If messages cannot be sent or received or connection cannot be established when you use an SDK to connect to an ApsaraMQ for Kafka instance to send and receive messages, you can use the self-check tool provided by ApsaraMQ for Kafka to perform a health check on the instance. A health check can help determine whether the network is connected, whether the instance runs as expected, and whether the client code is correctly configured.
Prerequisites
JDK 1.8 or later is installed. For more information, see Java Downloads.
The self-check tool kafka-checker.zip is downloaded and decompressed.
A topic and a consumer group are created on the ApsaraMQ for Kafka instance. For more information, see Step 3: Create resources. The topic and consumer group are used to test message production and consumption.
Test network connectivity
Obtain the endpoint of the ApsaraMQ for Kafka instance.
Log on to the ApsaraMQ for Kafka console.
In the Resource Distribution section of the Overview page, select the region where the ApsaraMQ for Kafka instance that you want to manage resides.
On the Instances page, click the name of the instance that you want to manage.
In the Endpoint Information section of the Instance Details page, view the endpoint of the instance.
 Note
NoteFor information about the differences among different types of endpoints, see Comparison among endpoints.
Use telnet to test the network connectivity. In this example, the Linux operating system is used.
Log on to the Linux operating system and enter the path in which the KafkaChecker.jar tool resides.
cd /usr/opt/kafka-checkerReplace
/usr/opt/kafka-checkerwith the actual local path.Run the following command to test whether the client can be connected to ApsaraMQ for Kafka:
java -jar KafkaChecker.jar telnet -s EndpointFor example, if the client is connected to the ApsaraMQ for Kafka instance over a virtual private cloud (VPC) by using the default endpoint, run
java -jar KafkaChecker.jar telnet -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9092,alikafka-pre-cn-zv**********-2-vpc.alikafka.aliyuncs.com:9092,alikafka-pre-cn-zv**********-3-vpc.alikafka.aliyuncs.com:9092.NoteIf a client is connected to an ApsaraMQ for Kafka instance over a VPC by using the default endpoint, make sure that the client and the instance are deployed in the same VPC.
If information similar to the following figure is returned, the network is connected.
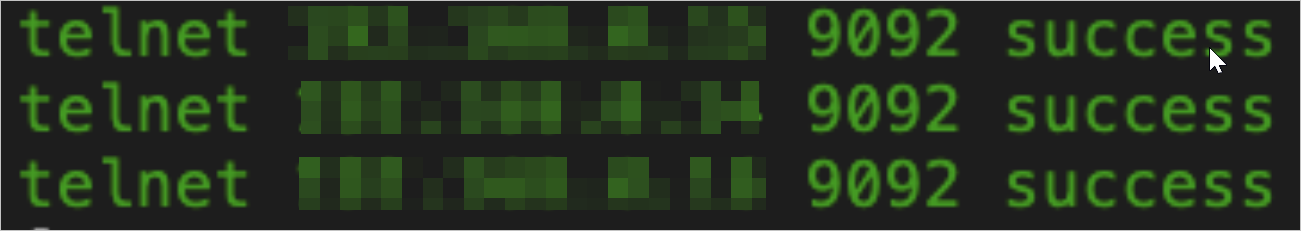
If information similar to the following figure is returned, the endpoint whitelist is not configured for the ApsaraMQ for Kafka instance. For information about how to configure a whitelist, see Configure whitelists.
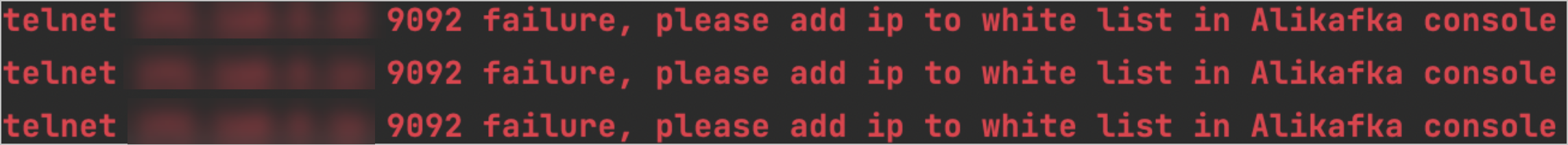
Test message sending
If a message is sent, real test data is generated. You must create a topic that is specifically used for self-check to prevent the impact on real business data.
Run one of the following commands to send messages based on the network type:
If the client is connected to the ApsaraMQ for Kafka instance by using the default endpoint and port 9092, run the following command:
java -jar KafkaChecker.jar send -s endpoint: 9092 --topic Topic nameExample:
java -jar KafkaChecker.jar send -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9092 --topic testIf the client is connected to the ApsaraMQ for Kafka instance over the Internet by using the Secure Sockets Layer (SSL) endpoint and port 9093, Simple Authentication and Security Layer (SASL) allows you to use the PLAIN or SCRAM-SHA-256 mechanism for authentication. In this case, run the command that corresponds to the authentication mechanism to send messages.
NoteIf a client is connected to an ApsaraMQ for Kafka instance over the Internet, the default SASL user of the instance uses the PLAIN mechanism for authentication.
You can create a Simple Authentication and Security Layer (SASL) user to perform fine-grained access control. You can specify the authentication mechanism as PLAIN or SCRAM-SHA-256. For more information, see Grant permissions to SASL users. You must run the command that corresponds to the authentication mechanism to send messages.
PLAIN mechanism
java -jar KafkaChecker.jar send -sm PLAIN -ss true -u username -psw password -s Endpoint domain name:9093 --topic Topic nameExample:
java -jar KafkaChecker.jar send -sm PLAIN -ss true -u test -psw test**** -s alikafka-pre-cn-zv**********-1.alikafka.aliyuncs.com:9093 --topic testSCRAM-SHA-256 mechanism
java -jar KafkaChecker.jar send -sm SCRAM-SHA-256 -ss true -u username -psw password -s Endpoint domain name:9093 --topic Topic nameExample:
java -jar KafkaChecker.jar send -sm SCRAM-SHA-256 -ss true -u test -psw test**** -s alikafka-pre-cn-zv**********-1.alikafka.aliyuncs.com:9093 --topic testIf the client is connected to the ApsaraMQ for Kafka instance over a VPC by using the SSL endpoint and port 9094, SASL allows you to use the PLAIN or SCRAM-SHA-256 mechanism for authentication. In this case, run the command that corresponds to the authentication mechanism to send messages.
PLAIN mechanism
java -jar KafkaChecker.jar send -sm PLAIN -sp true -u username -psw password -s Endpoint domain name:9094 --topic Topic nameExample:
java -jar KafkaChecker.jar send -sm PLAIN -sp true -u test -psw test**** -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9094 --topic testSCRAM-SHA-256 mechanism
java -jar KafkaChecker.jar send -sm SCRAM-SHA-256 -sp true -u username -psw password -s Endpoint domain name:9094 --topic Topic nameExample:
java -jar KafkaChecker.jar send -sm SCRAM-SHA-256 -sp true -u test -psw test**** -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9094 --topic test
If information similar to the following figure is returned, the messages are sent.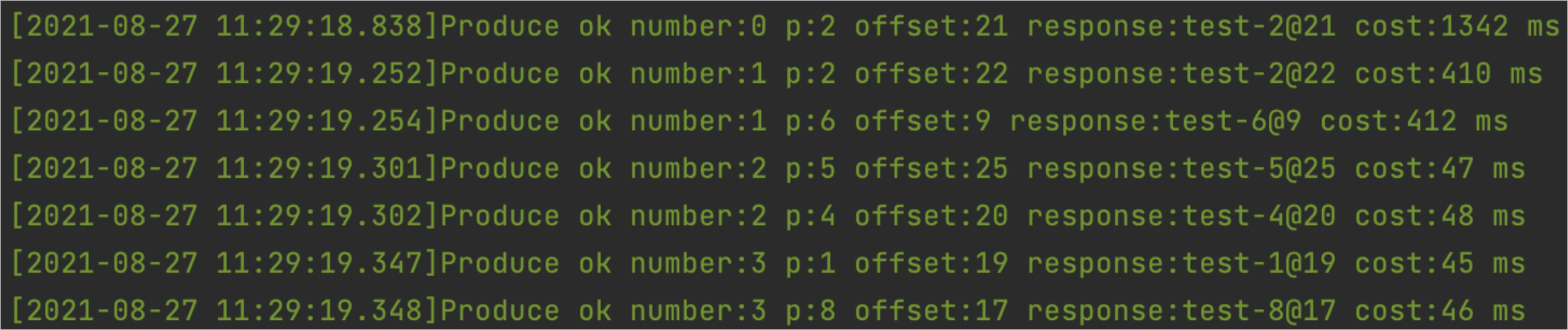
Test message consumption
Run one of the following commands to consume messages based on the network type:
If the client is connected to the ApsaraMQ for Kafka instance by using the default endpoint and port 9092, run the following command:
java -jar KafkaChecker.jar pull -s Endpoint domain name:9092 --topic Topic name --group Group name --partition 0 --offset 0 --count 10Example:
java -jar KafkaChecker.jar pull -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9092 --topic test --group test --partition 0 --offset 0 --count 10If the client is connected to the ApsaraMQ for Kafka instance over the Internet by using the SSL endpoint and port 9093, SASL allows you to use the PLAIN or SCRAM-SHA-256 mechanism for authentication. In this case, run the command that corresponds to the authentication mechanism to consume messages.
NoteIf a client is connected to an ApsaraMQ for Kafka instance over the Internet, the default SASL user of the instance uses the PLAIN mechanism for authentication.
You can create a SASL user to perform fine-grained access control. You can specify the authentication mechanism as PLAIN or SCRAM-SHA-256. For more information, see Grant permissions to SASL users. You must run the command that corresponds to the authentication mechanism to consume messages.
PLAIN mechanism
java -jar KafkaChecker.jar pull -sm PLAIN -ss true -u username -psw password -s Endpoint domain name:9093 --topic Topic name --group Group name --partition 0 --offset 0 --count 10Example:
java -jar KafkaChecker.jar pull -sm PLAIN -ss true -u test -psw test**** -s alikafka-pre-cn-zv**********-1.alikafka.aliyuncs.com:9093 --topic test --group test --partition 0 --offset 0 --count 10SCRAM-SHA-256 mechanism
java -jar KafkaChecker.jar pull -sm SCRAM-SHA-256 -ss true -u username -psw password -s Endpoint domain name:9093 --topic Topic name --group Group name --partition 0 --offset 0 --count 10Example:
java -jar KafkaChecker.jar pull -sm SCRAM-SHA-256 -ss true -u test -psw test**** -s alikafka-pre-cn-zv**********-1.alikafka.aliyuncs.com:9093 --topic test --group test --partition 0 --offset 0 --count 10If the client is connected to the ApsaraMQ for Kafka instance over a VPC by using the SSL endpoint and port 9094, SASL allows you to use the PLAIN or SCRAM-SHA-256 mechanism for authentication. In this case, run the command that corresponds to the authentication mechanism to consume messages.
PLAIN mechanism
java -jar KafkaChecker.jar pull -sm PLAIN -sp true -u username -psw password -s Endpoint domain name:9094 --topic Topic name --group Group name --partition 0 --offset 0 --count 10Example:
java -jar KafkaChecker.jar pull -sm PLAIN -sp true -u test -psw test**** -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9094 --topic test --group test --partition 0 --offset 0 --count 10SCRAM-SHA-256 mechanism
java -jar KafkaChecker.jar pull -sm SCRAM-SHA-256 -sp true -u username -psw password -s Endpoint domain name:9094 --topic Topic name --group Group name --partition 0 --offset 0 --count 10Example:
java -jar KafkaChecker.jar pull -sm SCRAM-SHA-256 -sp true -u test -psw test**** -s alikafka-pre-cn-zv**********-1-vpc.alikafka.aliyuncs.com:9094 --topic test --group test --partition 0 --offset 0 --count 10
If information similar to the following figure is returned, the messages are consumed.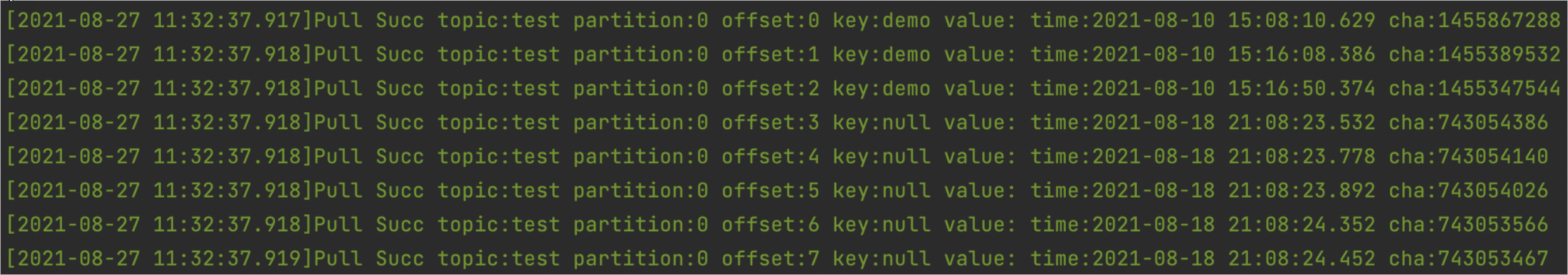
References
For information about the related SDK code packages, see Overview.