您可以按需为RAM用户和RAM角色赋予不同的权限,仅具有权限的RAM用户和RAM角色才可以在ASM控制台上进行创建网格实例、更新服务网格功能配置等操作,避免因暴露阿里云账号密钥而造成安全风险。本文以RAM用户为例,介绍如何为RAM用户和RAM角色进行RAM授权。
前提条件
已创建RAM用户和RAM角色。具体操作,请参见创建RAM用户和创建可信实体为阿里云账号的RAM角色。
已了解授权策略语言的基本结构和语法。更多信息,请参见权限策略语法和结构。
背景信息
RAM用户和RAM角色的使用场景不同,授予的权限也不同,具体区别如下:
如果RAM用户和RAM角色只需要服务网格的操作权限,不涉及集群的操作,您只需要授予RAM用户服务网格权限。具体操作,请参见授予RAM用户和RAM角色系统策略和授予RAM用户和RAM角色自定义策略。
如果RAM用户和RAM角色需要服务网格和集群的操作权限(例如添加或删除网格内的ACK集群),您需要授予RAM用户服务网格和对应集群的权限。具体操作,请参见授予RAM用户和RAM角色系统策略、授予RAM用户和RAM角色自定义策略和授予RAM用户集群权限。
授予RAM用户和RAM角色系统策略
ASM默认已创建AliyunASMReadOnlyAccess和AliyunASMFullAccess策略,您直接授权使用即可。以下为系统策略的详细介绍:
AliyunASMReadOnlyAccess
只读管理阿里云服务网格(ASM)的权限,仅看服务网格状态等只读接口权限,无法对服务网格进行变更操作。
AliyunASMFullAccess
管理阿里云服务网格(ASM)的权限,RAM用户拥有该授权后,对于镜像资源的权限等同于阿里云账号,可以做任意操作。
以下以授予AliyunASMReadOnlyAccess权限策略为例,介绍如何授予RAM用户系统策略。关于RAM用户授权和RAM角色授权的更多信息,请参见为RAM用户授权和为RAM角色授权。
使用RAM管理员登录RAM控制台。
在左侧导航栏,选择。
在用户页面,单击目标RAM用户操作列的添加权限。
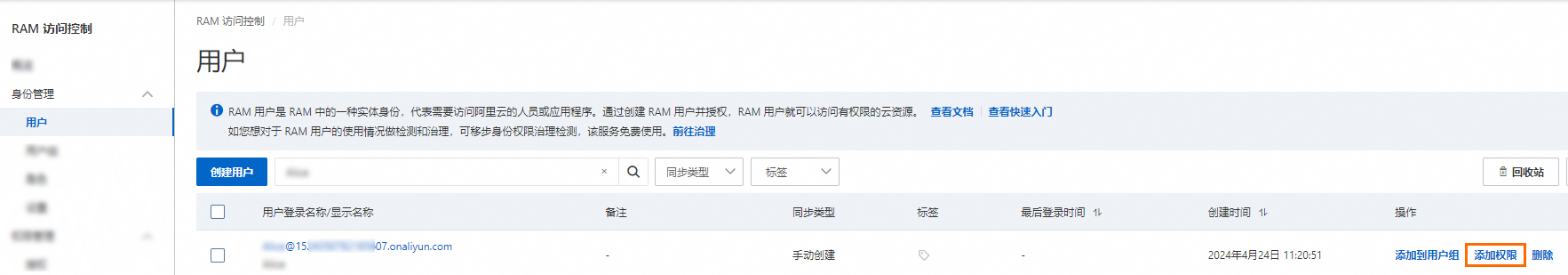
您也可以选中多个RAM用户,单击用户列表下方的添加权限,为RAM用户批量授权。
在新增授权面板,为RAM用户添加权限。
选择资源范围。
账号级别:权限在当前阿里云账号内生效。
资源组级别:权限在指定的资源组内生效。
重要指定资源组授权生效的前提是该云服务及资源类型已支持资源组,详情请参见支持资源组的云服务。资源组授权示例,请参见使用资源组限制RAM用户管理指定的ECS实例。
选择授权主体。
授权主体即需要添加权限的RAM用户。系统会自动选择当前的RAM用户。
在所有策略类型下单击系统策略,在文本框中输入AliyunASMReadOnlyAccess,然后单击AliyunASMReadOnlyAccess。
说明每次最多绑定5条策略,如需绑定更多策略,请分次操作。
单击确认新增授权。
单击关闭。
授予RAM用户和RAM角色自定义策略
如果您想对权限进行细粒度控制,您可以自定义策略,然后授予RAM用户和RAM角色自定义策略权限。
创建授予访问ASM实例的权限策略
使用RAM管理员登录RAM控制台。
在左侧导航栏,选择。
在权限策略页面,单击创建权限策略。
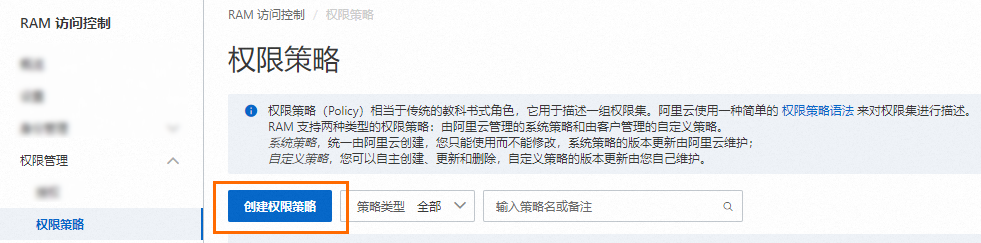
在创建权限策略页面,单击脚本编辑页签。
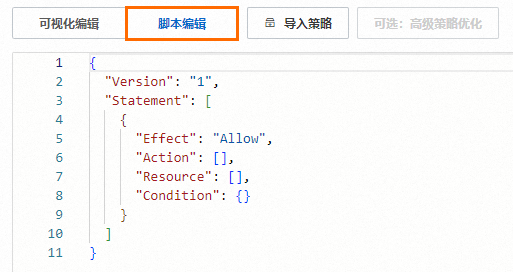
输入您的授权策略内容,然后单击继续编辑基本信息。
通过改变
Statement中的Action字段,可以实现API的细粒度鉴权。本文以授予受限访问权限策略为例,受限访问权限策略包括除RBAC授权之外的服务网格的所有RAM权限,拥有该权限的RAM用户不可以对其他用户进行RBAC授权,但拥有除此之外的其他所有权限。关于权限策略语法结构的详情,请参见权限策略语法和结构。{ "Statement": [ { "Effect": "Allow", "Action": [ "servicemesh:Add*", "servicemesh:CRBatchDeletion", "servicemesh:Create*", "servicemesh:Delete*", "servicemesh:Describe*", "servicemesh:Enable*", "servicemesh:Disable*", "servicemesh:Get*", "servicemesh:InvokeApiServer", "servicemesh:List*", "servicemesh:Modify*", "servicemesh:Re*", "servicemesh:Run*", "servicemesh:Set*", "servicemesh:Sync*", "servicemesh:Update*", "servicemesh:Upgrade*" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "log:ListLogStores", "log:ListDashboard", "log:GetDashboard", "log:ListSavedSearch", "log:ListProject" ], "Resource": "*" }, { "Effect": "Allow", "Action": "log:GetLogStoreLogs", "Resource": "acs:log:*:*:project/*/logstore/audit-*" }, { "Effect": "Allow", "Action": "log:GetLogStoreLogs", "Resource": "acs:log:*:*:project/*/logstore/istio-*" }, { "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": "servicemesh.aliyuncs.com" } } } ], "Version": "1" }在基本信息区域输入策略名称,本文设置为ASMPolicy1,然后单击确定。
授予RAM用户和RAM角色权限策略
本文以授予RAM用户权限为例,关于RAM角色权限的具体操作,请参见为RAM角色授权。
使用RAM管理员登录RAM控制台。
在左侧导航栏,选择。
在用户页面,单击目标RAM用户操作列的添加权限。

您也可以选中多个RAM用户,单击用户列表下方的添加权限,为RAM用户批量授权。
在新增授权面板,为RAM用户添加权限。
选择资源范围。
账号级别:权限在当前阿里云账号内生效。
资源组级别:权限在指定的资源组内生效。
重要指定资源组授权生效的前提是该云服务及资源类型已支持资源组,详情请参见支持资源组的云服务。资源组授权示例,请参见使用资源组限制RAM用户管理指定的ECS实例。
选择授权主体。
授权主体即需要添加权限的RAM用户。系统会自动选择当前的RAM用户。
在所有策略类型下单击自定义策略,在文本框中输入ASMPolicy1,然后单击ASMPolicy1。
说明每次最多绑定5条策略,如需绑定更多策略,请分次操作。
单击确认新增授权。
单击关闭。
自定义策略场景示例
场景一:授予单个网格实例的管理权限
您可以使用以下脚本创建拥有单个网格实例管理权限的策略,授予RAM用户或RAM角色该权限策略后,RAM用户或RAM角色只能管理指定ID的网格实例。
创建权限策略时,请将以下脚本中的<ServicemeshId>替换成实际需要授权的网格实例ID。
{
"Statement": [
{
"Effect": "Allow",
"Action": "servicemesh:*",
"Resource": "acs:servicemesh:*:*:servicemesh/<ServicemeshId>"
},
{
"Effect": "Allow",
"Action": "servicemesh:DescribeServiceMeshes",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "log:GetLogStoreLogs",
"Resource": "acs:log:*:*:project/*/logstore/audit-<ServicemeshId>"
},
{
"Effect": "Allow",
"Action": "log:GetLogStoreLogs",
"Resource": "acs:log:*:*:project/*/logstore/istio-<ServicemeshId>"
}
],
"Version": "1"
}场景二:授予使用ASM控制台管理Istio资源的读写权限
ASM默认提供的AliyunASMReadOnlyAccess系统策略可以授予RAM用户或RAM角色只读管理阿里云服务网格ASM的权限,但被授予此权限的RAM用户或RAM角色无法管理网格中的Istio资源。
您可以使用以下脚本创建拥有Istio资源读写权限的策略,授予RAM用户或RAM角色该权限策略后,RAM用户或RAM角色可以正常使用ASM控制台管理网格中的Istio资源,同时无法对网格的其它部分(例如功能设置等)进行任何变更。
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"servicemesh:List*",
"servicemesh:Describe*",
"servicemesh:Get*",
"servicemesh:InvokeApiServer"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"log:ListLogStores",
"log:ListDashboard",
"log:GetDashboard",
"log:ListSavedSearch"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "log:GetLogStoreLogs",
"Resource": "acs:log:*:*:project/*/logstore/audit-*"
}
],
"Version": "1"
}场景三:授予对其它用户或角色进行RBAC授权的权限
您可以使用以下脚本创建拥有对其它用户或角色进行RBAC授权的权限策略,授予RAM用户或RAM角色该权限策略后,RAM用户或RAM角色可以使用ASM控制台管理其它RAM角色或RAM用户的RBAC权限,同时无法操作或查看任何网格实例。
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"servicemesh:DescribeUserPermissions",
"servicemesh:GrantUserPermissions",
"servicemesh:DescribeServiceMeshes",
"servicemesh:DescribeUsersWithPermissions"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "ims:ListUserBasicInfos",
"Resource": "*"
}
],
"Version": "1"
}