
Abstract: How does a data leak occur? What should we do in case of data leaks? How should we prevent data leaks? 81.9% of network attackers are able to successfully intrude into another computer within one minute. A vast majority of attackers are able to infiltrate into an enterprise's Internet within one day. However, less than one fourth of enterprises are able to detect "imminent disaster" within one day after the data leak.
How do data leaks occur? What can we do to prevent them? According to the 2016 Verizon Data Breach Investigations Report, 81.9% of network attackers can successfully intrude another computer within one minute. Additionally, a vast majority of attackers are able to infiltrate into an enterprise's network within one day. However, less than one fourth of enterprises are able to detect an "imminent disaster" within one day after a data leak.
A network attack is similar to a viral infection in humans –it will inevitably spread once contracted, resulting in more data leaks. However, that does not mean that attackers are the sole culprit of data leaks. Failure to take preventive measures is one of the leading causes of data leakage for many enterprises. In this article, we will examine how exposed your enterprise is to data leaks with the following six questions.
1. Are you familiar with your own data?
When speaking of data leaks, we must first address the data itself. Many enterprises do not clearly classify their own data and do not know which data has been disclosed. They might not even know where sensitive data is located (such as server, terminal, network disk).
Recommendation: Before deploying security and protection mechanisms, enterprises should first sort out their data storage locations, the security of the storage locations, and the level of data sensitivity. For example, they should define which data is the most sensitive and most prone to attacks (such as user account, password, and credit card information), and which data is less risky. Enterprises that clearly understand their own data can save a lot of trouble when implementing permission management, protection deployment, and vulnerability fixes.
Meanwhile, employees can regularly maintain the locations where data is stored, such as upgrading servers and terminal systems.
2. Is your data encrypted?
Data is a likely target of tampering, hijacking, and phishing during the process of data generation, communication, transmission, and storage. If data is not encrypted, attackers can easily steal it since it is in plaintext. Many enterprises do not do enough to protect their data. Half of the enterprises in the world have not upgraded their websites from HTTP to HTTPS, leaving their data exposed on the Internet.
HTTPS offers more security and is the preferred choice for large enterprises around the world. Apple has announced that all apps submitted to the App Store must enable the App Transport Security (ATS) security standard starting January 1, 2017, and all connections must use HTTPS encryption. Android has also made a similar HTTPS requirement for connections.
Recommendation: Enterprises need to protect critical, sensitive data throughout its life cycle. Data generation, communication, storage, and destruction must be performed within a controlled and encrypted environment. In addition, we recommend enterprises to use cloud certificate services to implement one-click HTTPS transformation.
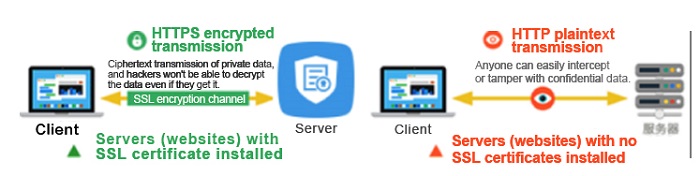
The above figure shows an encrypted communication between the client and the server. If data is hijacked in this communication scheme, the hijackers will only be able to see encrypted text, which looks gibberish.
3. Are you familiar with the biggest threats and high-risk channels in your industry?
As mentioned in The Art of War by Sun Tzu, "know thy self, know thy enemy, and you need not fear the outcome of a hundred battles." Similarly, enterprises need to know the main types of attacks in their own industries. For example, data leaks caused by DDoS attacks in the live video and gaming industries are frequent.
Regardless of the industry, web attacks remain the biggest threat to cybersecurity. Alibaba Cloud security team found that more than 85% of enterprise data leaks are caused by web attacks, including SQL injection, phishing, social engineering attacks, and credential stuffing.
Recommendation: You are not advised to "follow suit" when deploying security products. Instead, enterprises should customize security solutions for their own industries. Security experts across multiple industries typically have intimate knowledge of high-risk events and corresponding attack types in their respective industries. Thus, they are able to tailor the production, architecture, and protection procedures for a particular industry.
We recommend every enterprise deploy Web Application Firewall (WAF) to protect from web attacks. According to Alibaba Cloud security team's estimates, if an enterprise successfully performs risk scanning and system upgrades, and then deploys WAF, more than 90% of web intrusion incidents can be effectively prevented.
4. Can you fix vulnerabilities in a timely manner?
Alibaba Cloud security studies show that about 20% of enterprises put off fixing high-risk vulnerabilities for a month or longer, leaving their systems exposed.
Recommendation: Enterprises should regularly scan for vulnerabilities and upgrade their systems accordingly. In addition, due to the limited amount of resources, vulnerability fixes should be focused. Enterprises should prioritize vulnerabilities that are most easily targeted by attackers.
For example, in June 2013, it was revealed that Struts version 2.3.15 had a major security vulnerability. Struts2 is a web framework under the Apache project and is widely used in major enterprises and portals. Enterprises needed to fix the vulnerability within a few hours and work out temporary remedial measures. Otherwise, attackers could remotely execute scripts on the target machine to steal data.
This example teaches us that eliminating vulnerabilities not only requires fixes but also relies heavily on prevention. We recommend enterprises to carry out regular security tests or use public test programs to diagnose loopholes and eliminate vulnerabilities more effectively.
5. Are permissions assigned to trusted individuals?
Permission management and access control are essential for protecting sensitive data and preventing industrial espionage because employees can secretly disclose confidential data for personal gain.
Recommendation: In such cases, you should assign permissions and isolate partitions based on the employee's role. You must also determine who is allowed access to specific data. We recommend the two-factor authentication mechanism (MFA) for accounts and passwords, password security policies, and auditing functions for tenant accounts on the cloud. Enterprises can easily enable and disable such features on their own cloud interfaces to ensure the security of cloud service accounts.
In terms of access control, enterprises can limit the IP addresses that are allowed to access via SSH and RDP, as well as limit the IP addresses that are allowed to access the database, thereby reducing the scope of access as much as possible. By doing this, we can ensure only trusted employees are allowed access, and network activity can be analyzed and audited in real time.
6. Are your employees well trained in security awareness?
Many large-scale security incidents originate from small errors. It is common for employees to share screenshots and click on suspicious links in e-mails without doing exercising caution. so you must pay special attention to code security. Many data leaks are caused by the lack of basic security competency and awareness on the part of employees.
A particularly common mistake is setting weak passwords. Verizon's report shows that 63% of data leaks were due to the use of weak passwords, default passwords, and passwords that have already been cracked. Looking at the figure below, we can see that the top 500 passwords in the world are relatively easy to crack.
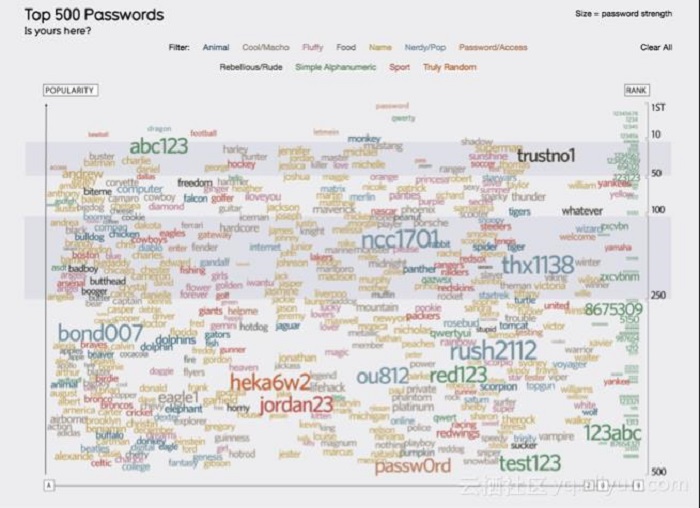
(Source: Information is Beautiful)
Recommendation: Security awareness training for employees should start from the basics. Data classification and job classification are the foundation, while situational data security reminders should be present everywhere. In addition, it is best for all employees to have basic knowledge of network security, such as the concepts of vulnerability disclosure and DDoS attacks.
Now that you've finished reading, it's time to evaluate yourself!
If you answered all YES – Congratulations! You have a fully secure network.
Your enterprise is secure from virtually every network threat.
If you answered one to two NO's – You have a stable network.
Although imperfect, you have surpassed the average enterprise security score. We recommend you to invest more effort in security management, procedures, and employee security awareness to make up for the shortcomings.
If you answered three to four NO's – You have potential network risks.
Do not panic. Most enterprises can only meet two to three of the requirements mentioned above, so your score is average. Ambiguous data classification, undefined permissions, and delayed vulnerability fixes are a "ticking time bomb" for enterprise security. We recommend that you deploy fundamental protection products and sort out the security flaws based on your business requirements.
If you answered five to six NO's – You have a vulnerable network!
Your enterprise is exposed and the security is still in the early stages. Your enterprise has not taken the necessary measures for security, perhaps because of budget constraints, limited labor, or undefined security needs. However, this puts your enterprise at high-risk to network attacks. We strongly urge you to weigh the consequences of data leaks. A safe, stable system can not only protect your data and property but also help enterprises to build trust among users, allowing the business to go further.
Of course, not all enterprises have the resources to implement all of our suggestions on security. Enterprises can selectively launch security measures based on the available funds, labor, and security policies.
For example, fast vulnerability fixes, data encryption, and regular detection and scanning are measures with immediate benefits. If you also want long-term security and stable operations for your enterprise, you will need to invest in improving employee security awareness, data visibility management, and code review procedures.
Alibaba Cloud WAF is an independently developed security product developed based on over 10 years of attack defense experience. Alibaba Cloud WAF is also the industry's first cloud WAF that provides business risk control solutions, full-version support of custom certificate HTTPS service, and dual-engine web app attack protection services. Many customers from the financial, e-commerce, and gaming industries are already using the business data risk control and protection feature of WAF. Alibaba Cloud WAF protects enterprises from message tampering, virtual theft, malicious web crawling, credential stuffing, malicious registration, and other business risks.
How Does Alibaba Cloud Power the Biggest Online Shopping Festival?

2,593 posts | 790 followers
FollowAlibaba Clouder - July 10, 2019
Alibaba Clouder - July 12, 2019
Ali Ali - June 27, 2025
Alibaba Clouder - July 23, 2020
Alibaba Clouder - July 18, 2019
Alibaba Cloud Community - September 2, 2025

2,593 posts | 790 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More Web App Service
Web App Service
Web App Service allows you to deploy, scale, adjust, and monitor applications in an easy, efficient, secure, and flexible manner.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn MoreMore Posts by Alibaba Clouder