本文介紹如何基於標籤控制RAM使用者權限,實現不同的使用者可以擁有不同雲資源的訪問和操作許可權。
背景資訊
標籤可用於標識雲資源,實現分類管理資源;存取控制RAM可基於權限原則,控制雲資源的訪問和操作許可權。結合標籤和RAM,將標籤作為權限原則的匹配條件,可以實現雲資源精微調權限管理。
基於標籤控制RAM使用者權限(即標籤鑒權)的邏輯如下:

支援綁定標籤的ECI資源套件括ECI執行個體、鏡像緩衝和虛擬節點;僅支援在建立或者更新ECI資源時為其綁定標籤。更多資訊,請參見使用標籤管理ECI執行個體。
配置樣本
樣本情境說明
本文以下述情境作為樣本,說明如何?標籤鑒權。
假設您需要控制某一RAM使用者只能操作特定(假設綁定了env:test標籤)的ECI資源,如下圖: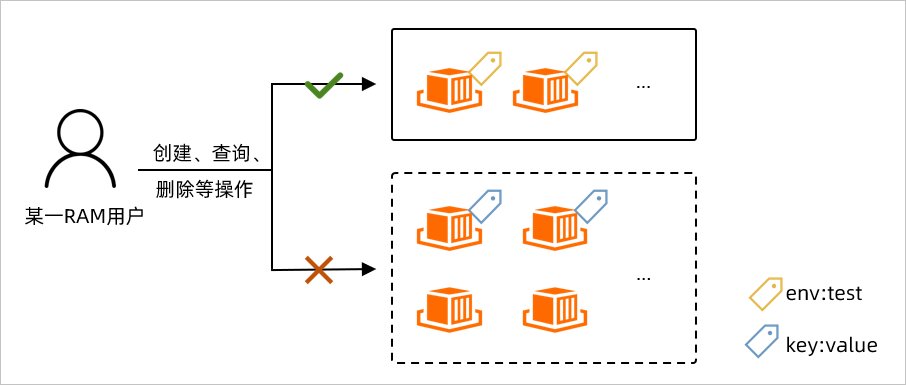
具體需求包括:
需求1:不允許建立不帶標籤的ECI資源,僅當建立時為ECI資源綁定
env:test標籤才可以建立成功。需求2:只允許操作自身建立(即綁定
env:test標籤)的ECI資源,不允許操作其他ECI資源。需求3:查詢ECI資源時,只允許查看自身建立(即綁定
env:test標籤)的ECI資源。
步驟一:配置自訂權限原則並授權
使用阿里雲帳號登入RAM控制台。
在左側導覽列選擇許可權管理>權限原則。
在權限原則頁面,單擊建立權限原則。
完成自訂策略配置。
單擊匯入策略頁簽。
在彈出的對話方塊的右側篩選項中選擇系統策略,然後搜尋並選中AliyunECIFullAccess,單擊匯入。
AliyunECIFullAccess為系統預設的管理ECI資源的許可權,包括操作ECI資源、查詢相關資源(安全性群組、VPC等資源)、建立ECI服務關聯角色等許可權。
單擊指令碼編輯頁簽。
在編輯框中修改權限原則內容,然後單擊繼續編輯基本資料。
在權限原則的
Condition中,您可以增加需要匹配標籤的條件來限制操作許可權。支援的標籤條件關鍵字如下:標籤條件關鍵字
說明
acs:RequestTag限制在請求中必須傳入特定的標籤。
如果API請求中沒有標籤參數,則不能使用
acs:RequestTag,否則會導致鑒權失敗。acs:ResourceTag限制指定的資源必須包含特定的標籤。
如果API請求中沒有資源ID參數,則不能使用
acs:ResourceTag,否則會導致鑒權失敗。說明設計權限原則時,您可以根據各操作介面特性(API請求是否需要指定資源ID、是否支援傳入標籤),結合實際業務需求,來設定
acs:RequestTag或acs:ResourceTag。更多資訊,請參見API介面鑒權說明。根據樣本情境中的需求,設計權限原則如下:
需求
權限原則
不允許建立不帶標籤的ECI資源,僅當建立時為ECI資源綁定
env:test標籤才可以建立成功{ "Effect": "Allow", "Action": "eci:Create*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }只允許操作綁定了env:test標籤的ECI資源,不允許操作其他資源
{ "Effect": "Allow", "Action": "eci:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/env": "test" } } }查詢ECI資源時,只允許查看綁定了env:test標籤的ECI資源。
{ "Effect": "Allow", "Action": "eci:Describe*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }結合AliyunECIFullAccess已有的權限原則,完整權限原則樣本如下:
{ "Version": "1", "Statement": [{ "Effect": "Allow", "Action": "eci:Create*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }, { "Effect": "Allow", "Action": "eci:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/env": "test" } } }, { "Effect": "Allow", "Action": "eci:Describe*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }, { "Action": [ "ecs:DescribeSecurityGroups" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "vpc:DescribeVSwitches", "vpc:DescribeVpcs", "vpc:DescribeEipAddresses" ], "Resource": "*", "Effect": "Allow" }, { "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": [ "eci.aliyuncs.com", "vnode.eci.aliyuncs.com" ] } } } ] }說明如果您通過OpenAPI操作ECI資源,則使用AliyunECIFullAccess的許可權即可;如果您通過ECI控制台操作ECI資源,則除了AliyunECIFullAccess的許可權外,還需添加額外許可權。更多資訊,請參見為RAM使用者授權。
輸入權限原則名稱,單擊確定。
將自訂權限原則授予RAM使用者。
步驟二:驗證權限原則是否生效
使用RAM使用者登入OpenAPI平台。
測試權限原則是否生效。
以ECI執行個體為例進行測試:
建立ECI執行個體
設定了
env:test標籤,則可以建立。沒有設定標籤或者設定了其他標籤,則無法建立,提示沒有許可權。
刪除ECI執行個體
刪除的執行個體綁定了
env:test標籤,則可以刪除。刪除的執行個體沒有綁定
env:test標籤,則無法刪除,提示沒有許可權。
查詢ECI執行個體
指定執行個體(該執行個體綁定了
env:test標籤)但沒有設定標籤,則查詢出指定執行個體的資訊。指定執行個體(該執行個體沒有綁定
env:test標籤),則查詢結果為空白。沒有指定執行個體,僅設定
env:test標籤,則查詢出帶有env:test標籤的所有執行個體資訊。沒有指定執行個體也沒有設定標籤,則查詢結果為空白。
API介面鑒權說明
為某一RAM使用者授予含有標籤鑒權的權限原則後,該RAM使用者調用各API介面時的鑒權情況如下表所示:
介面 | 鑒權說明 |
CreateContainerGroup、CreateImageCache等建立介面 | 該類介面無需指定資源ID,則匹配
|
DescribeContainerGroups、DescribeImageCaches等查詢介面 | 該類介面按需指定資源ID或傳入標籤,則匹配
說明 查詢介面在鑒權不通過時,返回結果為空白,並不會報錯。 |
UpdateContainerGroup、UpdateImageCache等更新介面 | 該類介面必須指定資源ID,則匹配
說明 更新標籤時,RAM使用者需要分別具有更新前後的標籤許可權。即授權時,需要授予使用者兩個自訂權限原則,分別包含更新前後的標籤條件限制。 |
RestartContainerGroup、ExecContainerCommand等其他動作介面 | 該類介面必須指定資源ID,則匹配
|