To use the Alibaba Cloud Trusted System, you must enable specific permissions when you create a trusted instance. This allows the trusted instance to report trust information to Security Center upon startup. This topic describes how to create a trusted instance that uses the Alibaba Cloud Trusted System.
Create a trusted instance
Console
The steps to create a trusted instance in the console are similar to the steps for creating a regular instance. However, you must configure specific options. This section describes the configurations that are specific to trusted instances. For more information about other general configurations, see Create an instance using the wizard.
Go to ECS console - Instances.
Click Create Instance.
In the Instance and Image section, select an instance and an image.
Instance: Select a vTPM-enabled instance type. For more information, see Instance families that support trusted computing.
Image:
Select Trusted System.
NoteIf you select Trusted System, the Alibaba Cloud Trusted System is enabled for the instance and performs trust verification when the instance starts. If you want to build your own trusted service system, you can skip this step.
Select a supported image version based on the instance family.
In the Bandwidth and Security Group section, select a security group. If the Activate KMS dialog box appears, click Activate.
You must activate KMS when you create a trusted instance. Otherwise, instance creation fails.
If required, click Advanced Settings and select Instance RAM Role.
If you have selected Trusted System for the instance, you must set a RAM role that has permissions to access the trusted service. Alibaba Cloud provides the service role AliyunECSInstanceForYundunSysTrustRole for this purpose. We recommend that you follow these steps to set this role:
NoteIf you require more precise or customized configurations, you can create a custom role and grant the required permissions. For more information about the precautions for creating a custom RAM role, see Precautions on RAM role permissions.
Click Authorize.
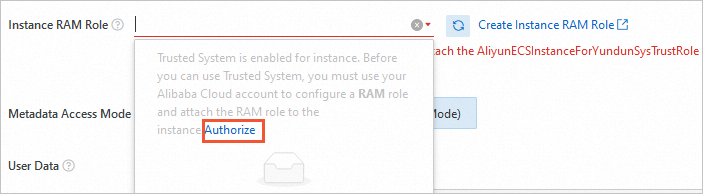
In the Authorize Access to Cloud Resources dialog box, click Approve
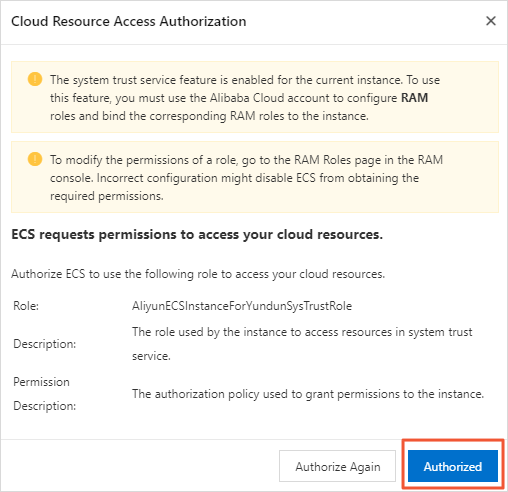
In the new window, click Authorize.
Click Authorized.
Select the AliyunECSInstanceForYundunSysTrustRole RAM role.
 Note
NoteYou can also skip this step and grant the authorization after you create the instance. For more information, see Instance RAM role.
Follow the on-screen instructions to complete the instance creation.
API
When you call an API to create a trusted instance, note the following points:
You must first activate KMS. Otherwise, instance creation fails. For more information, see Activate Key Management Service.
If you use the Alibaba Cloud Trusted System, you must set a RAM role that has permissions to access the trusted service. This allows the trusted instance to report trust information to Security Center upon startup. For more information, see Instance RAM role. For information about the precautions for creating a custom RAM role, see Precautions on RAM role permissions.
NoteIf you build your own trusted service system, you do not need to set this RAM role.
You can call RunInstances or CreateInstance to create an instance. The following table describes the parameters that you must configure.
Parameter | Description | Example |
InstanceType | Specify an instance type that supports the vTPM feature. For more information, see Instance families that support trusted computing. | ecs.c6t.large |
ImageId | Specify the ID of an image that is supported by trusted instances. You can call DescribeImages to view image IDs. | aliyun_2_1903_x64_20G_secured_alibase_20210325.vhd |
SystemDisk.Category | Trusted instances support only ESSDs. | cloud_essd |
VSwitchId | Trusted instances support only VPCs. Therefore, you must specify a virtual switch ID. | vsw-bp134jzf285qg9u6w**** |
RamRoleName | Specify the name of the RAM role. You can also call AttachInstanceRamRole to grant a RAM role to the instance after the instance is created. | AliyunECSInstanceForYundunSysTrustRole |
UserData | Specify the installation script for installing the Alibaba Cloud Trusted System. The script must be Base64-encoded. For the plaintext content of the script before Base64 encoding, see Script for installing the Alibaba Cloud Trusted System. | |
SecurityOptions.TrustedSystemMode | The trusted system mode. When you call RunInstances to create a trusted instance, if you set the InstanceType parameter to g7t, c7t, or r7t, you must set Note When you create an ECS instance for a trusted system using an OpenAPI, you can only call RunInstances. CreateInstance does not support the trusted system mode parameter ( | vTPM |
Sample request:
https://ecs.aliyuncs.com/?Action=RunInstances
&RegionId=cn-hangzhou
&InstanceType=ecs.c6t.large
&ImageId=aliyun_2_1903_x64_20G_secured_alibase_20210325.vhd
&SystemDisk.Category=cloud_essd
&VSwitchId=vsw-bp134jzf285qg9u6w****
&SecurityGroupId=sg-bp1c3o8hzd14dovh****
&RamRoleName=AliyunECSInstanceForYundunSysTrustRole
&UserData=IyEvYmluL3NoCkNVUlBBVEg9YHB3ZGAKU0NSSVBUX1BBVEg9Ii9kb3dubG9hZC9saW51eC9zY3JpcHQvVHJ1c3RBZ2VudEluc3RhbGwuc2giClRPS0VOPWBjdXJsIC1zIC1YIFBVVCAtSCAiWC1hbGl5dW4tZWNzLW1ldGFkYXRhLXRva2VuLXR0bC1zZWNvbmRzOiA1IiAiaHR0cDovLzEwMC4xMDAuMTAwLjIwMC9sYXRlc3QvYXBpL3Rva2VuImAKUkVHSU9OX0lEPWBjdXJsIC1zIC1IICJYLWFsaXl1bi1lY3MtbWV0YWRhdGEtdG9rZW46ICR0b2tlbiIgaHR0cDovLzEwMC4xMDAuMTAwLjIwMC9sYXRlc3QvbWV0YS1kYXRhL3JlZ2lvbi1pZGAKVVBEQVRFX1NJVEUxPWh0dHA6Ly90cnVzdGNsaWVudC0ke1JFR0lPTl9JRH0ub3NzLSR7UkVHSU9OX0lEfS1pbnRlcm5hbC5hbGl5dW5jcy5jb20KVVBEQVRFX1NJVEUyPWh0dHA6Ly90cnVzdGNsaWVudC0ke1JFR0lPTl9JRH0ub3NzLSR7UkVHSU9OX0lEfS5hbGl5dW5jcy5jb20KVVBEQVRFX1NJVEUzPWh0dHA6Ly90LXRydXN0Y2xpZW50LSR7UkVHSU9OX0lEfS5vc3MteyRSRUdJT05fSUR9LWludGVybmFsLmFsaXl1bmNzLmNvbQpNU0dfSU5GTz0iZG93bmxvYWRpbmcgaW5zdGFsbCBzY3JpcHQgZnJvbSBzaXRlIgpNU0dfRVJSPSJkb3dubG9hZCBmaWxlIGVycm9yLiIKTVNHX09LPSJ0cnVzdCBjbGllbnQgaW5pdCBkb25lLiIKCmluc3RhbGwoKQp7CmVjaG8gIiR7TVNHX0lORk99IiIgMS4uLiIKY3VybCAtZnNTTCAiJHtVUERBVEVfU0lURTF9IiIke1NDUklQVF9QQVRIfSJ8c2gKaWYgWyAkPyA9PSAwIF07IHRoZW4KcmV0dXJuIDEKZmkKZWNobyAiJHtNU0dfSU5GT30iIiAyLi4uIgpjdXJsIC1mc1NMICIke1VQREFURV9TSVRFMn0iIiR7U0NSSVBUX1BBVEh9InxzaAppZiBbICQ/ID09IDAgXTsgdGhlbgpyZXR1cm4gMgpmaQplY2hvICIke01TR19JTkZPfSIiIDMuLi4iCmN1cmwgLWZzU0wgIiR7VVBEQVRFX1NJVEUzfSIiJHtTQ1JJUFRfUEFUSH0ifHNoCmlmIFsgJD8gPT0gMCBdOyB0aGVuCnJldHVybiAzCmZpCmVjaG8gIiIgMT4mMgpleGl0IDEKfQoKaW5zdGFsbAplY2hvICIke01TR19PS30iCgpleGl0IDAK
&<Common request parameters>Sample responses:
XML format
<RunInstancesResponse> <RequestId>04F0F334-1335-436C-A1D7-6C044FE73368</RequestId> <InstanceIdSets> <InstanceIdSet>i-bp16byi4f3fti5b3****</InstanceIdSet> </InstanceIdSets> </RunInstancesResponse>JSON format
{ "RequestId": "BB694A51-7860-4B5C-B906-9B4077798672", "InstanceIdSets": { "InstanceIdSet": [ "i-bp16byi4f3fti5b3****" ] } }
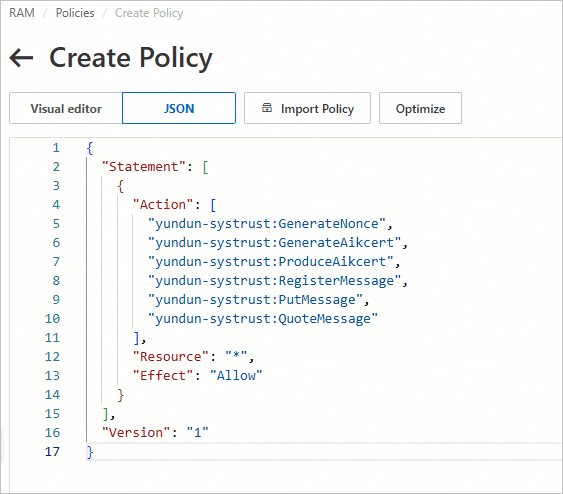
Precautions on RAM role permissions
We recommend that you create a custom policy with the minimum required permissions and attach it to the RAM role. You can select System Policy (AliyunSysTrustFullAccess) or Custom Policy for the trusted service. The following policy provides fine-grained permissions for accessing the trusted service:
RAM permissions involve security risks. We strongly recommend that you follow the principle of least privilege and do not grant excessive permissions to roles. For more information, see What is Resource Access Management.
{
"Statement": [
{
"Action": [
"yundun-systrust:GenerateNonce",
"yundun-systrust:GenerateAikcert",
"yundun-systrust:ProduceAikcert",
"yundun-systrust:RegisterMessage",
"yundun-systrust:PutMessage",
"yundun-systrust:QuoteMessage"
],
"Resource": "*",
"Effect": "Allow"
}
],
"Version": "1"
}Script for installing the Alibaba Cloud Trusted System
#!/bin/sh
CURPATH=`pwd`
SCRIPT_PATH="/download/linux/script/TrustAgentInstall.sh"
TOKEN=`curl -s -X PUT -H "X-aliyun-ecs-metadata-token-ttl-seconds: 5" "http://100.100.100.200/latest/api/token"`
REGION_ID=`curl -s -H "X-aliyun-ecs-metadata-token: $token" http://100.100.100.200/latest/meta-data/region-id`
UPDATE_SITE1=http://trustclient-${REGION_ID}.oss-${REGION_ID}-internal.aliyuncs.com
UPDATE_SITE2=http://trustclient-${REGION_ID}.oss-${REGION_ID}.aliyuncs.com
UPDATE_SITE3=http://t-trustclient-${REGION_ID}.oss-{$REGION_ID}-internal.aliyuncs.com
MSG_INFO="downloading install script from site"
MSG_ERR="download file error."
MSG_OK="trust client init done."
install()
{
echo "${MSG_INFO}"" 1..."
curl -fsSL "${UPDATE_SITE1}""${SCRIPT_PATH}"|sh
if [ $? == 0 ]; then
return 1
fi
echo "${MSG_INFO}"" 2..."
curl -fsSL "${UPDATE_SITE2}""${SCRIPT_PATH}"|sh
if [ $? == 0 ]; then
return 2
fi
echo "${MSG_INFO}"" 3..."
curl -fsSL "${UPDATE_SITE3}""${SCRIPT_PATH}"|sh
if [ $? == 0 ]; then
return 3
fi
echo "" 1>&2
exit 1
}
install
echo "${MSG_OK}"
exit 0