Function Compute may need to access other Alibaba Cloud services when functions run. For example, it may need to deliver function logs to a Logstore in Simple Log Service, pull images from Container Registry, or access services that are deployed in virtual private clouds (VPCs). Therefore, you must grant Function Compute permissions to access these other Alibaba Cloud services. AliyunFCDefaultRole is a default role that grants coarse-grained permissions needed for Function Compute to operate properly. If more specific permissions are required, you can manually create a role to grant those permissions to your services and functions.
How it works
Based on the function role, Function Compute uses AssumeRole to obtain a Security Token Service (STS) token as the temporary key. It then passes the temporary key to the function by using the Credentials or credentials parameter in the context. This temporary key contains all the resources for which the function has been granted permissions. You can use it in your function code for Function Compute to access other Alibaba Cloud services.
The temporary key is valid for 36 hours and cannot be modified. The maximum duration allowed to execute a function is 24 hours. Therefore, the temporary key remains valid during the execution of the function.
The location of the Credentials or credentials parameter varies in different runtimes. You can refer to the following topics for references. It should be noted that when you use a custom runtime or a Custom Container runtime, the temporary key is injected into the headers of HTTP requests.
AliyunFCDefaultRole
To simplify permission granting, Function Compute provides a default system role named AliyunFCDefaultRole, which can grant Function Compute permissions to access certain Alibaba Cloud services. For more information about how to create this default role and let Function Compute assume the role, see Step 1: Activate Function Compute.
You can log on to the Resource Access Management (RAM) console to view the permission policies bound to AliyunFCDefaultRole.
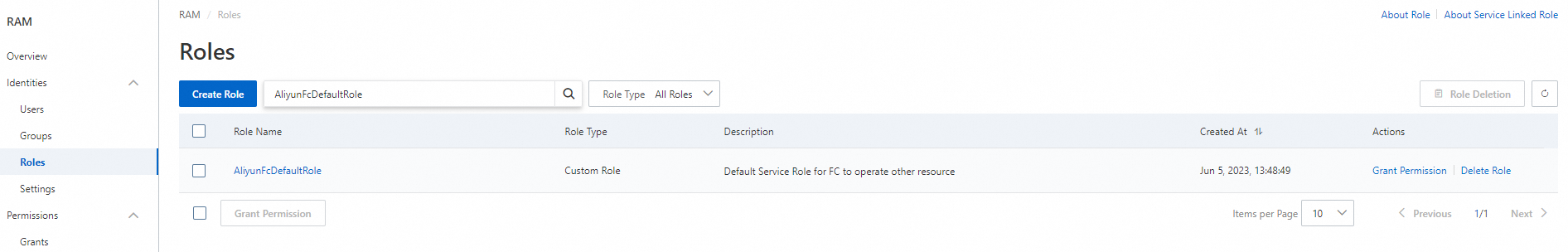
AliyunFCDefaultRole is a default system role dedicated to Function Compute that can be assumed by all Function Compute services. Do not attach any additional policies to the role. If the permissions provided by this default role cannot meet your business requirements, you can create other roles and attach permission policies to them as needed. For more information, see Create a RAM role for a trusted Alibaba Cloud service.
Example: Grant Function Compute permissions to access OSS
In this example, Function Compute is granted permissions to manage Object Storage Service (OSS) resources. If you want to grant all functions in a specified Function Compute service permissions to manage OSS resources, you can bind the corresponding role to that service.
Prerequisites
The service and function are created. For more information, see Create a service and Create a function.
Procedure
Log on to the Function Compute console. In the left-side navigation pane, click Services & Functions.
In the top navigation bar, select a region. On the Services page, find the desired service and click Configure in the Actions column.
In the Role Settings section of the Modify Service page, click Create Role to go to the RAM console. Create a role as prompted and grant the required permissions to that role.
If you already have a usable role, you can directly use it. If the role does not have the required permissions, you can click Modify Policy to attach policies to the role. For more information, see Grant permissions to a RAM role.
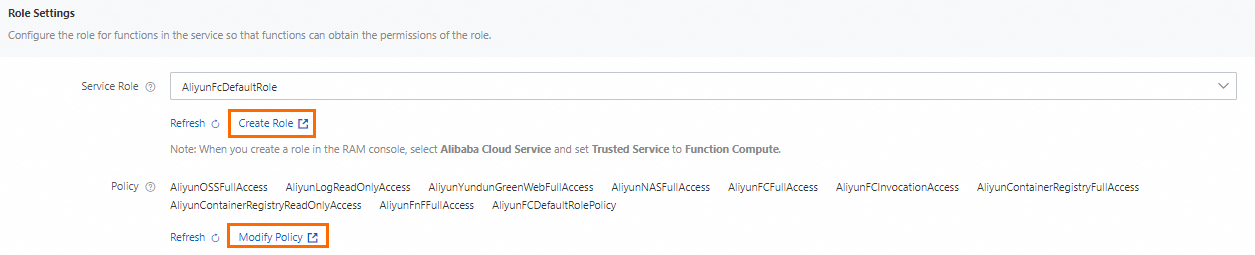
On the Roles page of the RAM console, click Create Role.
In the Select Role Type step, select Alibaba Cloud Service as the trusted entity, and click Next.
In the Configure Role step, set Role Type to Normal Service Role, specify the RAM role name, set Select Trusted Service to Function Compute, and then click OK. In this example, the RAM role name is
mytestrole.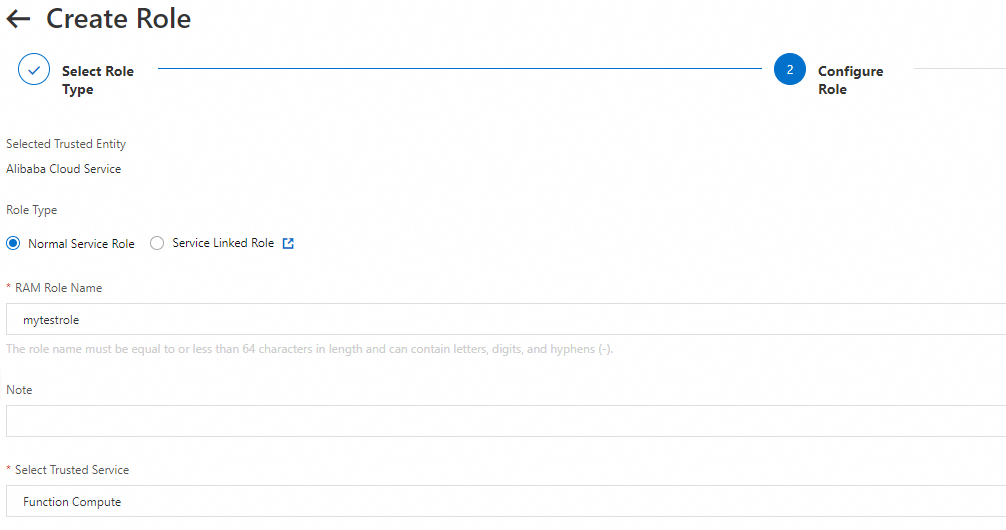
In the Finish step, click Add Permissions to RAM Role and click Grant Permission.
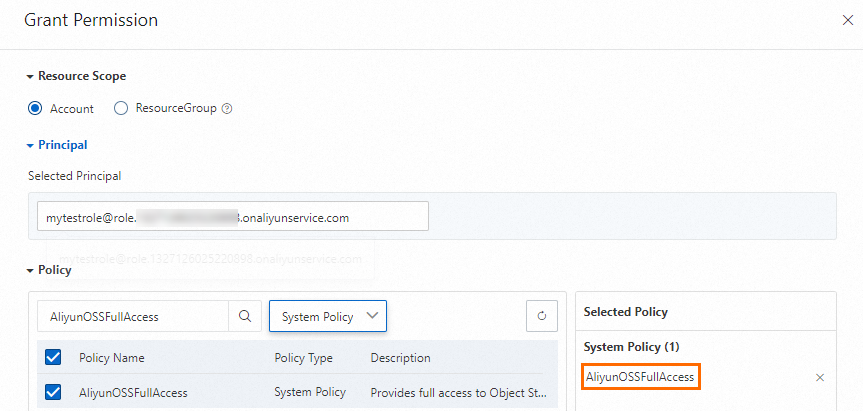
In the Grant Permission panel, specify the Resource Scope and Principal parameters. The principal defaults to the selected role. Select the system and custom policies that you need, which will then be added to the Selected Policy section on the right side of the panel. Once you have made your selections, click Grant permissions. For more information, see Policies and sample policies. The following items describe the options for the Resource Scope parameter.
Account: The permissions are valid for all resources within the current Alibaba Cloud account.
ResourceGroup: The permissions are valid for a specific resource group. If you select ResourceGroup for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group.
In this example, AliyunOSSFullAccess is attached to the created role to grant Function Compute permissions to access OSS.
Bind the new role
mytestrolecreated in the previous step to the Function Compute service to which you want to grant permissions.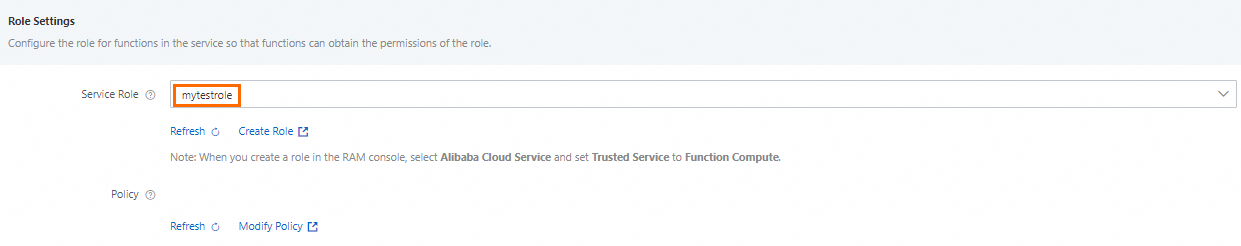
After the service assumes the
mytestrolerole, test whether all functions in that service can manage OSS resources.Find the function that you want to test from the service list, and then click it. In the Code tab of the function, click the arrow next to Test Function, and select Configure Test Parameters. The following code snippet shows the test parameters:
{ "endpoint": "http://oss-cn-hangzhou.aliyuncs.com", "bucket": "web****", "objectName": "myObj", "message": "your-message" }On the Code tab, write code in the code editor and click Deploy.
In this example, a built-in Python runtime is used. You can use the temporary key provided by Function Compute to access OSS.
import json import oss2 def handler(event, context): evt = json.loads(event) creds = context.credentials # Enter the temporary key, including the temporary token. # The AccessKey ID and AccessKey secret of an Alibaba Cloud account can be used to access all API operations. Using these credentials to perform operations in Function Compute is a high-risk operation. We recommend that you use a RAM user to call API operations or perform routine O&M. # We recommend that you avoid saving the AccessKey pair in your project code. If this sensitive information is leaked, the security of all resources in your account could be compromised. # In this example, the AccessKey pair is obtained from the context. auth = oss2.StsAuth(creds.access_key_id, creds.access_key_secret, creds.security_token) bucket = oss2.Bucket(auth, evt['endpoint'], evt['bucket']) bucket.put_object(evt['objectName'], evt['message']) return 'success'Click Test Function. After the function is executed, log on to the OSS console and find the desired bucket. You can see that the content of the object is replaced with
messagein the test parameters.