After a website is added to WAF, the website can be accessed over HTTP, but fails to be accessed over HTTPS. For example, the website may fail to open, the certificate may be untrusted, interfaces may fail to be called, or errors may be reported for devices, OSs, or apps of specific types. This topic describes how to troubleshoot the access issues.
Check whether HTTPS is selected in the WAF console and whether the required certificate is uploaded
Check whether the certificate chain is valid
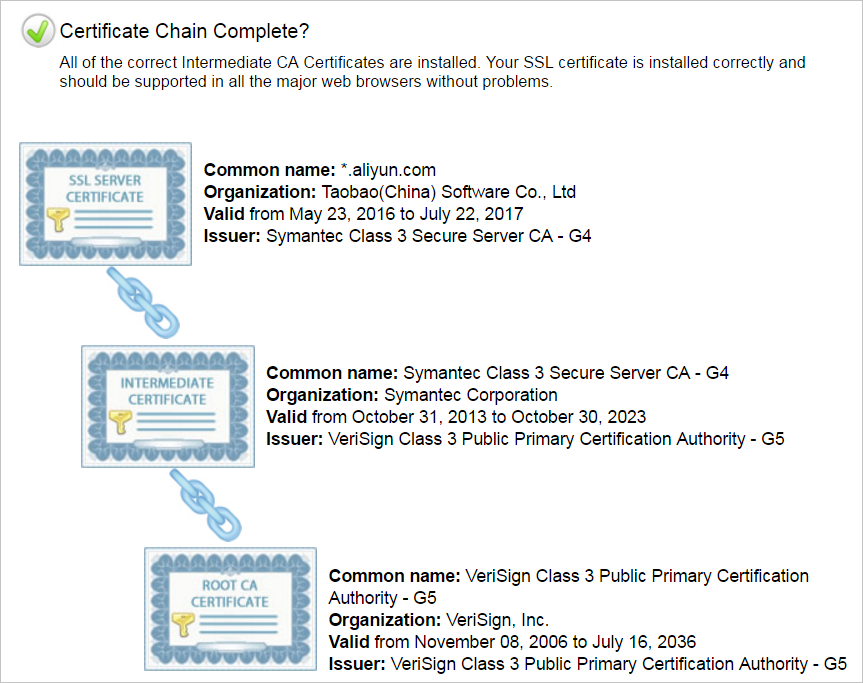
-----BEGIN CERTIFICATE-----
……
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
……
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
……
-----END CERTIFICATE-----If a certificate chain is invalid, the browser displays an on-screen message to prompt that the certificate is untrusted. In this case, if the website is accessed from Android mobile phones, specific OSs, or apps of specific types, errors are reported in some environments.
Check whether a server name indication (SNI) compatibility issue occurs
If clients or apps of specific types cannot access your website over HTTPS and the error message "SSL handshake failed/error" or "the certificate cannot be trusted" is displayed, the clients or apps may not support SNI. Clients that use outdated versions of Android and apps that are developed by using outdated versions of Java are incompatible with SNI. Internet Explorer, outdated mobile phones, and callback interfaces for third-party payment systems are incompatible with SNI.
Most browsers, apps, and payment callback interfaces of Alipay and WeChat support SNI. If you can access your website when your website is mapped to the origin server but cannot access your website when your website is mapped to WAF, an SNI compatibility issue occurs. We recommend that you upgrade the client or map your website to the origin server.
For more information, see HTTPS access exceptions arising from SNI compatibility ("Certificate not trusted").
Check whether your website is hosted on Windows Server 2003 or IIS6 servers
After a website that is hosted on Windows Server 2003 or IIS6 servers is added to WAF, the HTTP 502 status code is returned when the website is accessed over HTTPS. The status code is returned because the TLS version and cipher suite of the system are outdated and do not meet the security requirements. The TLS and cipher suite are incompatible with the default HTTPS back-to-origin algorithm of WAF. The feature that allows you to redirect HTTPS requests to origin servers is not supported for websites that are hosted Windows Server 2003 servers. Microsoft recommends that you do not host your HTTPS website on Windows Server 2003 servers. We recommend that you host your website on servers that run Windows Server 2008 or later to ensure secure communications.
Check whether the Diffie-Hellman (DH) key meets the length requirements
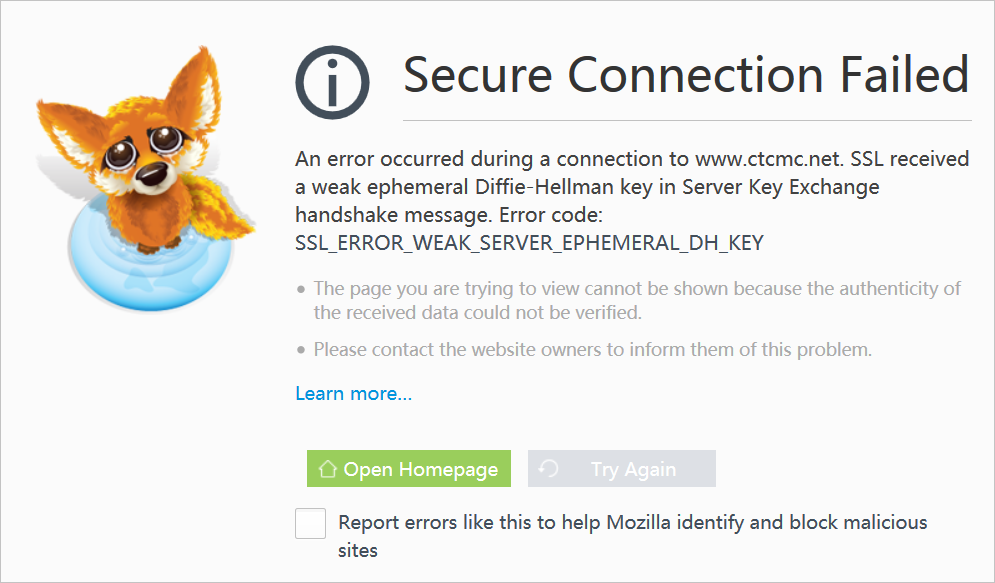
SSL routines:ssl3_check_cert_and_algorithm:dh key too small.
Check whether HTTP is selected
If you enable the feature that redirects HTTP requests to HTTPS requests on the origin server, you must select HTTP and HTTPS in the WAF console. If you select only HTTP or HTTPS in this situation, WAF cannot forward HTTPS requests to the origin server, and errors are reported.