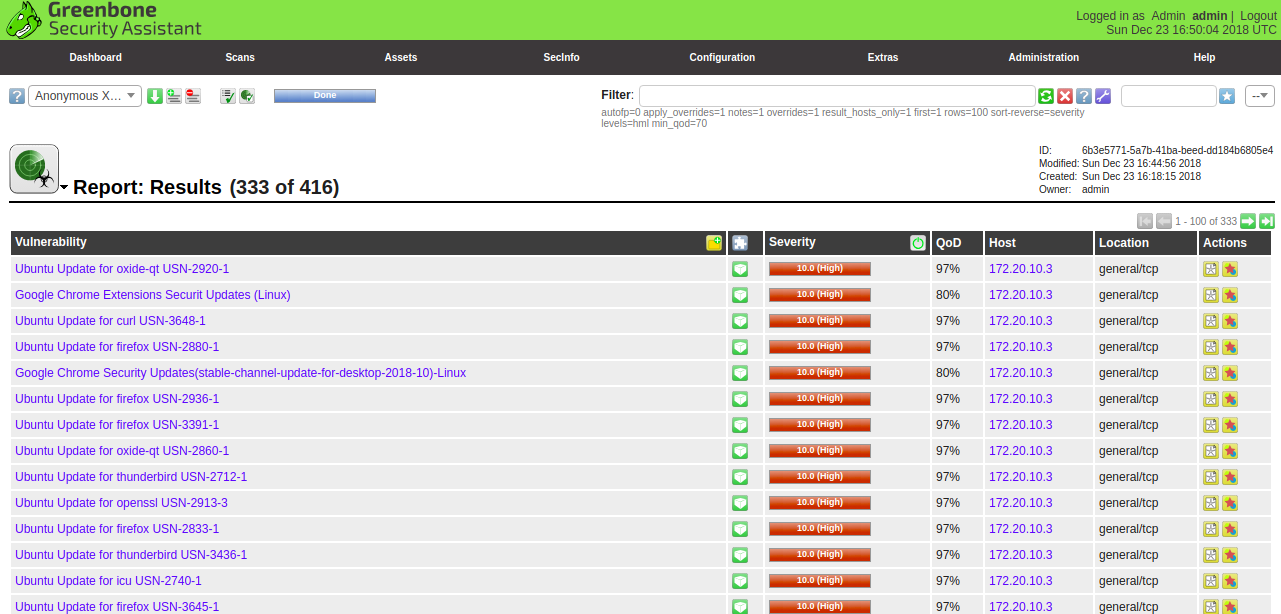
Next, click on the report name. You should see the overview of all discovered vulnerabilities on the target2 host:

2,605 posts | 747 followers
FollowAlibaba Clouder - November 27, 2018
Alibaba Clouder - July 5, 2019
Alibaba Clouder - November 21, 2019
Alibaba Clouder - July 5, 2019
Alibaba Clouder - January 9, 2020
Alibaba Clouder - November 22, 2018

2,605 posts | 747 followers
Follow ECS(Elastic Compute Service)
ECS(Elastic Compute Service)
Elastic and secure virtual cloud servers to cater all your cloud hosting needs.
Learn MoreLearn More
 OSS(Object Storage Service)
OSS(Object Storage Service)
An encrypted and secure cloud storage service which stores, processes and accesses massive amounts of data from anywhere in the world
Learn MoreMore Posts by Alibaba Clouder