セキュリティトークンサービス (STS) を使用すると、一時的な認証情報を使用して Object Storage Service (OSS) に保存されているデータへの時間制限付きアクセスを許可できます。一時的な認証情報の有効期限が切れると、その認証情報を使用してデータにアクセスすることはできなくなります。これにより、柔軟で時間制限のあるアクセス制御が可能になります。
利用シーン
ある E コマース企業が、大量の商品データを OSS に保存しています。この企業のサプライヤーは、自社の業務システムから企業の OSS バケットに定期的にデータをアップロードする必要があります。
この企業には、以下の情報セキュリティおよびコンプライアンス要件があります:
データセキュリティ:コアビジネスデータへの不正アクセスを防ぐため、企業は自社の OSS の AccessKey ペアをサプライヤーに公開したくありません。
権限制御:企業は、きめ細かな権限制御を必要としています。具体的には、サプライヤーにデータアップロードの権限を付与し、要件の変更に応じてこれらの権限を動的に調整できるようにしたいと考えています。
権限管理:企業は、長期的な認証情報を管理することなく、サプライヤーや将来のパートナーのためにアクセス認証情報を柔軟に生成したいと考えています。
時間制限付きアクセス:企業は、サプライヤーに時間制限付きアクセスを許可したいと考えています。指定された期間が経過すると、サプライヤーはデータへのアクセスを拒否されます。
仕組み
企業は、サプライヤーが OSS バケットに一時的にファイルをアップロードすることを許可します。

企業はまず、Resource Access Management (RAM) ユーザーと RAM ロールを作成し、必要な権限を付与します。サプライヤーは企業に一時的な認証情報をリクエストし、企業は AssumeRole 操作を呼び出して一時的な認証情報を生成し、サプライヤーに返します。サプライヤーは、その一時的な認証情報を使用して、企業が所有する OSS バケットにデータをアップロードします。
前提条件
企業は既存の OSS バケットを所有している必要があります。詳細については、「バケットの作成」をご参照ください。
ステップ 1:企業による一時的な認証情報の生成
1. RAM ユーザーの作成
Alibaba Cloud アカウントのオーナーまたは管理権限を持つ RAM ユーザーが RAM ユーザーを作成できます。
RAM コンソールにログインします。
左側のナビゲーションウィンドウで、アイデンティティ > [ユーザー] を選択します。
[ユーザー] ページで、ユーザーの作成 をクリックします。
ログイン名 と [表示名] を指定します。
アクセスモード セクションで、[永続的な AccessKey を使用したアクセス] を選択し、[OK] をクリックします。
画面の指示に従って、セキュリティ検証を完了します。
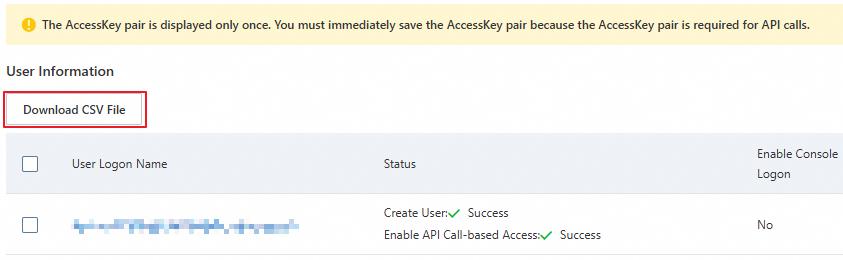
AccessKey ペア (AccessKey ID と AccessKey Secret) をコピーし、安全に保管されたローカルファイルに貼り付けます。
重要RAM ユーザーの AccessKey Secret は、RAM ユーザーの作成時にのみ取得できます。AccessKey ペアを含む CSV ファイルをデバイスの安全な場所にダウンロードしてください。
2. AssumeRole 操作を呼び出すための RAM ユーザーへの権限付与
次に、企業は Alibaba Cloud アカウントまたは RAM の管理権限を持つ RAM ユーザーを使用して、作成した RAM ユーザーに AssumeRole 操作を呼び出す権限を付与します。
RAM コンソールにログインします。
左側のナビゲーションウィンドウで、アイデンティティ > [ユーザー] を選択します。先ほど作成した RAM ユーザーを見つけ、[操作] 列の 権限の追加 をクリックします。
[権限の付与] パネルの [ポリシー] セクションで、AliyunSTSAssumeRoleAccess ポリシーを選択します。
説明AliyunSTSAssumeRoleAccess ポリシーは、RAM ユーザーが AssumeRole 操作を呼び出すことを許可します。このポリシーは、RAM ユーザーが STS から一時的な認証情報を取得し、OSS へのリクエストを開始するために必要な権限を付与するものではありません。

[権限を付与] をクリックします。
3. RAM ロールの作成
企業は、Alibaba Cloud アカウントまたは RAM の管理権限を持つ RAM ユーザーを使用して、以下の手順で RAM ロールを作成します:
RAM コンソールにログインします。
左側のナビゲーションウィンドウで、アイデンティティ > [ロール] を選択します。
[ロール] ページで、[ロールの作成] をクリックします。
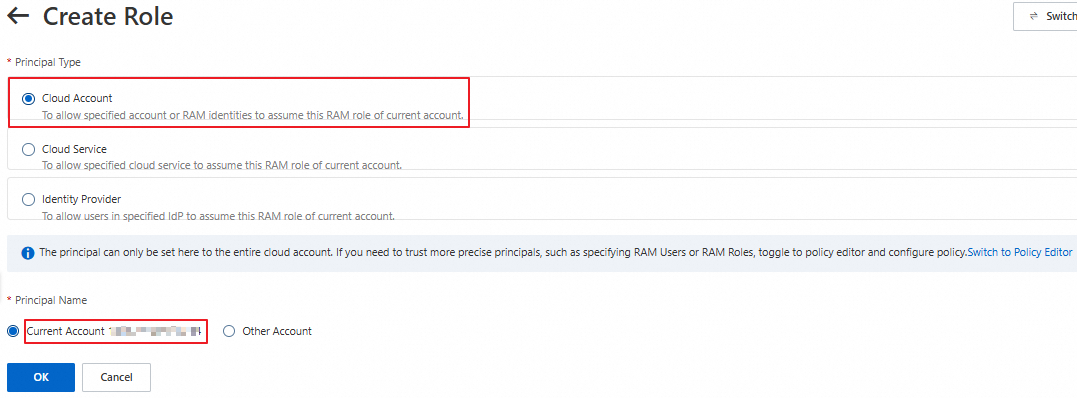
[ロールの作成] ページで、[プリンシパルタイプ] に [クラウドアカウント] を選択し、[プリンシパル名] に [現在のアカウント] を選択して、[OK] をクリックします。
[ロールの作成] ダイアログボックスで、ロール名を指定し、[OK] をクリックします。
表示されるロール詳細ページで、[基本情報] セクションの ARN フィールドの横にある [コピー] をクリックします。

4. OSS にオブジェクトをアップロードする権限の RAM ロールへの付与
RAM ロールに OSS へのアクセスを許可するには、企業は Alibaba Cloud アカウントを使用するか、RAM の管理権限を持つ RAM ユーザーとして、1 つ以上のポリシーを RAM ロールにアタッチする必要があります。たとえば、RAM ロールには、指定されたバケットにデータをアップロードするための OSS 書き込み権限が必要です。
オブジェクトをアップロードする権限をロールに付与するカスタムポリシーを作成します。
RAM コンソールにログインします。
左側のナビゲーションウィンドウで、権限管理 > ポリシー を選択します。
ポリシー ページで、ポリシーの作成 をクリックします。
ポリシーの作成 ページで、[JSON] をクリックします。コードエディタで、指定されたバケットにデータをアップロードする権限を入力します。以下のスクリプトはポリシーの例です:
警告以下の例は参考用です。過剰な権限を付与しないように、要件に基づいてきめ細かな RAM ポリシーを設定する必要があります。きめ細かな RAM ポリシーの設定方法の詳細については、「例 9:RAM または STS を使用した OSS リソースへのユーザーアクセスの権限付与」をご参照ください。
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "oss:PutObject" ], "Resource": [ "acs:oss:*:*:examplebucket/*" ] } ] }説明Action 要素は、RAM ロールに付与する権限を指定します。たとえば、oss:PutObject を指定すると、RAM ロールを偽装した RAM ユーザーは、シンプルアップロード、フォームアップロード、追加アップロード、マルチパートアップロード、再開可能なアップロードなど、さまざまなアップロード方法を使用して、指定されたバケットにオブジェクトをアップロードできます。詳細については、「OSS の RAM ポリシーにおける Action 要素」をご参照ください。
[OK] をクリックします。[ポリシーの作成] ダイアログボックスで、[ポリシー名] フィールドにポリシー名 (この例では RamTestPolicy) を指定し、[OK] をクリックします。
カスタムポリシーを RamOssTest ロールにアタッチして権限を付与します。
RAM コンソールにログインします。
左側のナビゲーションウィンドウで、[ID] > [ロール] を選択します。
[ロール] ページで、RamOssTest ロールを見つけます。
[操作] 列の [権限の付与] をクリックします。
[権限の付与] ページの [ポリシー] セクションで、タイプドロップダウンリストから [カスタムポリシー] を選択し、カスタムポリシー RamTestPolicy を選択します。
[権限を付与] をクリックします。
5. RAM ユーザーを使用した RAM ロールの偽装と一時的な認証情報の生成
Alibaba Cloud アカウントの AccessKey ペアを使用して STS API を呼び出すと失敗します。RAM ユーザーの AccessKey ペアを使用する必要があります。以下のサンプルコードでは、RAM ユーザーの AccessKey ペアを使用して一時的な認証情報をリクエストします。
先ほど作成した RAM ユーザーが RAM ロールを偽装して、一時的な認証情報を取得します。一時的な認証情報には、STS トークン (SecurityToken)、一時的な AccessKey ペア (AccessKey ID と AccessKey Secret)、および有効期間 (Expiration) が含まれます。以下のサンプルコードは、シンプルアップロードに必要な
oss:PutObject権限を提供する一時的な認証情報を生成します。他のプログラミング言語の STS SDK を使用して一時的な認証情報を生成する方法の詳細については、「STS SDK の概要」をご参照ください。サンプルコードのエンドポイントは、STS エンドポイントを指定します。アプリケーションサーバーと同じリージョンまたはその近くにある STS エンドポイントを使用すると、STS の応答速度が向上します。STS エンドポイントの詳細については、「エンドポイント」をご参照ください。
Java
import com.aliyuncs.DefaultAcsClient;
import com.aliyuncs.exceptions.ClientException;
import com.aliyuncs.http.MethodType;
import com.aliyuncs.profile.DefaultProfile;
import com.aliyuncs.profile.IClientProfile;
import com.aliyuncs.auth.sts.AssumeRoleRequest;
import com.aliyuncs.auth.sts.AssumeRoleResponse;
public class StsServiceSample {
public static void main(String[] args) {
// STS エンドポイントを指定します。例:sts.cn-hangzhou.aliyuncs.com。STS には、インターネットまたは VPC 経由でアクセスできます。
String endpoint = "sts.cn-hangzhou.aliyuncs.com";
// ステップ 1.1 で生成された RAM ユーザーの AccessKey ID と AccessKey Secret を環境変数から取得します。
String accessKeyId = System.getenv("ACCESS_KEY_ID");
String accessKeySecret = System.getenv("ACCESS_KEY_SECRET");
// ステップ 1.3 で生成された RAM ロールの ARN を環境変数から取得します。
String roleArn = System.getenv("RAM_ROLE_ARN");
// 異なるトークンを区別するために、カスタムのロールセッション名を指定します。例:SessionTest。
String roleSessionName = "yourRoleSessionName";
// 一時的な認証情報が RAM ロールのすべての権限を持つことを指定します。
String policy = null;
// 一時的な認証情報の有効期間を指定します。単位:秒。最小有効期間は 900 秒です。最大有効期間は、現在のロールに指定された最大セッション期間と同じです。現在のロールの最大セッション期間は 3,600 秒から 43,200 秒の範囲です。現在のロールのデフォルトの最大セッション期間は 3,600 秒です。
// ラージオブジェクトのアップロードやその他の時間のかかるユースケースでは、タスクが完了する前に STS API 操作を繰り返し呼び出して一時的な認証情報を取得する必要がないように、適切な有効期間を設定します。
Long durationSeconds = 3600L;
try {
// STS のリージョンを指定します。デフォルト値を維持します。デフォルト値は空の文字列 ("") です。
String regionId = "";
// エンドポイントを指定します。次の行は、STS SDK for Java V3.12.0 以降に適用されます。
DefaultProfile.addEndpoint(regionId, "Sts", endpoint);
// エンドポイントを指定します。次の行は、V3.12.0 より前の STS SDK for Java バージョンに適用されます。
// DefaultProfile.addEndpoint("",regionId, "Sts", endpoint);
// デフォルトのプロファイルを作成します。
IClientProfile profile = DefaultProfile.getProfile(regionId, accessKeyId, accessKeySecret);
// プロファイルを使用してクライアントを作成します。
DefaultAcsClient client = new DefaultAcsClient(profile);
final AssumeRoleRequest request = new AssumeRoleRequest();
// 次の行は、STS SDK for Java V3.12.0 以降に適用されます。
request.setSysMethod(MethodType.POST);
// 次の行は、V3.12.0 より前の STS SDK for Java バージョンに適用されます。
// request.setMethod(MethodType.POST);
request.setRoleArn(roleArn);
request.setRoleSessionName(roleSessionName);
request.setPolicy(policy);
request.setDurationSeconds(durationSeconds);
final AssumeRoleResponse response = client.getAcsResponse(request);
System.out.println("Expiration: " + response.getCredentials().getExpiration());
System.out.println("Access Key Id: " + response.getCredentials().getAccessKeyId());
System.out.println("Access Key Secret: " + response.getCredentials().getAccessKeySecret());
System.out.println("Security Token: " + response.getCredentials().getSecurityToken());
System.out.println("RequestId: " + response.getRequestId());
} catch (ClientException e) {
System.out.println("Failed: ");
System.out.println("Error code: " + e.getErrCode());
System.out.println("Error message: " + e.getErrMsg());
System.out.println("RequestId: " + e.getRequestId());
}
}
}Python
# -*- coding: utf-8 -*-
from aliyunsdkcore import client
from aliyunsdkcore.request import CommonRequest
import json
import oss2
import os
# ステップ 1.1 で生成された RAM ユーザーの AccessKey ID と AccessKey Secret を環境変数から取得します。
access_key_id = os.getenv("ACCESS_KEY_ID")
access_key_secret = os.getenv("ACCESS_KEY_SECRET")
# ステップ 1.3 で生成された RAM ロールの ARN を環境変数から取得します。
role_arn = os.getenv("RAM_ROLE_ARN")
# ポリシーを作成します。
clt = client.AcsClient(access_key_id, access_key_secret, 'cn-hangzhou')
request = CommonRequest(product="Sts", version='2015-04-01', action_name='AssumeRole')
request.set_method('POST')
request.set_protocol_type('https')
request.add_query_param('RoleArn', role_arn)
# 異なるトークンを区別するために、カスタムのロールセッション名を指定します。例:sessiontest。
request.add_query_param('RoleSessionName', 'sessiontest')
# 一時的な認証情報の有効期間を 3,600 秒に設定します。
request.add_query_param('DurationSeconds', '3600')
request.set_accept_format('JSON')
body = clt.do_action_with_exception(request)
# RAM ユーザーの AccessKey ペアを使用して、STS に一時的な認証情報を申請します。
token = json.loads(oss2.to_unicode(body))
# STS から返された一時的な認証情報の AccessKey ID、AccessKey Secret、セキュリティトークン、および有効期限を表示します。
print('AccessKeyId: ' + token['Credentials']['AccessKeyId'])
print('AccessKeySecret: ' + token['Credentials']['AccessKeySecret'])
print('SecurityToken: ' + token['Credentials']['SecurityToken'])
print('Expiration: ' + token['Credentials']['Expiration'])Node.js
const { STS } = require('ali-oss');
const express = require("express");
const app = express();
app.get('/sts', (req, res) => {
let sts = new STS({
// ステップ 1.1 で生成された RAM ユーザーの AccessKey ID と AccessKey Secret を環境変数から取得します。
accessKeyId : process.env.ACCESS_KEY_ID,
accessKeySecret : process.env.ACCESS_KEY_SECRET
});
// 環境変数から RAM ロールの ARN を取得します (ステップ 1.3 で作成)。
// カスタムポリシーを指定して、一時的な認証情報の権限を制限します。カスタムポリシーを指定しない場合、一時的な認証情報は指定された RAM ロールのすべての権限を持ちます。
// 一時的な認証情報によって取得される権限は、ステップ 4 で設定されたロール権限と、カスタム RAM ポリシーで指定された権限の共通部分です。
// 一時的な認証情報の有効期間を指定します。単位:秒。一時的な認証情報の最小有効期間は 900 秒です。一時的な認証情報の最大有効期間は、現在のロールに指定された最大セッション期間です。この例では、有効期間は 3,600 秒に設定されています。
// 異なるトークンを区別するために、カスタムのロールセッション名を指定します。例:sessiontest。
sts.assumeRole('process.env.RAM_ROLE_ARN', ``, '3600', 'sessiontest').then((result) => {
console.log(result);
res.set('Access-Control-Allow-Origin', '*');
res.set('Access-Control-Allow-METHOD', 'GET');
res.json({
AccessKeyId: result.credentials.AccessKeyId,
AccessKeySecret: result.credentials.AccessKeySecret,
SecurityToken: result.credentials.SecurityToken,
Expiration: result.credentials.Expiration
});
}).catch((err) => {
console.log(err);
res.status(400).json(err.message);
});
});
app.listen(8000,()=>{
console.log("server listen on:8000")
})Go
package main
import (
"fmt"
"os"
openapi "github.com/alibabacloud-go/darabonba-openapi/v2/client"
sts20150401 "github.com/alibabacloud-go/sts-20150401/v2/client"
util "github.com/alibabacloud-go/tea-utils/v2/service"
"github.com/alibabacloud-go/tea/tea"
)
func main() {
// ステップ 1.1 で生成された RAM ユーザーの AccessKey ID と AccessKey Secret を環境変数から取得します。
accessKeyId := os.Getenv("ACCESS_KEY_ID")
accessKeySecret := os.Getenv("ACCESS_KEY_SECRET")
// ステップ 1.3 で生成された RAM ロールの ARN を環境変数から取得します。
roleArn := os.Getenv("RAM_ROLE_ARN")
// クライアントを作成します。
config := &openapi.Config{
// ステップ 1.1 で取得した AccessKey ID を指定します。
AccessKeyId: tea.String(accessKeyId),
// ステップ 1.1 で取得した AccessKey Secret を指定します。
AccessKeySecret: tea.String(accessKeySecret),
}
// バケットが配置されているリージョンのエンドポイントを指定します。詳細については、https://api.alibabacloud.com/product/Sts をご参照ください。
config.Endpoint = tea.String("sts.cn-hangzhou.aliyuncs.com")
client, err := sts20150401.NewClient(config)
if err != nil {
fmt.Printf("Failed to create client: %v\n", err)
return
}
// RAM ユーザーの AccessKey ペアを使用して、STS に一時的な認証情報を申請します。
request := &sts20150401.AssumeRoleRequest{
// 一時的な認証情報の有効期間を 3,600 秒に設定します。
DurationSeconds: tea.Int64(3600),
// ステップ 1.3 で生成された RAM ロールの ARN を環境変数から取得します。
RoleArn: tea.String(roleArn),
// カスタムセッション名を指定します。
RoleSessionName: tea.String("examplename"),
}
response, err := client.AssumeRoleWithOptions(request, &util.RuntimeOptions{})
if err != nil {
fmt.Printf("Failed to assume role: %v\n", err)
return
}
// STS から返された一時的な認証情報の AccessKey ID、AccessKey Secret、セキュリティトークン、および有効期限を表示します。
credentials := response.Body.Credentials
fmt.Println("AccessKeyId: " + tea.StringValue(credentials.AccessKeyId))
fmt.Println("AccessKeySecret: " + tea.StringValue(credentials.AccessKeySecret))
fmt.Println("SecurityToken: " + tea.StringValue(credentials.SecurityToken))
fmt.Println("Expiration: " + tea.StringValue(credentials.Expiration))
}php
<?php
require __DIR__ . '/vendor/autoload.php';
use AlibabaCloud\Client\AlibabaCloud;
use AlibabaCloud\Client\Exception\ClientException;
use AlibabaCloud\Client\Exception\ServerException;
use AlibabaCloud\Sts\Sts;
// ステップ 1.1 で生成された RAM ユーザーの AccessKey ID と AccessKey Secret を環境変数から取得します。
$accessKeyId = getenv("ACCESS_KEY_ID");
$accessKeySecret = getenv("ACCESS_KEY_SECRET");
// ステップ 1.3 で生成された RAM ロールの ARN を環境変数から取得します。
$roleArn = getenv("RAM_ROLE_ARN");
// Alibaba Cloud クライアントを初期化します。
AlibabaCloud::accessKeyClient($accessKeyId, $accessKeySecret)
->regionId('cn-hangzhou')
->asDefaultClient();
try {
// STS から一時的な認証情報を取得するリクエストを作成します。
$result = Sts::v20150401()
->assumeRole()
// ロールの ARN を指定します。
->withRoleArn($roleArn)
// 異なるトークンを区別するために、ロールのカスタムセッション名を指定します。
->withRoleSessionName('sessiontest')
// 一時的な認証情報の有効期間を 3,600 秒に設定します。
->withDurationSeconds(3600)
->request();
// 応答の認証情報を表示します。
$credentials = $result['Credentials'];
// STS から返された一時的な認証情報の AccessKey ID、AccessKey Secret、セキュリティトークン、および有効期限を表示します。
echo 'AccessKeyId: ' . $credentials['AccessKeyId'] . PHP_EOL;
echo 'AccessKeySecret: ' . $credentials['AccessKeySecret'] . PHP_EOL;
echo 'SecurityToken: ' . $credentials['SecurityToken'] . PHP_EOL;
echo 'Expiration: ' . $credentials['Expiration'] . PHP_EOL;
} catch (ClientException $e) {
// クライアント例外を処理します。
echo $e->getErrorMessage() . PHP_EOL;
} catch (ServerException $e) {
// サーバー例外を処理します。
echo $e->getErrorMessage() . PHP_EOL;
}Ruby
require 'sinatra'
require 'base64'
require 'open-uri'
require 'cgi'
require 'openssl'
require 'json'
require 'sinatra/reloader'
require 'sinatra/content_for'
require 'aliyunsdkcore'
# public-folder フォルダのパスを、現在のフォルダ内の templates サブフォルダに設定します。
set :public_folder, File.dirname(__FILE__) + '/templates'
def get_sts_token_for_oss_upload()
client = RPCClient.new(
# ステップ 1.1 で生成された RAM ユーザーの AccessKey ID と AccessKey Secret を環境変数から取得します。
access_key_id: ENV['ACCESS_KEY_ID'],
access_key_secret: ENV['ACCESS_KEY_SECRET'],
endpoint: 'https://sts.cn-hangzhou.aliyuncs.com',
api_version: '2015-04-01'
)
response = client.request(
action: 'AssumeRole',
params: {
# ステップ 1.3 で生成された RAM ロールの ARN を環境変数から取得します。
"RoleArn": ENV['RAM_ROLE_ARN'],
# 一時的な認証情報の有効期間を 3,600 秒に設定します。
"DurationSeconds": 3600,
# 異なるトークンを区別するために使用されるカスタムのロールセッション名を指定します。例:sessiontest。
"RoleSessionName": "sessiontest"
},
opts: {
method: 'POST',
format_params: true
}
)
end
if ARGV.length == 1
$server_port = ARGV[0]
elsif ARGV.length == 2
$server_ip = ARGV[0]
$server_port = ARGV[1]
end
$server_ip = "127.0.0.1" # 0.0.0.0 などの別の IP アドレスをリッスンするには、サーバー側で認証メカニズムを実装します。
$server_port = 8000
puts "App server is running on: http://#{$server_ip}:#{$server_port}"
set :bind, $server_ip
set :port, $server_port
get '/get_sts_token_for_oss_upload' do
token = get_sts_token_for_oss_upload()
response = {
"AccessKeyId" => token["Credentials"]["AccessKeyId"],
"AccessKeySecret" => token["Credentials"]["AccessKeySecret"],
"SecurityToken" => token["Credentials"]["SecurityToken"],
"Expiration" => token["Credentials"]["Expiration"]
}
response.to_json
end
get '/*' do
puts "********************* GET "
send_file File.join(settings.public_folder, 'index.html')
end一時的な認証情報の例
説明Alibaba Cloud アカウント、およびその RAM ユーザーと RAM ロールは、一時的な認証情報をリクエストするために STS に 1 秒あたり最大 100 件のリクエスト (RPS) を送信できます。高い同時実行性が求められるユースケースでは、一時的な認証情報を再利用してください。
一時的な認証情報の有効期限は UTC 形式です。たとえば、有効期限が 2024-04-18T11:33:40Z の場合、一時的な認証情報は 2024 年 4 月 18 日 19:33:40 (UTC+8) に失効します。
{ "AccessKeyId": "STS.****************", "AccessKeySecret": "3dZn*******************************************", "SecurityToken": "CAIS*****************************************************************************************************************************************", "Expiration": "2024-**-*****:**:50Z" }
一時的な認証情報のきめ細かな権限
一時的な認証情報が RAM ロールから権限を取得した後、一時的な認証情報の権限をさらに制限できます。たとえば、一時的な認証情報が examplebucket バケットにオブジェクトをアップロードする権限を持っている場合、アクセス認証情報がバケット内の特定のディレクトリにのみデータをアップロードするために使用できるように指定します。以下のサンプルコードは、一時的な認証情報の権限を制限します。
// 以下のポリシーは、一時的な認証情報が examplebucket バケットの src ディレクトリにのみオブジェクトをアップロードできることを指定します。 // 一時的な認証情報に最終的に付与される権限は、ステップ 4 で指定されたロール権限と、ポリシーで指定された権限の共通部分です。これにより、examplebucket バケットの src ディレクトリへのデータアップロードのみが許可されます。 String policy = "{\n" + " \"Version\": \"1\", \n" + " \"Statement\": [\n" + " {\n" + " \"Action\": [\n" + " \"oss:PutObject\"\n" + " ], \n" + " \"Resource\": [\n" + " \"acs:oss:*:*:examplebucket/src/*\" \n" + " ], \n" + " \"Effect\": \"Allow\"\n" + " }\n" + " ]\n" + "}";
ステップ 2:サプライヤーによる一時的な認証情報を使用したデータアップロード
コンプライアンスとセキュリティを向上させるためのポリシー変更により、2025 年 3 月 20 日より、新規 OSS ユーザーは、中国本土リージョンにある OSS バケットでデータ API 操作を実行する場合、カスタムドメイン名を使用する必要があります (CNAME)。これらの操作では、デフォルトのパブリックエンドポイントは制限されます。影響を受ける操作の完全なリストについては、公式発表をご参照ください。HTTPS 経由でデータにアクセスする場合、カスタムドメインに有効な SSL 証明書をバインドする必要があります。コンソールでは HTTPS が適用されるため、これはOSS コンソールへのアクセスには必須です。
以下のサンプルコードは、一時的な認証情報を使用してデータをアップロードする方法を示しています。他のプログラミング言語の OSS SDK を使用して一時的な認証情報に基づいて OSS にデータをアップロードする方法の詳細については、「概要」をご参照ください。
Java
import com.aliyun.oss.*;
import com.aliyun.oss.common.auth.CredentialsProvider;
import com.aliyun.oss.common.auth.DefaultCredentialProvider;
import com.aliyun.oss.common.comm.SignVersion;
import com.aliyun.oss.model.PutObjectRequest;
import com.aliyun.oss.model.PutObjectResult;
import java.io.File;
public class Demo {
public static void main(String[] args) throws Exception {
// ステップ 1.5 で生成された一時的な AccessKey ID、AccessKey Secret、および STS トークンを指定します。RAM ユーザーの認証情報は使用しないでください。
// STS が提供する AccessKey ID は STS で始まることに注意してください。
String accessKeyId = "yourSTSAccessKeyID";
String accessKeySecret = "yourSTSAccessKeySecret";
// STS から取得したセキュリティトークンを指定します。
String stsToken= "yourSecurityToken";
// AccessKey ID と Secret を DefaultCredentialProvider に渡して、認証情報プロバイダーを初期化します。
CredentialsProvider credentialsProvider = new DefaultCredentialProvider(accessKeyId, accessKeySecret, stsToken);
// credentialsProvider を使用してクライアントを初期化します。
ClientBuilderConfiguration clientBuilderConfiguration = new ClientBuilderConfiguration();
// V4 署名アルゴリズムの使用を明示的に宣言します。
clientBuilderConfiguration.setSignatureVersion(SignVersion.V4);
// OSSClient インスタンスを作成します。
// OSSClient が不要になったら、shutdown メソッドを呼び出してリソースを解放します。
OSS ossClient = OSSClientBuilder.create()
// バケットが配置されているリージョンのエンドポイントを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、エンドポイントを https://oss-cn-hangzhou.aliyuncs.com に設定します。
.endpoint("endpoint")
.credentialsProvider(credentialsProvider)
.clientConfiguration(clientBuilderConfiguration)
// リージョン ID を指定します。例:cn-hangzhou。
.region("region")
.build();
try {
// PutObjectRequest オブジェクトを作成します。ローカルファイル exampletest.txt を examplebucket にアップロードします。
PutObjectRequest putObjectRequest = new PutObjectRequest("examplebucket", "exampletest.txt", new File("D:\\localpath\\exampletest.txt"));
// オプション。オブジェクトのストレージクラスと ACL を指定します。
// ObjectMetadata metadata = new ObjectMetadata();
// metadata.setHeader(OSSHeaders.OSS_STORAGE_CLASS, StorageClass.Standard.toString());
// metadata.setObjectAcl(CannedAccessControlList.Private);
// putObjectRequest.setMetadata(metadata);
// オブジェクトをアップロードします。
PutObjectResult result = ossClient.putObject(putObjectRequest);
} catch (OSSException oe) {
System.out.println("Caught an OSSException, which means your request made it to OSS, "
+ "but was rejected with an error response for some reason.");
System.out.println("Error Message:" + oe.getErrorMessage());
System.out.println("Error Code:" + oe.getErrorCode());
System.out.println("Request ID:" + oe.getRequestId());
System.out.println("Host ID:" + oe.getHostId());
} catch (ClientException ce) {
System.out.println("Caught an ClientException, which means the client encountered "
+ "a serious internal problem while trying to communicate with OSS, "
+ "such as not being able to access the network.");
System.out.println("Error Message:" + ce.getMessage());
} finally {
if (ossClient != null) {
ossClient.shutdown();
}
}
}
}
Python
OSS SDK for Python には、2.0 と 1.0 の 2 つのバージョンがあります。OSS SDK for Python 2.0 は 1.0 を完全にリファクタリングしたもので、認証、リクエストの再試行、エラー処理などのコア操作を合理化しています。より柔軟なパラメーター構成を提供し、新しい高度な機能を導入しています。以下の例は、実際の要件に基づいて OSS SDK for Python を実装するのに役立ちます。
OSS SDK for Python 2.0
import alibabacloud_oss_v2 as oss
def main():
# ステップ 1.5 で生成された一時的な AccessKey ID、AccessKey Secret、および STS トークンを指定します。RAM ユーザーの認証情報は使用しないでください。
# STS が提供する AccessKey ID は STS で始まることに注意してください。
sts_access_key_id = 'yourSTSAccessKeyID'
sts_access_key_secret = 'yourSTSAccessKeySecret'
# STS から取得した STS トークンを指定します。
sts_security_token = 'yourSecurityToken'
# 静的な認証情報プロバイダーを作成し、STS が提供する AccessKey ID、AccessKey Secret、および STS トークンを明示的に指定します。
credentials_provider = oss.credentials.StaticCredentialsProvider(
access_key_id=sts_access_key_id,
access_key_secret=sts_access_key_secret,
security_token=sts_security_token,
)
# SDK のデフォルト構成をロードし、認証情報プロバイダーを指定します。
cfg = oss.config.load_default()
cfg.credentials_provider = credentials_provider
# バケットが配置されているリージョンを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、リージョンを cn-hangzhou に設定します。
cfg.region = 'cn-hangzhou'
# 上記の構成を使用して OSSClient インスタンスを作成します。
client = oss.Client(cfg)
# アップロードするローカルオブジェクトの完全なパスを指定します。例:D:\\localpath\\exampletest.txt。
local_file_path = 'D:\\localpath\\exampletest.txt'
with open(local_file_path, 'rb') as file:
data = file.read()
# exampletest.txt を examplebucket にアップロードするリクエストを実行します。
result = client.put_object(oss.PutObjectRequest(
# バケットの名前。
bucket='examplebucket',
# アップロードするオブジェクトの名前。
key='exampletest.txt',
body=data,
))
# HTTP ステータスコード、リクエスト ID、MD5 ハッシュ、ETag、CRC-64 値、およびオブジェクトバージョン ID を表示して、リクエストが成功したかどうかを確認します。
print(f'status code: {result.status_code},'
f' request id: {result.request_id},'
f' content md5: {result.content_md5},'
f' etag: {result.etag},'
f' hash crc64: {result.hash_crc64},'
f' version id: {result.version_id},'
)
# スクリプトが直接実行されたときに main 関数を呼び出します。
if __name__ == "__main__":
main() # スクリプトのエントリポイント。スクリプトが直接実行されると、main 関数が呼び出されます。OSS SDK for Python 1.0
# -*- coding: utf-8 -*-
import oss2
# バケットが配置されているリージョンのエンドポイントを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、エンドポイントを https://oss-cn-hangzhou.aliyuncs.com に設定します。
endpoint = 'https://oss-cn-hangzhou.aliyuncs.com'
# ステップ 1.5 で生成された一時的な AccessKey ID と AccessKey Secret を指定します。Alibaba Cloud アカウントの AccessKey ID と AccessKey Secret は使用しないでください。
sts_access_key_id = 'yourAccessKeyId'
sts_access_key_secret = 'yourAccessKeySecret'
# バケットの名前を指定します。
bucket_name = 'examplebucket'
# 文字列を使用してオブジェクトの完全なパスを指定します。完全なパスにバケット名を含めないでください。
object_name = 'examplebt.txt'
# ステップ 1.5 で生成された STS トークンを入力します。
security_token = 'yourSecurityToken'
# 一時的な認証情報を使用して StsAuth インスタンスを初期化します。
auth = oss2.StsAuth(sts_access_key_id,
sts_access_key_secret,
security_token)
# StsAuth インスタンスを使用してバケットを初期化します。
bucket = oss2.Bucket(auth, endpoint, bucket_name)
# オブジェクトをアップロードします。
result = bucket.put_object(object_name, "hello world")
print(result.status)Go
OSS SDK for Go には、2.0 と 1.0 の 2 つのバージョンがあります。OSS SDK for Go 2.0 は 1.0 を完全にリファクタリングしたもので、認証、リクエストの再試行、エラー処理などのコア操作を合理化しています。より柔軟なパラメーター構成を提供し、新しい高度な機能を導入しています。以下の例は、実際の要件に基づいて OSS SDK for Go を実装するのに役立ちます。
OSS SDK for Go 2.0
package main
import (
"context"
"log"
"github.com/aliyun/alibabacloud-oss-go-sdk-v2/oss"
"github.com/aliyun/alibabacloud-oss-go-sdk-v2/oss/credentials"
)
func main() {
// バケットが配置されているリージョンを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、リージョンを cn-hangzhou に設定します。
region := "cn-hangzhou"
// ステップ 1.5 で生成された一時的な AccessKey ID、AccessKey Secret、および STS トークンを指定します。RAM ユーザーの認証情報は使用しないでください。
// STS が提供する AccessKey ID は STS で始まることに注意してください。
accessKeyID := "yourSTSAccessKeyID"
accessKeySecret := "yourSTSAccessKeySecret"
// STS から取得した STS トークンを指定します。
stsToken := "yourSecurityToken"
// NewStaticCredentialsProvider メソッドを使用して、AccessKey ID、AccessKey Secret、および STS トークンを指定します。
provider := credentials.NewStaticCredentialsProvider(accessKeyID, accessKeySecret, stsToken)
// SDK のデフォルト構成をロードし、認証情報プロバイダーとリージョンを指定します。
cfg := oss.LoadDefaultConfig().
WithCredentialsProvider(provider).
WithRegion(region)
// OSS クライアントを作成します。
client := oss.NewClient(cfg)
// アップロードするローカルファイルのパスを指定します。例:D:\\localpath\\exampletest.txt。
localFile := "D:\\localpath\\exampletest.txt"
// オブジェクトをアップロードするリクエストを作成します。
putRequest := &oss.PutObjectRequest{
Bucket: oss.Ptr("examplebucket"), // バケットの名前。
Key: oss.Ptr("exampletest.txt"), // アップロードするオブジェクトの名前。
StorageClass: oss.StorageClassStandard, // オブジェクトのストレージクラスを標準に設定します。
Acl: oss.ObjectACLPrivate, // オブジェクトの ACL を非公開に設定します。
Metadata: map[string]string{
"yourMetadataKey1": "yourMetadataValue1", // オブジェクトのメタデータを構成します。
},
}
// exampletest.txt を examplebucket にアップロードするリクエストを実行します。
result, err := client.PutObjectFromFile(context.TODO(), putRequest, localFile)
if err != nil {
log.Fatalf("failed to put object from file %v", err)
}
// オブジェクトアップロードの結果を表示します。
log.Printf("put object from file result:%#v\n", result)
}OSS SDK for Go 1.0
package main
import (
"fmt""github.com/aliyun/aliyun-oss-go-sdk/oss""os"
)
func main() {
// 環境変数から一時的な認証情報を取得します。サンプルコードを実行する前に、OSS_ACCESS_KEY_ID、OSS_ACCESS_KEY_SECRET、および OSS_SESSION_TOKEN 環境変数が構成されていることを確認してください。
provider, err := oss.NewEnvironmentVariableCredentialsProvider()
if err != nil {
fmt.Println("Error:", err)
os.Exit(-1)
}
// OSSClient インスタンスを作成します。// バケットが配置されているリージョンのエンドポイントを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、エンドポイントを https://oss-cn-hangzhou.aliyuncs.com に設定します。実際のエンドポイントを指定してください。
client, err := oss.New("yourEndpoint", "", "", oss.SetCredentialsProvider(&provider))
if err != nil {
fmt.Println("Error:", err)
os.Exit(-1)
}
// バケットの名前を指定します。例:examplebucket。
bucketName := "examplebucket"// オブジェクトの完全なパスを指定します。完全なパスにバケット名を含めないでください。例:exampledir/exampleobject.txt。
objectName := "exampledir/exampleobject.txt"// ローカルオブジェクトの完全なパスを指定します。例:D:\\localpath\\examplefile.txt。
filepath := "D:\\localpath\\examplefile.txt"
bucket,err := client.Bucket(bucketName)
// 一時的な認証情報を使用してローカルファイルをアップロードします。
err = bucket.PutObjectFromFile(objectName,filepath)
if err != nil {
fmt.Println("Error:", err)
os.Exit(-1)
}
fmt.Println("upload success")
}Node.js
このサンプルコードには Axios が必要です。
const axios = require("axios");
const OSS = require("ali-oss");
// 一時的な認証情報を使用して OSSClient インスタンスを初期化します。このインスタンスは、OSS リソースへの一時的なアクセスを許可するために使用されます。
const getToken = async () => {
// クライアントが一時的な認証情報を取得するために使用するアドレスを指定します。
await axios.get("http://localhost:8000/sts").then((token) => {
const client = new OSS({
// バケットが配置されているリージョンを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、リージョンを oss-cn-hangzhou に設定します。
region: 'oss-cn-hangzhou',
// ステップ 1.5 で生成された一時的な AccessKey ID、AccessKey Secret、および STS トークンを指定します。RAM ユーザーの認証情報は使用しないでください。
accessKeyId: token.data.AccessKeyId,
accessKeySecret: token.data.AccessKeySecret,
// ステップ 1.5 で生成された STS トークンを入力します。
stsToken: token.data.SecurityToken,
authorizationV4: true,
// バケットの名前を指定します。
bucket: "examplebucket",
// 一時的な認証情報をリフレッシュします。
refreshSTSToken: async () => {
const refreshToken = await axios.get("http://localhost:8000/sts");
return {
accessKeyId: refreshToken.data.AccessKeyId,
accessKeySecret: refreshToken.data.AccessKeySecret,
stsToken: refreshToken.data.SecurityToken,
};
},
});
// 一時的な認証情報を使用してオブジェクトをアップロードします。
// オブジェクトの完全なパスを指定します。完全なパスにバケット名を含めないでください。例:exampleobject.jpg。
// ローカルオブジェクトの完全なパスを指定します。例:D:\\example.jpg。
client.put('exampleobject.jpg', 'D:\\example.jpg').then((res)=>{console.log(res)}).catch(e=>console.log(e))
});
};
getToken()php
<?php
if (is_file(__DIR__ . 'autoload.php')) {
require_once __DIR__ . 'autoload.php';
}
if (is_file(__DIR__ . '/vendor/autoload.php')) {
require_once __DIR__ . '/vendor/autoload.php';
}
use OSS\Credentials\StaticCredentialsProvider;
use OSS\OssClient;
use OSS\Core\OssException;
try {
// ステップ 1.5 で生成された一時的な AccessKey ID、AccessKey Secret、および STS トークンを指定します。RAM ユーザーの認証情報は使用しないでください。
// STS が提供する AccessKey ID は STS で始まることに注意してください。
$accessKeyId = 'yourSTSAccessKeyID';
$accessKeySecret = 'yourSTSAccessKeySecret';
// STS から取得した STS トークンを指定します。
$securityToken = 'yourSecurityToken';
// StaticCredentialsProvider を使用して認証情報プロバイダーを作成します。
$provider = new StaticCredentialsProvider($accessKeyId, $accessKeySecret, $securityToken);
// バケットが配置されているリージョンのエンドポイントを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、エンドポイントを https://oss-cn-hangzhou.aliyuncs.com に設定します。
$endpoint = "https://oss-cn-hangzhou.aliyuncs.com";
// バケットの名前を指定します。例:examplebucket。
$bucket= "examplebucket";
// アップロードするオブジェクトの名前を指定します。
$object = "exampletest.txt";
// アップロードするローカルオブジェクトの完全なパスを指定します。例:D:\\localpath\\exampletest.txt。
$localFilePath = "D:\\localpath\\exampletest.txt";
// アップロードリクエストのヘッダーを構成して、アップロードされた文字列に関する情報を指定します。たとえば、オブジェクトの ACL を非公開に設定し、オブジェクトのユーザーメタデータを構成します。
$options = array(
OssClient::OSS_HEADERS => array(
'x-oss-object-acl' => 'private',
'x-oss-meta-info' => 'yourinfo'
),
);
$config = array(
"provider" => $provider,
"endpoint" => $endpoint,
"signatureVersion" => OssClient::OSS_SIGNATURE_VERSION_V4,
// バケットが配置されているリージョンを指定します。たとえば、バケットが中国 (杭州) リージョンにある場合、リージョンを cn-hangzhou に設定します。
"region" => "cn-hangzhou"
);
// 上記の構成を使用して OSSClient インスタンスを作成します。
$ossClient = new OssClient($config);
// exampletest.txt という名前のローカルファイルを examplebucket にアップロードするリクエストを送信します。
$ossClient->putObject($bucket, $object, $localFilePath, $options);
} catch (OssException $e) {
printf($e->getMessage() . "\n");
return;
}Ruby
require 'aliyun/sts'
require 'aliyun/oss'
client = Aliyun::OSS::Client.new(
# この例では、中国 (杭州) リージョンのエンドポイントが使用されています。実際のエンドポイントを指定してください。
endpoint: 'https://oss-cn-hangzhou.aliyuncs.com',
# ステップ 1.5 で生成された一時的な AccessKey ID と AccessKey Secret を指定します。Alibaba Cloud アカウントの AccessKey ID と AccessKey Secret は使用しないでください。
access_key_id: 'token.access_key_id',
access_key_secret: 'token.access_key_secret',
# ステップ 1.5 で生成された STS トークンを入力します。
sts_token: 'token.security_token'
)
# バケットの名前を指定します。例:examplebucket。
bucket = client.get_bucket('examplebucket')
# オブジェクトをアップロードします。
bucket.put_object('exampleobject.txt', :file => 'D:\test.txt')よくある質問
エラー「You are not authorized to do this action. You should be authorized by RAM」を解決するにはどうすればよいですか?
エラー「The Min/Max value of DurationSeconds is 15min/1hr」を解決するにはどうすればよいですか?
エラー「The security token you provided is invalid」を解決するにはどうすればよいですか?
エラー「The OSS Access Key Id you provided does not exist in our records」を解決するにはどうすればよいですか?
エラー「AccessDenied: Anonymous access is forbidden for this operation」を解決するにはどうすればよいですか?
エラー NoSuchBucket を解決するにはどうすればよいですか?
一時的な認証情報を使用して OSS リソースにアクセスしようとするとエラー「You have no right to access this object because of bucket acl」が発生する場合、どうすれば解決できますか?
STS から取得した一時的な認証情報を使用して OSS リソースに対する操作を実行する際に、エラー「Access denied by authorizer's policy」が発生する場合、どうすれば解決できますか?
エラー「The bucket you are attempting to access must be addressed using the specified endpoint」を解決するにはどうすればよいですか?
複数のセットの一時的な認証情報を同時に取得できますか?
時刻形式のエラーを解決するにはどうすればよいですか?
0003-0000301 エラーを解決するにはどうすればよいですか?
関連ドキュメント
一時的な認証情報を使用してクライアントから直接 OSS にデータをアップロードし、ファイルサイズ、ファイルタイプ、宛先ディレクトリなどのアップロード条件を指定します。詳細については、「クライアントからの直接アップロード」をご参照ください。
署名付き URL を使用して、一時的な認証情報を使用してアップロードされたオブジェクトを共有します。詳細については、「署名付き URL を使用したファイルのダウンロードまたはプレビュー」をご参照ください。